2014-12-16 - MALWARE INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-16-malspam-tracker.csv.zip 1.2 kB (1,195 bytes)
- 2014-12-16-unidentified-malware-run-on-VM.pcap.zip 74.2 kB (74,156 bytes)
- 2014-12-16-unidentified-malware-and-artifacts.zip 71.6 kB (71,599 bytes)
NOTES:
- On 2014-12-16 from 12:09 to 13:20 UTC, I noticed a wave of 12 emails with .cab attachments containing malware.
- These had spoofed UK sending addresses, and they were sent to recipients in the UK.
- Various sending IP addresses for the messages indicate this was a botnet-based campaign.
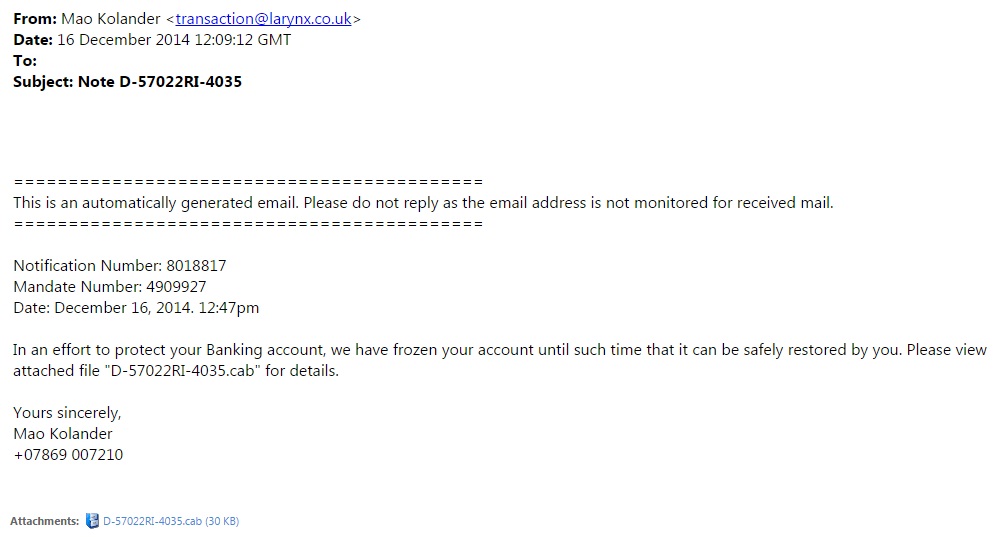
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: Mao Kolander <transaction@larynx[.]co[.]uk>
Date: 16 December 2014 12:09:12 GMT
To:
Subject: Note D-57022RI-4035
===========================================
This is an automatically generated email. Please do not reply as the email address is not monitored for received mail.
===========================================
Notification Number: 8018817
Mandate Number: 4909927
Date: December 16, 2014. 12:47pm
In an effort to protect your Banking account, we have frozen your account until such time that it can be safely restored by you. Please view attached file "D-57022RI-4035.cab" for details.
Yours sincerely,
Mao Kolander
+07869 007210
Attachment: D-57022RI-4035.cab (30 KB)
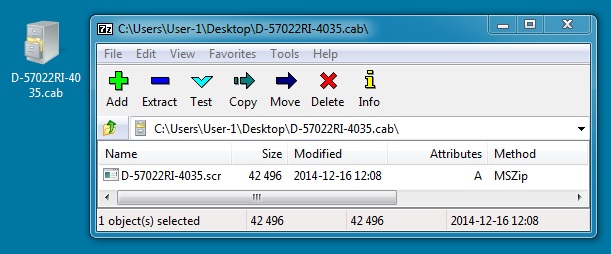
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: D-57022RI-4035.cab
File size: 30,805 bytes
MD5 hash: cfc6098ab3a1bbbb93c70fcf3f19cf5a
Detection ratio: 2 / 55
First submission: 2014-12-16 16:26:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/9d6065082b457c6991fdc14d6d2d72100f2772f2043739c05d7c0b4ecdc95893/analysis/
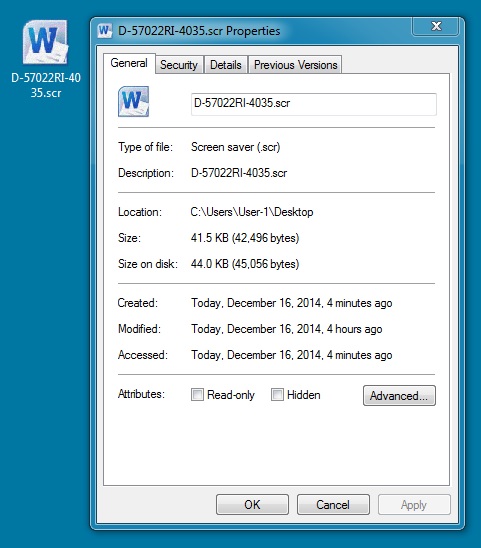
EXTRACTED MALWARE:
File name: D-57022RI-4035.scr
File size: 42,496 bytes
MD5 hash: 74a2e5ead62897387b0eb5da549f881b
Detection ratio: 2 / 53
First submission: 2014-12-16 16:27:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/b5b9e420229272e29edcca73411a7fe93bc2c6c978425ff803d1ed7fe01c3e4e/analysis/
INFECTION TRAFFIC
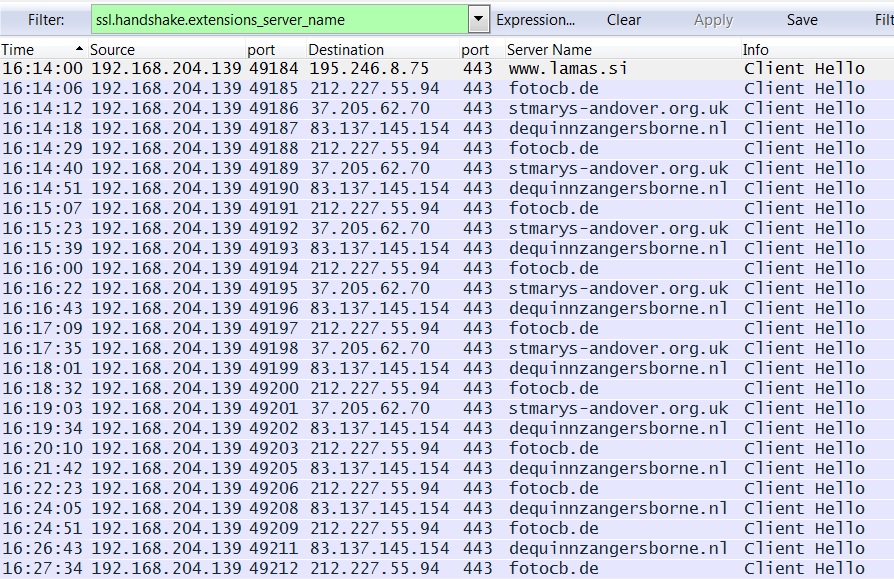
ASSOCIATED DOMAINS:
- 195.246.8[.]75 - www.lamas[.]si
- 212.227.55[.]94 - fotocb[.]de
- 37.205.62[.]70 - stmarys-andover[.]org[.]uk
- 83.137.145[.]154 - dequinnzangersborne[.]nl
EXECUTING THE EXTRACTED MALWARE IN A VM:
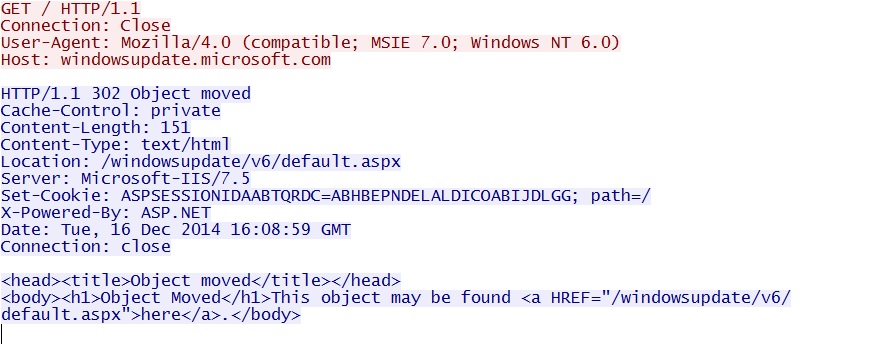
- 2014-12-16 16:08:59 UTC - 65.55.50[.]157:80 - windowsupdate.microsoft[.]com - GET /
- 2014-12-16 16:14:00 UTC - 195.246.8[.]75:443 - www.lamas[.]si - HTTPS traffic
- 2014-12-16 16:14:06 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:14:12 UTC - 37.205.62[.]70:443 - stmarys-andover[.]org[.]uk - HTTPS traffic
- 2014-12-16 16:14:18 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:14:29 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:14:40 UTC - 37.205.62[.]70:443 - stmarys-andover[.]org[.]uk - HTTPS traffic
- 2014-12-16 16:14:51 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:15:07 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:15:23 UTC - 37.205.62[.]70:443 - stmarys-andover[.]org[.]uk - HTTPS traffic
- 2014-12-16 16:15:39 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:16:00 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:16:22 UTC - 37.205.62[.]70:443 - stmarys-andover[.]org[.]uk - HTTPS traffic
- 2014-12-16 16:16:43 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:17:09 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:17:35 UTC - 37.205.62[.]70:443 - stmarys-andover[.]org[.]uk - HTTPS traffic
- 2014-12-16 16:18:01 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:18:32 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:19:03 UTC - 37.205.62[.]70:443 - stmarys-andover[.]org[.]uk - HTTPS traffic
- 2014-12-16 16:19:34 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:20:10 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:21:42 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:22:23 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:24:05 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:24:51 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
- 2014-12-16 16:26:43 UTC - 83.137.145[.]154:443 - dequinnzangersborne[.]nl - HTTPS traffic
- 2014-12-16 16:27:34 UTC - 212.227.55[.]94:443 - fotocb[.]de - HTTPS traffic
SNORT EVENTS
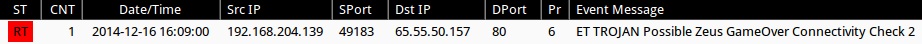
Emerging Threats and ETPRO rulesets from Sguil on Security Onion running Suricata (not including ET INFO or ET POLICY rules):
- 2014-12-16 16:09:00 UTC - 65.55.50[.]157:80 - ET TROJAN Possible Zeus GameOver? Connectivity Check 2 (sid:2019155)
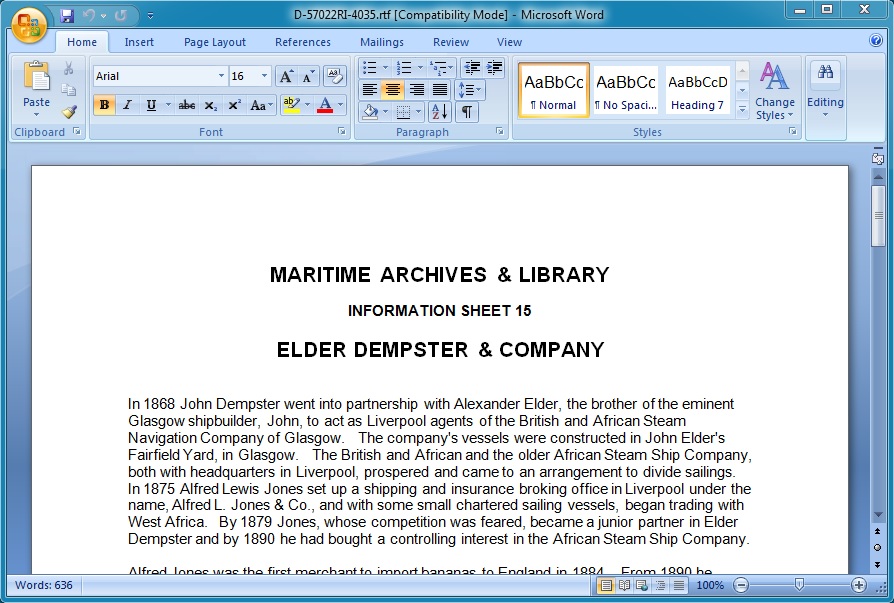
SCREENSHOTS
RTF document that appears when you run the malware:
Connectivity check by the malware:
The HTTPS traffic filtered in Wireshark:
Click here to return to the main page.