2014-12-12 - RANSOMWARE INFECTION AFTER NUCLEAR EK FROM 128.199.52[.]211 - YQUESRERMAN[.]GA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-12-Nuclear-EK-traffic.pcap.zip 612.7 kB (612,734 bytes)
- 2014-12-12-Nuclear-EK-malware.zip 185.5 kB (185,535 bytes)
NOTES:
- I'm finding more Nuclear EK, now that it's been updated and the traffic patterns have changed.
- See my 2014-12-10 blog entry for details on Nuclear EK's new traffic patterns (payload being XOR-ed, etc).
- Unlike the 2014-12-10 blog entry on Nuclear EK, this one was not caused by Operation Windigo, so it has a different payload.
- The malware didn't do anything when I infected the VM earlier in the day.
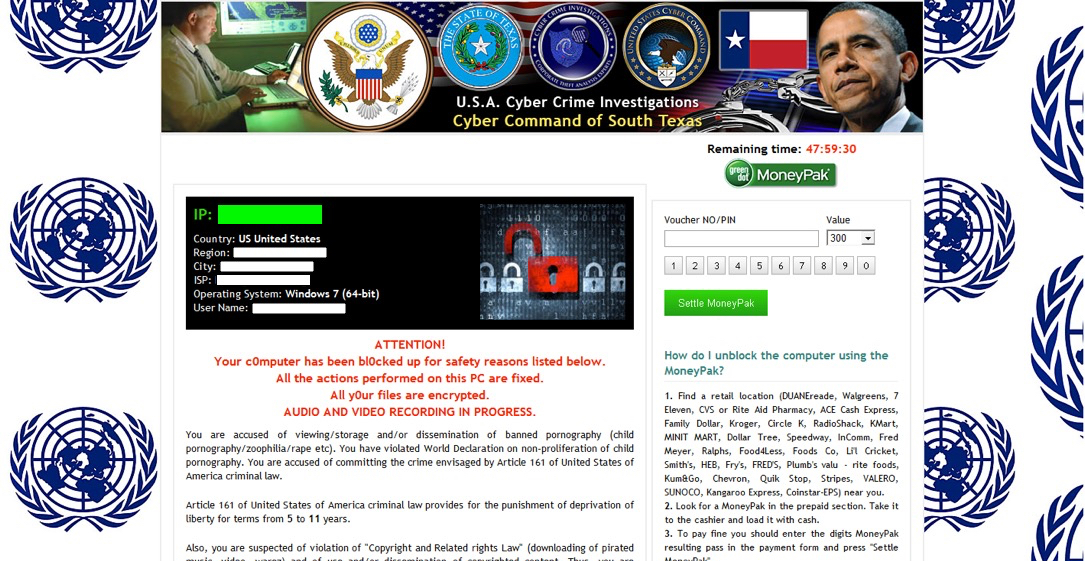
- I ran the malware on another VM later that evening and got ransomware (see the image below).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 128.199.52[.]211 - yquesrerman[.]ga - Nuclear EK
- 176.9.245[.]80 - bloghersked[.]com - post-infection traffic
Nuclear EK:
- 2014-12-12 21:43:07 UTC - yquesrerman[.]ga - GET /AkNVHkgGT0Q.html
- 2014-12-12 21:43:09 UTC - yquesrerman[.]ga - GET /AwoVG1ADAw4OUhlVDlRTBQoHRUJTXVYOUVYaAwtGXFRVVFxXVwBOVRtA
- 2014-12-12 21:43:11 UTC - yquesrerman[.]ga - GET /ABsJAkhWAkcLGlEaQRlWAAMLQ0BWUF5CGVMFHAJPQ0hXVkBLVQQGT0IOIhMIIw4ffQ
- 2014-12-12 21:43:15 UTC - yquesrerman[.]ga - GET /ABsJAkhWAkcLGlEaQRlWAAMLQ0BWUF5CGVMFHAJPQ0hXVkBLVQQGT0IOCB0uGQEzYlVPRQ
- 2014-12-12 21:43:16 UTC - yquesrerman[.]ga - GET /AwoVG1ADAw4OUhlVDlRTBQoHRUJTXVYOUVYaAwtGXFRVVFxXVwBOQB4eEAAU
- 2014-12-12 21:43:17 UTC - yquesrerman[.]ga - GET /ABsJAkhWAkcLGlEaQRlWAAMLQ0BWUF5CGVMFHAJPQ0hXVkBLVQQGT0AOIhMIIw4ffQ
- 2014-12-12 21:43:21 UTC - yquesrerman[.]ga - GET /ABsJAkhWAkcLGlEaQRlWAAMLQ0BWUF5CGVMFHAJPQ0hXVkBLVQQGT0AOCB0uGQEzYlVPRQ
- 2014-12-12 21:43:22 UTC - yquesrerman[.]ga - GET /ABsJAkhWAkcLGlEaQRlWAAMLQ0BWUF5CGVMFHAJPQ0hXVkBLVQQGT08OIhMIIw4ffQ
- 2014-12-12 21:43:25 UTC - yquesrerman[.]ga - GET /ABsJAkhWAkcLGlEaQRlWAAMLQ0BWUF5CGVMFHAJPQ0hXVkBLVQQGT08OCB0uGQEzYlVPRQ
POST-INFECTION TRAFFIC:
- 2014-12-12 21:44:23 UTC - bloghersked[.]com - GET /mf_llksxjSOQYxu5lzLdigricqvz2vcvt_jzifnsuoYbufEqAvPhOEip2ntpo3tzjz_yxhr_yhwg_zkbHgSqGyz1
QBzxPWCvDZppsmufIfatBFvshc1QvAsVZ.html - 2014-12-12 21:44:36 UTC - bloghersked[.]com - GET /vz_VCvt2jz0iFnSuoYbufVeLulGCbPatHjw9prneWHtwzl7SAsqvcdm9HOin6pcJWwq1gn0lj4lmoe-avD
ANNtavvas2yxsc_jnzx_bhdhrqzu9gfcb6hYIeHoypfx.html
SNORT EVENTS
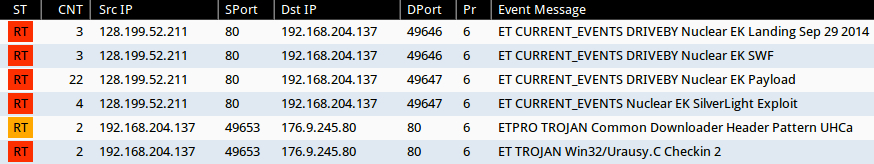
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata (without ET POLICY or ET INFO events):
- 128.199.52[.]211:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Sep 29 2014 (sid:2019315)
- 128.199.52[.]211:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 128.199.52[.]211:80 - ET CURRENT_EVENTS Nuclear EK SilverLight Exploit (sid:2019917)
- 128.199.52[.]211:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 176.9.245[.]80:80 - ETPRO TROJAN Common Downloader Header Pattern UHCa (sid:2803270)
- 176.9.245[.]80:80 - ET TROJAN Win32/Urausy.C Checkin 2 (sid:2016567)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Debian 7.6:
- 128.199.52[.]211:80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-12-12-Nuclear-EK-flash-exploit.swf
File size: 22,361 bytes
MD5 hash: 9b3ad66a2a61e8760602d98b537b7734
Detection ratio: 0 / 56
First submission: 2014-12-13 01:24:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/00730977f6a6c1e8a7221a11785e525cdc2a39638b869d77da9b828e4643f839/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-12-12-Nuclear-EK-silverlight-exploit.xap (same as the one from 2014-12-10)
File size: 6,924 bytes
MD5 hash: 87d140b1b68cbe2b46a4a355fbd87a09
Detection ratio: 10 / 55
First submission: 2014-12-10 18:31:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/a0b5876419025568915bfea24d22163169f4b3634935edafd998c26d57900055/analysis/
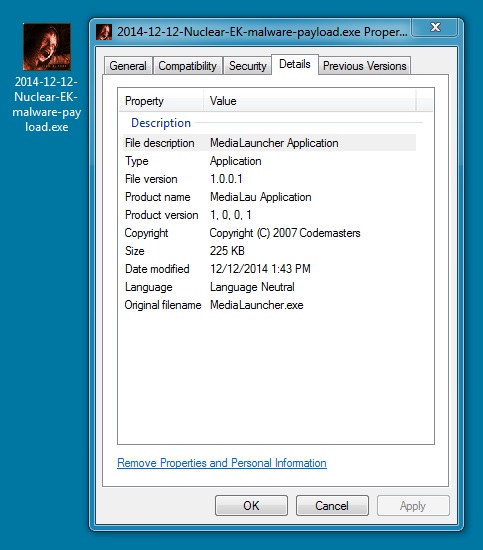
MALWARE PAYLOAD:
File name: 2014-12-12-Nuclear-EK-malware-payload.exe
File size: 230,400 bytes
MD5 hash: bf230af91ac92924a745f42021abbba0
Detection ratio: 7 / 53
First submission: 2014-12-13 01:24:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/18cb84c0d9c87fa5ed74da826270bd416aa039795b731fc91e700b03b7738610/analysis/
SCREENSHOTS
Full view of the ransomware screen from the infected VM:
Click here to return to the main page.