2015-02-08 - TRAFFIC ANALYSIS EXERCISE: FINAL ROUND
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
PCAP AND MORE:
- 2015-02-08-traffic-analysis-exercise.pcap.zip 1.9 MB (1,937,094 bytes)
- 2015-02-08-traffic-analysis-exercise-email-the-user-received.eml.zip 13.3 kB (13,279 bytes)
- 2015-02-08-traffic-analysis-exercise-all-the-malware.zip 353.2 kB (353,227 bytes)
FINAL DECISION - YOU GET ALL THE INFORMATION BEFORE FINISHING THE REPORT
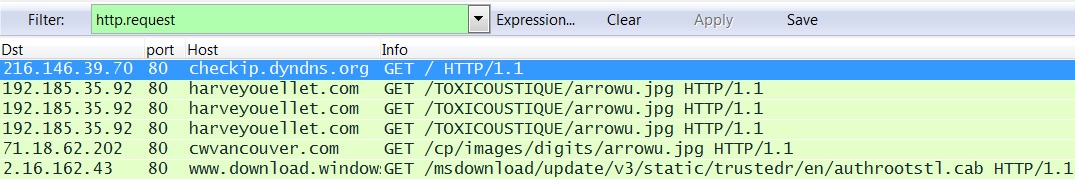
First things first. You already looked at the pcap in wireshark. Hopefully, you've set it up as I've described in my tutorial here. Use http.request for the filter and see what we've got:
A Google search on the domain names will indicate what's going on. You'll find a submission to malwr.com that shows the same network traffic (under the "Network Analysis" section). You'll also find a blog entry on TechHelpList.com discussing the same URLs from the pcap.
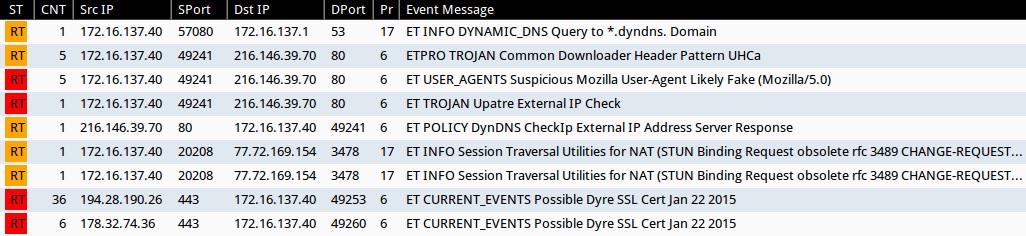
With that information, you might not need the EmergingThreats events generated by running the pcap through Snort or Security Onion:
INITIAL ASSESSMENT
An incident report of the activity should also include a technical details section after the short summary. It would have all URLs, domains, IP addresses, and other malicious traffic associated with the incident.
THE MALICIOUS EMAIL
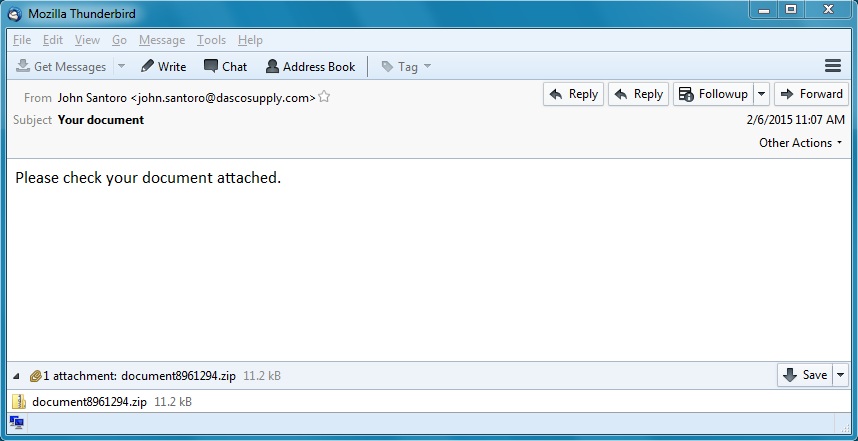
Here's the malicious email:
Shown above: Screenshot of the malicious email.
Here's the malware from the email:
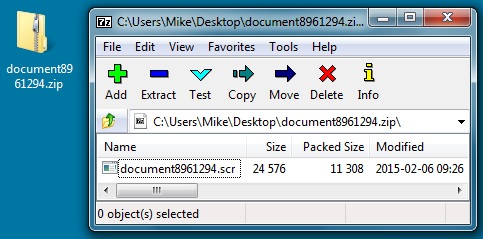
Shown above: The email attachment (a zip file).
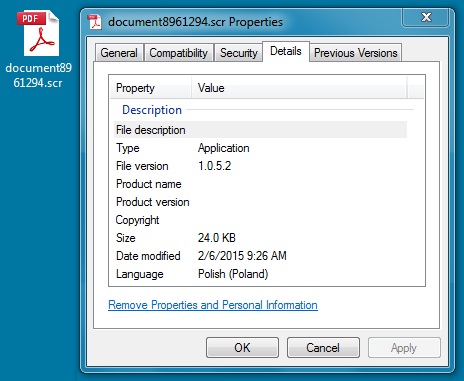
Shown above: Extracted malware from the zip file.
You look up the information on VirusTotal and Malwr[.]com:
- VirusTotal report on the malicious zip file: link
- VirusTotal report on the extracted malware: link
- Malwr.com report on the extracted malware: link
MALWARE FOUND ON THE INFECTED HOST
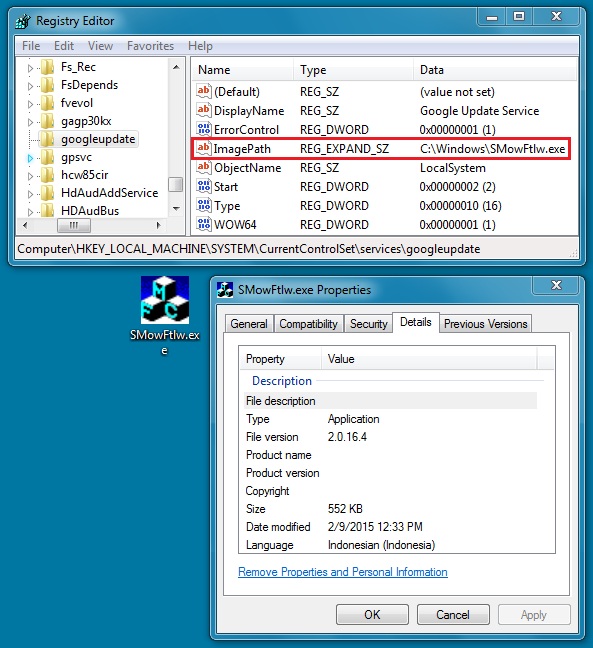
Here's the Dyreza file taken from the forensic image of Mike's infected computer:
You now have a file hash of the Dyreza malware, and you can finish your report with this additional info.
Double-check your work to make sure it includes the correct file hashes from the associated malware. The image on this page for the Dyreza sample shows the associated registry key, which is something you could also include in the report.
FINAL WORDS
This should cover most of the information an analyst might find from a traffic analysis or incident response perspective. In most cases, these types of malicious emails are blocked by your organization's spam filters. Unfortunately, users can (and sometimes do) infect their computers with the same type of emails through personal webmail accounts.
From an incident response perspective, you can finish the report based on the traffic alone (and possibly a phone call to Mike). Finishing the report at the first decision point is not necessarily bad, especially if you have other events to investigate. You you might miss another infection if you spend too much time on any one particular incident.
Thanks for going through this exercise. Hopefully, it provided some insight on these sort of infections.
Click here to return to the main page.