2015-07-08 - ANGLER EK SENDS CRYPTOWALL 3.0 RANSOMWARE - 2 EXAMPLES
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-07-08-Angler-EK-sends-CryptoWall-3.0-ransomware-2-pcaps.zip
- 2015-07-08-Angler-EK-and-CryptoWall-3.0-ransomware-files.zip
NOTES:
- Generated 2 separate instances of Angler EK within 30 minutes of each other
- The malware payload in both cases (CryptoWall 3.0 ransomware) had different file sizes and file hashes.
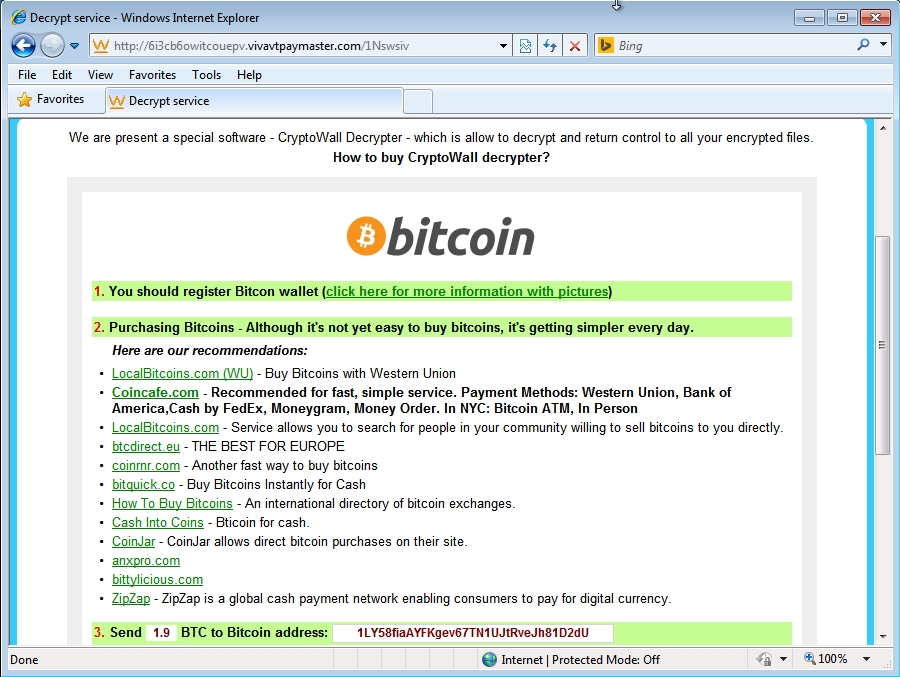
- Bitcoin address for the CryptoWall 3.0 ransomware traffic in both examples was: 1LY58fiaAYFKgev67TN1UJtRveJh81D2dU
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 176.9.245[.]141 port 80 - stairstepped-waibula.piklamp[.]nl - Angler EK (example 1)
- 160.153.0[.]1 port 80 - aslikarabulut[.]com - CrytpoWall 3.0 ransomware check-in (example 1)
- 176.9.245[.]141 port 80 - zastapiony.piklamp[.]nl - Angler EK (example 2)
- 173.201.244[.]70 port 80 - bfiproductsinc[.]com - CrytpoWall 3.0 ransomware check-in (example 2)
- 95.163.121[.]228 port 80 - 6i3cb6owitcouepv.myportopay[.]com - Domain for decrypt instructions (both examples)
- 95.163.121[.]228 port 80 - 6i3cb6owitcouepv.vivavtpaymaster[.]com - Domain for decrypt instructions (both examples)
- 6i3cb6owitcouepv.misterpayall[.]com - Another domain listed in decrypt instructions (did not resolve to an IP)
- 6i3cb6owitcouepv.fraspartypay[.]com - Another domain listed in decrypt instructions (did not resolve to an IP)
ANGLER EK - 2015-07-08 at 15:42 UTC:
- 2015-07-08 15:42:40 UTC - stairstepped-waibula.piklamp[.]nl - GET /viewtopic.php?t=767&m=1&me=119&gx=898
- 2015-07-08 15:42:42 UTC - stairstepped-waibula.piklamp[.]nl - GET /voice.edge?real=hw0zQPZvT&break=aGX&test=7Ly&product=e3W3MntghQ&house=fepy&
federal=f5Fv&world=JyK6A_boiNZ3fEE
- 2015-07-08 15:42:45 UTC - stairstepped-waibula.piklamp[.]nl - GET /which.edge?contribute=&help=1duomCSX&lead=&sale=whUN&announce=wG2SeoO&
after=ogKHl&administration=-upUCzX_i5&more=&increase=JPXvykCY&study=5L3KF6
- 2015-07-08 15:42:46 UTC - stairstepped-waibula.piklamp[.]nl - GET /love.zul?length=&must=V0Rbm_&create=j4KdVjz&room=UMbZVXNEE&enough=jxnTPZ8&
under=D6RPZXha&instance=_wKJJuaGjK&mind=j
IP-ADDR.ES IP CHECK & CRYPTOWALL 3.0 RANSOMWARE CHECK-IN:
- 2015-07-08 15:42:48 UTC - ip-addr[.]es - GET /
- 2015-07-08 15:42:48 UTC - aslikarabulut[.]com - POST /wp-content/plugins/aa.php?t=x55c411nagl75
- 2015-07-08 15:42:51 UTC - aslikarabulut[.]com - POST /wp-content/plugins/aa.php?z=mer156lt24ah
- 2015-07-08 15:42:54 UTC - aslikarabulut[.]com - POST /wp-content/plugins/aa.php?p=58r4xamshb487we
- 2015-07-08 15:43:17 UTC - aslikarabulut[.]com - POST /wp-content/plugins/aa.php?g=e7n7ps1759uyr
ANGLER EK - 2015-07-08 at 16:08 UTC:
- 2015-07-08 16:08:46 UTC - zastapiony.piklamp[.]nl - GET /viewtopic.php?lb=84&x=8&n=0774&ek=35&vh=8
- 2015-07-08 16:08:48 UTC - zastapiony.piklamp[.]nl - GET /military.xbel?face=jlthEvD&oil=70UfcEdppE&similar=0T9GXVd&plane=&never=XzUI&size=h-S&
building=3NHL3LH4j&play=Ke9C4&over=&pattern=gKK
- 2015-07-08 16:08:53 UTC - zastapiony.piklamp[.]nl - GET /need.webarchivexml?permit=&arm=xeIzC36LXW&tell=&right=tWQfAn&directly=kr9njs37&knowledge=&
fail=Ed4rJ&none=&hear=D0tVDuOi&nor=IElUs&fiscal=hdb406
- 2015-07-08 16:08:55 UTC - zastapiony.piklamp[.]nl - GET /manager.hdm?industrial=&follow=Z7x&large=&kid=b3wOWyaiw&mean=mi7&local=XOFt&paper=&
time=XO4o&captain=rU8ZuvYZ&only=g8F4R&smile=Ukbh&such=njJRI9AF
- 2015-07-08 16:08:57 UTC - zastapiony.piklamp[.]nl - GET /there.mvc?describe=HBe&personal=44pH&total=&test=UfLU&off=a5uf&open=rbPva--L&
door=TJUPeSK0nCc8Ks3uroFuRdExE
IP-ADDR.ES IP CHECK & CRYPTOWALL 3.0 RANSOMWARE CHECK-IN:
- 2015-07-08 16:08:58 UTC - ip-addr[.]es - GET /
- 2015-07-08 16:08:58 UTC - bfiproductsinc[.]com - POST /wp-content/plugins/aa.php?d=1e1vvzwkwyxac
- 2015-07-08 16:09:01 UTC - bfiproductsinc[.]com - POST /wp-content/plugins/aa.php?l=fgywaiklqrurp3u
- 2015-07-08 16:09:05 UTC - bfiproductsinc[.]com - POST /wp-content/plugins/aa.php?g=7tsubm8q4lsd3i
- 2015-07-08 16:09:14 UTC - bfiproductsinc[.]com - POST /wp-content/plugins/aa.php?t=m0jhy77rcu1nf
Click here to return to the main page.