2015-02-23 - SWEET ORANGE EK FROM 95.183.8[.]177 - H.ROCKYHILLREALTOR.COM:8085
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-02-23-Sweet-Orange-EK-traffic.pcap.zip
- 2015-02-23-Sweet-Orange-EK-post-infection-traffic.pcap.zip
- 2015-02-23-Sweet-Orange-EK-malware.zip
NOTES:
- This traffic is extremely similar to the Sweet Orange EK traffic seen on 2015-02-09 (link).
- The gate domain leading to Sweet Orange EK is using the same IP address (50.87.151[.]146) seen previously on 2015-02-09.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.87.151[.]146 - static.platinumweddingplanner[.]com - Gate to Sweet Orange EK
- 95.183.8[.]177 - h.rockyhillrealtor[.]com:8085 and k.rockyhillrealtor[.]com:8085 - Sweet Orange EK
- 66.240.194[.]139 port 80 - mqaqyrcqzltddqx.org and xfniqbczwzrwv[.]net - Post-infection traffic
- 69.89.31[.]157 port 80 - wxhlloterlldxa[.]biz - Post-infection traffic
- 74.50.25[.]220 port 80 - tgfuzlqdfqzuzascrnbhe[.]com and iporooljeteuckhibfmxs[.]org - Post-infection traffic
- 216.227.216[.]66 port 80 - qdpgrzesnnodsgrafecklaxpb[.]biz and uvxhzlybcacnbvg[.]org - Post-infection traffic
- 216.227.214[.]85 port 80 - scfcgysgeouqvcjp[.]info and mvxpehjudkxezuazkt[.]net - Post-infection traffic
- 181.224.138[.]240 port 21 and 34630 - no domain name - FTP server used by the malware in post-infection traffic
- 85.25.210[.]196 port 65400 - no domain name - TCP callback traffic caused by the malware
INFECTION TRAFFIC:
- 2015-02-23 16:00:08 UTC - static.platinumweddingplanner[.]com - GET /k?tstmp=918016303
- 2015-02-23 16:00:15 UTC - h.rockyhillrealtor[.]com:8085 - GET /1/lines.php?norway=3
- 2015-02-23 16:00:22 UTC - h.rockyhillrealtor[.]com:8085 - GET /1/Cv1ixRU47ltFEg
- 2015-02-23 16:00:26 UTC - k.rockyhillrealtor[.]com:8085 - GET /cars.php?soma=2776&humor=316&timeline=4&jobs=171&image=171&nomic=2517&anal=1390&urepair=errfix
- 2015-02-23 16:00:49 UTC - k.rockyhillrealtor[.]com:8085 - GET /cars.php?soma=2776&humor=316&timeline=4&jobs=171&image=171&nomic=2517&anal=1390
POST-INFECTION TRAFFIC:
- 2015-02-23 16:43:47 UTC - google[.]com - GET /
- 2015-02-23 16:43:48 UTC - tgfuzlqdfqzuzascrnbhe[.]com - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:48 UTC - sanjose.speedtest.comcast[.]net - GET /speedtest/random750x750.jpg?x=32408&y=1
- 2015-02-23 16:43:48 UTC - www.godaddy[.]com - GET /
- 2015-02-23 16:43:48 UTC - www.ip-adress[.]com - GET /
- 2015-02-23 16:43:49 UTC - boston.speedtest.comcast[.]net - GET /speedtest/random750x750.jpg?x=16179&y=1
- 2015-02-23 16:43:50 UTC - www.download.windowsupdate[.]com - GET /msdownload/update/v3/static/trustedr/en/authrootstl.cab
- 2015-02-23 16:43:51 UTC - ocsp.godaddy[.]com - GET //MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTk[long string of characters]
- 2015-02-23 16:43:51 UTC - jacksonville.speedtest.comcast[.]net - GET /speedtest/random750x750.jpg?x=24239&y=1
- 2015-02-23 16:43:51 UTC - ocsp.godaddy[.]com - GET //MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQ[long string of characters]
- 2015-02-23 16:43:52 UTC - ocsp.godaddy[.]com - GET //MEgwRjBEMEIwQDAJBgUrDgMCGgUABBS2[long string of characters]
- 2015-02-23 16:43:53 UTC - 181.224.138[.]240 - [FTP traffic]
- 2015-02-23 16:43:52 UTC - houston.speedtest.comcast[.]net - GET /speedtest/random750x750.jpg?x=19907&y=1
- 2015-02-23 16:43:53 UTC - scfcgysgeouqvcjp[.]info - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:53 UTC - www.godaddy[.]com - GET /
- 2015-02-23 16:43:53 UTC - 85.25.210[.]196 - [TCP traffic]
- 2015-02-23 16:43:55 UTC - wxhlloterlldxa[.]biz - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:55 UTC - wxhlloterlldxa[.]biz - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:55 UTC - www.godaddy[.]com - GET /
- 2015-02-23 16:43:56 UTC - qdpgrzesnnodsgrafecklaxpb[.]biz - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:56 UTC - mqaqyrcqzltddqx.org - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:57 UTC - uvxhzlybcacnbvg[.]org - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:57 UTC - iporooljeteuckhibfmxs[.]org - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:57 UTC - mvxpehjudkxezuazkt[.]net - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
- 2015-02-23 16:43:57 UTC - xfniqbczwzrwv[.]net - POST /sq2gMsSwSdT7Ko9xe05BRJHg.php
ALERTS
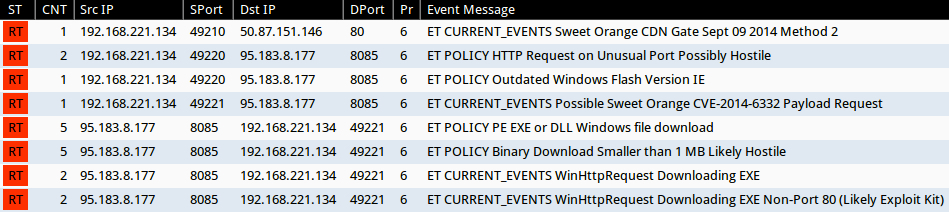
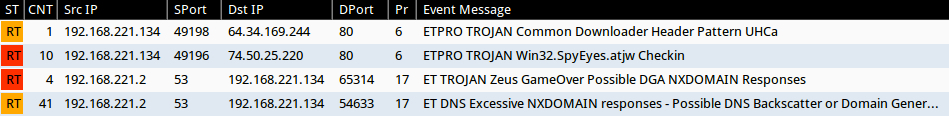
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 50.87.151[.]146 port 80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 95.183.8[.]177 port 8085 - ET CURRENT_EVENTS Possible Sweet Orange CVE-2014-6332 Payload Request (sid:2019752)
- 95.183.8[.]177 port 8085 - ET CURRENT_EVENTS WinHttpRequest Downloading EXE (sid:2019822)
- 95.183.8[.]177 port 8085 - ET CURRENT_EVENTS WinHttpRequest Downloading EXE Non-Port 80 (Likely Exploit Kit) (sid:2019823)
- 64.34.169[.]244 port 80 (www.ip-adress[.]com) - ETPRO TROJAN Common Downloader Header Pattern UHCa (sid:2803270)
- 69.89.31[.]157 port 80 - ETPRO TROJAN Win32.SpyEyes.atjw Checkin (sid:2809522)
- 74.50.25[.]220 port 80 - ETPRO TROJAN Win32.SpyEyes.atjw Checkin (sid:2809522)
- 216.227.216[.]66 port 80 - ETPRO TROJAN Win32.SpyEyes.atjw Checkin (sid:2809522)
- 216.227.214[.]85 port 80 - ETPRO TROJAN Win32.SpyEyes.atjw Checkin (sid:2809522)
- DNS queries for several different domains - ET DNS Excessive NXDOMAIN responses - Possible DNS Backscatter or Domain Generation Algorithm Lookups (sid:2008470)
- DNS responses for different domains - ET TROJAN Zeus GameOver Possible DGA NXDOMAIN Responses (sid:2018316)
Notable signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 95.183.8[.]177 port 8085 - [1:32638:1] EXPLOIT-KIT Sweet Orange exploit kit Adobe Flash exploit on defined port
- 95.183.8[.]177 port 8085 - [1:11192:16] FILE-EXECUTABLE download of executable content (x2)
- 95.183.8[.]177 port 8085 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x2)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-02-23-Sweet-Orange-EK-flash-exploit.swf
File size: 8,272 bytes
MD5 hash: 270533e84d9dc5b978699892d37313d3
Detection ratio: 1 / 56
First submission: 2015-02-17 08:08:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/1e45ccf263a43971cb2a6d86271d0773ad997a387ffbc1dab4b3bfa8f952e561/analysis/
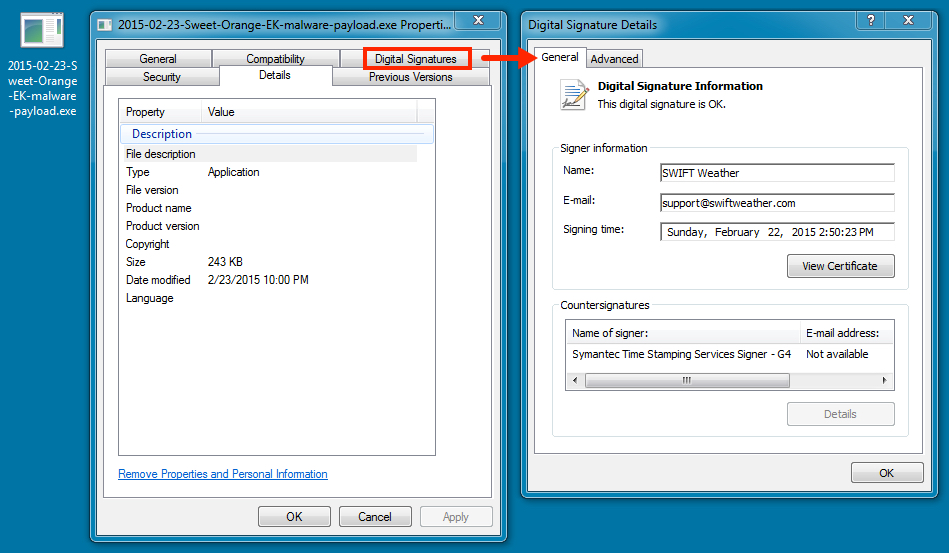
MALWARE PAYLOAD:
File name: 2015-02-23-Sweet-Orange-EK-malware-payload.exe
File size: 248,880 bytes
MD5 hash: 616f8966d03a3a6f00891d40a17b00c5
Detection ratio: 25 / 57
First submission: 2015-02-23 00:05:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/d2025e0d2adb28d51debe5f64387bf238503434dc76c9666e3c09fbc0c6951f2/analysis/
Click here to return to the main page.