2015-07-24 - TRAFFIC ANALYSIS EXERCISE - ANSWERS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
TRAFFIC:
- 2015-07-24-traffic-analysis-exercise.pcap.zip 52.1 MB (52,090,873 bytes)
ANSWERS
The infected computer's host name:
- Leonardo-PC
The infected computer's MAC address:
- 80:c1:6e:6a:0b:f2 (HewlettP_6a:0b:f2)
The infected computer's operating system and browser:
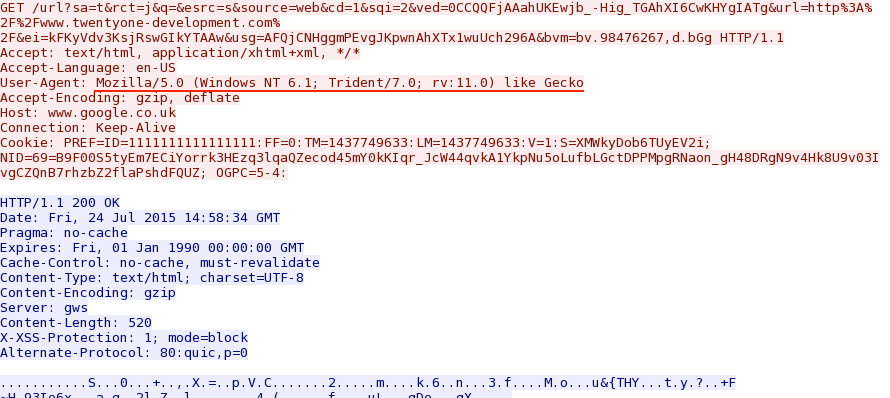
- Windows 7 and Internet Explorer 11
Exploit kit (Angler, Magnitude, or Nuclear?):
- Angler exploit kit
IP address and domain name used by the exploit kit:
- 185.43.223[.]164 - kiralyi.arcadiumentertainment[.]com
Compromised website that caused the exploit kit traffic:
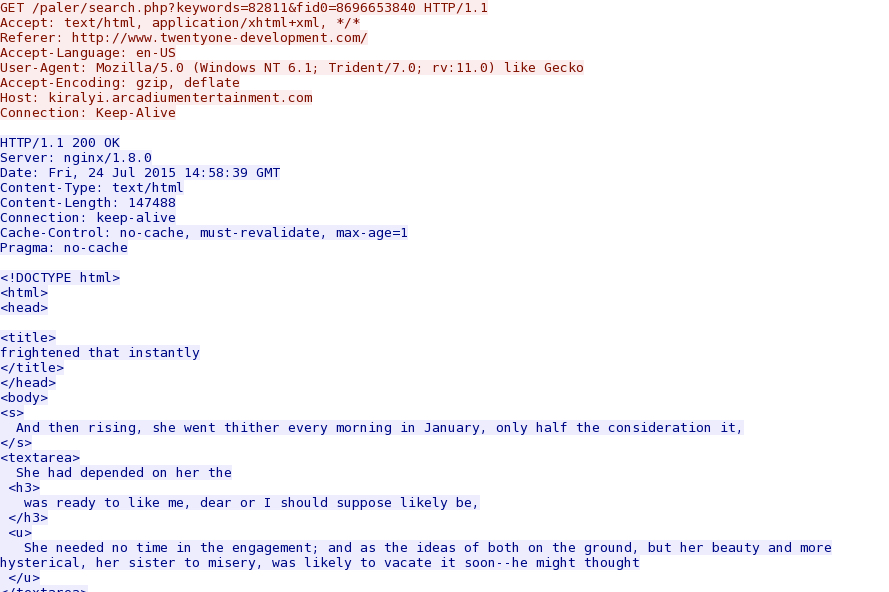
- www.twentyone-development[.]com
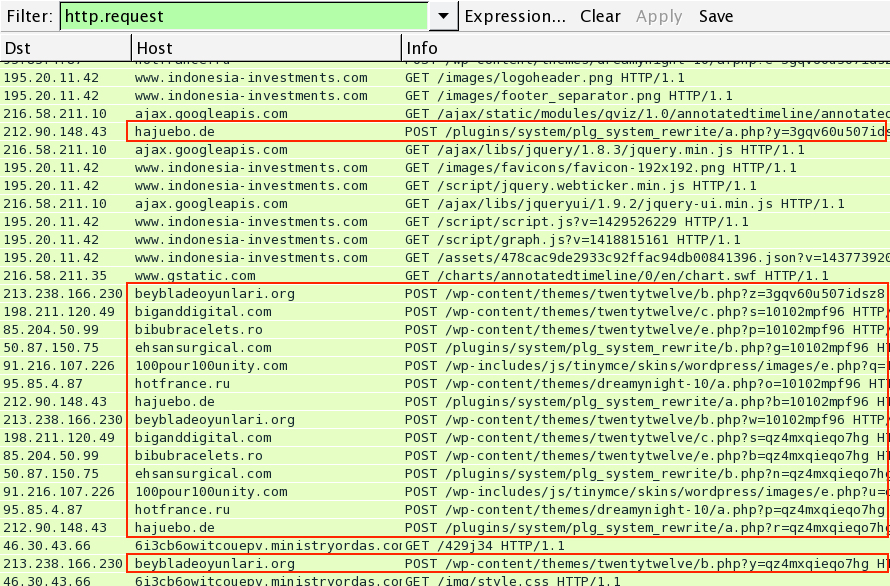
Domains and IP addresses from the CryptoWall 3.0 post-infection traffic:
- ip-addr[.]es - 188.165.164[.]184
- biganddigital[.]com - 198.211.120[.]49
- bibubracelets[.]ro - 85.204.50[.]99
- ehsansurgical[.]com - 50.87.150[.]75
- 100pour100unity[.]com - 91.216.107[.]226
- hotfrance[.]ru - 95.85.4[.]87
- hajuebo[.]de - 212.90.148[.]43
- beybladeoyunlari[.]org - 213.238.166[.]230
- 6i3cb6owitcouepv.ministryordas[.]com - 46.30.43[.]66
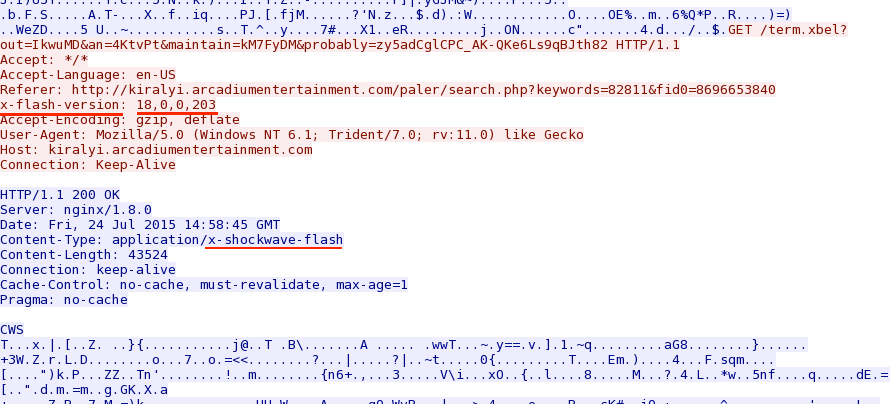
What was vulnerable one the user's computer? (the browser, Flash, Java, Silverlight, etc.):
- Flash (running 18.0.0.203 whis is vulnerable to the most recent hacking team exploits).
HINTS
Finding the computer's host name and mac address through DHCP traffic in the pcap:
Finding the OS and browser? Look for the user-agent string in one of the requests to Google. In the example below, you see it's Windows 7 (NT 6.1) and this user-agent string is used for Internet Explorer 11 (rv:11.0):
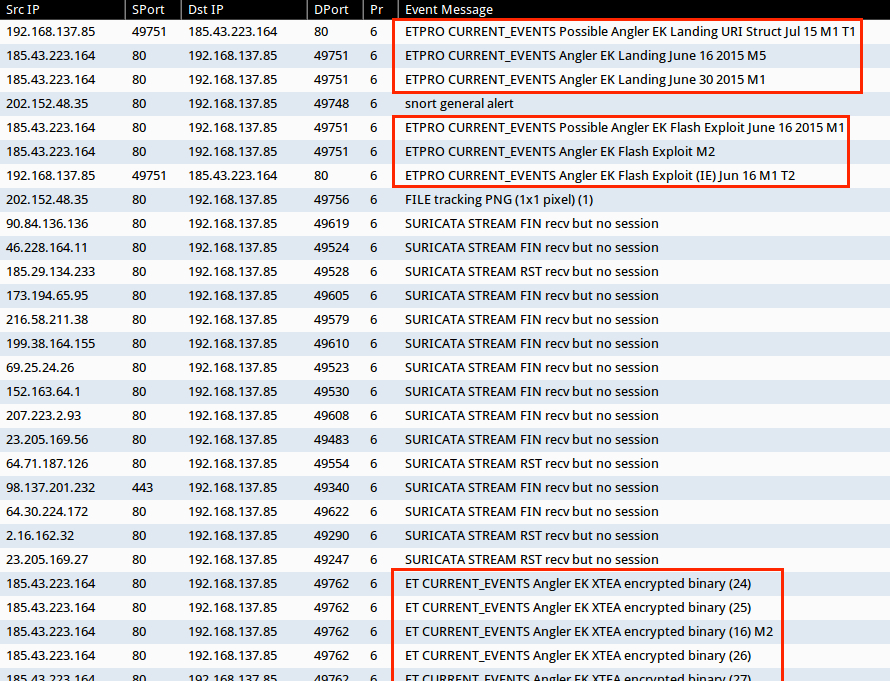
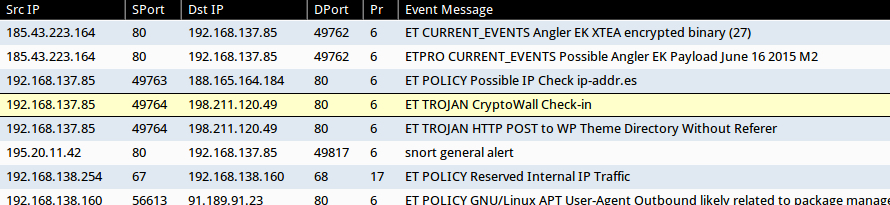
Snort events using Suricata in Security Onion (with the EmergingThreats and ET PRO rulesets) show alerts for the Angler exploit kit on 185.43.223[.]164:
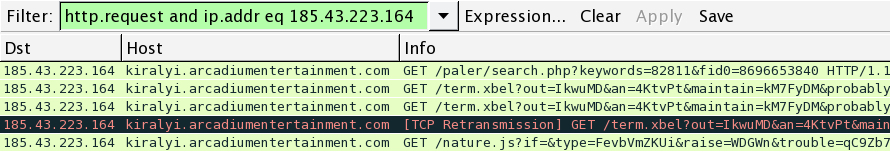
Filter in Wireshark on 185.43.223[.]164 to find the domain name used by Angler EK:
Follow the TCP stream for the first HTTP GET request by Angler EK, and you'll see the "referer" line showing the compromised website that kicked off this infection chain:
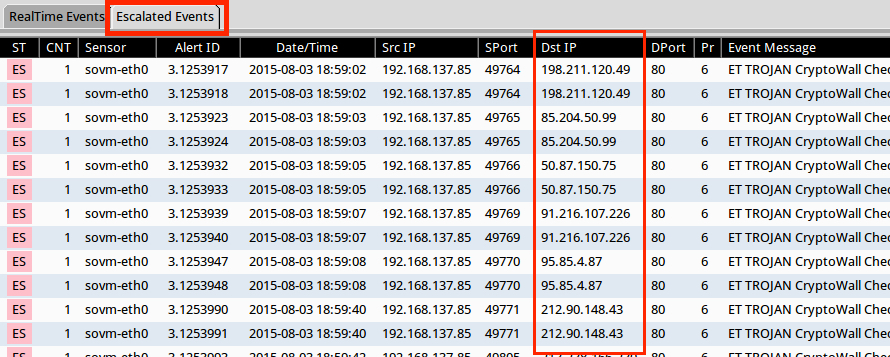
In Security Onion, I use Squil. Squil will group alerts according to source IP. That means there could be several destination IPs. Select the alert and hit F9 to escalate these events and see them individually:
Go to the "Escallated Events" tab in Squil, and you'll see individual events with all the destination IP addresses:
You can double-check the CryptoWall post-infection traffic, noted in the image blow (outlined in red). Of note, 6i3cb6owitcouepv.ministryordas[.]com is a domain for the page that the user went to for decrypt instructions. Traffic to ip-addr[.]es is the CryptoWall 3.0 checking the infected host's IP address.
Below shows the Flash version as 18.0.0.203, which is vulnerable to Flash exploits used by Angler EK: