2015-03-16 - EXAMPLES OF NUCLEAR EK PUSHING KELIHOS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-03-16-Nuclear-EK-from-threatglass-stripped-down-traffic.pcap.zip
- 2015-03-16-Nuclear-EK-from-my-infected-VM.pcap.zip
NOTES:
- I've noticed a recent trend on Threatglass, where Nuclear EK is pushing what EmergingThreats identifies as Kelihos malware.
- Kelihos is a well-publicized botnet, easy to search for on Google.
TODAY'S THREATGLASS ENTRY:
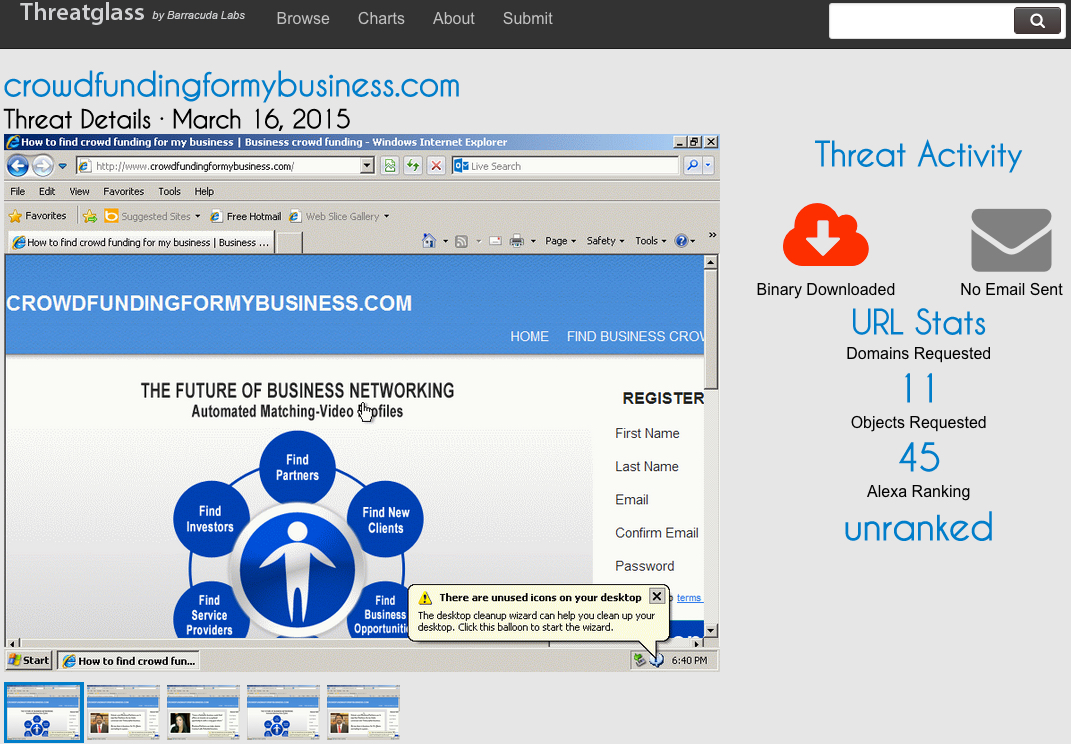
- Date/Time: 2015-03-16 19:39 UTC
- 162.144.66[.]10 port 80 - www.crowdfundingformybusiness[.]com - Compromised website
- 185.14.30[.]37 port 80 - goog1eanalitics[.]pw - First redirect
- 178.32.173[.]105 port 80 - 178.32.173[.]105 - Second redirect
- 46.101.59[.]201 port 80 - osooraudie[.]co[.]vu - Nuclear EK
- 89.144.2[.]115 port 80 - - GET /kernel1.exe HTTP/1.0 [follow-up Kelihos download]
SIMILAR THREATGLASS ENTRIES
https://web.archive.org/web/20151128042133/http://threatglass.com/malicious_urls/ncef-org-np
- Date/Time: 2015-03-11 18:44 UTC
- 184.171.254[.]44 - ncef[.]org[.]np - compromised website
- 178.32.173[.]105 - redirect
- 180.61.166[.]110 - charlottmehrmann[.]cf - Nuclear EK
- 85.65.55[.]219 - GET /kernel1.exe HTTP/1.0 [follow-up Kelihos download]
- 31.170.158[.]55 - GET /kernel1.exe HTTP/1.0 [follow-up Kelihos download]
https://web.archive.org/web/20151128042055/http://threatglass.com/malicious_urls/konopialeczy-pl
- Date/Time: 2015-03-11 18:24 UTC
- 195.88.51[.]209 - konopialeczy[.]pl - compromised website
- 178.32.173[.]105 - redirect
- 108.61.166[.]110 - zipsdiablo[.]ml - Nuclear EK
- 5.105.56[.]87 - GET /kernel1.exe HTTP/1.0 [follow-up Kelihos download]
https://web.archive.org/web/20151128042128/http://threatglass.com/malicious_urls/namiknam-com
- Date/Time: 2015-03-11 18:24 UTC
- 31.169.80[.]50 - namiknam[.]com - compromised website
- 178.32.173[.]105 - redirect
- 108.61.166[.]110 - zipsdiablo[.]ml - Nuclear EK
- 98.236.244[.]44 - GET /kernel1.exe HTTP/1.0 [follow-up Kelihos download]
- 119.238.10[.]9 - GET /kernel1.exe HTTP/1.0 [follow-up Kelihos download]
TODAY'S TRAFFIC
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2015-03-16 19:39:54 UTC - www.crowdfundingformybusiness[.]com - GET /wp-content/plugins/acismit/wp-facebook.php
- 2015-03-16 19:39:56 UTC - goog1eanalitics[.]pw - GET /iliv.cgi?
- 2015-03-16 19:39:56 UTC - 178.32.173[.]105 - GET /
NUCLEAR EK:
- 2015-03-16 19:39:57 UTC - osooraudie[.]co[.]vu - GET /W1EAUk9UWRlU.html
- 2015-03-16 19:39:58 UTC - osooraudie[.]co[.]vu - GET /BhlJSgtVWAEZVQEfUEUHB1dXUFZQDldRRQAHS1NWUEoIVlQXDgMZBwlX
- 2015-03-16 19:40:00 UTC - osooraudie[.]co[.]vu - GET /BQhVU09dUVwBGAhbHQhKAlFTU1BXDVRVCUoFUU9XVlEXUlQMGAtVHVAZDVYvFHNRVTA
- 2015-03-16 19:40:01 UTC - osooraudie[.]co[.]vu - GET /BQhVU09dUVwBGAhbHQhKAlFTU1BXDVRVCUoFUU9XVlEXUlQMGAtVHVAZNEoMElNQQyItGVc
POST-INFECTION CALL FOR MORE MALWARE:
- 2015-03-16 19:41:58 UTC - 89.144.2[.]115 - GET /kernel1.exe
ALERTS
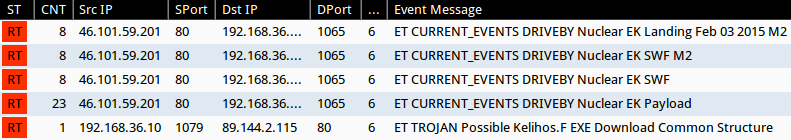
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 46.101.59[.]201 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Feb 03 2015 M2 (sid:2020354)
- 46.101.59[.]201 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 46.101.59[.]201 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020311)
- 46.101.59[.]201 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 89.144.2[.]115 port 80 - ET TROJAN Possible Kelihos.F EXE Download Common Structure (sid:2017598)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.0 on Debian 7:
- 46.101.59[.]201 port 80 - [1:32359:1] FILE-FLASH Adobe Flash Player worker shared object user-after-free attempt
- 89.144.2[.]115 port 80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 89.144.2[.]115 port 80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 89.144.2[.]115 port 80 - [1:33717:1] OS-WINDOWS Microsoft Windows Task Scheduler access control bypass attempt
NOTE: The second pcap from my infected host (not reviewed here) generated more Emergingthreats related to Kelihos:
- ET TROJAN Win32/Kelihos.F Checkin (sid:2017191)
- ETPRO TROJAN Win32/Kryptik.BLYP Checkin (sid:2807093)
- ET TROJAN Possible Kelihos Infection Executable Download With Malformed Header (sid:2018241)
- ET TROJAN Storm/Waledac 3.0 Checkin 1 (sid:2012137)
- ET TROJAN Suspicious double Server Header (sid:2012707)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-03-16-Nuclear-EK-flash-exploit.swf
File size: 9,571 bytes
MD5 hash: 695a07cbcac3ca64010e168fe495ff4a
Detection ratio: 1 / 56
First submission: 2015-03-16 20:15:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/a4ddec2928f1fe9a2ccf305ada60dd93b057bdaf6db911d9c0c763883c2e3cb3/analysis/
MALWARE PAYLOAD:
File name: 2015-03-16-Nuclear-EK-malware-payload.exe
File size: 115,200 bytes
MD5 hash: eff5e3e630ad238c08984fe9ad59b87d
Detection ratio: 5 / 56
First submission: 2015-03-16 20:12:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/9394b044686bf90ee7a1fe94c1e543b834d430db0f37812dc91b4d3c2c68d0ef/analysis/
FOLLOW-UP MALWARE:
File name: kernel1.exe
File size: 11,493,504 bytes
MD5 hash: d8b81506190ea42454329159d6e182ca
Detection ratio: 8 / 57
First submission: 2015-03-16 20:13:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/c7fd604e0ee81919549ad13259b7cadb9bd653a5adc39a51c18117dd17cb1496/analysis/
Click here to return to the main page.
