2015-01-15 - GUEST BLOG POST BY JACK MOTT - ANOTHER UPATRE/DYRE PHISHING WAVE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-15-Upatre-Dyre-traffic-example.pcap.zip 435.7 kB (435,655 bytes)
- 2015-01-15-zip-file-from-web-link.zip 11.1 kB (11,085 bytes)
- 2015-01-15-Upatre-Dyer-phishing-email-sender-info.csv.zip 1.8 kB (1,843 bytes)
NOTES:
- Information for this blog post was submitted by Jack Mott.
- Jack Mott is an information security analyst in based in Denver, Colorado (United States).
PHISHING EMAIL INFORMATION
OVERVIEW:
- Observed wave: Thursday, 2015-01-15 from 14:29:58 to 16:00:52 UTC
- Senders noted: bankline.administrator@nutwest[.]com
- Example of the subject lines: Payment Advice - Advice Ref:[GB128669] / CHAPS credits
EXAMPLE OF THE MESSAGE:
Sir/Madam,
Please download document from dropbox, payment advice is issued at the request of our customer. The advice is for your reference only.
Download link:
hxxp[:]//[www.example.domain]/NATWEST_RELEASES/bankline.html
Yours faithfully,
Global Payments and Cash Management
HSBC
***************************************************************************
This is an auto-generated email, please DO NOT REPLY. Any replies to this email will be disregarded.
***************************************************************************
Security tips
1. Install virus detection software and personal firewall on your computer. This software needs to be updated regularly to ensure you have the latest protection.
2. To prevent viruses or other unwanted problems, do not open attachments from unknown or non-trustworthy sources.
3. If you discover any unusual activity, please contact the remitter of this payment as soon as possible.
*******************************************************************
This e-mail is confidential. It may also be legally privileged. If you are not the addressee you may not copy, forward, disclose or use any part of it. If you have received this message in error, please delete it and all copies from your system and notify the sender immediately by return e-mail.
Internet communications cannot be guaranteed to be timely, secure, error or virus-free. The sender does not accept liability for any errors or omissions.
*******************************************************************
"SAVE PAPER - THINK BEFORE YOU PRINT!"
TRAFFIC CHARACTERISTICS
LINKS FROM THE EMAILS:
- 62.149.177[.]11 - waveonnord[.]com - GET /NATWEST_RELEASES/bankline.html
- 64.29.151[.]221 - aeiou2[.]com - GET /NATWEST_RELEASES/bankline.html
- 64.29.151[.]221 - art4yogis[.]com - GET /NATWEST_RELEASES/bankline.html
- 64.29.151[.]221 - callproc[.]com - GET /NATWEST_RELEASES/bankline.html
- 66.175.58[.]9 - alastaya[.]com - GET /NATWEST_RELEASES/bankline.html
- 67.55.33[.]115 - runtheville[.]com - GET /NATWEST_RELEASES/bankline.html
- 69.49.96[.]23 - avralab[.]com - GET /NATWEST_RELEASES/bankline.html
- 69.49.101[.]57 - communityconnectionsinc[.]com - GET /NATWEST_RELEASES/bankline.html
- 69.49.101[.]57 - brianpekarchuk[.]com - GET /NATWEST_RELEASES/bankline.html
- 81.88.57[.]68 - ruedubox[.]fr - GET /NATWEST_RELEASES/bankline.html
- 88.86.113[.]152 - s-net[.]wz[.]cz - GET /NATWEST_RELEASES/bankline.html
- 98.129.229[.]71 - chcoa[.]com - GET /NATWEST_RELEASES/bankline.html
- 202.142.212[.]15 - wss[.]ac[.]th - GET /NATWEST_RELEASES/bankline.html
- 216.251.43[.]17 - rlmenterprisesinc[.]com - GET /NATWEST_RELEASES/bankline.html
SOME TRAFFIC GENERATED BY THESE LINKS:
- 69.89.27[.]218 - y-design.promagnumcorp[.]com - GET /js/jquery-1.39.15.js?get_message=[random numbers]
- 86.35.15[.]212 - tls[.]ro - GET /js/jquery-1.39.15.js?get_message=[random numbers]
- 86.35.15[.]215 - moda-arad[.]ro - GET /js/jquery-1.39.15.js?get_message=[random numbers]
- 216.251.43[.]11 - beyondprintfinishing[.]com - GET /js/jquery-1.39.15.js?get_message=[random numbers]
FIDDLER INFO
EXAMPLE OF THE TRAFFIC SEEN:
MALWARE INFO
DOWNLOADED ZIP FILE:
File name: doc172_pdf.zip
MD5 hash: b4157a9f819a9aeb401a4b7784f7916e
VT: 25/57 - https://www.virustotal.com/en/file/b3a5fdcca34a55c4b7e0010e1202ae56c38137ac96e4dddf9f31f103859187bb/analysis/
EXTRACTED MALWARE:
File name: doc255_pdf.exe
MD5 hash: b4157a9f819a9aeb401a4b7784f7916e
VT: 25/57 - https://www.virustotal.com/en/file/8cd4a12cf21a4e1f9bf2da069be51b52c777328ae6ed87ce29b495412773cd72/analysis/
NOTES:
- Different file hashes were noted during the 2015-01-15 phishing wave.
- This matches traffic seen in previous Upatre/Dyre phishing waves.
- Only one example is included here.
ADDITIONAL INFO
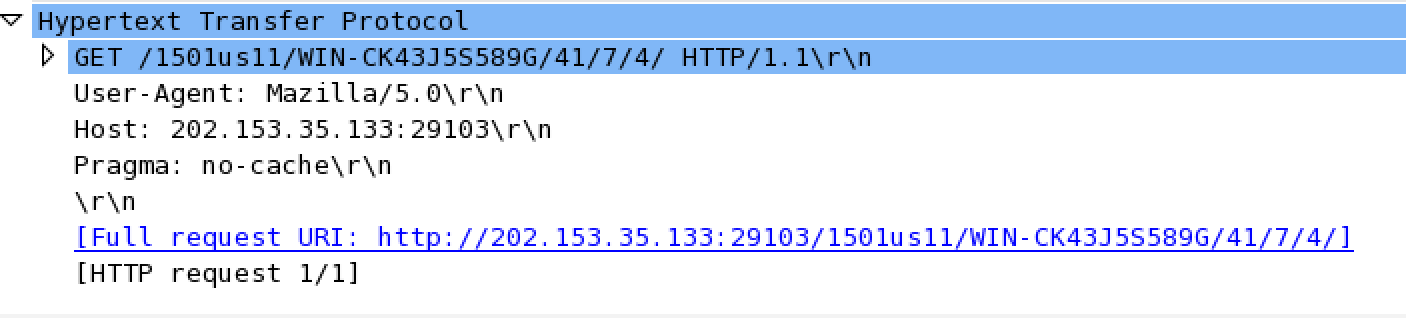
EXAMPLE OF AN HTTP GET REQUEST GENERATED BY THE UPATRE DOWNLOADER:
Click here to return to the main page.