2015-05-07 - ANGLER EK FROM 94.242.255[.]60 DELIVERS ALPHA CRYPT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-05-07-Angler-EK-sends-Alpha-Crypt-ransomware.pcap.zip
- 2015-05-07-Angler-EK-and-Alpha-Crypt-ransomware-files.zip
NOTES:
- The latest case of Angler EK delivering Alpha Crypt ransomware.
- Alpha Crypt is a Teslacrypt clone, which already was a CryptoLocker clone.
- I previously posted a blog about this on 2015-04-30 and yesterday 2015-05-06.
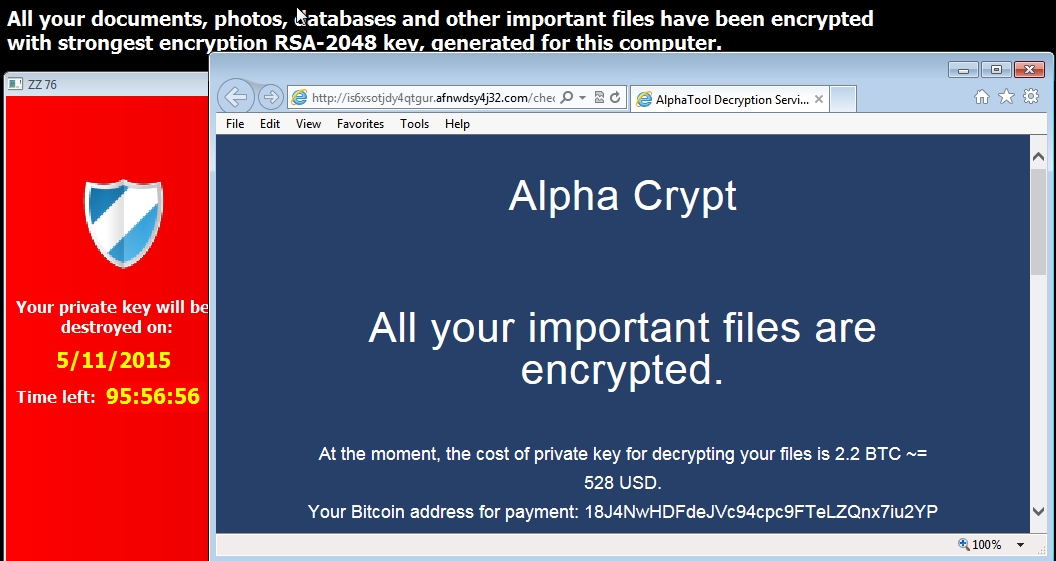
- Today's sample has the same post-infection domains as yesterday, but a different bitcoin address for the ransom payment.
- Bitcoin address for this sample's ransom payment is: 18J4NwHDFdeJVc94cpc9FTeLZQnx7iu2YP
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 94.242.255[.]60 port 80 - destinazione.grippertires[.]net - Angler EK
- 54.93.61[.]143 port 80 - ipinfo[.]io - IP address check by the malware [not inherently malicious]
- 104.28.15[.]226 port 80 - dpckd2ftmf7lelsa.afnwdsy4j32[.]com - Alpha Crypt traffic
- 104.28.14[.]226 port 80 - is6xsotjdy4qtgur.afnwdsy4j32[.]com - Alpha Crypt traffic
- 104.18.47[.]12 - is6xsotjdy4qtgur.9isernvur33[.]com - another domain from the Alpha Crypt instructions
- 192.251.226[.]206 - is6xsotjdy4qtgur.tor2web.blutmagie[.]de - another domain from the Alpha Crypt instructions
ANGLER EK:
- 2015-05-07 17:12:56 UTC - destinazione.grippertires[.]net - GET /scenically-septic-caricatured-ejects/147586249566271245
- 2015-05-07 17:12:58 UTC - destinazione.grippertires[.]net - GET /vw7-1xTy9o8XTXeans-WH-TPFNWLnQL4D73by26k99EB-Zo3
- 2015-05-07 17:13:01 UTC - destinazione.grippertires[.]net - GET /X-f--R3Zyg_ltm8haiRSbyoS8M7fTef6eZQjdcxMqAnjml_0
POST-INFECTION TRAFFIC:
- 2015-05-07 17:13:05 UTC - ipinfo[.]io - GET /ip
- 2015-05-07 17:13:06 UTC - dpckd2ftmf7lelsa.afnwdsy4j32[.]com - GET /tsdfewr2.php?U3ViamVjdD1QaW5[long string of characters]
- 2015-05-07 17:13:31 UTC - dpckd2ftmf7lelsa.afnwdsy4j32[.]com - GET /tsdfewr2.php?U3ViamVjdD1Dcnl[long string of characters]
- 2015-05-07 17:13:44 UTC - is6xsotjdy4qtgur.afnwdsy4j32[.]com - GET /?enc=18J4NwHDFdeJVc94cpc9FTeLZQnx7iu2YP
- 2015-05-07 17:13:45 UTC - is6xsotjdy4qtgur.afnwdsy4j32[.]com - GET /check.php
- 2015-05-07 17:13:46 UTC - is6xsotjdy4qtgur.afnwdsy4j32[.]com - GET /style.css
- 2015-05-07 17:13:46 UTC - is6xsotjdy4qtgur.afnwdsy4j32[.]com - GET /favicon.ico
- 2015-05-07 17:13:46 UTC - is6xsotjdy4qtgur.afnwdsy4j32[.]com - GET /img/curr.svg
- 2015-05-07 17:13:47 UTC - is6xsotjdy4qtgur.afnwdsy4j32[.]com - GET /img/decrypt.svg
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD:
File name: 2015-05-07-Alpha-Crypt-ransomware-sample.exe
File size: 275,456 bytes
MD5 hash: a08784f5691a0a8ce6249e1981dea82c
Detection ratio: 8 / 57
First submission to VirusTotal: 2015-05-07 11:27:45 UTC
Click here to return to the main page.