2015-07-16 - RIG EK FROM 46.30.42[.]238
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
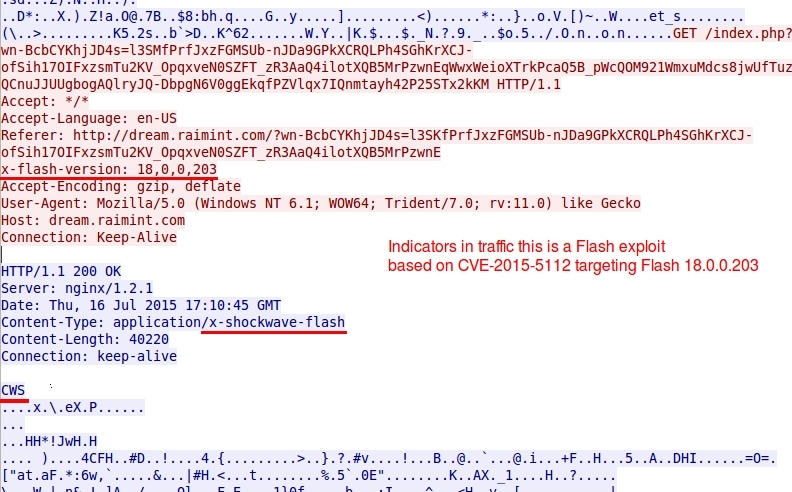
- Kafeine has already posted about Rig EK having the lastest Flash exploits from the Hacking Team compromise:
https://malware.dontneedcoffee.com/2015/07/cve-2015-5122-hackingteam-0d-two-flash.html
TRAFFIC
ASSOCIATED DOMAINS:
- 23.254.240[.]185 port 80 - valuemajor[.]com - Redirect/gate to Rig EK
- 46.30.42[.]238 port 80 - dream.raimint[.]com - Rig EK
TRAFFIC:
- 2015-07-16 17:10:42 UTC - valuemajor[.]com - GET /boom/jtr/order.php
- 2015-07-16 17:10:43 UTC - dream.raimint[.]com - GET /?wn-BcbCYKhjJD4s=l3SKfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioXTrkPcaQ5B_pWcQOM921WmxuMdcs8jwUfTuzQCnuJJUUgbrA
- 2015-07-16 17:10:44 UTC - dream.raimint[.]com - GET /index.php?wn-BcbCYKhjJD4s=l3SMfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioXTrkPcaQ5B_pWcQOM921WmxuMdcs8jwUfTuzQCnuJJUUgbogAQlryJQ-
DbpgN6V0ggEkqfPZVlqx7IQnmtayh42P25STx2kKM
- 2015-07-16 17:10:47 UTC - dream.raimint[.]com - GET /index.php?wn-BcbCYKhjJD4s=l3SMfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioXTrkPcaQ5B_pWcQOM921WmxuMdcs8jwUfTuzQCnuJJUUgbogAQlryJQ-
DbpgN6V0ggDE3KPZVlqx7IQnmtayh42P24RDN1nOWD&dop=0
Click here to return to the main page.