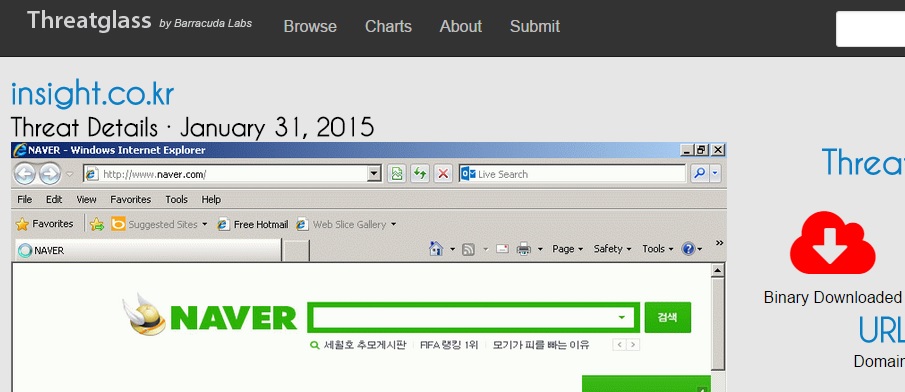
2015-01-31 KAIXIN EK FROM 103.251.38[.]20:802 - EK PAYLOAD FROM 210.109.101[.]13 - WWW.MYRSVP[.]CO[.]KR
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-01-31-KaiXin-EK-traffic.pcap.zip 1.3 MB (1,323,535 bytes)
- 2015-01-31-KaiXin-EK-traffic.pcap (1,728,572 bytes)
- 2015-01-31-KaiXin-EK-malware.zip 349.1 kB (349,086 bytes)
- dou.exe (355,840 bytes)
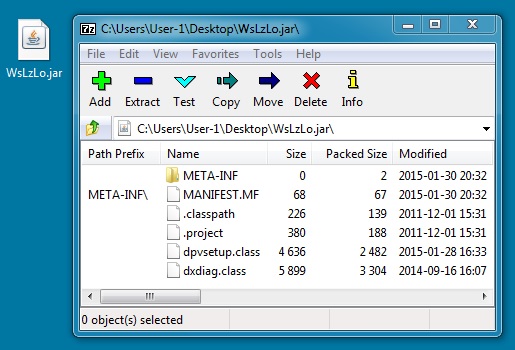
- WsLzLo.jar (6,910 bytes)
NOTES:
- For some reason, I wasn't getting any EK-specific alerts, but the traffic patterns are KaiXin EK as noted in my previous blog entry for KaiXin on 2015-01-03.
- I retrieved a pcap of the KaiXin EK traffic from a Threatglass entry here.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 58.229.185[.]164 port 80 - insight[.]co[.]kr - Comrpomised website
- 211.40.118[.]130 port 80 - ganseokmaru[.]co[.]kr - Redirect/gate leading to KaiXin EK
- 103.251.38[.]24 port 802 - 103.251.38[.]24:802 - KaiXin EK
- 103.251.38[.]20 port 802 - 103.251.38[.]20:802 - another IP sending KaiXin EK traffic
- 210.109.101[.]13 port 80 - www.myrsvp[.]co[.]kr - KaiXin EK malware payload
- 23.61.194[.]216 port 80 - r.qzone.qq[.]com - Win32/Spy.Agent.OLF Retrieving CnC IP
- 218.188.204[.]16 port 80 - 218.188.204[.]16 - Trojan/W32.KRBanker.60928.C Checkin
COMPROMISED WEBSITE AND CHAIN OF EVENTS TO THE EXPLOIT KIT (EK):
- 2015-01-31 19:51:48 UTC - 58.229.185[.]164:80 - insight[.]co[.]kr - GET /
- 2015-01-31 19:51:49 UTC - 58.229.185[.]164:80 - insight[.]co[.]kr - GET /js/common.js
- 2015-01-31 19:51:50 UTC - 211.40.118[.]130:80 - ganseokmaru[.]co[.]kr - GET /bob/1.js
- 2015-01-31 19:51:50 UTC - 211.40.118[.]130:80 - ganseokmaru[.]co[.]kr - GET /bob/1.html
KAIXIN EK:
- 2015-01-31 19:51:51 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /index.html
- 2015-01-31 19:51:51 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /swfobject.js
- 2015-01-31 19:51:51 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /jquery-1.4.2.min.js
- 2015-01-31 19:51:52 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /main.html
- 2015-01-31 19:51:54 UTC - 103.251.38[.]20:802 - 103.251.38[.]20:802 - GET /2.html
- 2015-01-31 19:51:56 UTC - 210.109.101[.]13:80 - www.myrsvp[.]co[.]kr - GET /dou.exe
- 2015-01-31 19:52:01 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /WsLzLo.jar
- 2015-01-31 19:52:02 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /dpvsetup.class
- 2015-01-31 19:52:02 UTC - 103.251.38[.]24:802 - 103.251.38[.]24:802 - GET /dpvsetup/class.class
POST-INFECTION TRAFFIC:
- 2015-01-31 19:52:02 UTC - 23.61.194[.]216:80 - r.qzone.qq[.]com - GET /cgi-bin/user/cgi_personal_card?uin=2903262151?=24745
- 2015-01-31 19:52:04 UTC - 218.188.204[.]16:80 - 218.188.204[.]16 - GET /ip.php?=31377
- 2015-01-31 19:52:07 UTC - 218.188.204[.]16:80 - 218.188.204[.]16 - POST /upload.php
- 2015-01-31 19:52:11 UTC - 218.188.204[.]16:80 - www.naver[.]com - GET /
ALERTS
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion:
- ET DNS DNS Query for Suspicious .co.kr Domain (sid:2011411)
- 58.229.185[.]164 port 80 - ET WEB_CLIENT Hex Obfuscation of Script Tag % Encoding (sid:2012263)
- 103.251.38[.]24 port 802 - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 103.251.38[.]24 port 802 - ET CURRENT_EVENTS Possible Internet Explorer CVE-2014-6332 Common Construct (Reversed) (sid:2019806)
- 103.251.38[.]24 port 802 - ET EXPLOIT Possible Internet Explorer VBscript failure to handle error case information disclosure CVE-2014-6332 Common Function Name (sid:2019733)
- 103.251.38[.]24 port 802 - ET WEB_CLIENT Possible Internet Explorer VBscript CVE-2014-6332 multiple redim preserve (sid:2019842)
- 210.109.101[.]13 port 80 - ET POLICY exe download via HTTP - Informational (sid:2003595)
- 210.109.101[.]13 port 80 - ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile (sid:2019714)
- 210.109.101[.]13 port 80 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- 210.109.101[.]13 port 80 - ET POLICY Binary Download Smaller than 1 MB Likely Hostile (sid:2007671)
- 210.109.101[.]13 port 80 - ET TROJAN UPX compressed file download possible malware (sid:2001046)
- 103.251.38[.]24 port 802 - ET POLICY Vulnerable Java Version 1.6.x Detected (sid:2011582)
- 103.251.38[.]24 port 802 - ET CURRENT_EVENTS Likely SweetOrange EK Java Exploit Struct (JAR) (sid:2019542)
- 103.251.38[.]24 port 802 - ET INFO JAVA - Java Archive Download By Vulnerable Client (sid:2014473)
- 218.188.204[.]16 port 80 - ET TROJAN Trojan/W32.KRBanker.60928.C Checkin (sid:2019828)
- 23.61.194[.]216 port 80 - ETPRO TROJAN Win32/Spy.Agent.OLF Retrieving CnC IP (sid:2809239)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 58.229.185[.]164 port 80 - [1:21039:4] INDICATOR-OBFUSCATION potential javascript unescape obfuscation attempt detected
- 58.229.185[.]164 port 80 - [1:19887:3] INDICATOR-OBFUSCATION potential javascript unescape obfuscation attempt detected
- 210.109.101[.]13 port 80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 210.109.101[.]13 port 80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 210.109.101[.]13 port 80 - [1:16435:14] FILE-IDENTIFY Ultimate Packer for Executables/UPX v0.62-v1.22 packed file magic detected
- 103.251.38[.]24 port 802 - [1:32639:1] EXPLOIT-KIT Sweet Orange exploit kit jar file requested on defined port
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD:
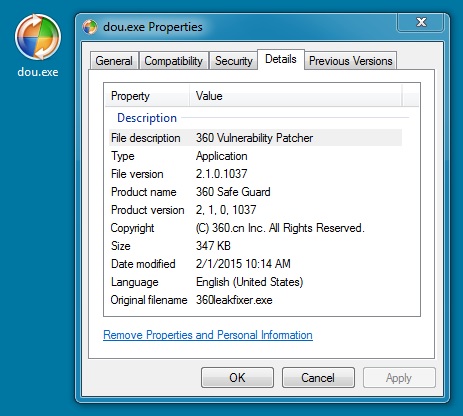
File name: dou.exe
File size: 355,840 bytes
MD5 hash: 8421f430cafac253263b3d1d93e0a3f3
Detection ratio: 23 / 57
First submission to VirusTotal: 2015-01-31 11:09:10 UTC
JAVA EXPLOIT (SENT AFTER MALWARE PAYLOAD):
File name: WsLzLo.jar
File size: 6,910 bytes
MD5 hash: bf4705cedd537bfb2a81eb397df3dbe4
Detection ratio: 12 / 57
First submission to VirusTotal: 2015-02-01 03:19:06 UTC
Click here to return to the main page.