2015-06-08 - ANGLER EK - MORE CHANGES IN TRAFFIC PATTERNS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-06-08-Angler-EK-sends-Vawtrak.pcap.zip
- 2015-06-08-Angler-EK-and-Vawtrak-malware-and-artifacts.zip
NOTES:
- Been seeing a lot of cases where Angler EK is sending CryptoWall 3.0 ransomware as the payload today.
- This one sent Vawtrak, though.
- URL patterns for Angler EK changed when I checked this morning.
- I forgot to get a copy of the Flash banner redirect that led to Angler (can't extract it from the pcap, because some data is missing).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 194.15.126[.]7 port 80 - joans[.]ga - Flash banner ad leading to Angler EK
- 131.72.136[.]114 port 80 - fit.everylittlething[.]xyz - Angler EK
- 91.121.54[.]20 port 80 - transfercom[.]net - Vawtrak callback traffic
FLASH AD REDIRECT:
- 2015-06-08 13:33:09 UTC - joans[.]ga - GET /banner.php?sid=425AB2B199B62D037FB459B962D07E2D17AE45F4F4EF707357
- 2015-06-08 13:33:12 UTC - joans[.]ga - GET /blog.php?id=425AB2B199B62D037FB459B962D07E2D17AE45F4F4EF707357
ANGLER EK:
- 2015-06-08 13:33:13 UTC - fit.everylittlething[.]xyz - GET /marginalisation-gunboat-locales-bristle/11101444414174830
- 2015-06-08 13:33:15 UTC - fit.everylittlething[.]xyz - GET /0fPTVpcOtNMOnt3aluOCuN-QmBW8PDBMwJGbKE4pNhDM_Gxl.pycharm?ten=VIMnR
- 2015-06-08 13:33:18 UTC - fit.everylittlething[.]xyz - GET /sbQAMHvfwBzZpKfMIrXCwZ4b1CmuBmen3WH-c-76hG51d3Rn.cppbin?four=FQVZC
&seven=W47VAT5tRs&nine=28122299&one=XCjvfp&ten=279573
POST-INFECTION TRAFFIC:
- 2015-06-08 13:38:56 UTC - transfercom[.]net - POST /collection/00000050/00/8EBFD947
- 2015-06-08 13:38:57 UTC - transfercom[.]net - POST /collection/00000050/02/8EBFD947
- 2015-06-08 13:39:14 UTC - transfercom[.]net - POST /collection/00000050/02/8EBFD947
ALERTS
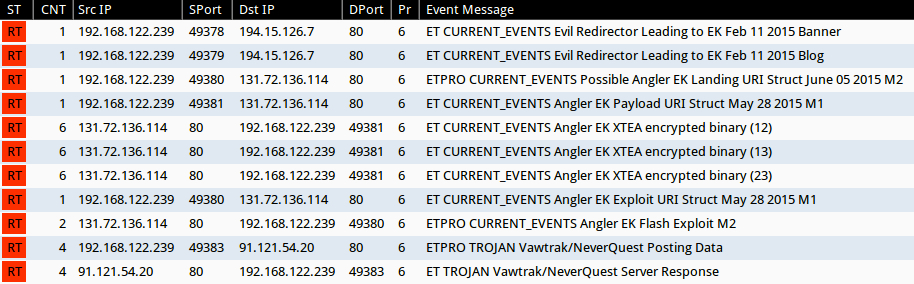
Signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion (without ET POLICY or ET INFO events):
- 194.15.126[.]7 port 80 - ET CURRENT_EVENTS Evil Redirector Leading to EK Feb 11 2015 Banner (sid:2020408)
- 194.15.126[.]7 port 80 - ET CURRENT_EVENTS Evil Redirector Leading to EK Feb 11 2015 Blog (sid:2020409)
- 131.72.136[.]114 port 80 - ETPRO CURRENT_EVENTS Possible Angler EK Landing URI Struct June 05 2015 M2 (sid:2811274)
- 131.72.136[.]114 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (12) (sid:2020591)
- 131.72.136[.]114 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (13) (sid:2020592)
- 131.72.136[.]114 port 80 - ET CURRENT_EVENTS Angler EK XTEA encrypted binary (23) (sid:2021059)
- 131.72.136[.]114 port 80 - ET CURRENT_EVENTS Angler EK Payload URI Struct May 28 2015 M1 (sid:2021158)
- 131.72.136[.]114 port 80 - ET CURRENT_EVENTS Angler EK Exploit URI Struct May 28 2015 M1 (sid:2021157)
- 131.72.136[.]114 port 80 - ETPRO CURRENT_EVENTS Angler EK Flash Exploit M2 (sid:2811284)
- 91.121.54[.]20 port 80 - ETPRO TROJAN Vawtrak/NeverQuest Posting Data (sid:2809464)
- 91.121.54[.]20 port 80 - ET TROJAN Vawtrak/NeverQuest Server Response (sid:2019499)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-06-08-Angler-EK-flash-exploit.swf
File size: 55,364 bytes
MD5 hash: e1ee52baee1ac7fe876cf6581e669b6c
Detection ratio: 1 / 57
First submission to VirusTotal: 2015-06-08 07:42:59 UTC
MALWARE PAYLOAD:
File name: 2015-06-08-Angler-EK-malware-payload.exe
File size: 371,060 bytes
MD5 hash: d5cd69ad84cc4381275d93c400702f2f
Detection ratio: 1 / 57
First submission to VirusTotal: 2015-06-08 14:03:22 UTC
VAWTRAK FOUND ON INFECTED HOST:
File name: C:\ProgramData\DajaXunuq\PupqUhgo.pmh
File size: 284,582 bytes
MD5 hash: a0141ac093a4f2bb64e8da3829d4b8a8
Detection ratio: 3 / 57
First submission to VirusTotal: 2015-06-08 14:03:48 UTCHKEY_CURRENT_USER\Sofware\Microsoft\Windows\CurrentVersion\Run
Value name: DajaXunuq
Type: REG_SZ
Data: regsvr32.exe "C:\ProgramData\DajaXunuq\PupqUhgo.pmh"
Click here to return to the main page.