2015-01-02 - MALWARE INFECTION FROM ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
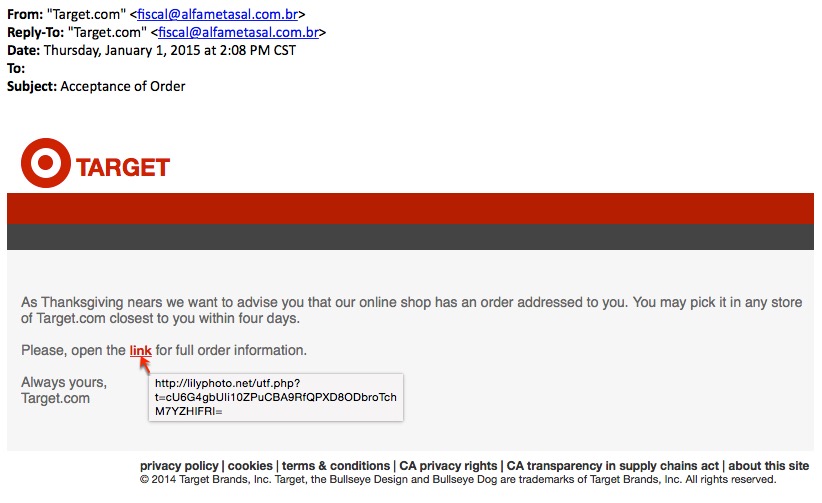
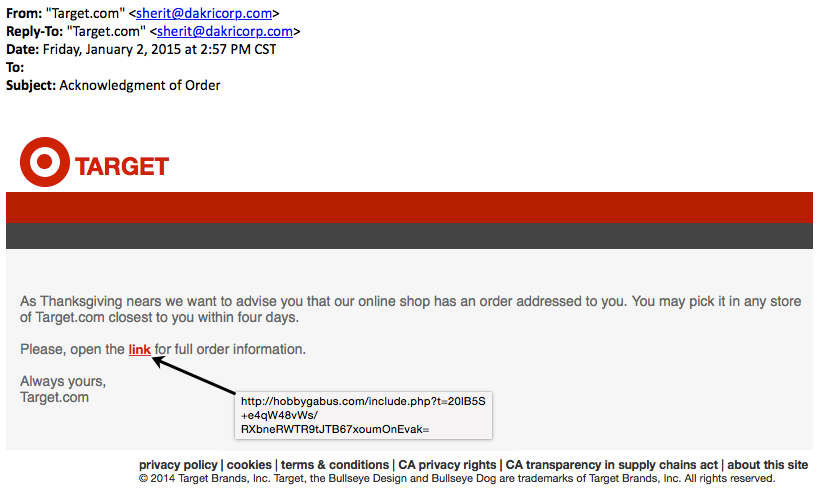
- The Asprox botnet forgot to update its template for Target. These emails start with, "As Thanksgiving nears..."
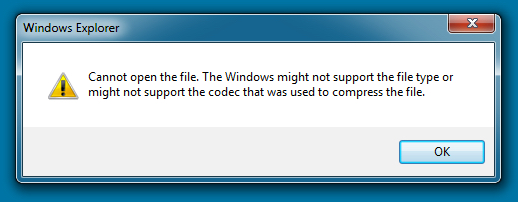
- The malware caused a pop-up stating, "Cannot open the file. The Windows might not support the file type or might not support the codec that was used to compress the file."
- That's a fake message. The malware is still working behind the scenes.
EXAMPLE OF THE EMAILS
SCREENSHOTS:
EXAMPLE OF THE MESSAGE TEXT:
From: "Target[.]com" <sherit@dakricorp[.]com>
Reply-To: "Target[.]com" <sherit@dakricorp[.]com>
Date: Friday, January 2, 2015 at 2:57 PM CST
To:
Subject: Acknowledgment of Order
TARGET
As Thanksgiving nears we want to advise you that our online shop has an order addressed to you. You may pick it in any store of Target[.]com closest to you within four days.
Please, open the link for full order information.
Always yours,
Target.com
privacy policy | cookies | terms & conditions | CA privacy rights | CA transparency in supply chains act | about this site
© 2014 Target Brands, Inc. Target, the Bullseye Design and Bullseye Dog are trademarks of Target Brands, Inc. All rights reserved.
LINKS TO THE MALWARE:
- 88.150.237[.]12 - lilyphoto[.]net - GET /utf.php?t=cU6G4gbUIi10ZPuCBA9RfQPXD8ODbroTchM7YZHIFRI=
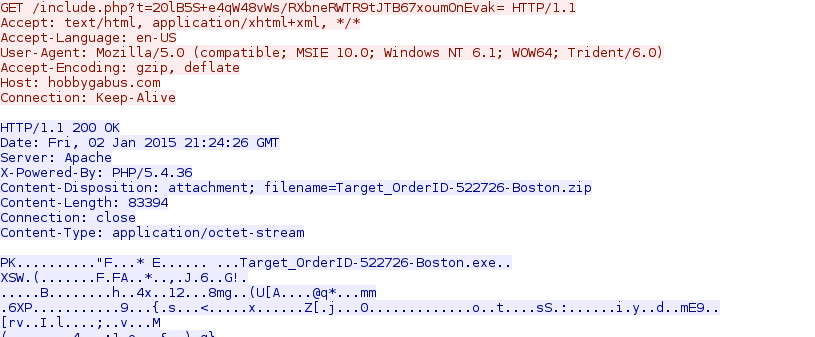
- 66.85.138[.]130 - hobbygabus[.]com - GET /include.php?t=20lB5S+e4qW48vWs/RXbneRWTR9tJTB67xoumOnEvak=
PRELIMINARY MALWARE ANALYSIS
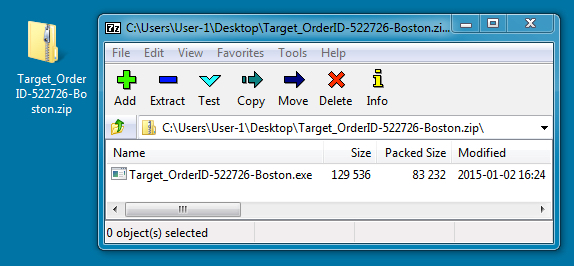
DOWNLOADED ZIP ARCHIVE:
File name: Target_OrderID-522726-Boston.zip
File size: 83,394 bytes
MD5 hash: a1487e707ab530658258c0813272c318
Detection ratio: 9 / 55
First submission: 2015-01-03 00:07:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/1b0fbbead396e2ec21e0703793f46680e6e7e96ce0036aae548ad669d89ec7bd/analysis/
EXTRACTED MALWARE:
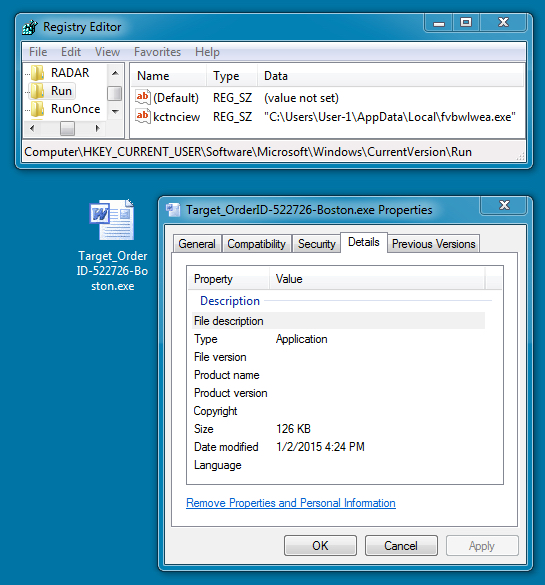
File name: Target_OrderID-522726-Boston.exe
File size: 129,536 bytes
MD5 hash: 1e0396dd06a86baa811937cfc4024c95
Detection ratio: 13 / 56
First submission: 2015-01-02 19:02:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/3ad9df812cb8124357f5bf87cd7eda0c954523fd2b74b4a1fac803e07397dd70/analysis/
INFECTION TRAFFIC
ASSOCIATED DOMAINS:
- 66.85.138[.]130 - hobbygabus[.]com - Compromised website hosting the malware zip file
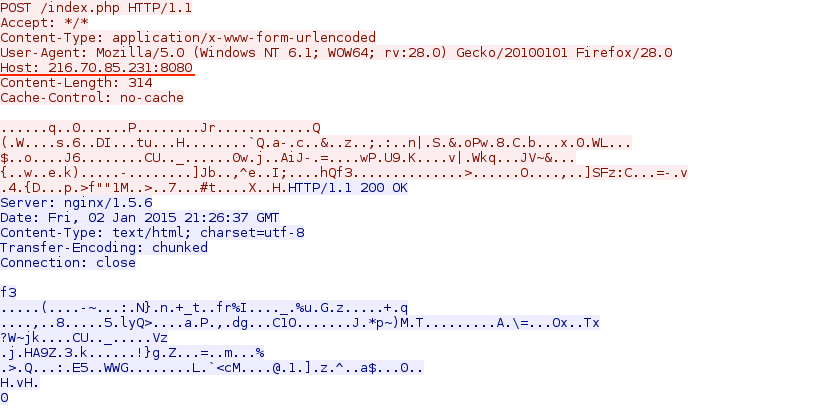
- 216.70.85[.]231 - 216.70.85[.]231 - Post-infection traffic over port 443
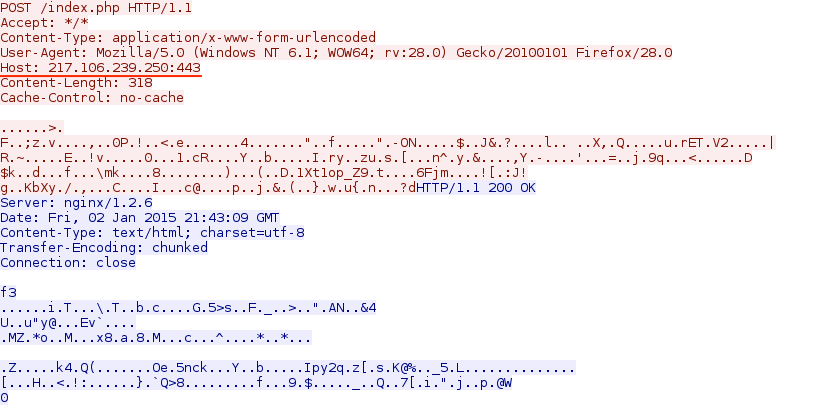
- 217.106.239[.]250 - 217.106.239[.]250 - Post-infection traffic over port 8080
TRAFFIC:
- 2015-01-02 21:24:25 UTC - hobbygabus[.]com - GET /include.php?t=20lB5S+e4qW48vWs/RXbneRWTR9tJTB67xoumOnEvak=
- 2015-01-02 21:25:18 UTC - www.bing[.]com - HTTPS over port 443 as a possible connectivity check
- 2015-01-02 21:26:36 UTC - 216.70.85[.]231:8080 - POST /index.php
- 2015-01-02 21:42:22 UTC - 217.106.239[.]250:443 - POST /index.php
ALERTS FROM SANDBOX ANALYSIS
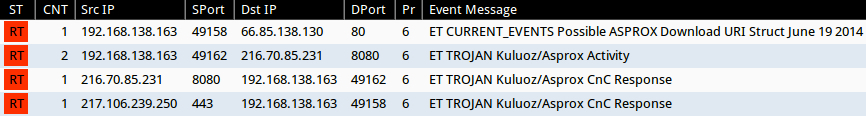
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 66.85.138[.]130:80 - ET CURRENT_EVENTS Possible ASPROX Download URI Struct June 19 2014 (sid:2018589)
- 216.70.85[.]231:8080 - ET TROJAN Kuluoz/Asprox Activity (sid:2017895)
- 216.70.85[.]231:8080 - ET TROJAN Kuluoz/Asprox CnC Response (sid:2019187)
- 217.106.239[.]250:443 - ET TROJAN Kuluoz/Asprox CnC Response (sid:2019187)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Debian 7 (not including preprocessor rules:
- 216.70.85[.]231:8080 - [1:32706:1] MALWARE-CNC Win.Trojan.Kuluoz variant outbound connection
- 217.106.239[.]250:443 - [1:32706:1] MALWARE-CNC Win.Trojan.Kuluoz variant outbound connection
SCREENSHOTS FROM THE TRAFFIC
Downloading the malicious zip file from the email link:
Post-infection traffic after running the extracted malware on a VM:
Click here to return to the main page.