2015-02-08 - TRAFFIC ANALYSIS EXERCISE: INFORMATION FROM ANOTHER ANALYST
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
PCAP AND MORE:
- 2015-02-08-traffic-analysis-exercise.pcap.zip 1.9 MB (1,937,094 bytes)
- 2015-02-08-traffic-analysis-exercise-email-the-user-received.eml.zip 13.3 kB (13,279 bytes)
FIRST DECISION POINT - YOU LOOK AT ADDITIONAL INFORMATION FROM ANOTHER ANALYST
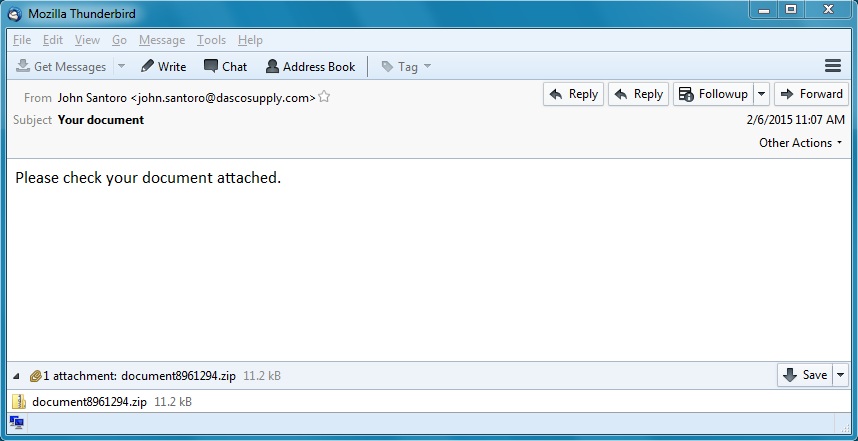
One of the other analysts found the following email from the Exchange server logs. The logs show this email was sent to Mike.
See the link above for a zip file containing the additional info. It's a zip archive containing an .eml copy of the email sent to Mike.
You can view the email using Thunderbird, which you've already installed on your computer. Other analysts say they can view it using their Mac mail client, but the budget was tight this year, and they did not issue you a Macbook. Fortunately, your 5 year-old Dell OptiPlex running Slackware Linux is up to the task. You open the email, get the zip file, and extract the malware.
A phone call to Mike confirms he read this email, opened the zip file, and double-clicked on the malware.
SECOND DECISION POINT
1) You've confirmed the activity. The SOC follows established procedures to handle the incident, and you finish your report. Case closed! You're back on the hunt, reviewing more IDS events for the rest of your 12-hour shift. (Only 10 hours left now. But who's counting?)
- click here to see if your report is accurate.
2) The Help Desk re-imaged Mike's computer, but someone did a forensic image of the infected hard drive first. The image has additional malware related to the incident.
- click here to complete your report with information on the additional malware.
Click here to return to the main page.