2015-07-20 - NUCLEAR EK SENDS TESLACRYPT 2.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-07-20-Nuclear-EK-sends-TeslaCrypt-2.0-ransomware.pcap.zip
- 2015-07-20-Nuclear-EK-and-TeslaCrypt-ransomware-files.zip
NOTES:
- Kafeine tweeted about this ransomware on 2015-07-13 ( link ).
- The next day on Securelist, Kaspersky Lab released details on how TeslaCrypt ransomware, now at version 2.0, has been impersonating CryptoWall 3.0 ( link ).
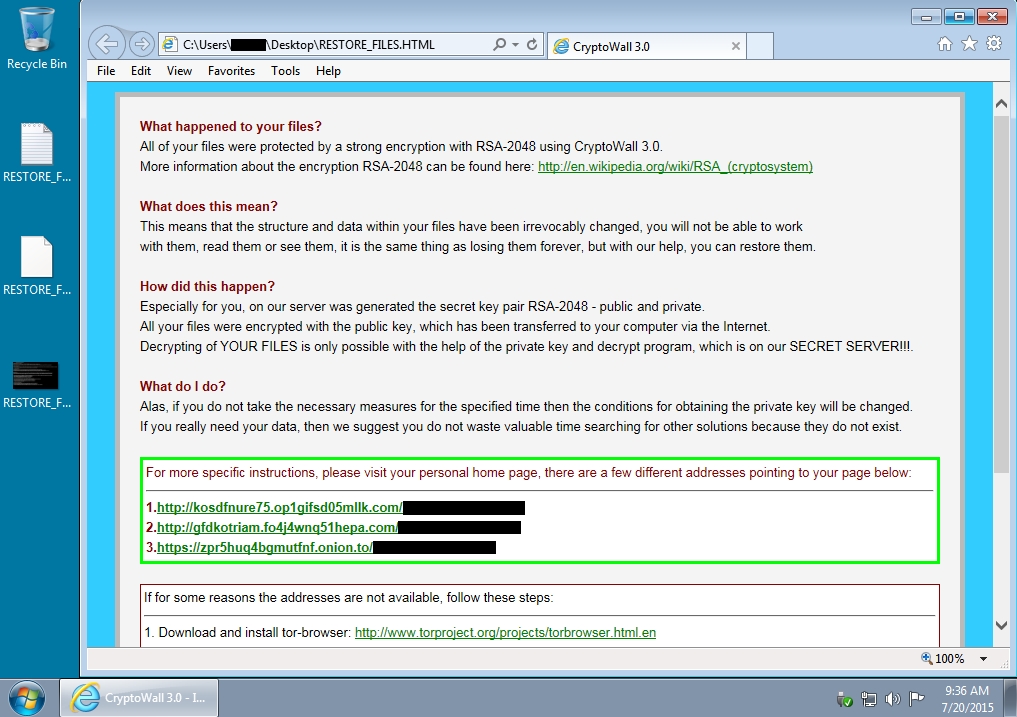
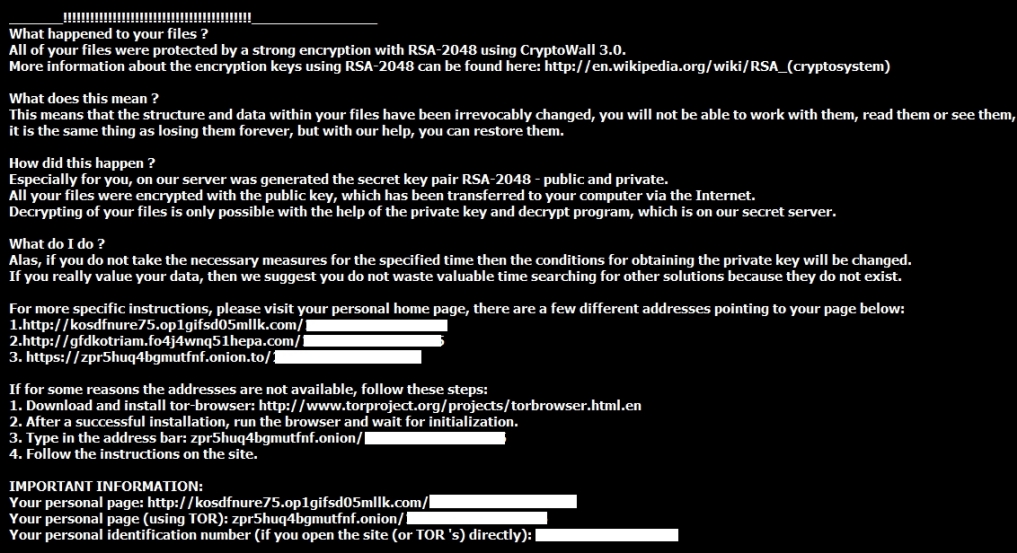
- On first glance, it might look like CryptoWall 3.0 ransomware, but artifacts and traffic from the infected host show this is an updated version of TeslaCrypt (also known as AlphaCrypt).
- Screenshots from the infected host are below.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 108.61.189[.]219 port 80 - evovapizdyk555[.]gq - Nuclear EK
- ipinfo[.]io - IP address check by the TeslaCrypt ransomware
- 104.28.4[.]29 port 80 - kosdfnure75.op1gifsd05mllk[.]com - Post-infection beaconing and checking the decrypt page
- 95.163.121[.]153 port 80 - gfdkotriam.fo4j4wnq51hepa[.]com - Checking anothe decrypt page
NUCLEAR EK:
- 2015-07-20 13:29:02 UTC - evovapizdyk555[.]gq - GET /RlBNXhNeTVBJAxNfRwBFDx9USAoAU1AeVhA.html
- 2015-07-20 13:29:02 UTC - evovapizdyk555[.]gq - GET /RlBNXhNeTVBJAxNfRwBFDx9USAoAU1AeVhA.html
- 2015-07-20 13:29:02 UTC - evovapizdyk555[.]gq - GET /VBlFGhIBSVlDCBkBTVAFGgBGXhdUFgxKVRheU1AFHwZEGlMGH1ANUUsGBU8HV1xMAFUGUVYJCVgGXxlWXVI
- 2015-07-20 13:29:05 UTC - evovapizdyk555[.]gq - GET /VwhZAxlHABkNEAtMAB0EVhlVRw5DBxVZSwVMDVAFBE9SFxkGB08EXlIeB1UbVFQJTVABVVIDCFkMVVxMBh1SF
iBKSR0E
POST-INFECTION TRAFFIC:
- 2015-07-20 13:29:09 UTC - ipinfo[.]io - GET /ip
- 2015-07-20 13:29:10 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img.php?412474D5A7CC8FA327D48B34F0891E99E14A63C6A3B0AC9D77DBAF21E1EEBA33B6F2
AA2BD5E8B228D806AD055F5ED50DEF46716CA7A2998241A14C397EA76A861C8AA838028245B889DB635230F5CCDE51C57887B5B367D1705703DF12073D1F8642
B1B2DCD30E4A20C5433C3D5820E729B96481F3550F594CA6B61DECCA08E5EE94972A1AF607E6F56CB1AE86EFAB6B97DAA9DA59B76F1262F84EBC6A23B7A68E
71C7E0468736881622B8855347B664D51829886767FFB9541E92F78B75E3FD7343E1BF1A9E7333E819AC93B193DCEA7873C223429B53403E59471574DCE42C
- 2015-07-20 13:29:36 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img.php?876C417D636DEF80B203C817C3D25DE3C19E3A10F3880A21B28652CF355E7AF1D961
DCC1ECCFD7A4D818A71A5D95F1AAEAAEF9849C19DF90C1C26AD9327BCE581807DEAFF495FE7CF6810E4FFBB9006F8803A333FBE5A5F3BCB24551C49738EA2
58314E5EAE70612469858944EBDA2B3DDA9E14D70A8A060D15BCE10A3A7486421CBD83A5C94AA2575156F3A5257B709E749455B517E9B2351549335CC97B259
- 2015-07-20 13:29:56 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /[information removed from the pcap (redacted)]
- 2015-07-20 13:29:57 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/style.css
- 2015-07-20 13:29:57 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/flags/us.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/flags/fr.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/flags/it.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/flags/es.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/flags/de.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /captcha.php
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/lt.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/rt.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/lb.png
- 2015-07-20 13:29:58 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/rb.png
- 2015-07-20 13:29:59 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /favicon.ico
- 2015-07-20 13:30:06 UTC - kosdfnure75.op1gifsd05mllk[.]com - POST /[information removed from the pcap (redacted)]
- 2015-07-20 13:30:08 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /service.php
- 2015-07-20 13:30:08 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/bitcoin.png
- 2015-07-20 13:30:08 UTC - kosdfnure75.op1gifsd05mllk[.]com - GET /img/button_pay.png
- 2015-07-20 13:30:42 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET [information removed from the pcap (redacted)]
- 2015-07-20 13:30:42 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/style.css
- 2015-07-20 13:30:42 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/flags/us.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/flags/it.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/flags/de.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/flags/es.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/flags/fr.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /captcha.php
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/lt.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/rt.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/lb.png
- 2015-07-20 13:30:43 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/rb.png
- 2015-07-20 13:30:44 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /favicon.ico
- 2015-07-20 13:30:47 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - POST /[information removed from the pcap (redacted)]
- 2015-07-20 13:30:48 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /service.php
- 2015-07-20 13:30:49 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/bitcoin.png
- 2015-07-20 13:30:49 UTC - gfdkotriam.fo4j4wnq51hepa[.]com - GET /img/button_pay.png
IDS ALERTS
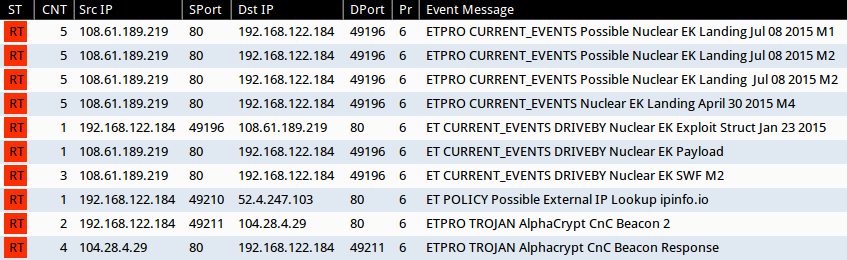
Significant signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion:
- 108.61.189[.]219 port 80 - ETPRO CURRENT_EVENTS Possible Nuclear EK Landing Jul 08 2015 M1 (sid:2811861)
- 108.61.189[.]219 port 80 - ETPRO CURRENT_EVENTS Possible Nuclear EK Landing Jul 08 2015 M2 (sid:2811862)
- 108.61.189[.]219 port 80 - ETPRO CURRENT_EVENTS Possible Nuclear EK Landing Jul 08 2015 M2 (sid:2811863)
- 108.61.189[.]219 port 80 - ETPRO CURRENT_EVENTS Nuclear EK Landing April 30 2015 M4 (sid:2810879)
- 108.61.189[.]219 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Exploit Struct Jan 23 2015 (sid:2020300)
- 108.61.189[.]219 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Payload (sid:2019873)
- 108.61.189[.]219 port 80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF M2 (sid:2020312)
- ipinfo[.]io port 80 - ET POLICY Possible External IP Lookup ipinfo[.]io (sid:2020716)
- 104.28.4[.]29 port 80 - ETPRO TROJAN AlphaCrypt CnC Beacon 2 (sid:2812046)
- 104.28.4[.]29 port 80 - ETPRO TROJAN Alphacrypt CnC Beacon Response (sid:2811043)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2015-07-20-Nuclear-EK-flash-exploit.swf
File size: 23,803 bytes
MD5 hash: 9d981efe8be1fe0a54937652cce94013
SHA256 hash: 8740775f8aea01d4e3013863ba4a8e1a553f89e71375530e7198865af2673488
Detection ratio: 1 / 55
First submission to VirusTotal: 2015-07-20 14:48:23 UTC
MALWARE PAYLOAD:
File name: 2015-07-20-Nuclear-EK-payload-TeslaCrypt-2.0-ransomware.exe
File size: 357,888 bytes
MD5 hash: 50fd967b39315d95f02127a2f05f6326
SHA256 hash: 8271d841b9971f04d6a48804d06ecd7185d71ed8546988b1697fbe01741a8572
Detection ratio: 7 / 55
First submission to VirusTotal: 2015-07-20 14:48:42 UTC
Click here to return to the main page.