2015-08-17 - ANGLER EK SENDS BEDEP FROM 94.23.170[.]230 - POVAZAN.SPACEDISCUSSIONS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
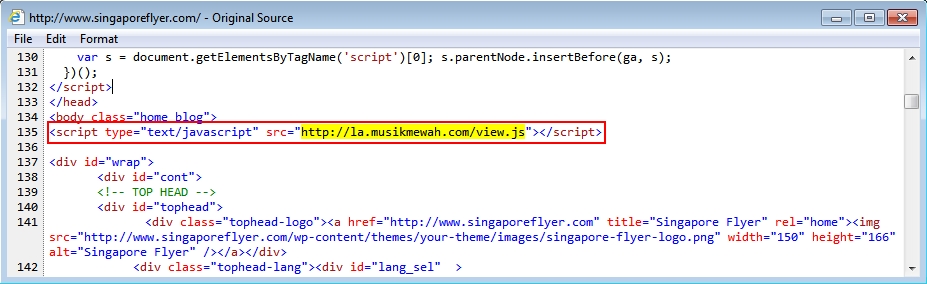
Shown above: malicious script in page from compromised website
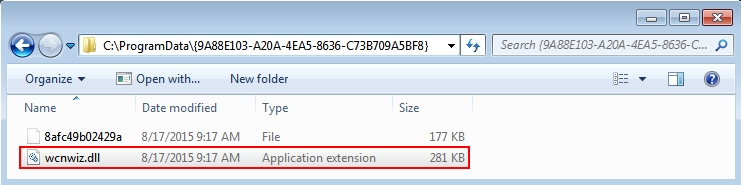
Shown above: malware found on the infected host
TRAFFIC
ASSOCIATED DOMAINS:
- www.singaporeflyer[.]com - Compromised website
- 46.4.100[.]240 port 80 - la.musikmewah[.]com - Redirect (gate)
- 94.23.170[.]230 port 80 - povazan.spacediscussions[.]com - Angler EK
- 83.149.127[.]8 port 80 - ajfszwomnhdfcyy[.]com - Bedep post-infection traffic
- 95.211.202[.]34 port 80 - e529afjrnl8[.]com - Click fraud traffic starts
- 162.244.34[.]39 port 80 - py9kqyq340w[.]com - Click fraud traffic starts
- 95.211.189[.]99 port 80 - hxye5y6bwyd1[.]com - Click fraud traffic starts
- 95.211.189[.]117 port 80 - zyoz6g1hrf[.]com - Click fraud traffic starts
COMPROMISED WEBSITE AND REDIRECT:
- 2015-08-17 14:14:52 UTC - www.singaporeflyer[.]com - GET /
- 2015-08-17 14:14:54 UTC - la.musikmewah[.]com - GET /view.js
ANGLER EK:
- 2015-08-17 14:14:59 UTC - povazan.spacediscussions[.]com - GET /civis/viewtopic.php?t=17g4q&f=u.95tl9w0y0664&
- 2015-08-17 14:15:15 UTC - povazan.spacediscussions[.]com - GET /else.hxs?mark=&walk=OR0HOT&press=&need=K-v0O&help=&night=TOI&
choose=ykY4qYIfK3&catch=MQep&describe=&hit=JFq&wife=JTk&period=ejlvzgOu&sense=SOfTTb
- 2015-08-17 14:15:33 UTC - povazan.spacediscussions[.]com - GET /along.xhtm?be=&never=nrKcXFl_Ei&already=&movement=l0aTYL&
apparently=9OxoV&save=BX2C9ASKg&until=BjsyVcfomo&across=mLFymLy&example=U
- 2015-08-17 14:15:43 UTC - povazan.spacediscussions[.]com - GET /window.mhtml?above=Wcw6MJH&medical=&marry=Y3-Lkxt4&local=&
information=trmPZ&another=_mZ&contribute=&six=uO7OxxhXGI&fiscal=&an=Wcu&individual=2ggpxBdU&brother=N27G
BEDEP-RELATED POST-INFECTION TRAFFIC:
- 2015-08-17 14:15:41 UTC - www.microsoft[.]com - GET /
- 2015-08-17 14:15:42 UTC - www.microsoft[.]com - GET /en-nz/
- 2015-08-17 14:15:45 UTC - www.ecb.europa[.]eu - GET /stats/eurofxref/eurofxref-hist-90d.xml?e1d9131dc7633558e6eb0f0d692bcb6f
- 2015-08-17 14:15:56 UTC - ajfszwomnhdfcyy[.]com - POST /album.php
- 2015-08-17 14:15:58 UTC - ajfszwomnhdfcyy[.]com - POST /newthread.php
- 2015-08-17 14:16:22 UTC - ajfszwomnhdfcyy[.]com - POST /include/functions_ad.php
- 2015-08-17 14:17:20 UTC - ajfszwomnhdfcyy[.]com - POST /calendar.php
- 2015-08-17 14:17:20 UTC - ajfszwomnhdfcyy[.]com - POST /include/class_database_explain.php
- 2015-08-17 14:17:21 UTC - ajfszwomnhdfcyy[.]com - POST /forum.php
- 2015-08-17 14:17:22 UTC - ajfszwomnhdfcyy[.]com - POST /sendmessage.php
- 2015-08-17 14:17:39 UTC - ajfszwomnhdfcyy[.]com - POST /register.php
CLICK FRAUD TRAFFIC BEGINS:
- 2015-08-17 14:18:27 UTC - e529afjrnl8[.]com - GET /ads.php?sid=1917
- 2015-08-17 14:18:27 UTC - py9kqyq340w[.]com - GET /ads.php?sid=1917
- 2015-08-17 14:18:27 UTC - hxye5y6bwyd1[.]com - GET /ads.php?sid=1917
- 2015-08-17 14:18:27 UTC - zyoz6g1hrf[.]com - GET /ads.php?sid=1917
Click here to return to the main page.
