2015-05-25 - ANGLER EK DELIVERS RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-05-25-Angler-EK-sends-ransomware-traffic.pcap.zip
- 2015-05-25-Angler-EK-and-ransomware-files.zip
NOTES:
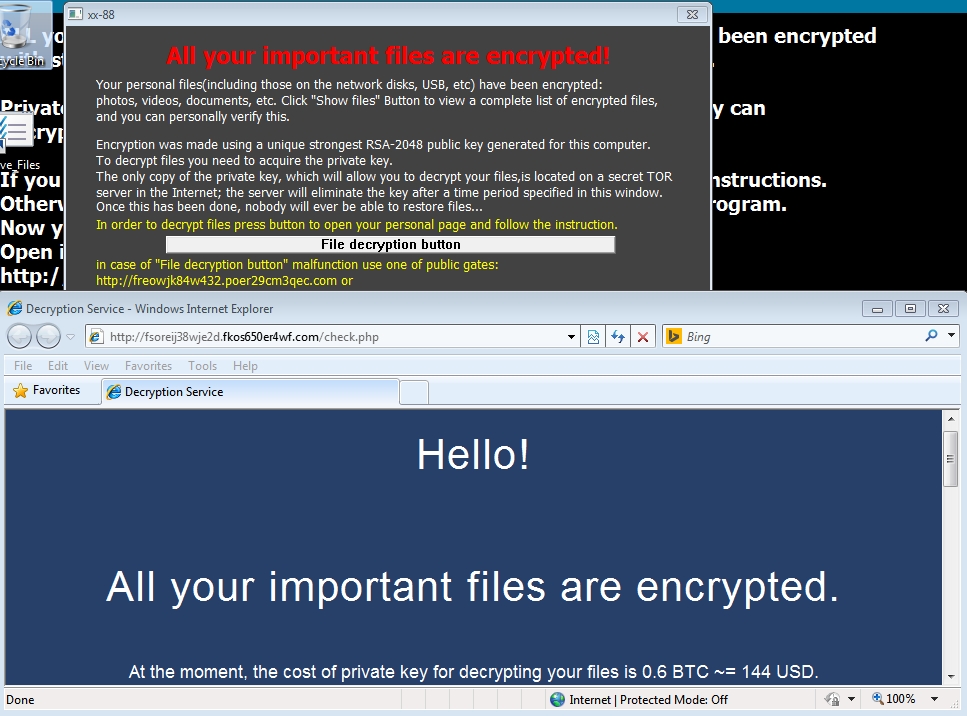
- More traffic from Angler exploit kit (EK) sending this TelsaCrypt/Alpha Crypt variant...
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.162.79[.]42 port 80 - geblevenen.cusumanovisioncenter[.]com - Angler EK
- 54.93.182[.]214 port 80 - ipinfo[.]io - Malware checking for the infected host's IP address
- 104.24.109[.]143 port 80 - aeo29sdw45ndf4.fkos650er4wf[.]com - Post-infection checkin by the malware
- 104.24.109[.]143 port 80 - fsoreij38wje2d.fkos650er4wf[.]com - Browser traffic after using "File decryption button"
- 104.27.139[.]38 port 80 - freowjk84w432.poer29cm3qec[.]com - Browser traffic when checking first public gate for decrypt instructions
- 192.251.226[.]206 port 443 - tlunjscxn5n76iyz.tor2web.blutmagie[.]de - Browser traffic when checking second public gate for decrypt instructions
ANGLER EK:
- 2015-05-25 14:10:43 UTC - geblevenen.cusumanovisioncenter[.]com - GET /violators_perinatal_lance_sufficing/955294902062826247
- 2015-05-25 14:10:47 UTC - geblevenen.cusumanovisioncenter[.]com - GET /MKRk8ogbQCbYQuqQ_SNgoFQj41TNjvPY-09F7O8na4NYDPFv
- 2015-05-25 14:10:51 UTC - geblevenen.cusumanovisioncenter[.]com - GET /rYfC_9JSzg4ThZeMCe0f_oB776apxCGyGOQP_ESv4gOcjOHh
- 2015-05-25 14:10:55 UTC - geblevenen.cusumanovisioncenter[.]com - GET /EcVwNuxSvmnCLwBr_vmtDjdnw-Fu_HmH27GLVVArqSJyN1wg
POST-INFECTION TRAFFIC:
- 2015-05-25 14:10:52 UTC - ipinfo[.]io - GET /ip
- 2015-05-25 14:10:53 UTC - aeo29sdw45ndf4.fkos650er4wf[.]com - GET /ping1.php?EBBA0FA36E85154E0EF48091B[long string of characters]
- 2015-05-25 14:10:59 UTC - aeo29sdw45ndf4.fkos650er4wf[.]com - GET /ping1.php?A6D121D21FBD4D853912A65FA[long string of characters]
- 2015-05-25 14:11:20 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /?enc=1HBNWQ8Y8dw872kg2bkkUqnSdmyzq2ATnd
- 2015-05-25 14:11:22 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /check.php
- 2015-05-25 14:11:23 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /style.css
- 2015-05-25 14:11:23 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /style.css
- 2015-05-25 14:11:23 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /img/curr.svg
- 2015-05-25 14:11:23 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /img/decrypt.svg
- 2015-05-25 14:11:25 UTC - fsoreij38wje2d.fkos650er4wf[.]com - GET /favicon.ico
- 2015-05-25 14:11:32 UTC - freowjk84w432.poer29cm3qec[.]com - GET /
- 2015-05-25 14:11:34 UTC - freowjk84w432.poer29cm3qec[.]com - GET /style.css
- 2015-05-25 14:11:34 UTC - freowjk84w432.poer29cm3qec[.]com - GET /style.css
- 2015-05-25 14:11:35 UTC - freowjk84w432.poer29cm3qec[.]com - GET /img/base.svg
- 2015-05-25 14:11:36 UTC - freowjk84w432.poer29cm3qec[.]com - GET /favicon.ico
- 2015-05-25 14:11:39 UTC - tlunjscxn5n76iyz.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-25 14:11:41 UTC - tlunjscxn5n76iyz.tor2web.blutmagie[.]de - HTTPS traffic
- 2015-05-25 14:11:41 UTC - tlunjscxn5n76iyz.tor2web.blutmagie[.]de - HTTPS traffic
ARTIFACTS LEFT FROM THE MALWARE INFECTION
- C:\Users\username\AppData\Roaming\rmcglnrra.exe (ransomware - filename is random characters before .exe)
- C:\Users\username\AppData\Roaming\storage.bin
- C:\Users\username\AppData\Roaming\log.html
- Various locations: help_restore_files_mbjmj.txt
Click here to return to the main page.