2015-02-01 - NUCLEAR EK FROM 178.62.250[.]102 - DISCREETTARGET[.]CF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 178.62.250[.]102 port 80 - discreettarget[.]cf - Nuclear EK
- 85.253.184[.]24 port 80 - 85.253.184[.]24 - Post-infection HTTP traffic
- 109.87.114[.]202 port 80 - Post-infection TCP traffic with encrypted data
- 37.57.30[.]35 port 80 - mydear[.]name - Post-infection HTTP traffic
- 88.198.20[.]41 port 18009 - Post-infection TCP traffic with encrypted data
- 46.165.229[.]125 port 80 - 46.165.229[.]125 - Post-infection HTTP traffic
- 190.93.245.30 port 80 - www.movieroomreviews[.]com - Start of click-fraud traffic
NUCLEAR EK:
- 2015-02-01 19:13:58 UTC - discreettarget[.]cf - GET /XgoDUEVXUUhS.html
- 2015-02-01 19:14:00 UTC - discreettarget[.]cf - GET /XUpHGF9dVwAZUFZEBUtVDVdRDFRVXQACS1EXU1EaV0xVAQdLAlVX
- 2015-02-01 19:14:01 UTC - discreettarget[.]cf - GET /XltbAUUDWwBRHlYKTgAYCFFRBl1TUwEKBxgMS1UGS1BKCQsCGAwZE1AdBTA
- 2015-02-01 19:14:02 UTC - discreettarget[.]cf - GET /XltbAUUDWwBRHlYKTgAYCFFRBl1TUwEKBxgMS1UGS1BKCQsCGAwZNVAmDBdEAA
- 2015-02-01 19:14:21 UTC - discreettarget[.]cf - GET /XUpHGF9dVwAZUFZEBUtVDVdRDFRVXQACS1EXU1EaV0xVAQdLF1AJFVEX
- 2015-02-01 19:14:22 UTC - discreettarget[.]cf - GET /XltbAUUDWwBRHlYKTgAYCFFRBl1TUwEKBxgMS1UGS1BKCQsCGA4ZE1AdBTA
- 2015-02-01 19:14:24 UTC - discreettarget[.]cf - GET /XltbAUUDWwBRHlYKTgAYCFFRBl1TUwEKBxgMS1UGS1BKCQsCGA4ZNVAmDBdEAA
- 2015-02-01 19:14:40 UTC - discreettarget[.]cf - GET /XltbAUUDWwBRHlYKTgAYCFFRBl1TUwEKBxgMS1UGS1BKCQsCGAEZE1AdBTA
- 2015-02-01 19:14:41 UTC - discreettarget[.]cf - GET /XltbAUUDWwBRHlYKTgAYCFFRBl1TUwEKBxgMS1UGS1BKCQsCGAEZNVAmDBdEAA
POST-INFECTION TRAFFIC:
- 2015-02-01 19:14:25 UTC - 109.87.114[.]202 port 80 - encrypted TCP traffic
- 2015-02-01 19:14:27 UTC - 85.253.184[.]24 - GET /online.htm
- 2015-02-01 19:14:28 UTC - 85.253.184[.]24 - GET /home.htm
- 2015-02-01 19:14:48 UTC - mydear[.]name - GET /page_umax.php
- 2015-02-01 19:14:54 UTC - 88.198.20[.]41 - encrypted TCP traffic on port 18009
- 2015-02-01 19:15:52 UTC - mydear[.]name - GET /page_umax.php
- 2015-02-01 19:16:05 UTC - 46.165.229[.]125 - GET /x/4wo5u8re22/dd41da8be9a9a06247e449b14996b686/AA/2
- 2015-02-01 19:16:06 UTC - www.movieroomreviews[.]com - GET /star-wars-episode-vii/jj-abrams-wanted-michael-arndt-star-wars-151155?utm_source=
28453&utm_medium=cpc&utm_campaign=clickpayz_28453 - [Click-fraud traffic starting with the above line continues for the rest of the pcap.]
ALERTS
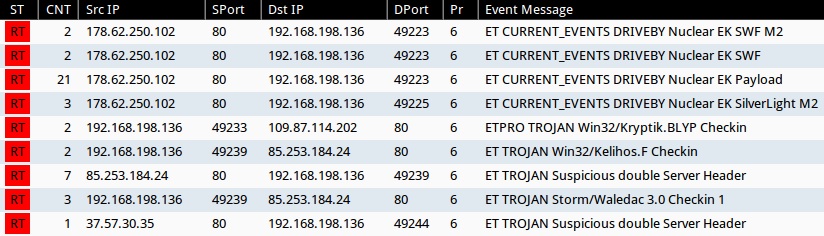
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 178.62.250[.]102 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 178.62.250[.]102 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020311)
- 178.62.250[.]102 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 178.62.250[.]102 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SilverLight M2 (sid:2020317)
- 109.87.114[.]202 port 80 - ETPRO TROJAN Win32/Kryptik.BLYP Checkin (sid:2807093)
- 85.253.184[.]24 port 80 - ET TROJAN Win32/Kelihos.F Checkin (sid:2017191)
- 85.253.184[.]24 port 80 - ET TROJAN Suspicious double Server Header (sid:2012707)
- 85.253.184[.]24 port 80 - ET TROJAN Storm/Waledac 3.0 Checkin 1 (sid:2012137)
- 37.57.30[.]35 port 80 - ET TROJAN Suspicious double Server Header (sid:2012707)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 178.62.250[.]102 port 80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
- 85.253.184[.]24 port 80 - [1:27775:4] MALWARE-CNC Win.Trojan.Fareit variant outbound connection
- 85.253.184[.]24 port 80 - [1:28554:1] MALWARE-CNC Win.Trojan.Fareit variant outbound connection - /online.htm GET Encrypted Payload
- 85.253.184[.]24 port 80 - [1:26369:1] MALWARE-OTHER Double HTTP Server declared
- 37.57.30[.]35 port 80 - [1:26369:1] MALWARE-OTHER Double HTTP Server declared
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-02-01-Nuclear-EK-flash-exploit.swf
File size: 10,392 bytes
MD5 hash: 43ad5d1fb45567e44f463fe575888802
Detection ratio: 3 / 56
First submission: 2015-02-01 10:16:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/9c6c10291c98c2d2f196f17d2d4c1eb1dbfea992f978f15cd5429170609ba1a8/analysis/
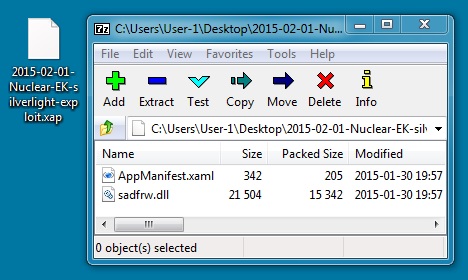
SILVERLIGHT EXPLOIT:
File name: 2015-02-01-Nuclear-EK-silverlight-exploit.xap
File size: 15,773 bytes
MD5 hash: ef1717e7fab3535b7d4bf5c7c38feb0f
Detection ratio: 1 / 57
First submission: 2015-02-01 20:39:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/c801e583ab71123f37bd22823df48a439465d767a3d3d8e9c90783be752bec98/analysis/
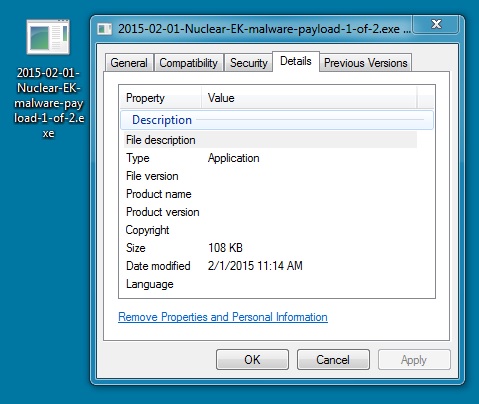
MALWARE PAYLOAD (1 OF 2):
File name: 2015-02-01-Nuclear-EK-malware-payload-1-of-2.exe
File size: 110,592 bytes
MD5 hash: 469e7a715c0c396cd9e3b3a4f19e4cc7
Detection ratio: 6 / 48
First submission: 2015-02-01 20:39:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/344258bf73648da7032e6106554d8a4e00d3737f39e0305f42c80639d3f3e116/analysis/
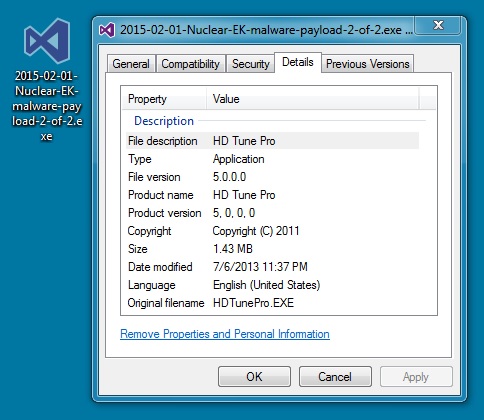
MALWARE PAYLOAD (2 OF 2):
File name: 2015-02-01-Nuclear-EK-malware-payload-2-of-2.exe
File size: 1,508,864 bytes
MD5 hash: 1d98adfa91d76de07415876f400f53fe
Detection ratio: 17 / 57
First submission: 2015-02-01 20:40:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/b3e6340265e861ea26e8ed44d9c8a98e890816283708a8e39eff28a7bd482ab3/analysis/
Click here to return to the main page.