2015-05-11 - FARIET/PONY INFECTION FROM EMAIL LINK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Seems to be another botnet-based malicious enail campaign
- These messages have links to a zip file with Fariet/Pony disguised as a .pif file inside.
- This malware downloads (and infects a host with) Rovnix.
EXAMPLE OF THE EMAILS
SENDERS:
- Sender (spoofed): orders@aa[.]com
SCREENSHOT:
- Subject: E-Ticket ready for Order # 997880727
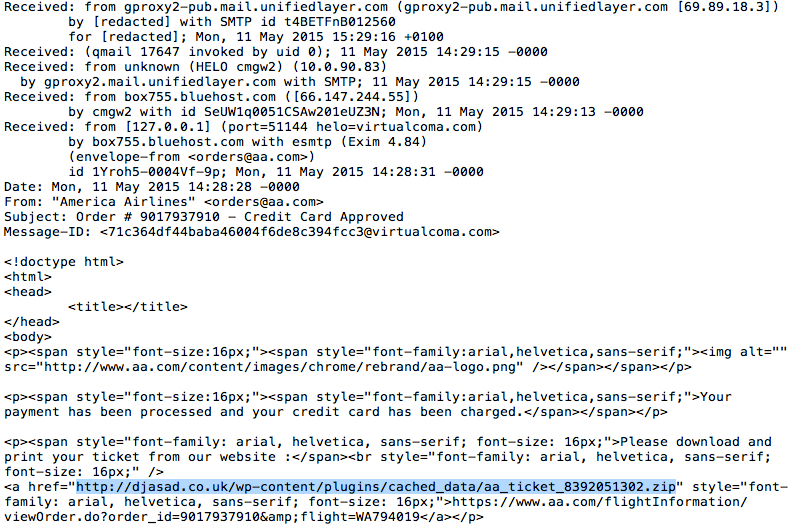
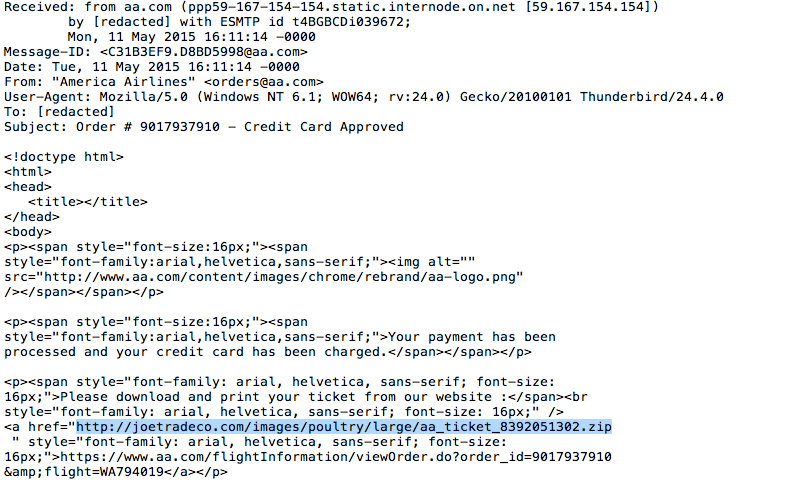
- Subject: Order # 9017937910 - Credit Card Approved
- Subject: E-Ticket ready for Order # 9017937910
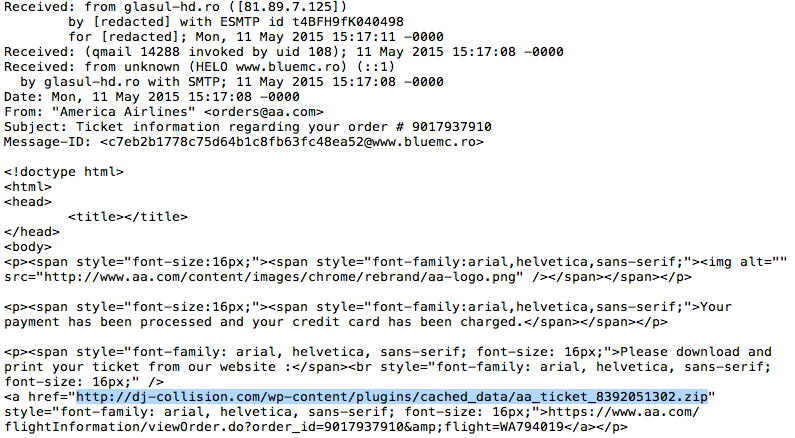
- Subject: Ticket information regarding your order # 9017937910
SCREENSHOT:
EXAMPLE OF THE MESSAGE TEXT:
Your payment has been processed and your credit card has been charged.
Please download and print your ticket from our website :
hxxps[:]//www.aa[.]com/flightInformation/viewOrder.do?order_id=9017937910&flight=WA794019
Below, you can find the order details and e-ticket information.
FLIGHT NUMBER / WA794019
DATE & TIME / May 11 2015, 13:30 CDT
DEPARTING / Washington, DC
TOTAL PRICE / $ 740.00
For more information regarding your order, contact our technical support by visiting :
hxxp[:]//www.aa[.]com/i18n/contactAA/contact-technical-support.jsp?
Thank you for flying with America Airlines.
EXAMPLES OF THE EMAIL HEADERS:
PRELIMINARY MALWARE ANALYSIS
FIRST SAMPLE:
Link to malware from the enauk:
- dugunorganizasyonu[.]co - GET /wp-content/plugins/cached_data/aa_ticket_9017937910.zip
Extracted File: aa_ticket_9017937910.pif (Fareit/Pony) - MD5 hash: f21072077e88c74b9b6d67f81ae63d84
Second-stage download: w1.exe (Rovnix) - MD5 hash: 3f11c42687d09d4a56c715f671143a58
Traffic from malware analysis tools:
- 198.57.196[.]20 - dev.mariocorp[.]com - GET /wp-content/plugins/cached_data/w1.exe HTTP/1.0
- 46.249.205[.]12 - dev.wbiz[.]it - GET /wp-content/plugins/cached_data/w1.exe HTTP/1.0
- 192.185.73[.]98 - diamondnailsvalpo[.]com - GET /wp-content/plugins/cached_data/w1.exe HTTP/1.0
- 62.76.179[.]132 - docscountry[.]com - POST /gate.php HTTP/1.0
- 91.217.90[.]137 - manterinvoice[.]com - POST /gate.php HTTP/1.0
- 46.4.145[.]94 - sampledocstrash[.]com - POST /gate.php HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /host.dat HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /101/hosts.dat HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /101/list32.dat HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /101/3257F7F8 HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /101/EB4E2654 HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /101/B06139B1 HTTP/1.0
- 107.181.174[.129 - heckwassleftran[.]ru - GET /101/1880376902_32.dat HTTP/1.0
SECOND SAMPLE
Link to malware from the enauk:
- djasad[.]co[.]uk - GET /wp-content/plugins/cached_data/aa_ticket_8392051302.zip/li>
- dj-collision[.]com - GET /wp-content/plugins/cached_data/aa_ticket_8392051302.zip/li>
- docitachocolates[.]com[.]br - GET /wp-content/plugins/cached_data/aa_ticket_8392051302.zip/li>
- joetradeco[.]com - GET /images/poultry/large/aa_ticket_8392051302.zip
Another link to malware from email:
- Link from email: www.danielbellini[.]it - GET /zvfjtrkw.php
- Goes to: bit[.]ly - GET /1F90aL5
- Goes to: (https) updateserver3.azurewebsites[.]net - GET /lander.php?id=10475
Extracted file: aa_ticket_8392051302.pif or aa_ticket_489965107764.pif (Fareit/Pony) - MD5 hash: 379c67ae879872d3fa0b601892c59605
Second-stage download: w2.exe (Rovnix) - MD5 hash: 6eb761ea46a40ad72018d3cee915c4cd
Traffic from malware analysis tools:
- 62.76.179[.]132 - docscountry[.]com - POST /gate.php HTTP/1.0
- 91.217.90[.]137 - manterinvoice[.]com - POST /gate.php HTTP/1.0
- 46.4.145[.]94 - sampledocstrash[.]com - POST /gate.php HTTP/1.0
- 50.62.52[.]1 - diamondlogosacademy[.]org - GET /wp-content/plugins/cached_data/w2.exe HTTP/1.0
- 185.36.134[.]3 - dierenkliniekpendrecht[.]nl - GET /wp-content/plugins/cached_data/w2.exe HTTP/1.0
- 81.0.104[.]144 - discoverbalaton[.]com - GET /wp-content/plugins/cached_data/w2.exe HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /host.dat HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /101/hosts.dat HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /101/list32.dat HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /101/3257F7F8 HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /101/EB4E2654 HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /101/B06139B1 HTTP/1.0
- 107.181.174[.]129 - heckwassleftran[.]ru - GET /101/1880376902_32.dat HTTP/1.0
INFECTION TRAFFIC
ASSOCIATED DOMAINS:
- 62.76.179[.]132 - docscountry[.]com - Pony/Fareit checkin
- 50.62.52[.]1 port 80 - diamondlogosacademy[.]org - request to download follow-up malware (Rovnix)
- 81.177.22[.]189 port 80 - ip.xss[.]ru - post-infection traffic (Rovnix)
- 107.181.174[.]129 port 80 - heckwassleftran[.]ru - post-infection traffic (Rovnix)
TRAFFIC FROM AN INFECTED HOST THAT WAS LEFT ALONE FOR A WHILE:
- 2015-05-11 16:45:06 UTC - docscountry[.]com - POST /gate.php HTTP/1.0
- 2015-05-11 16:45:09 UTC - diamondlogosacademy[.]org - GET /wp-content/plugins/cached_data/w2.exe HTTP/1.0
- 2015-05-11 16:45:25 UTC - heckwassleftran[.]ru - GET /host.dat HTTP/1.0
- 2015-05-11 16:45:31 UTC - heckwassleftran[.]ru - GET /101/hosts.dat HTTP/1.0
- 2015-05-11 16:45:41 UTC - heckwassleftran[.]ru - GET /101/list64.dat HTTP/1.0
- 2015-05-11 16:45:55 UTC - heckwassleftran[.]ru - GET /101/7B28207A HTTP/1.0
- 2015-05-11 16:46:02 UTC - heckwassleftran[.]ru - GET /101/0A14CF25 HTTP/1.0
- 2015-05-11 16:46:46 UTC - heckwassleftran[.]ru - GET /101/2325E690 HTTP/1.0
- 2015-05-11 16:46:52 UTC - heckwassleftran[.]ru - GET /101/1086666136_64.dat HTTP/1.0
- 2015-05-11 16:48:01 UTC - ip.xss[.]ru - GET / HTTP/1.0
- 2015-05-11 16:48:04 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=log HTTP/1.0
- 2015-05-11 16:48:07 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cfg&crc32=0 HTTP/1.0
- 2015-05-11 16:48:10 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:49:13 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:50:16 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:51:19 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:52:21 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:53:24 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:54:27 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:55:30 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:56:32 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:57:35 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:58:38 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 16:59:41 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:00:46 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:01:49 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:02:52 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:03:54 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:04:57 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:06:00 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:07:03 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:08:06 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:09:09 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:10:11 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
- 2015-05-11 17:11:14 UTC - heckwassleftran[.]ru POST /vbulletin/post.php?qu=cmd HTTP/1.0
ALERTS
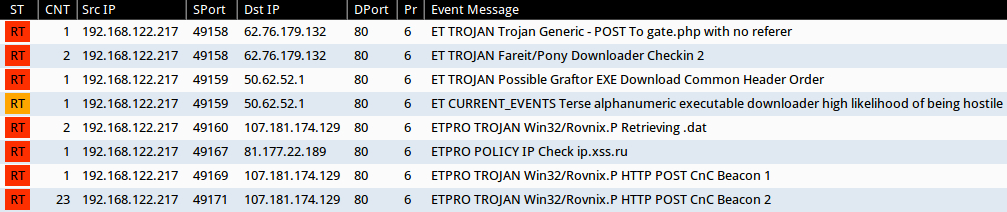
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 62.76.179[.]132 port 80 - ET TROJAN Trojan Generic - POST To gate.php with no referer (sid:2017930)
- 62.76.179[.]132 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- 50.62.52[.]1 port 80 - ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
- 50.62.52[.]1 port 80 - ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile (sid:2019714)
- 107.181.174[.]129 port 80 - ETPRO TROJAN Win32/Rovnix.P Retrieving .dat (sid:2810756)
- 107.181.174[.]129 port 80 - ETPRO TROJAN Win32/Rovnix.P HTTP POST CnC Beacon 1 (sid:2810758)
- 107.181.174[.]129 port 80 - ETPRO TROJAN Win32/Rovnix.P HTTP POST CnC Beacon 2 (sid:2810759)
Talos (Snort subrscriber) ruleset from Snort 2.9.6.2 on Debian 7:
- 62.76.179[.]132 port 80 - [1:27919:3] MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration
- 50.62.52[.]1 port 80 - [1:27918:2] MALWARE-CNC Win.Trojan.Zeus variant outbound connection
- 50.62.52[.]1 port 80 - [1:15306:22] FILE-EXECUTABLE Portable Executable binary file magic detected
Click here to return to the main page.