2015-09-04 - UPATRE/DYRE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSSOCIATED FILES:
- 2015-09-04-Upatre-Dyre-infection-traffic.pcap.zip
- 2015-09-04-Upatre-malspam-6-examples.zip
- 2015-09-04-Upatre-Dyre-malware-and-artifacts.zip
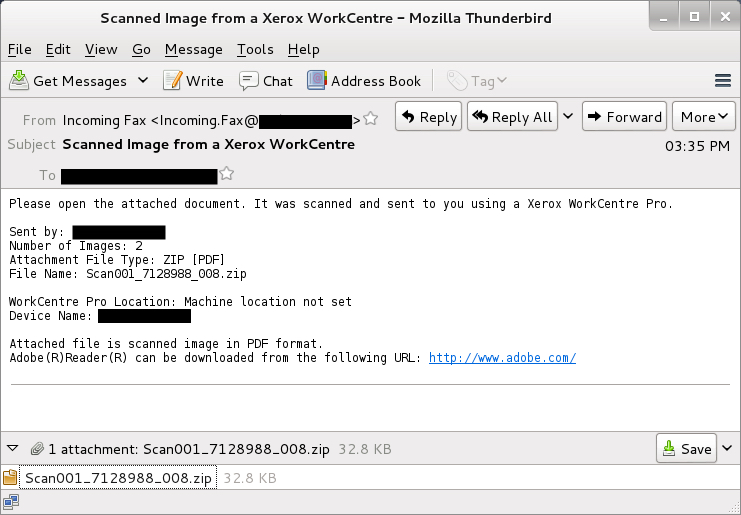
EXAMPLE OF THE MALSPAM
PRELIMINARY MALWARE ANALYSIS
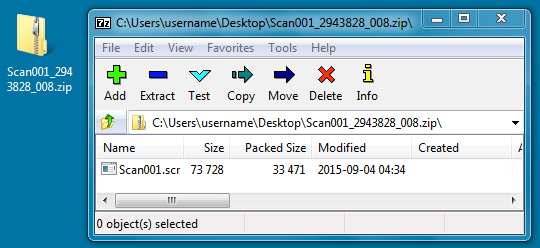
ATTACHMENT NAME: Scan001_7128988_008.zip
File size: 33,591 bytes
MD5 hash: e9cabedda5d774be751ab7c3d0057a77
SHA1 hash: dd8b5ec44b59d55bfbefd2035857ffcb86fbf14d
SHA256 hash: ea5b0f87e191a44e702b40c55b025b70fb6f889abef12f303b809ec93d575932
First submission: 2015-09-04 13:56:16 UTC
Detection ratio: 16 / 57
https://www.virustotal.com/en/file/ea5b0f87e191a44e702b40c55b025b70fb6f889abef12f303b809ec93d575932/analysis/
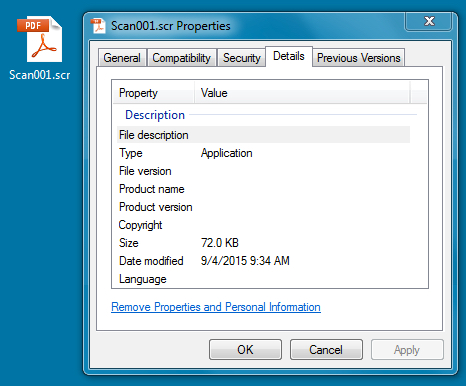
EXTRACTED FILE NAME: Scan001.scr
File size: 73,728 bytes
MD5 hash: 4196ff0ecb496055beb2d43c4e714aa9
SHA1 hash: 19c26ed6946c4c53f67796a057e814056a82d60f
SHA256 hash: 205844540987d4ec9d382d928ca1761d40e0013dc64378e78d21d0b29256a317
Detection ratio: 13 / 56
First submission: 2015-09-04 13:04:13 UTC
https://www.virustotal.com/en/file/205844540987d4ec9d382d928ca1761d40e0013dc64378e78d21d0b29256a317/analysis/
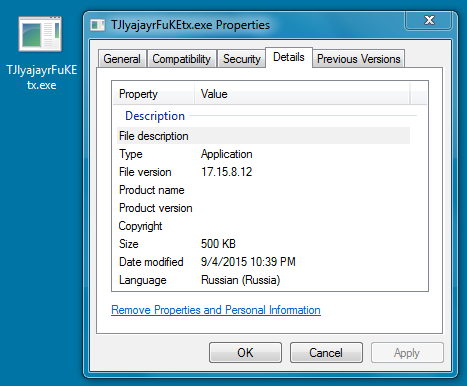
DOWNLOADED DYRE MALWARE: C:\User\username\AppData\Local\TJlyajayrFuKEtx.exe
File size: 512,000 bytes
MD5 hash: b6b11055833b55a9bdb6f2b344baf81f
SHA1 hash: ac4480d3bc81a2c91b3a342037dec0d9310b7964
SHA256 hash: 56f8fc385f36aea8d3ff8ab59ab6e75314190f3560ad76f51c1c1085a5b8ea1b
Detection ratio: 5 / 56
First submission: 2015-09-04 15:34:17 UTC
https://www.virustotal.com/en/file/56f8fc385f36aea8d3ff8ab59ab6e75314190f3560ad76f51c1c1085a5b8ea1b/analysis/
OTHER ARTIFACTS NOTED:
Encrypted or some sort of data binary: C:\User\username\AppData\Local\72c299b02320650fe75c0c638cb0b404
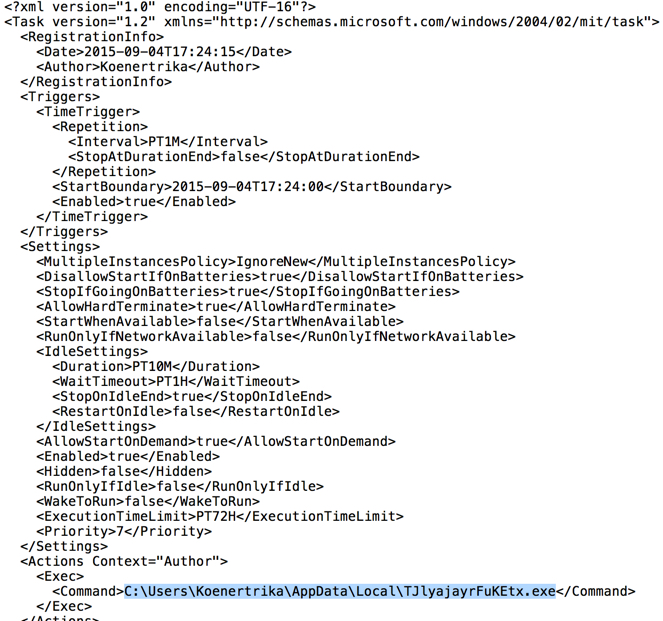
Task to keep the malware persistent: C:\Windows\System32\Tasks\TJlyajayrFuKEtx
CHAIN OF EVENTS
TRAFFIC:
- 2015-09-04 17:23:49 UTC - icanhazip[.]com - GET /
- 2015-09-04 17:23:52 UTC - 197.149.90[.]166:12299 - GET /4SU77/KOENERTRIKA-PC/0/61-SP1/0/KHBEEIBFEHBFEF
- 2015-09-04 17:23:53 UTC - 69.144.171[.]44 port 443 (https) - GET /warning77.zip
- 2015-09-04 17:23:57 UTC - 197.149.90[.166:12299 - GET /4SU77/KOENERTRIKA-PC/41/5/1/KHBEEIBFEHBFEF
- 2015-09-04 17:24:03 UTC - 64.233.176[.]113 port 80 - DNS query for google[.]com and attempted HTTP traffic
- 2015-09-04 17:24:03 UTC - 91.200.16[.]56 port 3478 - UDP STUN traffic to stun.noc.ams-ix[.]net
- 2015-09-04 17:24:05 UTC - 184.190.64[.]35 port 4443 (https) - Encrypted traffic, periodic TCP connections
- 2015-09-04 17:24:17 UTC - 82.103.71[.]149 port 443 (https) - Encrypted traffic
HTTP AND HTTPS TRAFFIC:
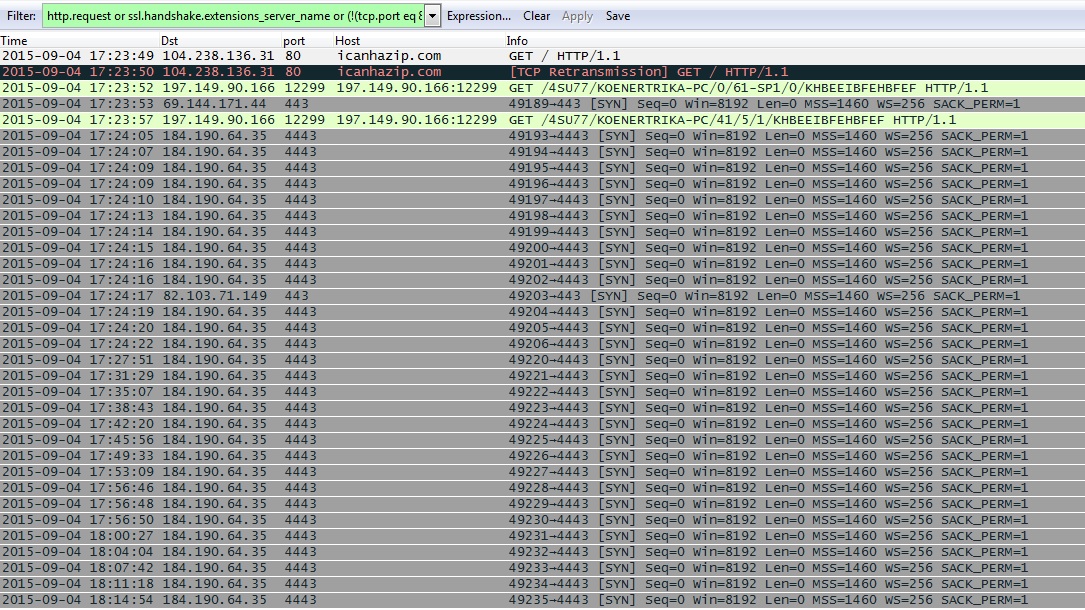
HTTPS REQUEST FROM THE INTERNET EXPLORER CACHE:
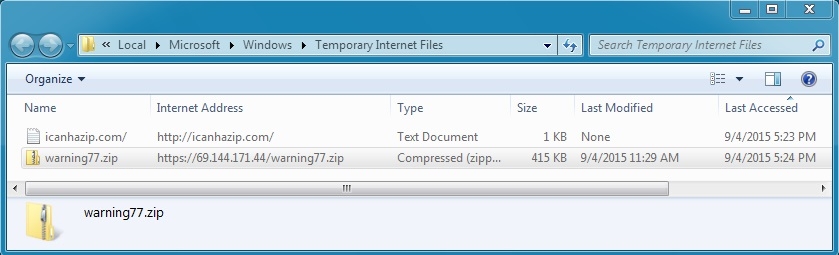
SOME OF THE CERTIFICATE DATA FROM THE HTTPS TRAFFIC:
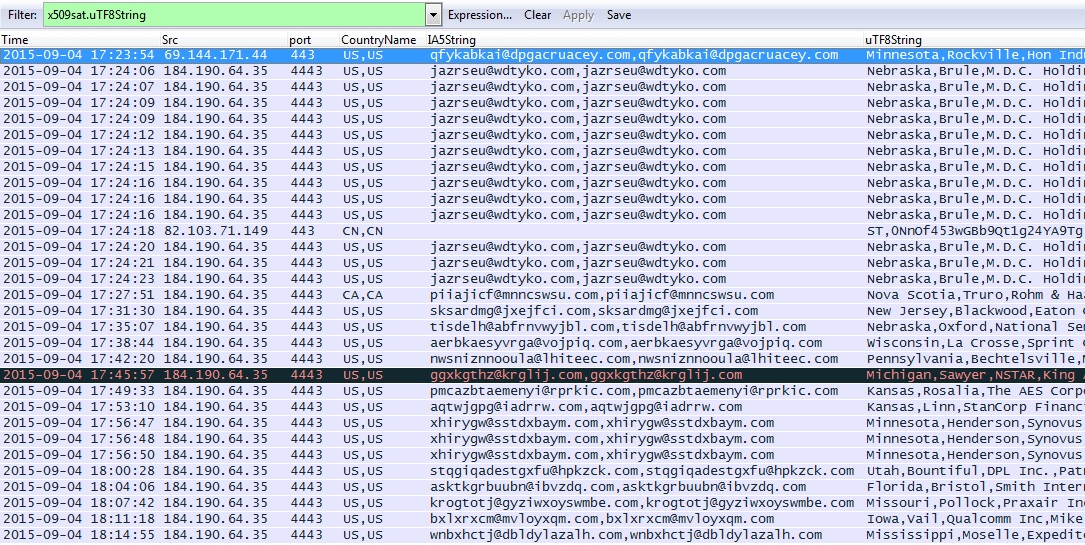
CERTIFICATE INFO
69.144.171[.]44 TCP PORT 443:
Country, State, Locality (city): US, Minnesota, Rockville
Organziation name: Hon Industries Inc.
Common name: Foster Elliot
Organizational Unit name: Hon Industries Inc.
Email address: qfykabkai@dpgacruacey[.]com
82.103.71[.]149 TCP PORT 443:
Country, State, Locality (city): CN, ST, 0NnOf453wGBb9Qt1g24YA9Tg
Organziation name: BrI9hRoBLnPjb9dWz04Bnb4T
Common name: oHbECjOD3mWybdlZ55TWBABk
184.190.64[.]35 TCP PORT 4443:
Country, State, Locality (city): CA, Nova Scotia, Truro
Organziation name: Rohm & Haas Co.
Common name: Forrest Khan
Organizational Unit name: Rohm & Haas Co.
Email address: piiajicf@mnncswsu[.]com
Country, State, Locality (city): US, Florida, Bristol
Organziation name: Smith International Inc
Common name: Abbie Wright
Organizational Unit name: Smith International Inc
Email address: asktkgrbuubn@ibvzdq[.]com
Country, State, Locality (city): US, Iowa, Vail
Organziation name: Qualcomm Inc
Common name: Mike Easton
Organizational Unit name: Qualcomm Inc
Email address: bxlxrxcm@mvloyxqm[.]com
Country, State, Locality (city): US, Kansas, Linn
Organziation name: StanCorp Financial Group Inc
Common name: Sutton Horne
Organizational Unit name: StanCorp Financial Group Inc
Email address: aqtwjgpg@iadrrw[.]com
Country, State, Locality (city): US, Kansas, Rosalia
Organziation name: The AES Corporation
Common name: Mitchell Olson
Organiztional Unit name: The AES Corporation
Email address: pmcazbtaemenyi@rprkic[.]com
Country, State, Locality (city): US, Michigan, Sawyer
Organziation name: NSTAR
Common name: King Alexis
Organizational Unit name: NSTAR
Email address: ggxkgthz@krglij[.]com
Country, State, Locality (city): US, Minnesota, Henderson
Organziation name: Synovus Financial Corp.
Common name: Gordon Mccartney
Organizational Unit name: Synovus Financial Corp.
Email address: xhirygw@sstdxbaym[.]com
Country, State, Locality (city): US, Mississippi, Moselle
Organziation name: Expeditors International of Washington Inc.
Common name: Doyle Moffatt
Organizational Unit name: Expeditors International of Washington Inc.
Email address: wnbxhctj@dbldylazalh[.]com
Country, State, Locality (city): US, Missouri, Pollock
Organziation name: Praxair Inc
Common name: Ollie \303\203\302\211douard
Organizational Unit name: Praxair Inc
Email address: krogtotj@gyziwxoyswmbe[.]com
Country, State, Locality (city): US, Nebraska, Brule
Organziation name: M.D.C. Holdings Inc.
Common name: Nicola Shannon
Organizational Unit name: M.D.C. Holdings Inc.
Email address: jazrseu@wdtyko[.]com
Country, State, Locality (city): US, Nebraska, Oxford
Organziation name: National Semiconductor Corporation
Common name: Stephanie Richeson
Organizational Unit name: National Semiconductor Corporation
Email address: tisdelh@abfrnvwyjbl[.]com
Country, State, Locality (city): US, New Jersey, Blackwood
Organziation name: Eaton Corporation
Common name: Hodgson Lapointe
Organizational Unit name: Eaton Corporation
Email address: sksardmg@jxejfci[.]com
Country, State, Locality (city): US, Pennsylvania, Bechtelsville
Organziation name: Merrill Lynch & Co. Inc.
Common name: Palmer Parr
Organizational Unit name: Merrill Lynch & Co. Inc.
Email address: nwsniznnooula@lhiteec[.]com
Country, State, Locality (city): US, Utah, Bountiful
Organziation name: DPL Inc.
Common name: Patrick Nagel
Organizational Unit name: vDPL Inc.
Email address: stqgiqadestgxfu@hpkzck[.]com
Country, State, Locality (city): US, Wisconsin, La Crosse
Organziation name: Sprint Corp.
Common name: Marcus Robertson
Organizational Unit name: Sprint Corp.
Email address: aerbkaesyvrga@vojpiq[.]com
Click here to return to the main page.