2015-04-03 - NUCLEAR EK SENDS TESLACRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-04-03-Nuclear-EK-sends-TeslaCrypt-ransomware.pcap.zip
- 2015-04-03-malwr_com-analysis-of-TeslaCrypt-ransomware.pcap.zip
- 2015-04-03-Nuclear-EK-and-TeslaCrypt-ransomware-files.zip
NOTES:
- Today, Nuclear EK used a serveftp[.]com domain, which is normally associated with Fiesta EK.
- Those Nuclear EK URLs keep getting longer.
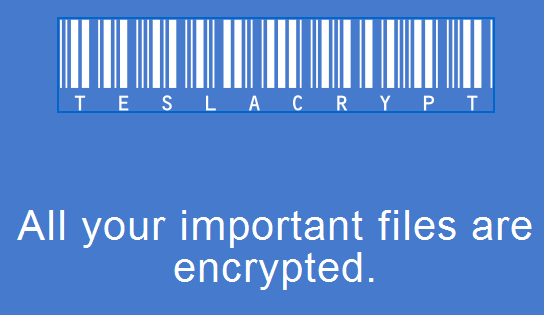
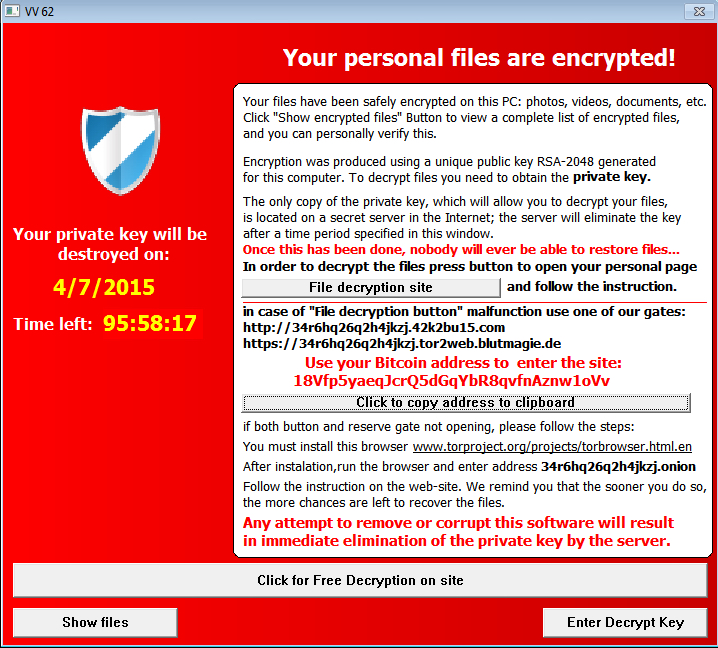
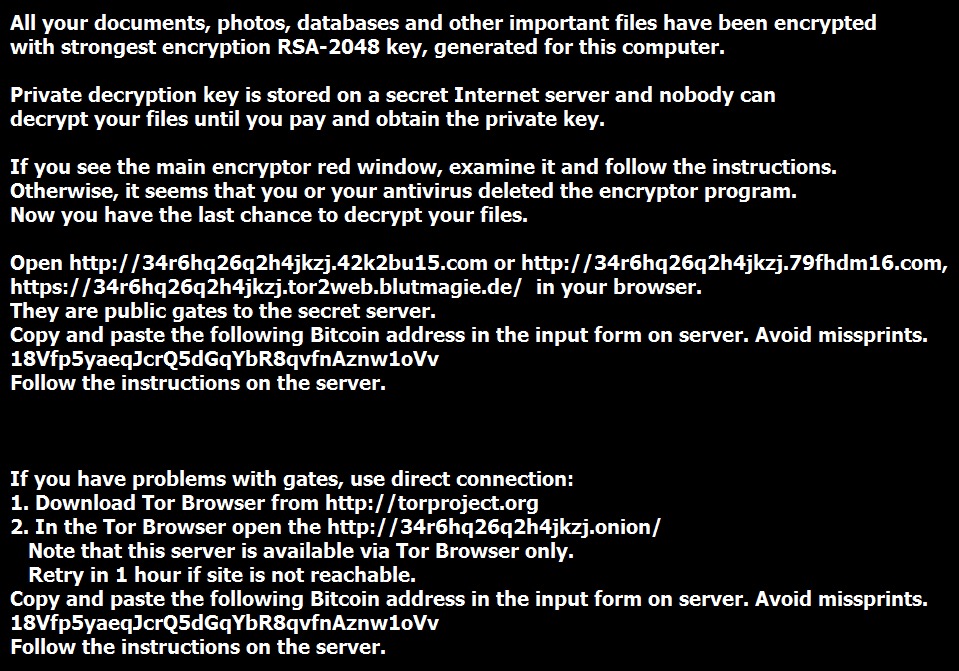
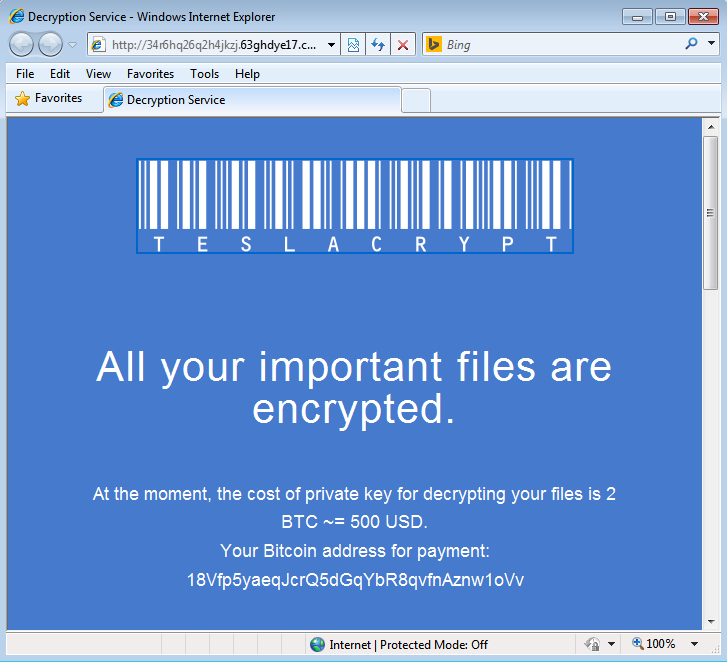
- Today's payload is TeslaCrypt ransomware, and the bitcoin address for the ransom payment is: 18Vfp5yaeqJcrQ5dGqYbR8qvfnAznw1oVv
CHAIN OF EVENTS
DATE AND TIME OF THE ACTIVITY:
- Start date/time of the pcap: 2015-04-03 15:06:03 UTC
- End date/time of the pcap: 2015-04-03 15:10:18 UTC
ASSOCIATED DOMAINS:
- 69.64.33[.]21 - pxymthldw.serveftp[.]com - Nuclear EK
- ipinfo[.]io - IP address check (not inherently malicious)
- 104.28.10[.]192 - 7tno4hib47vlep5o.63ghdye17[.]com - Initial callback by the TeslaCrypt ransomweare
- 104.28.10[.]192 - 34r6hq26q2h4jkzj.63ghdye17[.]com - Domain used when calling for the decrypt instructions
NUCLEAR EK:
- pxymthldw.serveftp[.]com - GET /E1JSDkMHGgJISUhNC0VcVVRDSEJRS0ZRAEVEF1NbCw.html
- pxymthldw.serveftp[.]com - GET /undefined
- pxymthldw.serveftp[.]com - GET /A0lERUVXAAZHCkwHGgJISUhNC0VcVVRDSEJRS0ZRAEVEF1NbC00CDx4FXgYaDgQaVQhICAQGXgEDCgUCVU1SVQI
- pxymthldw.serveftp[.]com - GET /AFhYXExBBVcDSgNIVU0HRUBMH1xAUVxQER9HXEJCA1dASR5XCVxIDwYaVwkDFwcASAINRQEAVAkEDgMBUAJIDExNLF9fSg
- pxymthldw.serveftp[.]com - GET /A0lERUVXAAZHCkwHGgJISUhNC0VcVVRDSEJRS0ZRAEVEF1NbC00CDx4FXgYaDgQaVQhICAQGXgEDCgUCVU1HUFxCA0M
- pxymthldw.serveftp[.]com - GET /AFhYXExBBVcDSgNIVU0HRUBMH1xAUVxQER9HXEJCA1dASR5XCVxIDwYaVwkDFwcASAINRQEAVAkEDgMBUAJIAUxNLF9fSg
POST-INFECTION TRAFFIC:
- ipinfo[.]io - GET /ip
- 7tno4hib47vlep5o.63ghdye17[.]com - GET /state1.php?U3ViamVjdD1QaW5nJmtleT1DMjc5MUV[long string of characters]
- 7tno4hib47vlep5o.63ghdye17[.]com - GET /state1.php?U3ViamVjdD1DcnlwdGVkJmtleT1DMjc[long string of characters]
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /?enc=18Vfp5yaeqJcrQ5dGqYbR8qvfnAznw1oVv
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /check.php
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /style.css
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /img/logo_white.png
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /img/curr.svg
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /img/decrypt.svg
- 34r6hq26q2h4jkzj.63ghdye17[.]com - GET /favicon.ico
ALERTS
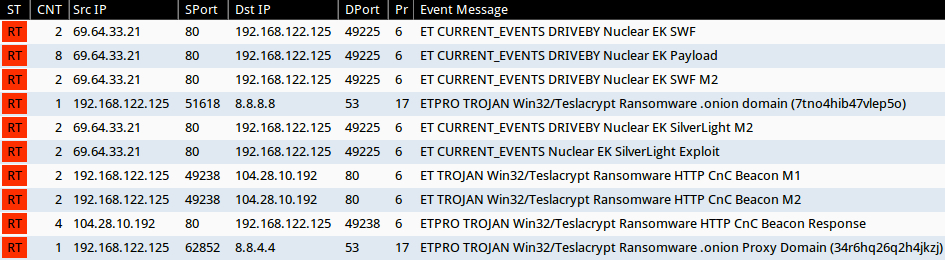
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 69.64.33[.]21 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2019845)
- 69.64.33[.]21 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020311)
- 69.64.33[.]21 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 69.64.33[.]21 port 80 - ET CURRENT_EVENTS Nuclear EK SilverLight Exploit (sid:2019917)
- 69.64.33[.]21 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SilverLight M2 (sid:2020317)
- DNS query for 7tno4hib47vlep5o.63ghdye17[.]com - ETPRO TROJAN Win32/Teslacrypt Ransomware .onion domain (7tno4hib47vlep5o) (sid:2809702)
- 104.28.10[.]192 port 80 - ET TROJAN Win32/Teslacrypt Ransomware HTTP CnC Beacon M1 (sid:2020717)
- 104.28.10[.]192 port 80 - ET TROJAN Win32/Teslacrypt Ransomware HTTP CnC Beacon M2 (sid:2020718)
- 104.28.10[.]192 port 80 - ETPRO TROJAN Win32/Teslacrypt Ransomware HTTP CnC Beacon Response (sid:2810074)
- DNS query for 34r6hq26q2h4jkzj.63ghdye17[.]com - ETPRO TROJAN Win32/Teslacrypt Ransomware .onion Proxy Domain (34r6hq26q2h4jkzj) (sid:2810075)
Significant signature hits from the Talos (Sourcefire VRT) ruleset using Snort 2.9.7.2 on Debian 7:
- 69.64.33[.]21 port 80 - [1:33981:2] EXPLOIT-KIT Nuclear exploit kit flash file download
- 104.28.10[.]192 port 80 - [1:33893:1] MALWARE-CNC Win.Trojan.TeslaCrypt outbound communication
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
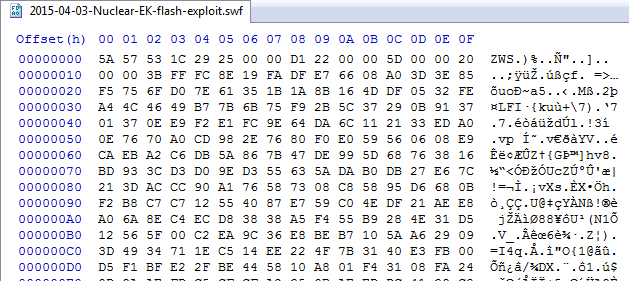
File name: 2015-04-03-Nuclear-EK-Flash-exploit.swf
File size: 8,930 bytes
MD5 hash: b7ed8635d35845d880d5e98c1568115e
Detection ratio: 0 / 42
First submission to VirusTotal: 2015-04-03 16:17:20 UTC
SILVERLIGHT EXPLOIT:
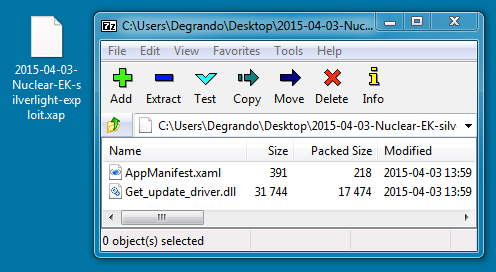
File name: 2015-04-03-Nuclear-EK-Silverlight-exploit.xap
File size: 17,940 bytes
MD5 hash: 2f6b618d8784229ff5911ece667d9320
Detection ratio: 0 / 42
First submission to VirusTotal: 2015-04-03 16:17:32 UTC
MALWARE PAYLOAD:
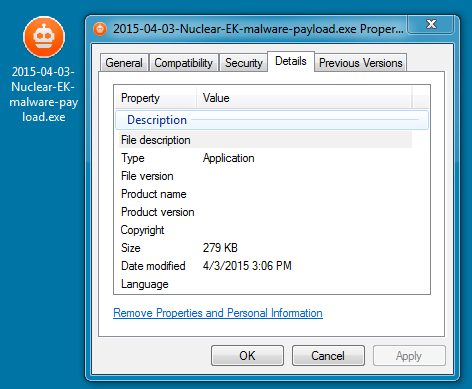
File name: 2015-04-03-Nuclear-EK-malware-payload-TeslaCrypt-ransomware.exe
File size: 285,696 bytes
MD5 hash: f3b12a197d732cda29d6d9e698ea58bf
Detection ratio: 2 / 57
First submission to VirusTotal: 2015-04-03 16:17:49 UTC
SCREENSHOTS FROM THE INFECTED HOST
Click here to return to the main page.