2015-03-18 - UPATRE/DYRE INFECTION FROM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-03-18-upatre-dyre-infection-traffic.pcap.zip
- 2015-03-18-upatre-dyre-email-example.eml.zip
- 2015-03-18-upatre-dyre-malware-and-artifacts.zip
NOTES:
- These emails came though on 2015-03-17, but I didn't find out about them until today.
- I thought this was interesting enough to dig into, but it's just another botnet-based Upatre/Dyre malspam run.
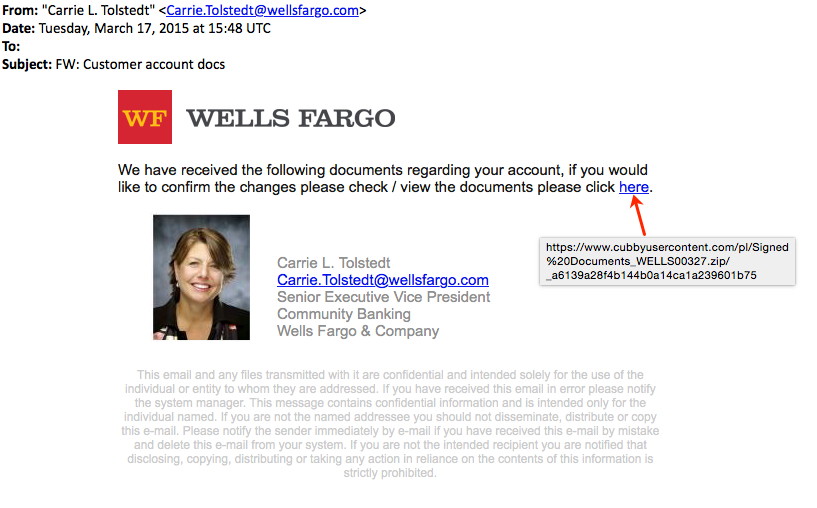
- Of note, the picture used in the email not Carrie L. Tolstedt. It's actually Jamie Moldafsky, Wells Fargo's Chief Marketing Officer.
- One wonders why the spammers didn't use a real image of Carrie L. Tolstedt. A quick Google search shows many images of Tolstedt.
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
From: "Carrie L. Tolstedt" <Carrie.Tolstedt@wellsfargo[.]com>
Date: Tuesday, March 17, 2015 at 15:48 UTC
To:
Subject: FW: Customer account docs
[image: Wells Fargo Logo]
We have received the following documents regarding your account, if you would like to confirm the changes please check / view the documents please click here.
[image: Carrie Tolstedt Portrait]
Carrie L. Tolstedt
Carrie.Tolstedt@wellsfargo[.]com
Senior Executive Vice President
Community Banking
Wells Fargo & Company
This email and any files transmitted with it are confidential and intended solely for the use of the individual or entity to whom they are addressed. If you have received this email in error please notify the system manager. This message contains confidential information and is intended only for the individual named. If you are not the named addressee you should not disseminate, distribute or copy this e-mail. Please notify the sender immediately by e-mail if you have received this e-mail by mistake and delete this e-mail from your system. If you are not the intended recipient you are notified that disclosing, copying, distributing or taking any action in reliance on the contents of this information is strictly prohibited.
EXAMPLES OF EMAIL HEADERS:
- Received from: bas2-sudbury98-1177593190.dsl.bell[.]ca [70.48.165[.]102] - envelope-sender <ore@bommer[.]com>
- Message-ID: <DDDW15IQ.4639879@bommer[.]com>
- Received from: atm4-0-0-70.tui1.tuileries.raei.francetelecom[.]net [194.51.110[.]141] - envelope-sender <teknique@tekniquethekingpin[.]com>
- Message-ID: <019GY37I.1520445@tekniquethekingpin[.]com>
- Received from: EWPILXSMOI [85.199.24[.]163] - envelope-sender <ucr@bngw.ballast-nedam[.]com>
- Message-ID: <DHZ991N6.7062496@bngw.ballast-nedam[.]com>
- Received from: static196-54-253-206-196.adsl196-8.iam[.]net[.]ma [196.206.253[.]54] - envelope-sender <ryr@bochkia[.]com>
- Message-ID: <GADHP5ZQ.8692574@bochkia[.]com>
- Received from: h96-60-115-86.applwi.dedicated.static.tds[.]net [96.60.115[.]86] - envelope-sender <xmoaaj@brankindesign[.]com>
- Message-ID: <9VENAB7B.3959045@brankindesign[.]com>
- Received from: 86-122-76-50.static.brasov.rdsnet[.]ro [86.122.76[.]50] - envelope-sender <pagepsprx@bpclawyers[.]com>
- Message-ID: <SSU7TWVA.6729472@bpclawyers[.]com>
- Received from: alicegate [79.61.4[.]235] - envelope-sender <wlov@bomp[.]com>
- Message-ID: <IT2DUZB3.3040631@bomp[.]com>
EXAMPLES OF LINKS TO THE MALWARE:
- https: www.cubbyusercontent[.]com - GET /pl/SignedDocuments.zip/_c336b3b9730b47be939954e53f673116
- https: www.cubbyusercontent[.]com - GET /pl/Signed%20Documents.zip/_84eb98c728b74a92a3ce63a8196cefa5
- https: www.cubbyusercontent[.]com - GET /pl/Signed%20Documents_WELLS00327.zip/_a6139a28f4b144b0a14ca1a239601b75 (didn't work when I checked it)
- https: www.cubbyusercontent[.]com - GET /pl/SignedDocuments_AN994264SKR.zip/_68174f755c6940cc81f33aab2cc6169a
- https: www.cubbyusercontent[.]com - GET /pl/SignedDocuments_770488311.zip/_c8914f25b8974a0aaedcb0db6ce89f9c
INFECTION TRAFFIC
DOWNLOAD OF ZIP FILE FROM HTTPS LINK:
- 2015-03-18 16:03:43 UTC - 69.25.30[.]70 port 443 - www.cubbyusercontent[.]com - HTTPS traffic
- 2015-03-18 16:03:43 UTC - 69.25.30[.]54 port 443 - ws.cubbyusercontent[.]com - HTTPS traffic
RUNNING THE EXTRACTED MALWARE ON A VM:
- 2015-03-18 16:12:26 UTC - 91.198.22[.]70 port 80 - checkip.dyndns[.]org - GET /
- 2015-03-18 16:12:28 UTC - 109.230.131[.]95 port 14447 - 109.230.131[.]95:14447 - GET /1703no11/WIN-C2KE6N4W3N1/0/61-SP1/0/JJBELKBJKBEMG
- 2015-03-18 16:12:28 UTC - 198.23.48[.]157 port 80 - maxprintingcentre[.]com - GET /swf/wusn.pdf
- 2015-03-18 16:12:29 UTC - 109.230.131[.]95 port 14447 - 109.230.131[.]95:14447 - GET /1703no11/WIN-C2KE6N4W3N1/41/2/1/JJBELKBJKBEMG
- 2015-03-18 16:12:29 UTC - 208.113.214[.]232 port 80 - ativokids[.]info - GET /downloads/Hugo/wusn.pdf
- 2015-03-18 16:12:29 UTC - 208.113.214[.]232 port 80 - www.ativokids[.]info - GET /downloads/Hugo/wusn.pdf
- 2015-03-18 16:12:38 UTC - 109.230.131[.]95 port 14446 - 109.230.131[.]95:14446 - GET /1703no11/WIN-C2KE6N4W3N1/41/7/4/
- 2015-03-18 16:14:16 UTC - 37.59.44[.]18 port 80 - 37.59.44[.]18 - GET /ml1from1.tar
POST-INFECTION UDP STUN TRAFFIC:
- 2015-03-18 16:12:48 UTC - 62.71.2[.]168 port 3478 - UDP STUN traffic to stun.rixtelecom[.]se
POST-INFECTION TCP TRAFFIC:
- 2015-03-18 16:13:31 UTC - 95.154.91[.]230 port 443 - attempted TCP connection - RST by server
- 2015-03-18 16:14:02 UTC - 194.28.190[.]167 port 443 - encrypted traffic
- 2015-03-18 16:14:19 UTC - 95.211.193[.]10 port 15695 - encrypted traffic
- 2015-03-18 16:14:20 UTC - 212.56.214[.]203 port 443 - encrypted traffic
- 2015-03-18 16:14:21 UTC - 95.211.189[.]208 port 25 - attempted TCP connection to docs233[.]com - RST by server
- 2015-03-18 16:14:21 UTC - 95.211.189[.]208 port 465 - TCP connection to mail.docs233[.]com (no data sent)
- 2015-03-18 16:14:33 UTC - 188.165.227[.]12 port 443 - attempted TCP connection - RST by server
ALERTS FROM THE TRAFFIC
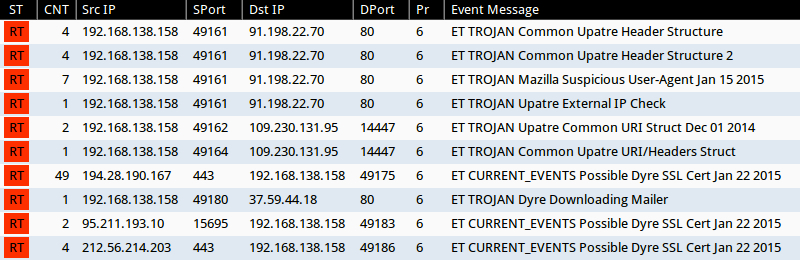
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 91.198.22[.]70 port 80 - ET TROJAN Common Upatre Header Structure (sid:2018394)
- 91.198.22[.]70 port 80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- 91.198.22[.]70 port 80 - ET TROJAN Mazilla Suspicious User-Agent Jan 15 2015 (sid:2020235)
- 91.198.22[.]70 port 80 - ET TROJAN Upatre External IP Check (sid:2020370)
- 109.230.131[.]95 port 14447 - ET TROJAN Upatre Common URI Struct Dec 01 2014 (sid:2019847)
- 109.230.131[.]95 port 14447 - ET TROJAN Common Upatre URI/Headers Struct (sid:2020369)
- 194.28.190.167 port 443 - ET CURRENT_EVENTS Possible Dyre SSL Cert Jan 22 2015 (sid:2020290)
- 37.59.44[.]18 port 80 - ET TROJAN Dyre Downloading Mailer (sid:2020308)
- 95.211.193[.]10 port 15695 - ET CURRENT_EVENTS Possible Dyre SSL Cert Jan 22 2015 (sid:2020290)
- 212.56.214[.]203 port 443 - ET CURRENT_EVENTS Possible Dyre SSL Cert Jan 22 2015 (sid:2020290)
Talos (Snort) ruleset from Snort 2.9.7.0 on Debian 7:
- 91.198.22[.]70 port 80 - [1:33211:3] MALWARE-CNC Win.Trojan.Upatre variant outbound connection
- 91.198.22[.]70 port 80 - [1:33207:2] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre
- 91.198.22[.]70 port 80 - [1:26353:1] INDICATOR-COMPROMISE IP address check to dyndns.org detected
- 109.230.131[.]95 port 14447 - [1:33207:2] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre (x2)
- 109.230.131[.]95 port 14447 - [1:33594:1] MALWARE-CNC Win.Trojan.Upatre variant outbound connection
- 198.23.48[.]157 port 80 - [1:33211:3] MALWARE-CNC Win.Trojan.Upatre variant outbound connection
- 198.23.48[.]157 port 80 - [1:33207:2] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre
- 208.113.214[.]232 port 80 - [1:33211:3] MALWARE-CNC Win.Trojan.Upatre variant outbound connection (x2)
- 208.113.214[.]232 port 80 - [1:33207:2] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre (x2)
- 109.230.131[.]95 port 14446 - [1:33207:2] BLACKLIST User-Agent known malicious user-agent string - Mazilla/5.0 - Win.Backdoor.Upatre
MALWARE FROM INFECTED HOST
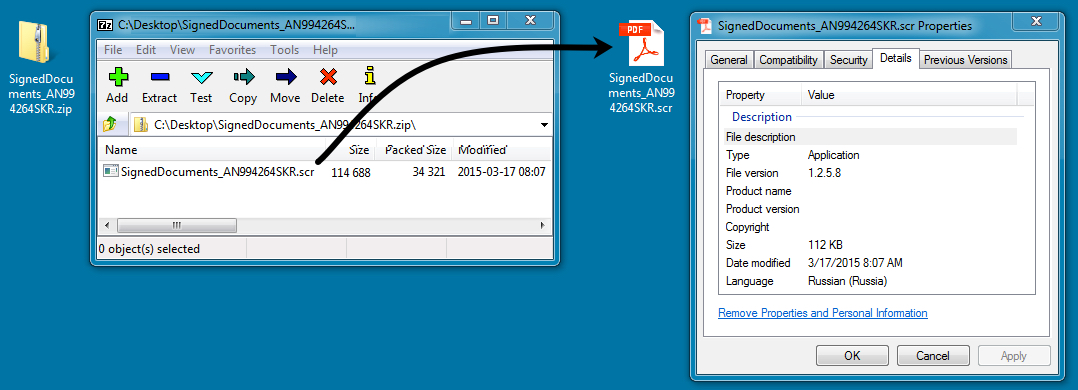
- SignedDocuments_AN994264SKR.zip (34,481 bytes) MD5 hash: 0ce2cfdd18451a44716986021e927224
- SignedDocuments_AN994264SKR.scr (114,688 bytes) MD5 hash: 1c443541f6c9379772c2324b7a515aa3
- C:\Users\username\AppData\Local\Temp\UqTiiq6.exe (114,688 bytes) MD5 hash: 1c443541f6c9379772c2324b7a515a
- C:\Users\username\AppData\Local\Temp\ajmgblqlq.exe (524,288 bytes) MD5 hash: 357f2b0ff6fa9ce1955a725fe191457e
- C:\Windows\WOYhNpjdmRaWTLM.exe (524,288 bytes) MD5 hash: 357f2b0ff6fa9ce1955a725fe191457e
- C:\Users\username\AppData\Local\Temp\temp15.pdf (42,107 bytes) MD5 hash: 832d591a36ad6e190ee8d37a4e2cb47a
- C:\Users\username\AppData\Local\Temp\tmp-8DA4.txt (489,401 bytes) MD5 hash: 0325313fcbe122dc99d15ae0d0e8c52f
- C:\Windows\temp\7AFF.tmp (1,075,200 bytes) MD5 hash: 29d0960d37c33c06466ecec5bdb80d0f
- C:\Windows\temp\3F38.tmp (43,520 bytes) MD5 hash: a078a7877628919c751f62e10c25f942
- C:\Windows\temp\A16.tmp (43,520 bytes) MD5 hash: a078a7877628919c751f62e10c25f942
- C:\Windows\temp\F5DC.tmp (43,520 bytes) MD5 hash: a078a7877628919c751f62e10c25f942
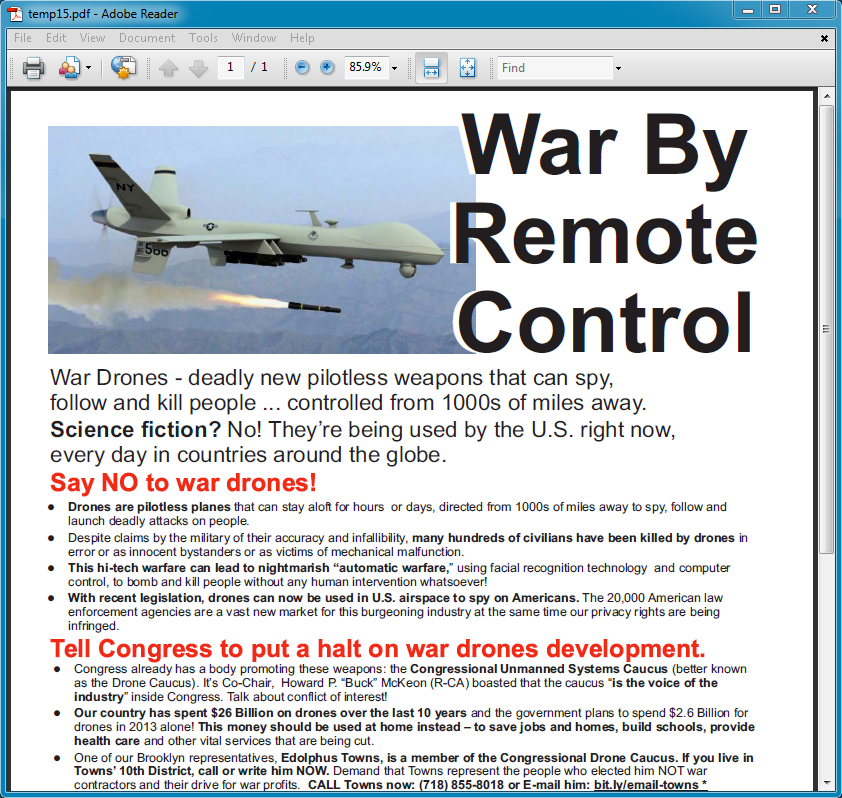
NOTE: temp15.pdf is a decoy PDF document (abour war drones) that opens on the desktop, drawing your attention away from the infection happening behind the scenes.
Click here to return to the main page.