2014-12-03 - EMOTET INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-03-Emotet-infection-traffic.pcap.zip 85.9 kB (85,938 bytes)
- 2014-12-03-malware-from-Emotet-infection.zip 252.5 kB (252,428 bytes)
REFERENCE:
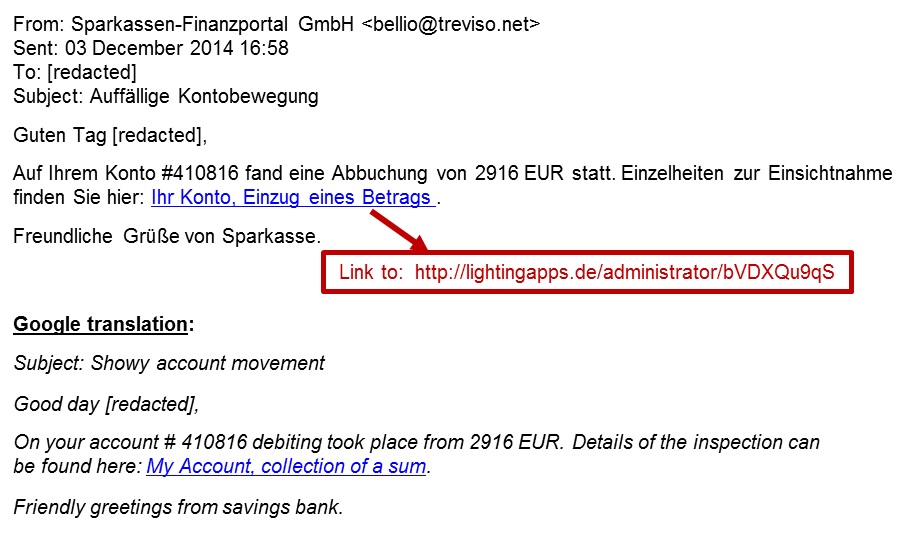
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: Sparkassen-Finanzportal GmbH <bellio@treviso[.]net>
Sent: 03 December 2014 16:58
To: [redacted]
Subject: Auffällige Kontobewegung
Guten Tag [redacted],
Auf Ihrem Konto #410816 fand eine Abbuchung von 2916 EUR statt. Einzelheiten zur Einsichtnahme finden Sie hier: Ihr Konto, Einzug eines Betrags .
Freundliche Grüße von Sparkasse.
GOOGLE TRANSLATION:
Subject: Showy account movement
Good day [redacted],
On your account # 410816 debiting took place from 2916 EUR. Details of the inspection can be found here: My Account, collection of a sum.
Friendly greetings from savings bank.
LINK FROM THE EMAIL:
80.86.91[.]225 - lightingapps[.]de - GET /administrator/bVDXQu9qS/
PRELIMINARY MALWARE ANALYSIS
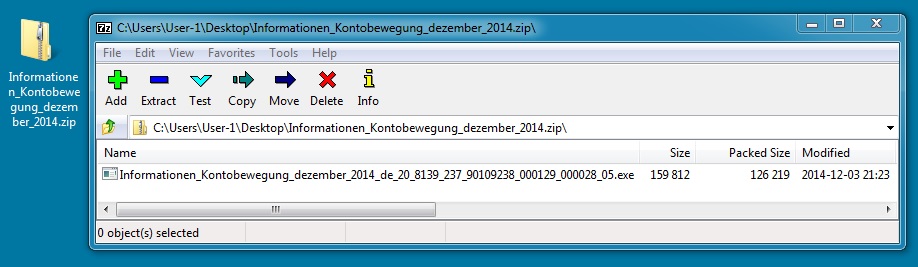
DOWNLOADED ZIP FILE:
File name: Informationen_Kontobewegung_dezember_2014.zip
File size: 126,489 bytes
MD5 hash: ab1740928bec43fde051c7c6c0cfccec
Detection ratio: 6 / 55
First submission: 2014-12-03 17:51:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/0e4dfe31a2b1e165b5e7fc7053d3e7a0ba1ae160d2fbd3435526d9dd76376d61/analysis/
EXTRACTED MALWARE:
File name: Informationen_Kontobewegung_dezember_2014_de_20_8139_237_90109238_000129_000028_05.exe
File size: 159,812 bytes
MD5 hash: 8e9111802bf368404c2a18222b3eb986
Detection ratio: 7 / 55
First submission: 2014-12-03 17:27:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c4ca41292c07252bb043dae7697a91c140ba9be82fac5cd62c9f9c802959e0d/analysis/
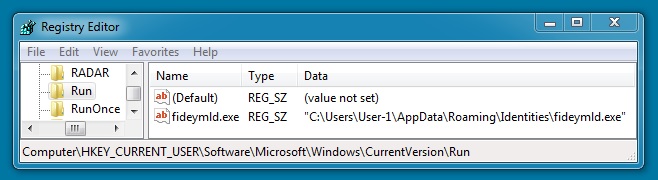
Shown above: registry entry indicating where the malware copies itself
INFECTION TRAFFIC
Downloading the malware:
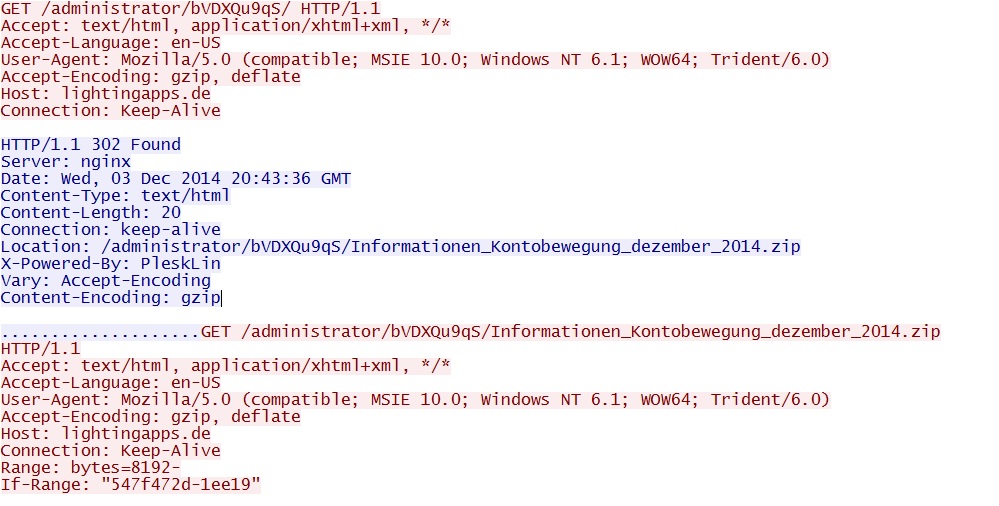
- 2014-12-03 20:43:54 UTC - 80.86.91[.]225:80 - lightingapps[.]de - GET /administrator/bVDXQu9qS/
- 2014-12-03 20:43:46 UTC - 80.86.91[.]225:80 - lightingapps[.]de - GET /administrator/bVDXQu9qS/Informationen_
Kontobewegung_dezember_2014.zip
Executing Informationen_Kontobewegung_dezember_2014_de_20_8139_237_90109238_000129_000028_05.exe in a VM:
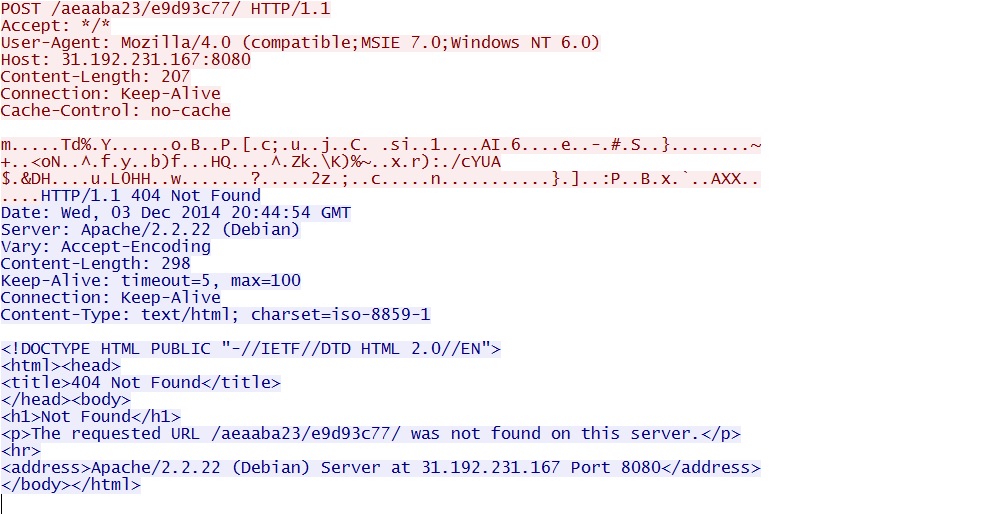
- 2014-12-03 20:44:54 UTC - 31.192.231[.]167:8080 - 31.192.231[.]167:8080 - POST /aeaaba23/e9d93c77/
- 2014-12-03 20:44:54 UTC - 198.7.59[.]161:8080 - 198.7.59[.]161:8080 - POST /aeaaba23/e9d93c77/
- 2014-12-03 20:44:55 UTC - 198.41.249[.]53:8080 - 198.41.249[.]53:8080 - POST /aeaaba23/e9d93c77/
- 2014-12-03 20:47:05 UTC - 104.28.26[.]52:8080 - 104.28.26[.]52:8080 - POST /aeaaba23/e9d93c77/
- 2014-12-03 20:48:16 UTC - 31.192.231[.]167:8080 - 31.192.231[.]167:8080 - POST /aeaaba23/e9d93c77/
- 2014-12-03 20:48:16 UTC - 198.7.59[.]161:8080 - 198.7.59[.]161:8080 - POST /aeaaba23/e9d93c77/
- 2014-12-03 20:48:16 UTC - 198.41.249[.]53:8080 - 198.41.249[.]53:8080 - POST /aeaaba23/e9d93c77/
SNORT EVENTS
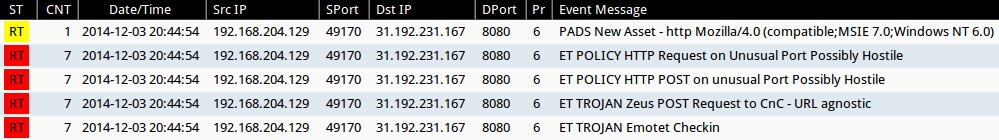
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata 2.0.4:
- 2014-12-03 20:44:54 UTC - 31.192.231[.]167:8080 - ET TROJAN Zeus POST Request to CnC - URL agnostic (sid:2013976)
- 2014-12-03 20:44:54 UTC - 31.192.231[.]167:8080 - ET TROJAN Emotet Checkin (sid:2019693)
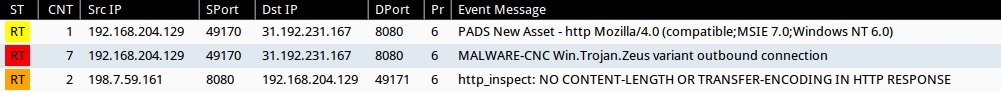
Sourcefire VRT ruleset from Sguil on Security Onion using Snort 2.9.7.0:
- 2014-12-03 20:44:54 UTC - 31.192.231[.]167:8080 - MALWARE-CNC Win.Trojan.Zeus variant outbound connection (sid:32585)
SCREENSHOTS
Downloading the malware from the email link:
Example of the post-infection traffic:
Click here to return to the main page.