2015-08-05 - AN EXAMPLE OF LEGITIMATE JAVA UPDATE TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
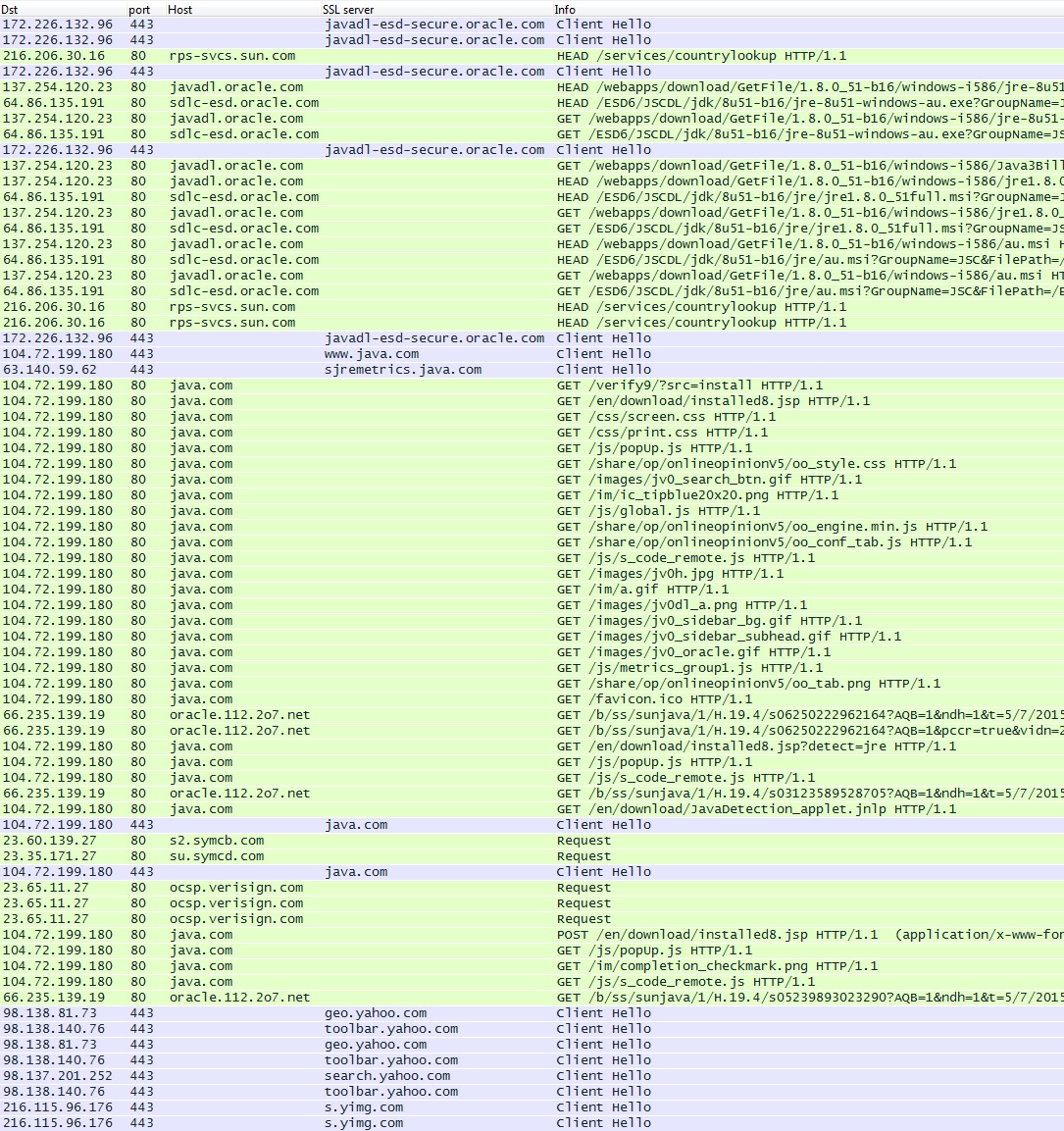
- I'm posting some legitimate Java update traffic in response to a reader request to see what it looks like.
- I had a machine update from some out-of-date version of Java 7 to the most up-to-date version of Java 8 (currently update 51).
- I heavily edited the pcap, so it should only have the HTTP requests, responses, and SSL packets that contain the server names in the Client Hello packet.
------Original Message------
From: [redacted]
Sent: Wednesday, July 29, 2015 02:26 UTC
To: brad@malware-traffic-analysis.net
Subject: RE: Password Request
Hi Brad,
Thanks very much for your blog and trace files and explanations.
I have still yet to have a good look through things, however I thought I'd ask if you have ever done an analysis of legitimate Java update traffic? I am curious to see what proper communications should look like, and what servers might be involved in the update process, as this might allow me to better catch traffic that attempts to hide itself under this process.
Would you have anything I might use? Might make for an interesting post otherwise?
Regards
[redacted]
------Original Message------
From: brad@malware-traffic-analysis.net
Sent: Wednesday, 29 July 2015 02:31 UTC
To: [redacted]
Subject: RE: Password Request
[redacted],
I don't have anything off-hand, but I might be able to generate some legitimate update traffic as an example. Let me see what I can come up with in the next few days.
Regards,
Brad
WHAT IT LOOKS LIKE FILTERED IN WIRESHARK
Click here to return to the main page.
