2015-02-13 - MAGNITUDE EK FROM 46.166.182[.]101
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 46.166.182[.]101 - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - Magnitude EK
MAGNITUDE EK:
- 2015-02-13 00:49:12 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /?2654434052544748554a47524308414949414a430845494b
- 2015-02-13 00:49:22 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /d8b7bd0646ae4b7344ff9e7df3b77f36
- 2015-02-13 00:49:22 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /1db70f31658d04615bd2ac4751bf6c54
- 2015-02-13 00:49:25 UTC - 46.166.182[.]101 - GET /?8a4e1cdfb85545ab7dc0296ada31c189
- 2015-02-13 00:49:26 UTC - 46.166.182[.]101 - GET /?aba053bd1f478e9f58ba3a41492dca6c
- 2015-02-13 00:49:27 UTC - 46.166.182[.]101 - GET /?9755bf8937a08ea1691cfb1d06e68693
- 2015-02-13 00:49:59 UTC - 46.166.182[.]101 - GET /?70c3af605f00b077c895dd9ff6756aad
- 2015-02-13 00:50:02 UTC - 46.166.182[.]101 - GET /?3044f2605deec94ba1c60eaaaba728a9
- 2015-02-13 00:50:03 UTC - 46.166.182[.]101 - GET /?81f7cef08a0a5570e7f43f44c2c66ddc
- 2015-02-13 00:50:03 UTC - 46.166.182[.]101 - GET /?18da21ef5ad8840bbb2800f21f66e235
- 2015-02-13 00:50:25 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /?2654434052544748554a47524308414949414a430845494b
- 2015-02-13 00:50:29 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /d8b7bd0646ae4b7344ff9e7df3b77f36
- 2015-02-13 00:50:29 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /1db70f31658d04615bd2ac4751bf6c54
- 2015-02-13 00:51:10 UTC - 49.2a716.d1.19.3a59.86.e67ab.b0a6.375be0.qq151et969.buildscontrols[.]in - GET /1db70f31658d04615bd2ac4751bf6c54
- 2015-02-13 00:51:13 UTC - 46.166.182[.]101 - GET /?8a4e1cdfb85545ab7dc0296ada31c189
- 2015-02-13 00:51:15 UTC - 46.166.182[.]101 - GET /?aba053bd1f478e9f58ba3a41492dca6c
- 2015-02-13 00:51:19 UTC - 46.166.182[.]101 - GET /?9755bf8937a08ea1691cfb1d06e68693
- 2015-02-13 00:51:23 UTC - 46.166.182[.]101 - GET /?70c3af605f00b077c895dd9ff6756aad
- 2015-02-13 00:51:23 UTC - 46.166.182[.]101 - GET /?3044f2605deec94ba1c60eaaaba728a9
- 2015-02-13 00:51:24 UTC - 46.166.182[.]101 - GET /?81f7cef08a0a5570e7f43f44c2c66ddc
- 2015-02-13 00:51:24 UTC - 46.166.182[.]101 - GET /?18da21ef5ad8840bbb2800f21f66e235
POST-INFECTION TRAFFIC:
- See the preliminary malware analysis for the post-infection traffic.
ALERTS
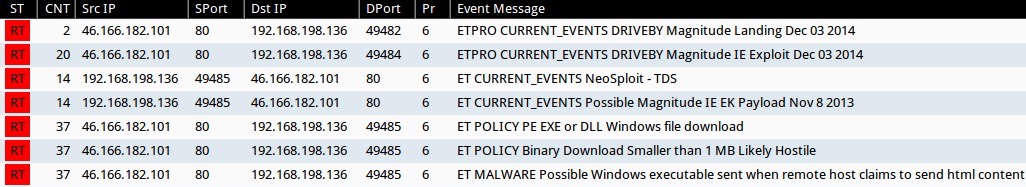
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 46.166.182[.]101 port 80 - ETPRO CURRENT_EVENTS DRIVEBY Magnitude Landing Dec 03 2014 (sid:2809273)
- 46.166.182[.]101 port 80 - ETPRO CURRENT_EVENTS DRIVEBY Magnitude IE Exploit Dec 03 2014 (sid:2809275)
- 46.166.182[.]101 port 80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 46.166.182[.]101 port 80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 46.166.182[.]101 port 80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 46.166.182[.]101 port 80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request (x14)
- 46.166.182[.]101 port 80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt (x8)
- 46.166.182[.]101 port 80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x4)
- 46.166.182[.]101 port 80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x4)
- 46.166.182[.]101 port 80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x8)
- 46.166.182[.]101 port 80 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-02-13-Magnitude-EK-flash-exploit.swf
File size: 19658 bytes
MD5 hash: c7dce4408ce25a91971bf2c76a30c7b3
Detection ratio: 2 / 56
First submission: 2015-02-13 19:42:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/4602e734035ab8ed5d2e5e3f33d3039b263585ddec54e75eb17bbfef588f3064/analysis/
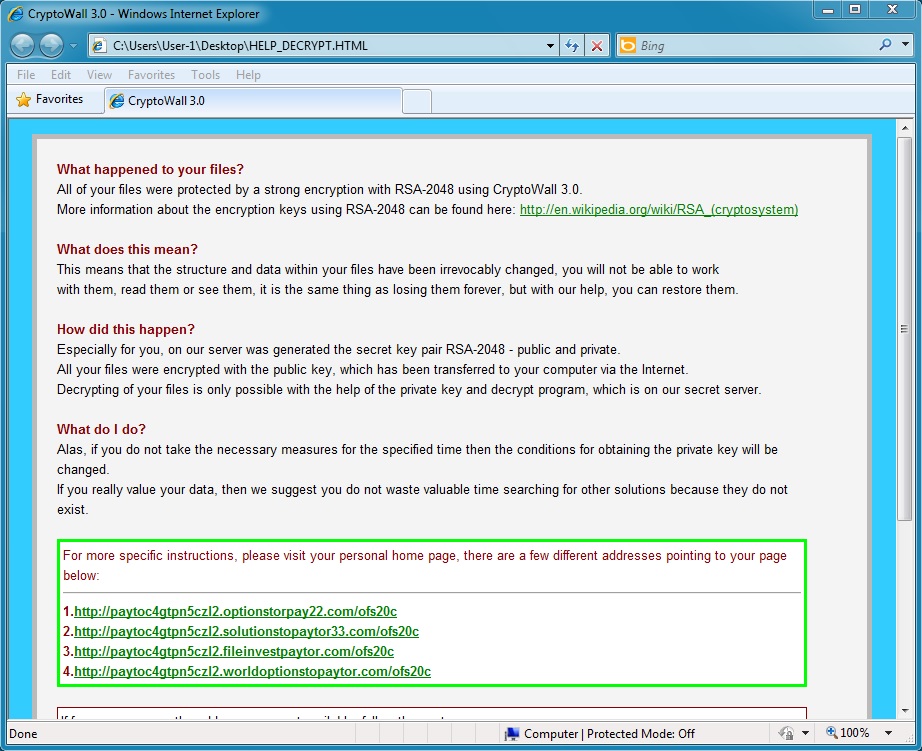
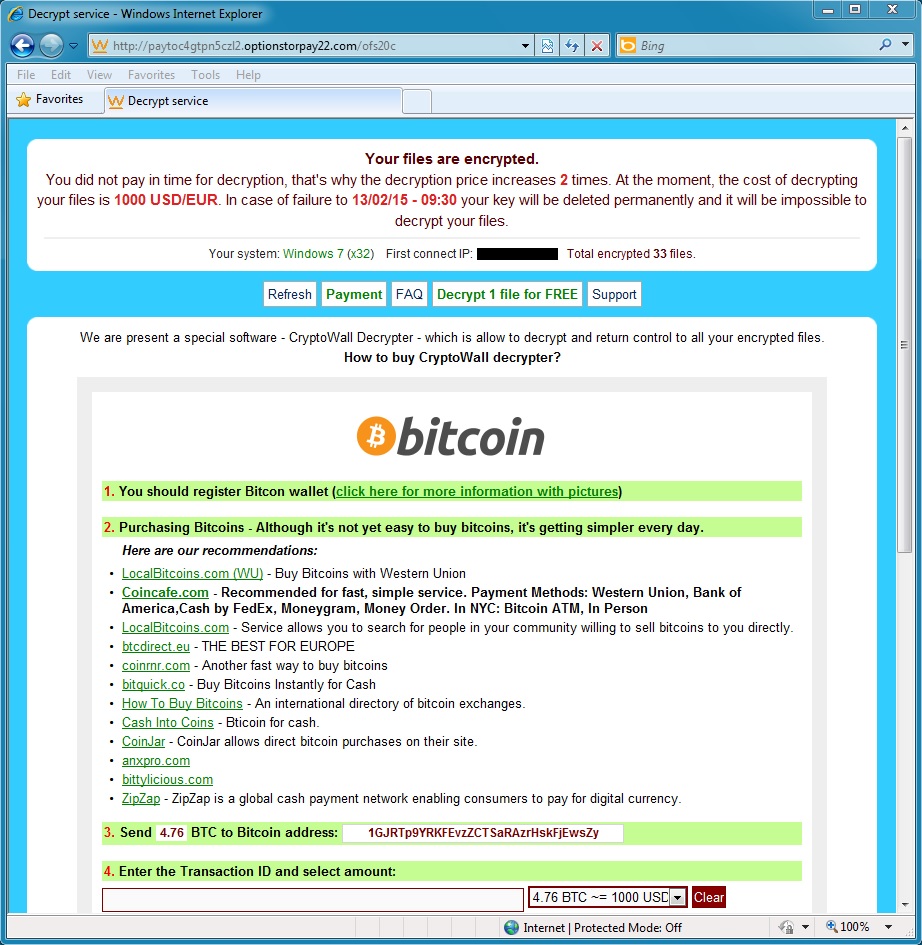
MALWARE PAYLOAD 1 OF 4 - CRYPTOWALL 3.0 RANSOMWARE:
File name: 2015-02-13-Magnitude-EK-payload-1-of-4-CryptoWall-3.0.exe
File size: 160768 bytes
MD5 hash: ac9f5c52e3f97fc07114050c05ee5fff
Detection ratio: 22 / 56
First submission: 2015-02-13 19:40:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/c5bf64c7c0b5ea729e487275f026f0fe866299152ff5d1789739db39b3aca602/analysis/Bitcoin address for ransomware payment: 1GJRTp9YRKFEvzZCTSaRAzrHskFjEwsZy
Post-infection traffic:
- 2015-02-13 19:41:43 UTC - port 80 - ip-addr[.]es GET /
- 2015-02-13 19:41:44 UTC - 72.29.73[.]163 port 80 - captainblowdri[.]com - POST /img4.php?u=p031cd8b8fyu
- 2015-02-13 19:41:52 UTC - 72.29.73[.]163 port 80 - captainblowdri[.]com - POST /img4.php?t=k2n6a8k25ga4x
- 2015-02-13 19:41:59 UTC - 72.29.73[.]163 port 80 - captainblowdri[.]com - POST /img4.php?v=6vtl146l07kgo2
Alerts:
- 72.29.73[.]163 port 80 - ET TROJAN CryptoWall Check-in (sid:2018452)
MALWARE PAYLOAD 2 OF 4 - REDYMS/RAMDO VARIANT:
File name: 2015-02-13-Magnitude-EK-payload-2-of-4-Redyms-Ramdo.exe
File size: 228,176 bytes
MD5 hash: 438969a9134912de002c60e8c32ddf36
Detection ratio: 5 / 57
First submission: 2015-02-13 19:40:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/6ba1b80c826536f75403d31d720c7d09affd00d17fc87863c151f4bf7923bba0/analysis/Post-infection traffic:
- 2015-02-13 19:45:09 UTC - 64.233.168[.]99 port 80 - www.google[.]com - GET /
- 2015-02-13 19:45:09 UTC - DNS request for: ywoqmcmwuqgysmcw[.]org [repeats - response: Server failure]
- 2015-02-13 19:45:19 UTC - 64.233.168[.]99 port 80 - www.google[.]com - GET /
- 2015-02-13 19:46:06 UTC - DNS request for: iqumgmcqwuqgaaus[.]org [repeats - response: No such name]
- 2015-02-13 19:46:06 UTC - 64.233.168[.]99 port 80 - www.google[.]com - GET /
- 2015-02-13 19:46:53 UTC - 166.78.144[.]80 port 80 - sksqqagakeicoeso[.]org - POST /
- 2015-02-13 19:46:53 UTC - 64.233.168[.]99 port 80 - www.google[.]com - GET /
- 2015-02-13 19:47:40 UTC - 192.42.116[.]41 port 80 - uoewuismooowgcui[.]org - POST /
- 2015-02-13 19:47:40 UTC - 64.233.168[.]99 port 80 - www.google[.]com - GET /
- 2015-02-13 19:48:29 UTC - 77.120.158[.]57 port 80 - uociwiiqgmqwwmkq[.]org - POST /
- 2015-02-13 19:48:31 UTC - 77.120.158[.]57 port 80 - uociwiiqgmqwwmkq[.]org - GET /04.cab
- 2015-02-13 19:48:31 UTC - 77.120.158[.]57 port 80 - uociwiiqgmqwwmkq[.]org - GET /04.cab
Alerts:
- www.google[.]com - port 80 - ET WEB_CLIENT SUSPICOUS Possible automated connectivity check (www.google[.]com) (sid:2018430)
- www.google[.]com - port 80 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 66.78.144[.]80 port 80 - ET TROJAN Connection to Georgia Tech Sinkhole IP (Possible Infected Host) (sid:2016994)
- 66.78.144[.]80 port 80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
- 192.42.116[.]41 port 80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
- 77.120.158[.]57 port 80 - ETPRO TROJAN W32/Redyms.AF (sid:2807393)
- 66.78.144[.]80 port 80 - ET TROJAN Known Sinkhole Response Header (sid:2016803)
- 192.42.116[.]41 port 80 - ET TROJAN Known Sinkhole Response Header (sid:2016803)
- www.google[.]com - port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute [**]
- 66.78.144[.]80 port 80 - [1:30547:2] MALWARE-CNC Win.Trojan.Ramdo variant outbound connection
- 192.42.116[.]41 port 80 - [1:30547:2] MALWARE-CNC Win.Trojan.Ramdo variant outbound connection
- 77.120.158[.]57 port 80 - [1:30547:2] MALWARE-CNC Win.Trojan.Ramdo variant outbound connection
- 66.78.144[.]80 port 80 - [1:25018:3] BLACKLIST Connection to malware sinkhole
- 192.42.116[.]41 port 80 - [1:30320:1] BLACKLIST Connection to malware sinkhole
MALWARE PAYLOAD 3 OF 4 - ZBOT/BUNITU VARIANT:
File name: 2015-02-13-Magnitude-EK-payload-3-of-4-Zbot-Bunitu.exe
File size: 94,208 bytes
MD5 hash: 9313462ed56d4c35b718b098d30713b0
Detection ratio: 16 / 57
First submission: 2015-02-13 19:40:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/d1b2935d1ed9a163394bcb63c9ca8e71bb0861430b477c0eba29962691de80dd/analysis/Post-infection traffic:
- 2015-02-13 19:44:24 UTC - 95.211.233[.]121 port 53 - [TCP] GET /adpick/garden?src=FB99A2B52D9B7E85AA&xbtn=y&platform=android&[long string]
- 2015-02-13 19:44:25 UTC - 66.199.229[.]91 port 53 - [TCP] POST /api/v1/sessionStart
- 2015-02-13 19:44:27 UTC - 85.17.143[.]84 port 53 - [TCP] TCP non-ASCII data
- 2015-02-13 19:44:28 UTC - 76.73.102[.]74 port 53 - [TCP] TCP non-ASCII data, continues throughout pcap
- 2015-02-13 19:44:55 UTC - 67.21.4[.]136 port 80 - hs.aarki[.]net GET /adpick/garden?src=FB99A2B52D9B7E85AA&xbtn=y&platform=android&[long string]
- 2015-02-13 19:44:56 UTC - 67.21.4[.]136 port 80 - hs.aarki[.]net GET /garden_content?src=FB99A2B52D9B7E85AA&xbtn=y&platform=android&[long string]
- 2015-02-13 19:45:11 UTC - 54.243.36[.]223 port 80 - api.vungle[.]com - POST /api/v1/sessionStart
- 2015-02-13 19:47:47 UTC - 95.211.121[.]18 port 80 - whoer[.]net - GET / [other associated HTTP GET requests]
- 2015-02-13 19:48:08 UTC - 208.82.236[.]242 port 80 - houston.craigslist[.]org - GET /pet/4890210854.html [other associated HTTP GET requests]
Alerts:
- 95.211.233[.]121 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 66.199.229[.]91 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 85.17.143[.]84 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 76.73.102[.]74 port 53 - ETPRO TROJAN Trojan/Win32.Zbot Covert Channel 2 port 53 (sid:2807561)
- 85.17.143[.]84 port 53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection
- 76.73.102[.]74 port 53 - [1:28996:4] MALWARE-CNC Win.Trojan.Bunitu variant outbound connection (more than 8000 hits)
MALWARE PAYLOAD 4 OF 4 - SIMDA:
File name: 2015-02-13-Magnitude-EK-payload-4-of-4-Simda.exe
File size: 858,112 bytes
MD5 hash: 69f27b07404cf9c51dd2d2e40fca4d65
Detection ratio: 16 / 56
First submission: 2015-02-13 19:40:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/5617238b8d3b232f0743258b89720bb04d941278253e841ee9cbf863d0985c32/analysis/Post-infection traffic:
- 2015-02-13 19:42:35 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?793c79u31=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:35 UTC - 217.23.12[.63 port 80 - report.55c5555gmy5555i[.]com - POST /
- 2015-02-13 19:42:35 UTC - 217.23.12[.63 port 80 - update.znutcptzo[.]com - GET /?tn=ka2glJbalV6wpdmryaGoqtRkm5%2Bg2q[long string of characters]
- 2015-02-13 19:42:35 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?IQG143=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:36 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?1k9yWS920=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:36 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?1y9c17u17=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:36 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?uO93m758=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:36 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?31eIQ55=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:41 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?9317aA116=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:42:52 UTC - 79.142.66[.239 port 80 - report.55c5555gmy5555i[.]com - GET /?k3y79309=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:43:02 UTC - port 80 - www.bing[.]com - GET /chrome/report.html?5s55s=%9B%EE%EDk%D9%DF%C6%[long string of characters]
- 2015-02-13 19:43:02 UTC - 79.142.66[.]239 port 80 - report.55c5555gmy5555i[.]com - GET /?mY317925=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:43:02 UTC - 79.142.66[.]239 port 80 - report.55c5555gmy5555i[.]com - GET /?I1qG57=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:43:02 UTC - 79.142.66[.]239 port 80 - report.55c5555gmy5555i[.]com - GET /?55c5sK563=%96%9D%A0%9F%A7%DA%[long string of characters]
- 2015-02-13 19:43:03 UTC - 79.142.66[.]239 port 80 - report.55c5555gmy5555i[.]com - GET /?931y918=%96%9D%A0%9F%A7%DA%[long string of characters]
Alerts:
- 79.142.66[.]239 port 80 - ET TROJAN Simda.C Checkin (sid:2016300)
- 217.23.12[.]63 port 80 - ETPRO TROJAN Backdoor.Win32.Simda.abpn Checkin (sid:2807145)
- 79.142.66[.]239 port 80 - [1:22937:5] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- 217.23.12[.]63 port 80 - [1:26212:2] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection
- www.bing[.]com - [1:20661:4] MALWARE-CNC Simbda variant outbound connection
- www.bing[.]com - [1:25038:2] BROWSER-WEBKIT Apple Safari Webkit css title memory corruption attempt
SCREENSHOTS FROM THE TRAFFIC
From the CryptoWall 3.0 ransomware sample:
Click here to return to the main page.