2015-05-14 - ANGLER EK DELIVERS RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- More ransomware from Angler EK...
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 144.76.161[.]38 port 80 - improvisaciondemarilhteet.eliteplusbp[.]com - Angler EK
- 54.93.182[.]214 port 80 - ipinfo[.]io - IP check by the malware [not inherently malicious]
- 104.27.143[.]176 port 80 - 24u4jf7s4regu6hn.fenaow48fn42[.]com - post-infection traffic
- 104.27.142[.]176 port 80 - iq3ahijcfeont3xx.fenaow48fn42[.]com - post-infection traffic
- 104.28.25[.]237 port 80 - iq3ahijcfeont3xx.sm4i8smr3f43[.]com - post-infection traffic
- 192.251.226[.]206 port 443 - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - post-infection traffic
ANGLER EK:
- 2015-05-14 14:28:18 UTC - improvisaciondemarilhteet.eliteplusbp[.]com - GET /indexing_raspberries_rejuvenation_sushis/415213137352185210
- 2015-05-14 14:28:22 UTC - improvisaciondemarilhteet.eliteplusbp[.]com - GET /IgewyT-H4AUwZK0MoXRsPJd4BF1n_J-v0SOdbYmqqElESEYq
- 2015-05-14 14:28:24 UTC - improvisaciondemarilhteet.eliteplusbp[.]com - GET /pUmOkg3ZnV4ZxHpcKTFSUCKaad5pKGJlO6FkHjJAxetpWIMU
POST-INFECTION TRAFFIC:
- 2015-05-14 14:28:29 UTC - ipinfo[.]io - GET /ip
- 2015-05-14 14:28:30 UTC - 24u4jf7s4regu6hn.fenaow48fn42[.]com - GET /ping.php?U3ViamVjdD1QaW5nJmtleT05Nzk[long string of characters]
- 2015-05-14 14:28:53 UTC - 24u4jf7s4regu6hn.fenaow48fn42[.]com - GET /ping.php?U3ViamVjdD1DcnlwdGVkJmtleT0[long string of characters]
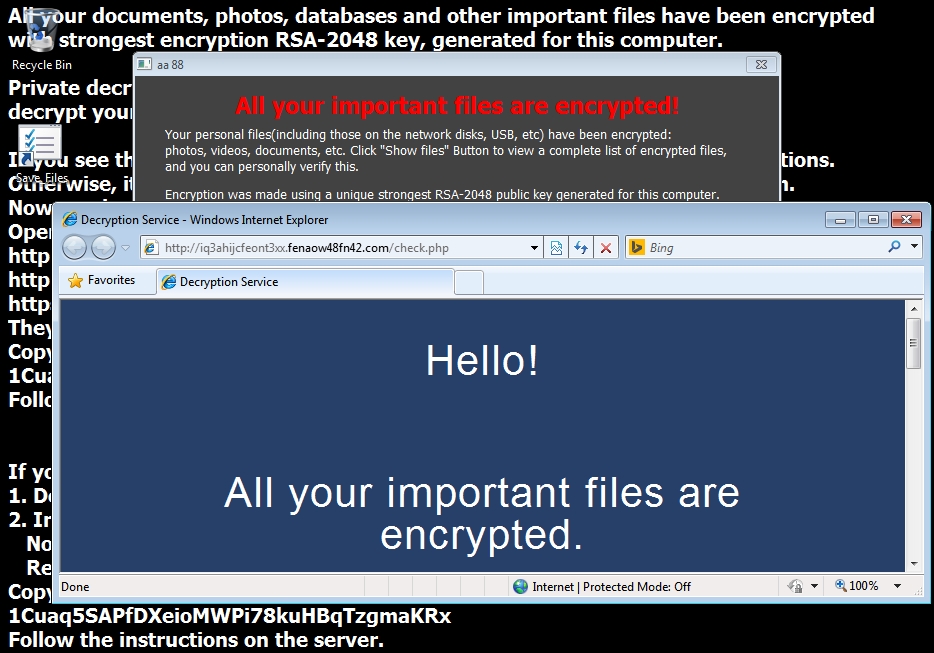
- 2015-05-14 14:28:59 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /?enc=1Cuaq5SAPfDXeioMWPi78kuHBqTzgmaKRx
- 2015-05-14 14:29:01 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /check.php
- 2015-05-14 14:29:02 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /style.css
- 2015-05-14 14:29:02 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /style.css
- 2015-05-14 14:29:03 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /img/curr.svg
- 2015-05-14 14:29:03 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /img/decrypt.svg
- 2015-05-14 14:29:04 UTC - iq3ahijcfeont3xx.fenaow48fn42[.]com - GET /favicon.ico
- 2015-05-14 14:29:36 UTC - iq3ahijcfeont3xx.sm4i8smr3f43[.]com - GET /
- 2015-05-14 14:29:38 UTC - iq3ahijcfeont3xx.sm4i8smr3f43[.]com - GET /style.css
- 2015-05-14 14:29:39 UTC - iq3ahijcfeont3xx.sm4i8smr3f43[.]com - GET /img/base.svg
- 2015-05-14 14:29:39 UTC - iq3ahijcfeont3xx.sm4i8smr3f43[.]com - GET /favicon.ico
- 2015-05-14 14:29:42 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-14 14:29:45 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-14 14:29:46 UTC - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic
PRELIMINARY MALWARE ANALYSIS
RANSOMWARE:
File name: C:\Users\username\AppData\Local\hfxtnsu.exe
File size: 383,488 bytes
MD5 hash: 59bb43ab2239baf5721807ec606d5397
Detection ratio: 3 / 57
First submission to VirusTotal: 2015-05-14 15:03:40 UTC
Click here to return to the main page.