2015-01-07 - DRIDEX ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Yesterday and today, we saw quite a few emails with Word documents and Excel spreadsheet attachments that were pushing Dridex malware.
- Other sources have already reported these emails, so I'm focusing more on the post-infection traffic and alerts.
- I infected two VMs using an example from each day. Lets look at the traffic...
MALWARE
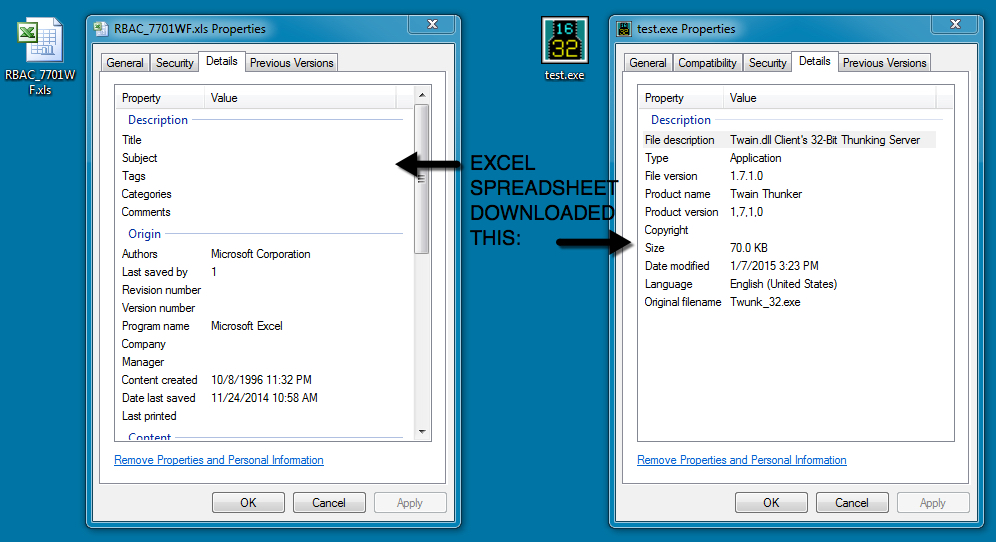
- Attachment name: RBAC_7701WF.xls
- MD5 hash: e3169ab66ecaf99758edbd090e06bb0f
- Malware downloaded by the spreadsheet: test.exe
- MD5 hash: 4bdc0b2c44041dd16e40eebc447d1fe8
TRAFFIC
TRAFFIC FROM AN INFECTION:
- 2015-01-07 15:23:17 UTC - 193.136.19[.]160:8080 - GET /mans/pops.php
- 2015-01-07 15:23:23 UTC - 194.146.136[.]1:8080 - POST /
- 2015-01-07 15:24:42 UTC - 46.4.152[.]122:80 - 46.4.152[.]122 - GET /ofA/CPo8/5msRb/XCLPT/4uJm/jLbWmvzjpuB@L/IOosQ
- 2015-01-07 15:24:44 UTC - 216.170.126[.]185 - GET /PqktR88EoqTvlih$wvxs_jgx+Blpfuu%3D/s@m%3FQp%2DF%3Ds%26M2+xS%24/sA=QgT+7Ep7gRF8
- 2015-01-07 15:24:44 UTC - 216.170.126[.]185 - POST /pnfrfitfh%3D..tqefm/hgkn%2Bm@qf%2B%2D/m%3Dkel@j%7Eheh%7E%2B%3D=%2B~/%3Do.cc%2C
- 2015-01-07 15:24:47 UTC - 216.170.126[.]185 - POST /Ee3r=1rBai5/yhcwMN/u%3DU/b/s3%3DC%3D
- 2015-01-07 15:24:50 UTC - 216.170.126[.]185 - POST /mh5g3181u&y+z%7E%3D2gboiamluu%3D/35v%2Dn/@blpr5vzcuh&$@p%24r/8$%3FmA%3Fg7%3D@h
- 2015-01-07 15:24:55 UTC - 216.170.126[.]185 - POST /R7&k%7E_%26/9&NS%2BR0LK+5GC/X%7Eix&t@
- 2015-01-07 15:24:57 UTC - 216.170.126[.]185 - POST /M9eoH3kEBtkyUQs%3FPcsbJGt%2D.S~C/2Rb2j0=/%3F4l5qMH0iRxL9&~$T%2D_%26V+Wk/oTJ_vu
- 2015-01-07 15:25:02 UTC - 216.170.126[.]185 - POST /q6M%3FYS+N%3Dx@tgPI%7E/%2BgCE%7ET6s/
- 2015-01-07 15:25:04 UTC - 216.170.126[.]185 - POST //////////%3D%26+%3D%7E%2B%3D%24$%2B%2D%24%24+_%2B&/%3F%24=_.=&=%2D%3F&&%7E%3D%24
- 2015-01-07 15:25:10 UTC - 216.170.126[.]185 - POST /He/h/PH+%2CE3JCsF%2D$zv/kc7Zw%24
- 2015-01-07 15:25:12 UTC - 216.170.126[.]185 - POST /Lf2P2YRjF90nBF2z/UmlbtFnbqQNky8FPXZx/Accos.X%24m2S%26%24
- 2015-01-07 15:25:16 UTC - 216.170.126[.]185 - POST /pgg4jHoPsJTy03l/KOuX+mMx2ssi82&/O+=nc
- 2015-01-07 15:25:18 UTC - 216.170.126[.]185 - POST /YGAZuSAsq34/N@SwP$UhxAEnYuQa6RvNk8h/6cCO8&%3DPN3f%2Db/a
- 2015-01-07 15:25:20 UTC - 216.170.126[.]185 - POST /GFAsP/s3p+$/jAxM%2C/n~
- 2015-01-07 15:25:23 UTC - 216.170.126[.]185 - POST /3Sv/IP6/o%3DgH2%24%3FP~xs=A/rG1oPvjwa./q%3D%2C/=w8Q%24
- 2015-01-07 15:25:28 UTC - 82.9.68[.]126 - POST /kikeehhijbi@a/~%24%2Cifel%24c%2B+&a%3F.e%7E%2Dgjicgba%3F%26%3Fi%2C~../h_=~%26%2D
- And so on...
TCP CONNECTIONS ATTEMPTED, BUT RESET BY SERVER:
- 90.30.88[.]105:80
- 129.215.207[.]186:80
- 130.209.116[.]185:80
- 147.213.79[.]114:8000
- 179.43.141[.]164:80
ALERTS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 194.146.136[.]1:8080 - ET TROJAN W32/Dridex POST CnC Beacon (sid:2019891)
- 216.170.126[.]185:80 - ET TROJAN Dridex Post Check-in Activity (sid:2020064)
Sourcefire VRT ruleset from Snort 2.9.7.0 on Debian 7 (not including preprocessor events):
- 193.136.19[.]160:8080 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 194.146.136[.]1:8080 - [1:32678:1] MALWARE-CNC Win.Trojan.Dridex variant outbound connection attempt
Click here to return to the main page.
