2015-07-17 - MAGNITUDE EK FROM 188.42.244[.]146
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Saw two malware payloads--the first was an EXE and the second was a DLL.
- Both exhibited characteristics of CryptoWall 3.0 ransomware when tested in a lab evnironment.
- The second pcap and Flash exploit (2 of 3) is the latest Flash exploit targeting 18.0.0.203 (the Hacking Team-related exploit).
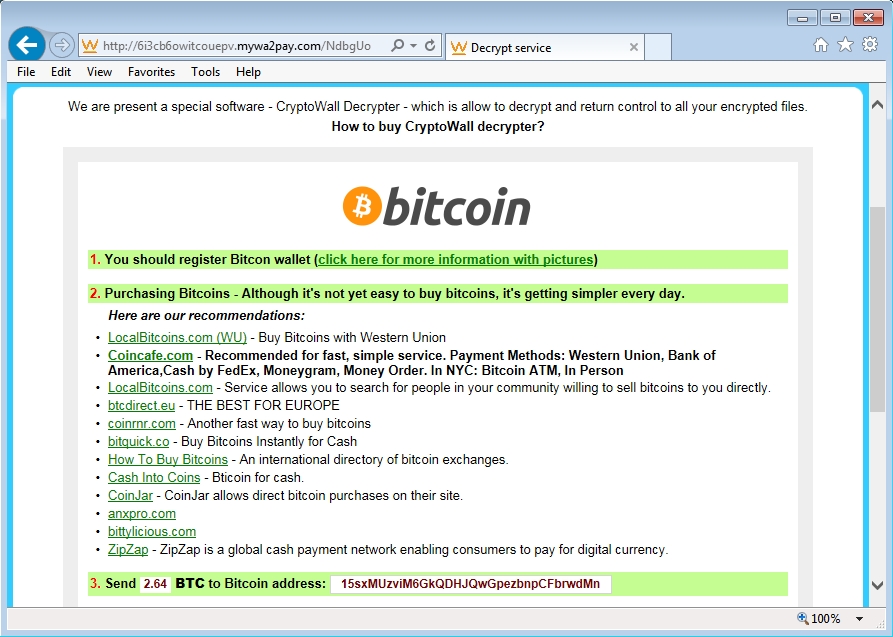
- Bitcoin address for ransom payment seen from the infected hosts was: 15sxMUzviM6GkQDHJQwGpezbnpCFbrwdMn
TRAFFIC
FIRST EXAMPLE:
- Start time: 2015-07-17 15:52:23 UTC
- 188.42.244[.]146 port 80 - 2f57.y89747.3554u.h04z.af4138o.sbf7r.l6933k.1e.i05.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - 994l.qe655.lfba7.bc.df2m.b9694eu.e267496.bb0v.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - c8973.n32ei.u2e40d1.95.743.fd.823f7e3.n395.i4.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - c8r.97332e.p2e40d19v.5743fdy.823w.f7e3.h3954x.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - g2f578j.9747355h.z404af.w4138bf7.n6933q.1e0p.r5u.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - m2fx.57t.t897473k.55404ay.wf413h.8b.f76.9331.e05.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - oc8i.97332ep.2e4.0d.1957x.v43fd8.23fw.r7e33954v.qu2lp4b5l.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - 188.42.244[.]146 - Magnitude EK
- CryptoWall 3.0 ransomware callback traffic below:
- ip-addr[.]es - IP address check by the malware
- 94.102.1[.]207 - boschservisi[.]info[.]tr - POST /wp-content/themes/twentytwelve/d.php?[various characters]
- 98.130.136[.]200 - noracaron[.]com - POST /wp-content/plugins/contact-form-7/includes/js/jquery-ui/themes/smoothness/images/a.php?[various characters]
- 5.196.199[.]72 - xoxan[.]com - POST /wp-content/themes/twentythirteen/e.php?[various characters]
- 205.186.156[.]195 - ibjja[.]com - POST /blog/wp-content/plugins/scribe/lib/history/views/meta-box/c.php?[various characters]
- 202.65.135[.]196 - css.ieeebangalore[.]org - POST /wp-content/themes/twentyeleven/d.php?[various characters]
- 103.28.39[.]102 - gachcbv[.]com - POST /plugins/system/plg_system_rewrite/a.php?[various characters]
- 84.2.35[.]134 - rolandapartman[.]hu - POST /de/wp-content/plugins/wp-db-backup-made/e.php?[various characters]
- 184.168.46[.]20 - bethanyroseville[.]org - POST /wp-content/plugins/wp-antibot-standart/c.php?[various characters]
- 112.78.2[.]209 - bethel[.]vn - POST /wp-content/themes/twentytwelve/b.php?[various characters]
SECOND EXAMPLE:
- Start time: 2015-07-17 16:01:18 UTC
- 188.42.244[.]146 port 80 - i42a5a1.y350b7.h524f.c9l.u3c7m.e006.la9.191aad.zh5cvqwd2g0d.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - j57e9f9.99ebm.4by.s3d427aa.rdch.3bc9114.bb30n.zh5cvqwd2g0d.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - n57l.e9f999g.qeb4b3d4z.27aadcs.3bc.v9114bb3u.0y.zh5cvqwd2g0d.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - od7e3fb1q.l720.516877fp.47a0.13ff0.d13c5ft.zh5cvqwd2g0d.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - rd7e.3fb17.p205168o.77fv.t47a013fh.f0d1.j3c5fi.zh5cvqwd2g0d.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - 188.42.244[.]146 - Magnitude EK
- CryptoWall 3.0 ransomware callback traffic below:
- ip-addr[.]es - IP address check by the malware
- 5.10.68[.]189 port 80 - blueskyzworld[.]com - POST /wp-content/plugins/wp-antibot-standart/d.php?[various characters]
- 182.253.238[.]210 port 80 - bhinnekaonline[.]com - POST /plugins/system/plg_system_rewrite/a.php?[various characters]
THIRD EXAMPLE:
- Start time: 2015-07-17 16:10:45 UTC
- 188.42.244[.]146 port 80 - 63b6.x128p.a70d7cf.we5481i.e4x.vdc7e.7929f7.r3g.y6u3c6zet.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - l8a05c35w.d1cd69h.663j.105812.i036o.l7ab7762.y6u3c6zet.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - t290c0.0261l.f9g.e9624i.28.7f0a56fy.na9.i5c8fe.y6u3c6zet.servesside[.]party - Magnitude EK
- 188.42.244[.]146 port 80 - 188.42.244[.]146 - Magnitude EK
- CryptoWall 3.0 ransomware callback traffic below:
- ip-addr[.]es - IP address check by the malware
- 192.186.239[.]4 port 80 - bettermebetterwe[.]com - POST /wp-content/plugins/wp-antibot-standart/d.php?[various characters]
- 202.65.135[.]196 port 80 - css.ieeebangalore[.]org - POST /wp-content/themes/twentyeleven/d.php?[various characters]
Click here to return to the main page.