2015-06-05 - ANGLER EK FROM 209.133.200[.]228 SENDS BEDEP AND NECURS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 89.39.144[.]155 port 80 - flash.casapiti[.]com[.]ar - Redirect/gate pointing to Angler EK
- 209.133.200[.]228 port 80 - haitallistakinaglaozonia.renteriaonline[.]com - Angler EK
- 83.149.127[.]8 port 80 - pigdoauhpaf6[.]com - Angler EK post-infection: Bedep
- 91.200.14[.]56 port 80 - 91.200.14[.]56 - Angler EK post-infection: Necurs
- 212.47.214[.]114 port 80 - 212.47.214[.]114 - Angler EK post-infection: Necurs
REDIRECT/GATE:
- 2015-06-05 15:09:59 UTC - flash.casapiti[.]com[.]ar - GET /js/view.js
ANGLER EK:
- 2015-06-05 15:10:01 UTC - haitallistakinaglaozonia.renteriaonline[.]com - GET /rashest_comfortably_bustle_reciprocal/310521150558154439
- 2015-06-05 15:10:05 UTC - haitallistakinaglaozonia.renteriaonline[.]com - GET /hkk9BuO9O9DUTeULcBxqvcQ7v5DkzCvC_RtKyWooU6n1qXEs.jsscript
- 2015-06-05 15:10:10 UTC - haitallistakinaglaozonia.renteriaonline[.]com - GET /MPQTRTuVP9jLogEBd7pL4GrYV6g5zzfBtg1bO4S6XjgDcE3W.aspnet
POST-INFECTION TRAFFIC:
- 2015-06-05 15:10:10 UTC - www.earthtools[.]org - GET /timezone-1.1/-32.71056/-121.57942
- 2015-06-05 15:10:11 UTC - www.ecb.europa[.]eu - GET /stats/eurofxref/eurofxref-hist-90d.xml?66ad8f5f8569954b6ed6931b6e63368c
- 2015-06-05 15:10:11 UTC - DNS query for: qdwkzufphsecknfaq[.]com (did not resolve)
- 2015-06-05 15:10:12 UTC - DNS query for: lqflroigrgcodemu[.]com (did not resolve)
- 2015-06-05 15:10:12 UTC - DNS query for: stxfwvzjfbfyg[.]com (did not resolve)
- 2015-06-05 15:10:12 UTC - DNS query for: xanwfvqgegrma[.]com (did not resolve)
- 2015-06-05 15:10:13 UTC - DNS query for: uenbmzupsizpsxujv[.]com (did not resolve)
- 2015-06-05 15:10:13 UTC - DNS query for: hpximcxemmdx9q[.]com (did not resolve)
- 2015-06-05 15:10:13 UTC - DNS query for: xdjwjcszwsgm4c[.]com (did not resolve)
- 2015-06-05 15:10:14 UTC - DNS query for: peaijgxhhssoqwiakh[.]com (did not resolve)
- 2015-06-05 15:10:14 UTC - DNS query for: khbkggvnhrdnsxmw[.]com (did not resolve)
- 2015-06-05 15:10:14 UTC - DNS query for: xnpqjuucczdk[.]com (did not resolve)
- 2015-06-05 15:10:14 UTC - DNS query for: vivnesxutjhbofq7[.]com (did not resolve)
- 2015-06-05 15:10:15 UTC - DNS query for: gpkoyqqypjqmlrrs9[.]com (did not resolve)
- 2015-06-05 15:10:15 UTC - DNS query for: rdjxvltnjcy3[.]com (did not resolve)
- 2015-06-05 15:10:15 UTC - DNS query for: ykqjnlcyzub2[.]com (did not resolve)
- 2015-06-05 15:10:15 UTC - DNS query for: yjmpssosqxtriitq[.]com (did not resolve)
- 2015-06-05 15:10:16 UTC - DNS query for: fvxmvtxpknzqdugub[.]com (did not resolve)
- 2015-06-05 15:10:17 UTC - pigdoauhpaf6[.]com - POST /calendar.php
- 2015-06-05 15:10:19 UTC - pigdoauhpaf6[.]com - POST /calendar.php
- 2015-06-05 15:10:26 UTC - TCP connection to 134.170.185[.]46 port 80 (after DNS query for: microsoft[.]com) but no content sent
- 2015-06-05 15:10:27 UTC - DNS query for: xlcvpjwgyg[.]com (did not resolve)
- 2015-06-05 15:10:27 UTC - DNS query for: vxaibdgnlyoldzq[.]com (did not resolve)
- 2015-06-05 15:10:27 UTC - DNS query for: sdjhdvfepfdhoh[.]com (did not resolve)
- 2015-06-05 15:10:27 UTC - DNS query for: aanlnugelqha[.]com (did not resolve)
- 2015-06-05 15:10:27 UTC - UDP traffic to: 201.231.199[.]3 - Source port: 7117 - Destination port: 6771
- 2015-06-05 15:10:29 UTC - DNS query for: npkxghmoru[.]biz (did not resolve)
- 2015-06-05 15:10:37 UTC - UDP traffic to: 89.205.63[.]43 - Source port: 7117 - Destination port: 5950
- 2015-06-05 15:10:42 UTC - UDP traffic to: 217.144.26[.]159 - Source port: 7117 - Destination port: 6548
- 2015-06-05 15:10:43 UTC - pigdoauhpaf6[.]com - POST /include/functions_misc.php
- 2015-06-05 15:10:47 UTC - UDP traffic to: 77.239.86[.]127 - Source port: 7117 - Destination port: 29112
- 2015-06-05 15:10:52 UTC - UDP traffic to: 200.60.41[.]150 - Source port: 7117 - Destination port: 30007 (return traffic noted)
- 2015-06-05 15:10:58 UTC - UDP traffic to: 181.171.228[.]134 - Source port: 7117 - Destination port: 4754
- 2015-06-05 15:10:58 UTC - 212.47.214[.]114 - POST /forum/db.php
- 2015-06-05 15:11:03 UTC - UDP traffic to: 190.18.142[.]81 - Source port: 7117 - Destination port: 15640
- 2015-06-05 15:11:08 UTC - UDP traffic to: 186.115.202[.]202 - Source port: 7117 - Destination port: 26507
- 2015-06-05 15:11:08 UTC - 91.200.14[.]56 - POST /forum/db.php
- 2015-06-05 15:11:10 UTC - 91.200.14[.]56 - POST /forum/db.php
- 2015-06-05 15:11:11 UTC - 91.200.14[.]56 - POST /forum/db.php
MALWARE
MALWARE FOUND ON THE INFECTED HOST:
- C:\Windows\Installer\{[random number]}\syshost.exe
- C:\Windows\System32\Drivers\[random number].sys
IMAGES
Edited screenshot of Wireshark showing the traffic:
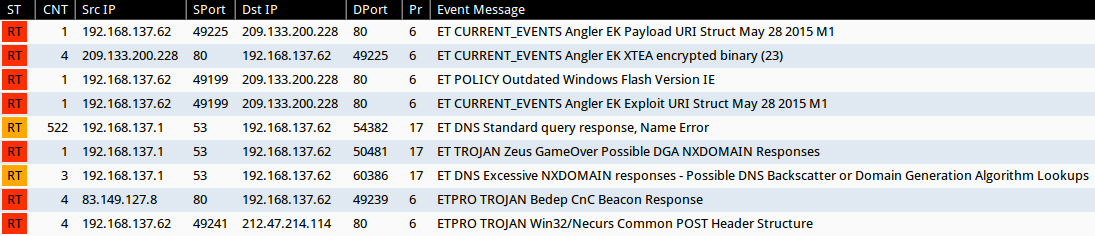
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
Click here to return to the main page.

