2014-12-11 - MALWARE INFECTION FROM ASPROX BOTNET MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-11-Asprox-malspam-tracking.csv.zip 2.5 kB (2,536 bytes)
- 2014-12-11-traffic-by-malware-from-Asprox-malspam-run-on-a-VM.pcap.zip 1.1 MB (1,076,064 bytes)
- 2014-12-11-malware-and-artifacts-from-the-infection.zip 757.6 kB (757,569 bytes)
- 2014-12-11-Asprox-malspam-example.eml.zip 1.9 kB (1,932 bytes)
NOTES:
- @Techhelplist (no longer active) reported on this earlier today at: techhelplist[.]com/index.php/spam-list/694-facebook-password-change-asprox-malware-v2 (page no longer exists, and it's not on the Internet Archive)
- This blog entry is a follow-up that includes the emails I've found, malware samples, and traffic from an infected VM.
- Below are the emails I found with the subject line Facebook password change. Asprox has used other variations with the word "Facebook" in the subject line.
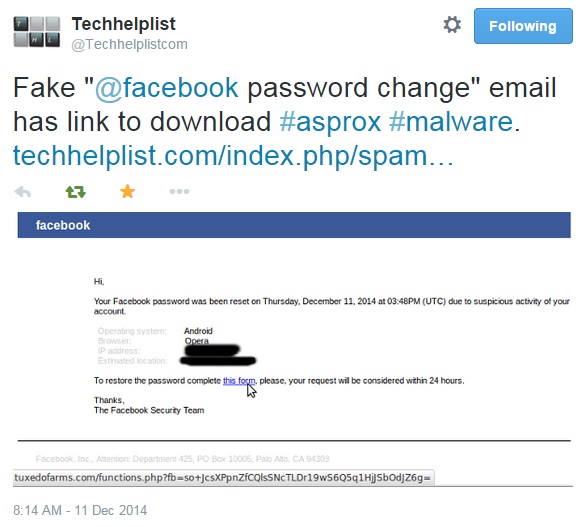
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
Subject: Facebook password change
Date: Thu, 11 Dec 2014 12:43:19 UTC
From: Facebook <notification@gruasorion[.]com>
Reply-To: Facebook <notification@gruasorion[.]com>
To:
Hi,
Your Facebook password was been reset on Thursday, December 11, 2014 at 12:42PM (UTC) due to suspicious activity of your account.
Operating system: Windows
Browser: Google Chrome
IP address: [omitted]
Estimated location: Proctor, OK, US
To restore the password complete this form please, your request will be considered within 24 hours.
Thanks,
The Facebook Security Team
Facebook, Inc., Attention: Department 425, PO Box 10005, Palo Alto, CA 94303
NOTE: From what I can tell, Asprox uses random values for the OS, browser, IP, and estimated location. I omitted the IP address above, because some people scrape these blog entries for malicious IP addresses.
VM INFECTION TRAFFIC
DOWNLOADING THE ASPROX ZIP FILE:
- 2014-12-11 17:40:08 UTC - 208.88.133[.]116:80 - digest.sagepub[.]com - GET /template.php?fb=ZqxmdLEfXtVt+vSTgZPQr4HuNeYy0gaxNY+SHrKn3zM=
EXECUTING THE EXTRACTED MALWARE IN A VM:
- 2014-12-11 17:43:51 UTC - 208.81.237[.]99:8080 - 208.81.237[.]99:8080 - POST /index.php
- 2014-12-11 17:44:10 UTC - 67.183.123[.]151:80 - lifeprooffre[.]com - GET /catalog/789
- 2014-12-11 17:44:12 UTC - 77.123.108[.]4:80 - adminaoffline[.]com - GET /datamousthoping/mod_smartslider2/
- 2014-12-11 17:46:50 UTC - 95.164.12[.]24:80 - adminaoffline[.]com - GET /jshoppi/soft32.dll
- 2014-12-11 17:46:59 UTC - 67.183.123[.]151:80 - linktohttps[.]com - GET /b/eve/d23e74dde53e536906ade2b3
- 2014-12-11 17:47:16 UTC - 133.242.54[.]221:443 - POST /index.php
- 2014-12-11 17:47:49 UTC - 37.25.102[.]37:80 - linktohttps[.]com - POST /b/opt/4C39DA050DB46D8E3AB44A3A
- 2014-12-11 17:47:54 UTC - 37.25.102[.]37:80 - linktohttps[.]com - GET /b/letr/83149EADBA4F7EC88D4F597C
- 2014-12-11 17:47:59 UTC - 37.25.102[.]37:80 - linktohttps[.]com - GET /b/letr/83149EADBA4F7EC88D4F597C
- 2014-12-11 17:48:00 UTC - 195.245.194[.]102:8080 - 195.245.194[.]102:8080 - POST /b/opt/85B756550F56CC0B3856EBBF
- 2014-12-11 17:48:06 UTC - 195.245.194[.]102:8080 - 195.245.194[.]102:8080 - GET /b/letr/385E5562C7E1145CF0E133E8
- 2014-12-11 17:48:09 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - POST /b/opt/D00275A2D88326A7EF830113
- 2014-12-11 17:48:12 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - POST /b/opt/A7E95B6D26206F1C112048A8
- 2014-12-11 17:48:31 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - POST /b/req/A04533BCFDCAE120CACAC694
- 2014-12-11 17:48:34 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - GET /b/eve/9ef85855a9f87fe16aef9187
- 2014-12-11 17:49:20 UTC - 133.242.54[.]221:443 - POST /index.php
- 2014-12-11 17:49:26 UTC - 79.142.66[.]239:80 - report.9i1q9ws7931yw3u7my1[.]com - GET /?EI9320=%96%9C%D4%[long string of characters]
- 2014-12-11 17:49:29 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - POST /b/req/5F29E613C0CB0FD7F7CB2863
- 2014-12-11 17:49:34 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - GET /b/eve/4b273de97c271a5da3f7f2d6
- 2014-12-11 17:50:31 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - POST /b/req/2F0BE089032BC999342BEE2D
- 2014-12-11 17:50:47 UTC - 70.32.94[.]46:8080 - 70.32.94[.]46:8080 - POST /b/req/BFCB8BC39FE7A71CA8E780A8
- 2014-12-11 17:50:59 UTC - 37.221.168[.]59:80 - 37.221.168[.]59 - GET /b/pkg/T51405fc9a5jjao
CLICK FRAUD TRAFFIC FROM THE INFECTED VM BEGINS:
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - sheepdog-shop[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - perspectivism-new[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - mainnav-active[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - sheepdog-shop[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - jseradio[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - personal-stereo[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - perspectivism-new[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - darkblue-new[.]com - GET /
- 2014-12-11 17:50:49 UTC - 46.161.41[.]220:80 - shimmer-lite[.]com - GET /
SNORT EVENTS
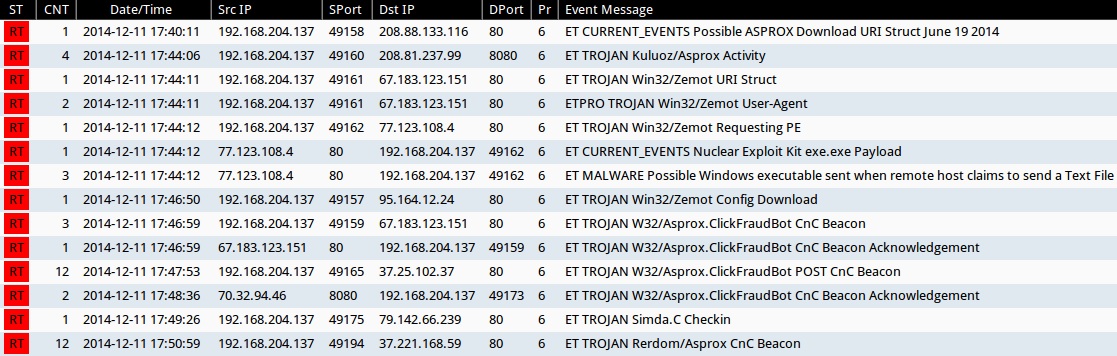
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata (not including ET INFO or ET POLICY rules):
- 2014-12-11 17:40:11 UTC - 208.88.133[.]116:80 - ET CURRENT_EVENTS Possible ASPROX Download URI Struct June 19 2014 (sid:2018589)
- 2014-12-11 17:44:06 UTC - 208.81.237[.]99:8080 - ET TROJAN Kuluoz/Asprox Activity (sid:2017895)
- 2014-12-11 17:44:11 UTC - 67.183.123[.]151:80 - ET TROJAN Win32/Zemot URI Struct (sid:2019458)
- 2014-12-11 17:44:11 UTC - 67.183.123[.]151:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-12-11 17:44:12 UTC - 77.123.108[.]4:80 - ET TROJAN Win32/Zemot Requesting PE (sid:2019759)
- 2014-12-11 17:44:12 UTC - 77.123.108[.]4:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- 2014-12-11 17:44:12 UTC - 77.123.108[.]4:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-12-11 17:46:50 UTC - 95.164.12[.]24:80 -ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 2014-12-11 17:46:59 UTC - 67.183.123[.]151:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-12-11 17:46:59 UTC - 67.183.123[.]151:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-12-11 17:47:53 UTC - 37.25.102[.]37:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 2014-12-11 17:48:36 UTC - 70.32.94[.]46:8080 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-12-11 17:49:26 UTC - 79.142.66[.]239:80 - ET TROJAN Simda.C Checkin (sid:2016300)
- 2014-12-11 17:50:59 UTC - 37.221.168[.]59:80 - 37.221.168[.]59 - ET TROJAN Rerdom/Asprox CnC Beacon (sid:2019760)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor rules):
- 2014-12-11 17:43:51 UTC - 208.81.237[.]99:8080 - [1:32706:1] MALWARE-CNC Win.Trojan.Kuluoz variant outbound connection
- 2014-12-11 17:44:12 UTC - 77.123.108[.]4:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- 2014-12-11 17:44:12 UTC - 77.123.108[.]4:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-12-11 17:46:59 UTC - 67.183.123[.]151:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-12-11 17:47:17 UTC - 133.242.54[.]221:443 - [1:32706:1] MALWARE-CNC Win.Trojan.Kuluoz variant outbound connection
- 2014-12-11 17:47:49 UTC - 37.25.102[.]37:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-12-11 17:48:00 UTC - 195.245.194[.]102:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-12-11 17:48:09 UTC - 70.32.94[.]46:8080 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- 2014-12-11 17:49:26 UTC - 79.142.66[.]239:80 - [1:22937:5] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
PRELIMINARY MALWARE ANALYSIS
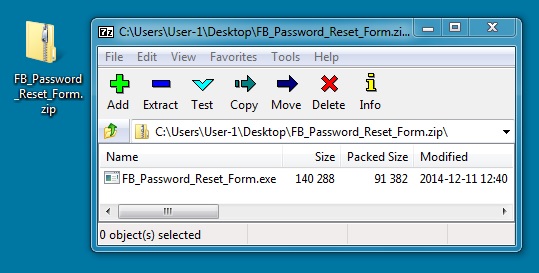
DOWNLOADED ZIP FILE:
File name: FB_Password_Reset_Form.zip
File size: 91,532 bytes
MD5 hash: 14e7aed0139942e33e9f072ed67ad455
Detection ratio: 7 / 49
First submission: 2014-12-11 18:15:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/ea678b163e037bc7c6fcd8611908102ece6ee3d76709559d9330473edf1da220/analysis/
EXTRACTED MALWARE:
File name: FB_Password_Reset_Form.exe
File size: 140,288 bytes
MD5 hash: d513bc67e078cd1bf8964e0abca63935
Detection ratio: 8 / 56
First submission: 2014-12-11 18:16:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/6cc8cd11080b3784377f3340b2eb8243bb7ee3a2650dbf2d46367365c4352f9c/analysis/
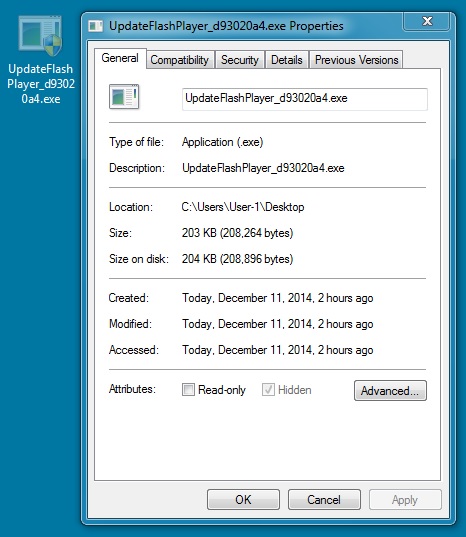
DROPPED MALWARE FROM INFECTED VM - RERDOM:
File name: UpdateFlashPlayer_d93020a4.exe
File size: 208,264 bytes
MD5 hash: 818c1fa464e63fb2e588c0e447cb2baf
Detection ratio: 6 / 56
First submission: 2014-12-11 17:38:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/8b39a15f8a43ea17c77e3b535224ccb29632ec152bfc18e92c19984fd60107f8/analysis/
ZIP of pcap from sandbox analysis: 2014-12-11-Asprox-dropped-malware-01.pcap.zip
Copy from the infected VM user's AppData\Local\Temp folder before it
deleted itself.
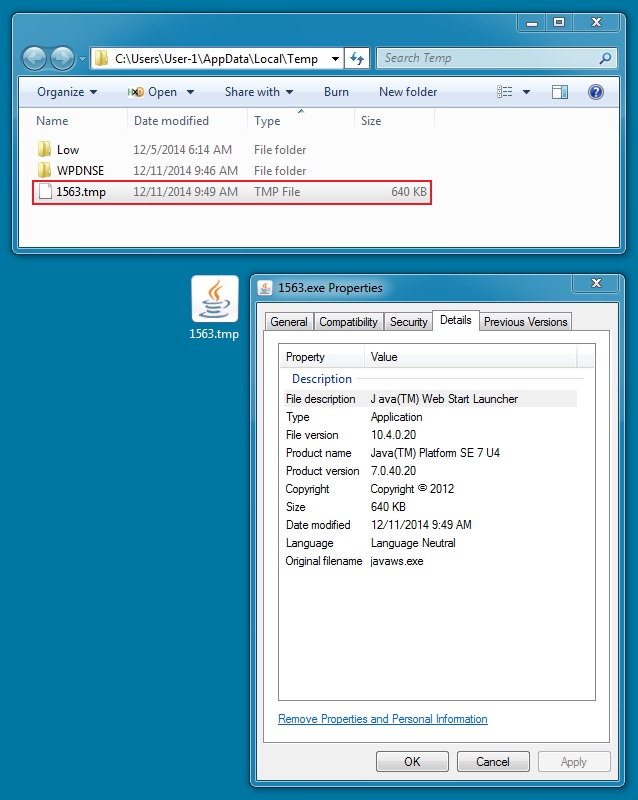
DROPPED MALWARE FROM INFECTED VM - SIMDA:
File name: 1563.tmp
File size: 655,360 bytes
MD5 hash: 7a3d8b487b21ff7f63632964682dc9cb
Detection ratio: 7 / 56
First submission: 2014-12-11 18:19:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/9c254302c8a1237af047633962fda6d55104cbd8e43fcd02221c7e2c42a0299a/analysis/
ZIP of pcap from sandbox analysis: 2014-12-11-Asprox-dropped-malware-02.pcap.zip
Click here to return to the main page.